2017-07-03 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-03-Hancitor-infection-with-ZLoader.pcap.zip 6.8 MB (6,767,169 bytes)
- 2017-07-03-Hancitor-infection-with-ZLoader.pcap (7,230,916 bytes)
- 2017-07-03-Hancitor-malspam-9-examples.zip 27.5 kB (27,458 bytes)
- 2017-07-03-Hancitor-malspam-142247-UTC.eml (21,614 bytes)
- 2017-07-03-Hancitor-malspam-142410-UTC.eml (21,625 bytes)
- 2017-07-03-Hancitor-malspam-143011-UTC.eml (21,625 bytes)
- 2017-07-03-Hancitor-malspam-143130-UTC.eml (21,619 bytes)
- 2017-07-03-Hancitor-malspam-143511-UTC.eml (21,627 bytes)
- 2017-07-03-Hancitor-malspam-150706-UTC.eml (21,617 bytes)
- 2017-07-03-Hancitor-malspam-151836-UTC.eml (21,625 bytes)
- 2017-07-03-Hancitor-malspam-160604-UTC.eml (21,629 bytes)
- 2017-07-03-Hancitor-malspam-162538-UTC.eml (21,633 bytes)
- 2017-07-03-malware-from-Hancitor-infection.zip 312.2 kB (312,299 bytes)
- BN2AE6.tmp (197,120 bytes)
- Invoice_yahoo.doc (359,936 bytes)
SOME TWEETS COVERING THE 2017-07-03 WAVE OF #HANCITOR MALSPAM:
