2017-06-28 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-28-Hancitor-infection-with-ZLoader.pcap.zip 9.3 MB (9,283,541 bytes)
- 2017-06-28-Hancitor-infection-with-ZLoader.pcap (10,102,479 bytes)
- 2017-06-28-Hancitor-malspam-13-examples.zip 25.7 kB (25,714 bytes)
- 2017-06-28-Hancitor-malspam-140314-UTC.eml (8,716 bytes)
- 2017-06-28-Hancitor-malspam-142551-UTC.eml (8,712 bytes)
- 2017-06-28-Hancitor-malspam-143504-UTC.eml (8,719 bytes)
- 2017-06-28-Hancitor-malspam-151209-UTC.eml (8,715 bytes)
- 2017-06-28-Hancitor-malspam-160108-UTC.eml (8,721 bytes)
- 2017-06-28-Hancitor-malspam-162417-UTC.eml (8,720 bytes)
- 2017-06-28-Hancitor-malspam-163623-UTC.eml (8,717 bytes)
- 2017-06-28-Hancitor-malspam-164557-UTC.eml (8,725 bytes)
- 2017-06-28-Hancitor-malspam-165812-UTC.eml (8,721 bytes)
- 2017-06-28-Hancitor-malspam-171623-UTC.eml (8,723 bytes)
- 2017-06-28-Hancitor-malspam-175725-UTC.eml (8,720 bytes)
- 2017-06-28-Hancitor-malspam-180522-UTC.eml (8,718 bytes)
- 2017-06-28-Hancitor-malspam-180554-UTC.eml (8,721 bytes)
- 2017-06-28-malware-from-Hancitor-infection.zip 304.9 kB (304,884 bytes)
- BNC3BB.tmp (188,416 bytes)
- Ringcentral_Fax_654608.doc (288,256 bytes)
SOME TWEETS COVERING THE 2017-06-28 WAVE OF #HANCITOR MALSPAM:
- @James_inthe_box: New #hancitor run "New Fax Message from <phone number> on <date> at <time> (link)
- @cheapbyte: #hancitor #malspam #phishing Hancitor June 28 2017 links, URLs at ghostbin (link)
EMAILS
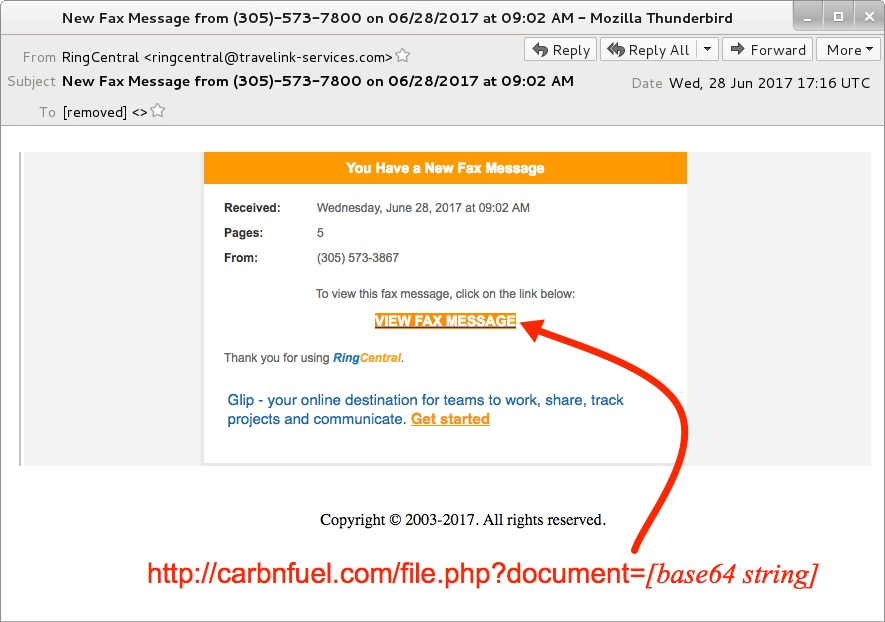
