2017-06-29 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-29-Hancitor-infection-with-ZLoader.pcap.zip 8.8 MB (8,772,664 bytes)
- 2017-06-29-Hancitor-infection-with-ZLoader.pcap (9,399,867 bytes)
- 2017-06-29-Hancitor-malspam-6-examples.zip 9.3 kB (9,259 bytes)
- 2017-06-29-Hancitor-malspam-152244-UTC.eml (3,540 bytes)
- 2017-06-29-Hancitor-malspam-152359-UTC.eml (3,526 bytes)
- 2017-06-29-Hancitor-malspam-160017-UTC.eml (3,535 bytes)
- 2017-06-29-Hancitor-malspam-160354-UTC.eml (3,535 bytes)
- 2017-06-29-Hancitor-malspam-161741-UTC.eml (3,545 bytes)
- 2017-06-29-Hancitor-malspam-173356-UTC.eml (3,532 bytes)
- 2017-06-29-malware-from-Hancitor-infection.zip 245.6 kB (245,585 bytes)
- BN8B1F.tmp (209,920 bytes)
- Subpoena_yahoo.doc (194,048 bytes)
A BLOG POST AND SOME TWEETS COVERING THE 2017-06-29 WAVE OF #HANCITOR MALSPAM:
- @fletchsec: #hancitor run, Subject: You have received a new document!, Sender: james@consultechmgti[.]com Links and hancitor C2: (Ghostbin link) (link)
- @James_inthe_box: And #hancitor "You have received a new document!" (Ghostbin link / Threatcrowd.org link) (link)
- @cheapbyte: #hancitor #malspam #phishing Hancitor links, now include multiple malware delivery sites, txt at Ghostbin (link)
EMAILS
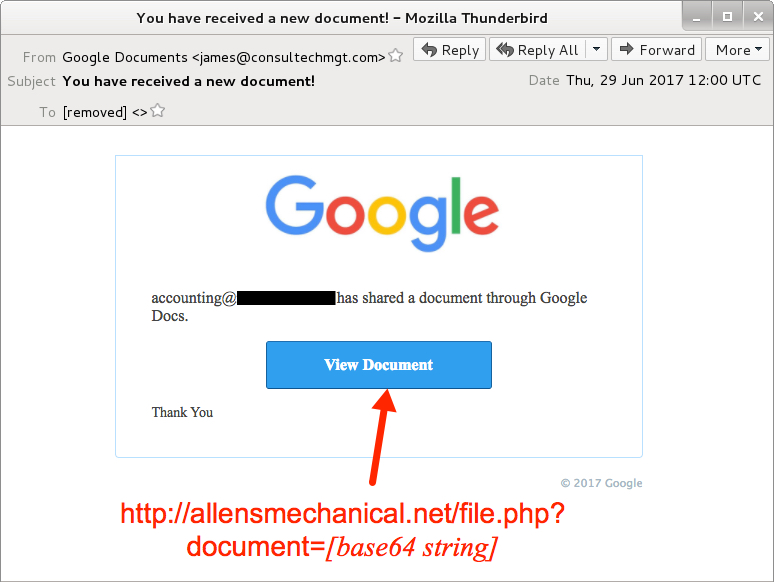
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date: Thursday 2017-06-29 as early as 15:22 UTC through at least 17:33 UTC
- From: "Google Documents" <james@consultechmgt[.]com>
- Subject: You have received a new document!
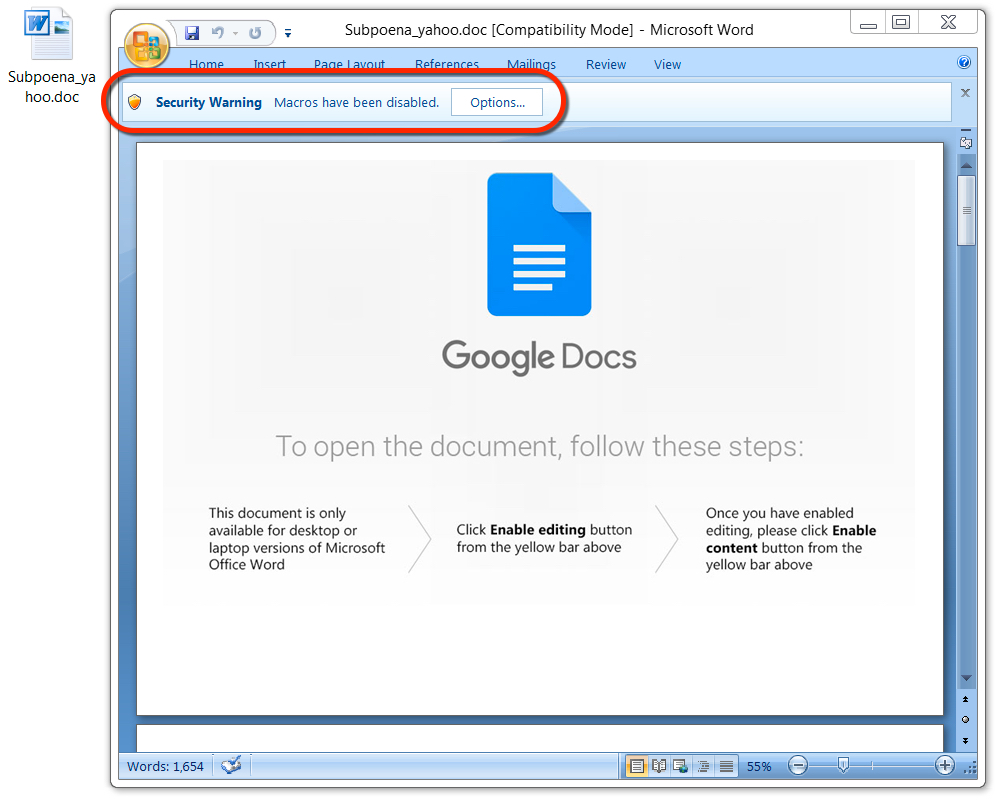
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
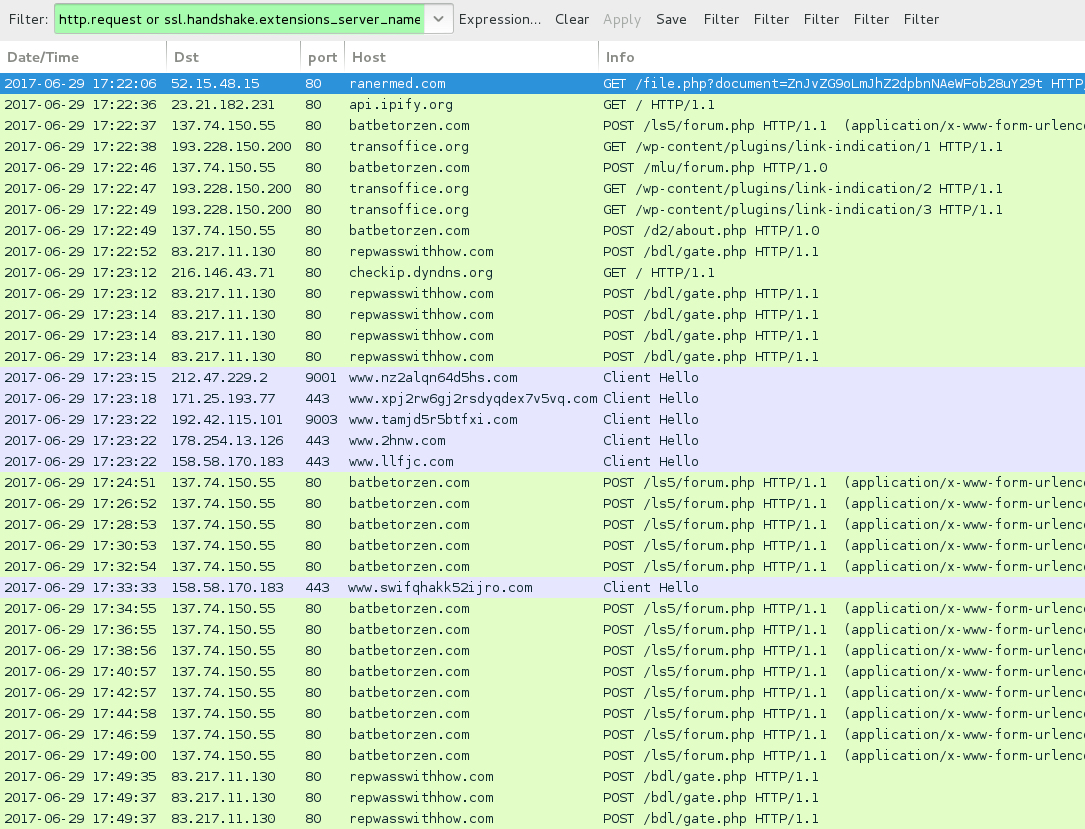
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUESTS FOR THE WORD DOCUMENT:
- ALLENSMECHANICAL[.]BIZ - GET /viewdoc/file.php?document=[base64 string]
- allensmechanical[.]net - GET /viewdoc/file.php?document=[base64 string]
- correspondentfunding[.]com - GET /viewdoc/file.php?document=[base64 string]
- FROGMAN-SCUBA[.]COM - GET /viewdoc/file.php?document=[base64 string]
- HAVEFUNMAKEMONEYHELPPEOPLE[.]COM - GET /viewdoc/file.php?document=[base64 string]
- ranermed[.]com - GET /viewdoc/file.php?document=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENTS:
- Subpoena_[recipient's email domain minus the suffix].doc
POST-INFECTION TRAFFIC FROM MY ONE INFECTED HOST:
- 137.74.150[.]55 port 80 - batbetorzen[.]com - POST /ls5/forum.php
- 137.74.150[.]55 port 80 - batbetorzen[.]com - POST /mlu/forum.php
- 137.74.150[.]55 port 80 - batbetorzen[.]com - POST /d2/about.php
- 193.228.150[.]200 port 80 - transoffice[.]org - GET /wp-content/plugins/ink-indication/1
- 193.228.150[.]200 port 80 - transoffice[.]org - GET /wp-content/plugins/ink-indication/2
- 193.228.150[.]200 port 80 - transoffice[.]org - GET /wp-content/plugins/ink-indication/3
- 83.217.11[.]130 port 80 - repwasswithhow[.]com - POST /bdl/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: f4f026fbe3df5ee8ed848bd844fffb72b63006cfa8d1f053a9f3ee4c271e9188
File name: Subpoena_yahoo.doc
File size: 194,048 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 8bf110d38b3084d065f975da641fd0ae2ae672f607e6c30cf5544699770dc905
File location: C:\Users\[username]\AppData\Local\Temp\BN8B1F.tmp.tmp
File size: 209,920 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