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date: Wednesday 2017-06-28 as early as 14:03 UTC through at least 18:05 UTC
- From: "RingCentral" <ringcentral@travelink-services[.]com>
- Subject: New Fax Message from (305)-003-2774 on 06/28/2017 at 09:02 AM
- Subject: New Fax Message from (305)-216-1424 on 06/28/2017 at 09:02 AM
- Subject: New Fax Message from (305)-282-2820 on 06/28/2017 at 09:02 AM
- Subject: New Fax Message from (305)-337-2748 on 06/28/2017 at 09:02 AM
- Subject: New Fax Message from (305)-436-6110 on 06/28/2017 at 09:02 AM
- Subject: New Fax Message from (305)-441-5456 on 06/28/2017 at 09:02 AM
- Subject: New Fax Message from (305)-464-2036 on 06/28/2017 at 09:02 AM
- Subject: New Fax Message from (305)-573-7800 on 06/28/2017 at 09:02 AM
- Subject: New Fax Message from (305)-621-5853 on 06/28/2017 at 09:02 AM
- Subject: New Fax Message from (305)-672-1683 on 06/28/2017 at 09:02 AM
- Subject: New Fax Message from (305)-746-7840 on 06/28/2017 at 09:02 AM
- Subject: New Fax Message from (305)-851-8471 on 06/28/2017 at 09:02 AM
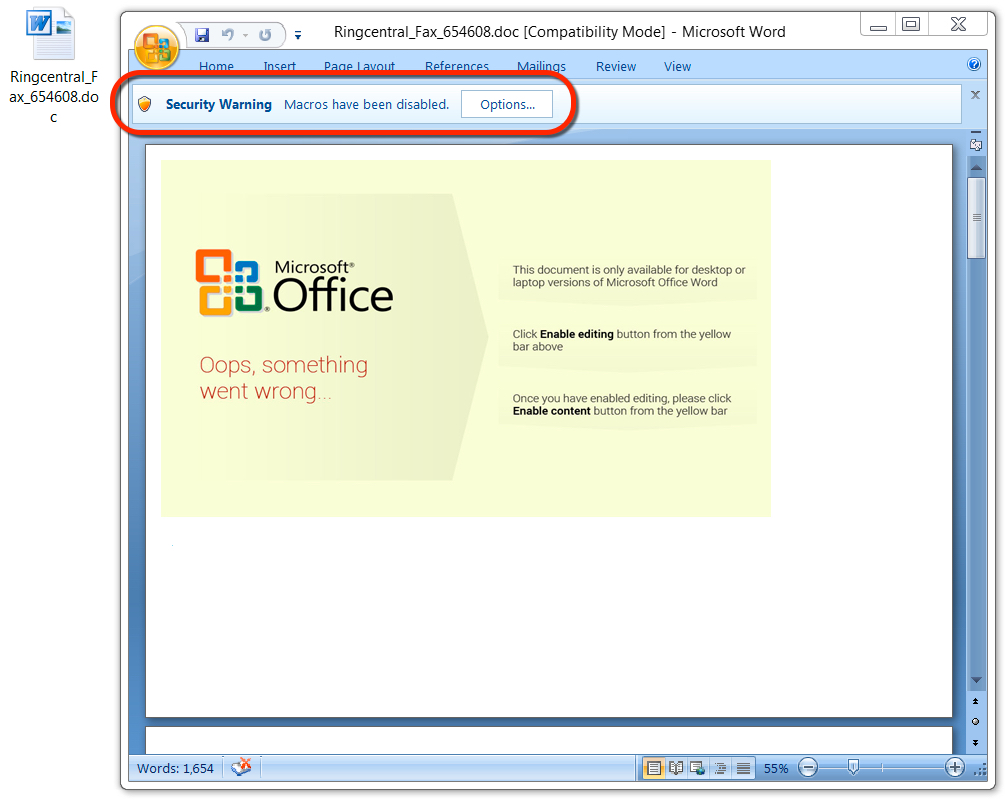
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
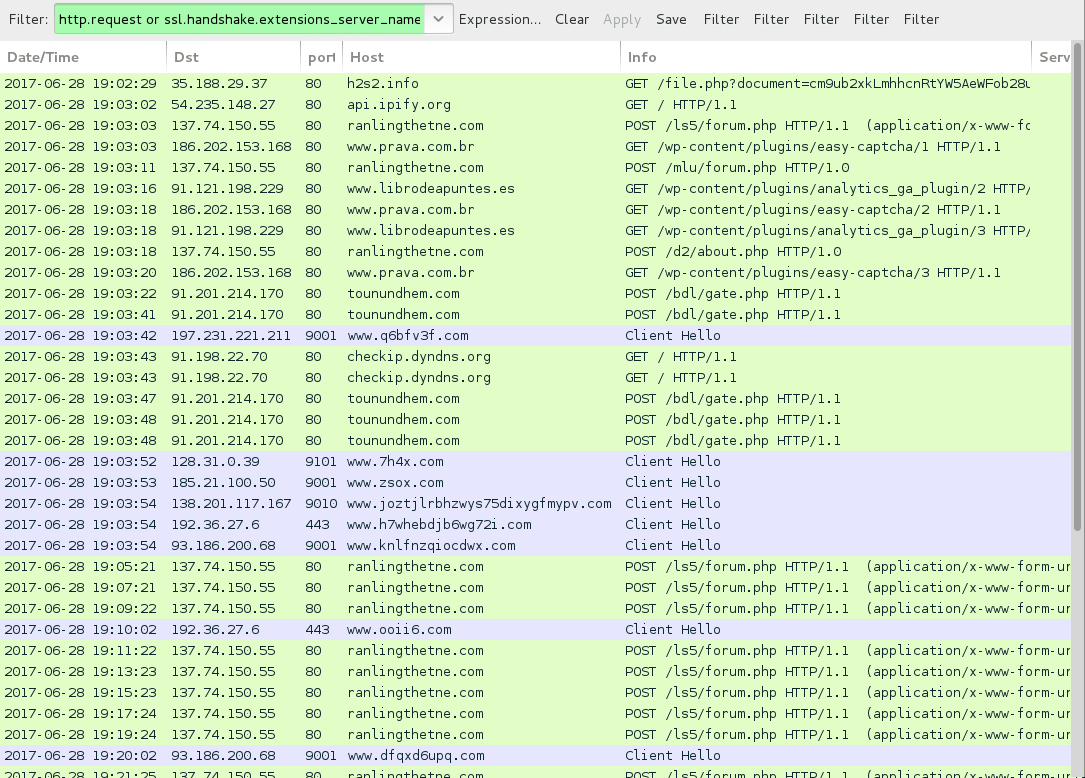
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUESTS FOR THE WORD DOCUMENT:
- AWAREARRESTALIGN[.]COM - GET /viewdoc/file.php?document=[base64 string]
- carbnfuel[.]com - GET /viewdoc/file.php?document=[base64 string]
- CARBONFULE[.]COM - GET /viewdoc/file.php?document=[base64 string]
- CATALINETICS[.]COM - GET /viewdoc/file.php?document=[base64 string]
- cognistix[.]net - GET /viewdoc/file.php?document=[base64 string]
- H2S2[.]INFO - GET /viewdoc/file.php?document=[base64 string]
- systemsmith[.]com - GET /viewdoc/file.php?document=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENTS:
- Ringcentral_Fax__[six-digit number].doc
POST-INFECTION TRAFFIC FROM MY ONE INFECTED HOST:
- 137.74.150[.]55 port 80 - ranlingthetne[.]com - POST /ls5/forum.php
- 137.74.150[.]55 port 80 - ranlingthetne[.]com - POST /mlu/forum.php
- 137.74.150[.]55 port 80 - ranlingthetne[.]com - POST /d2/about.php
- 186.202.153[.]168 port 80 - www.prava[.]com[.]br - GET /wp-content/plugins/easy-captcha/1
- 186.202.153[.]168 port 80 - www.prava[.]com[.]br - GET /wp-content/plugins/easy-captcha/2
- 186.202.153[.]168 port 80 - www.prava[.]com[.]br - GET /wp-content/plugins/easy-captcha/3
- 91.121.198[.]229 port 80 - www.librodeapuntes[.]es - GET /wp-content/plugins/analytics_ga_plugin/2
- 91.121.198[.]229 port 80 - www.librodeapuntes[.]es - GET /wp-content/plugins/analytics_ga_plugin/3
- 91.201.214[.]170 port 80 - tounundhem[.]com - POST /bdl/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 0cb34a9c52755ec21ad7eda70aecb961b9751441df65f93a928bf48819c2f7ae
File name: Ringcentral_Fax_654608.doc
File size: 288,256 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 530e2d72776104e6f7b9ed23513ec1d33fb968697d665470b104f566ef30d33f
File location: C:\Users\[username]\AppData\Local\Temp\BNC3BB.tmp
File size: 188,416 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