- @James_inthe_box: And #hancitor run with mod'd link structure: "FedEx Tracking <digits> Notification" (Ghostbin link) (link)
- @cheapbyte: And #hancitor #phishing #malspam Hancitor July 3, 2017 links and SHA (Ghostbin link) Check the malware download 1,2,3 (link)
EMAILS
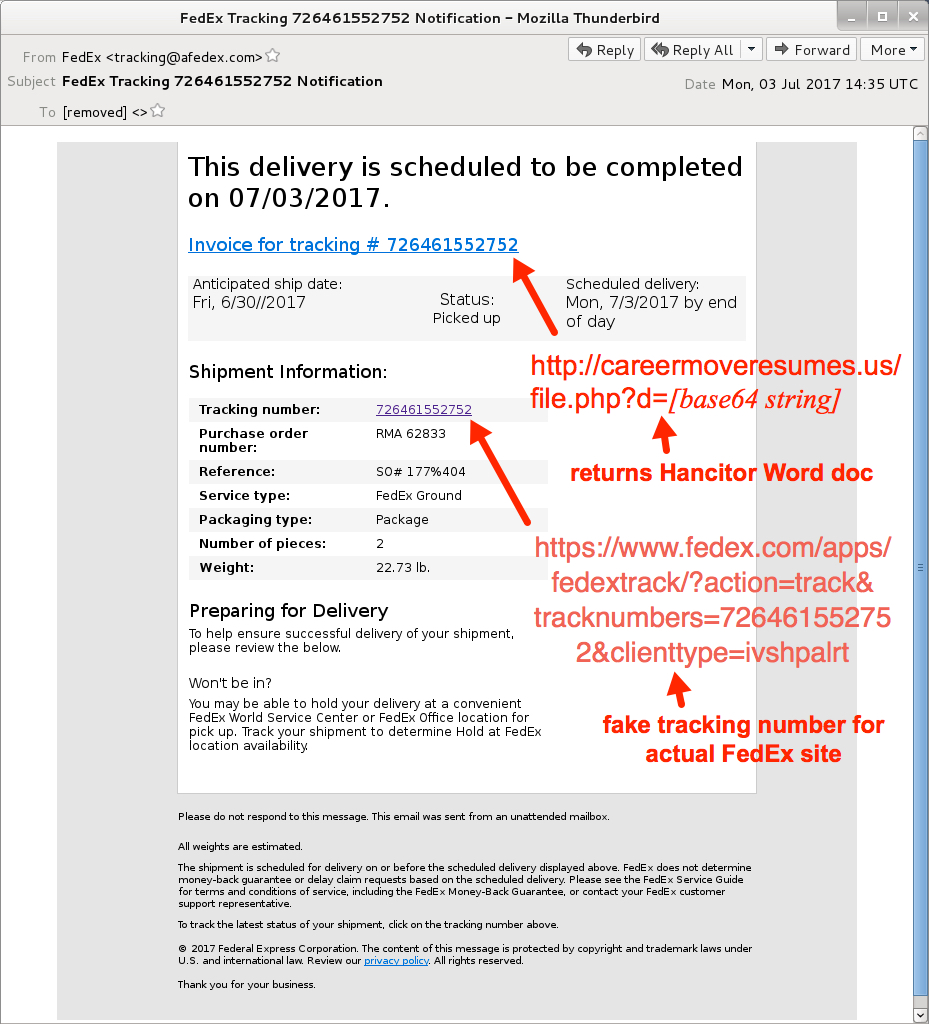
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date: Monday 2017-07-03 as early as 14:22 UTC through at least 16:25 UTC
- From: "FedEx" <tracking@afedex[.]com>
- Subject: FedEx Tracking 715715163815 Notification
- Subject: FedEx Tracking 716387320236 Notification
- Subject: FedEx Tracking 720158312704 Notification
- Subject: FedEx Tracking 723824805710 Notification
- Subject: FedEx Tracking 725323300358 Notification
- Subject: FedEx Tracking 726461552752 Notification
- Subject: FedEx Tracking 758633840738 Notification
- Subject: FedEx Tracking 764042320736 Notification
- Subject: FedEx Tracking 778208545774 Notification
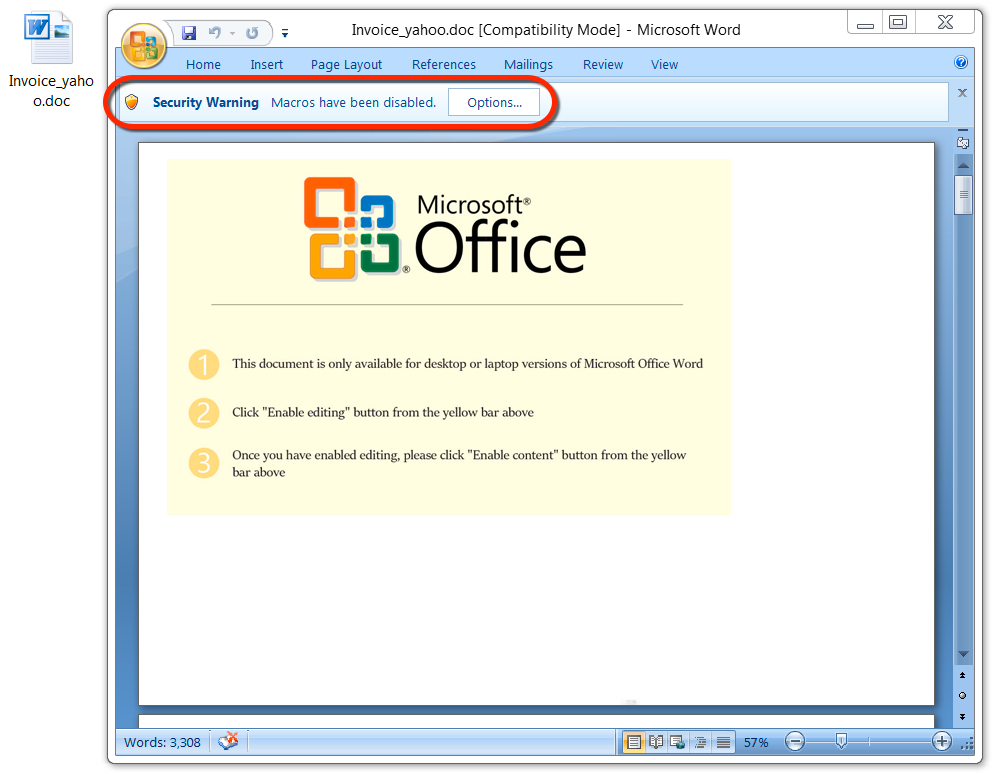
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
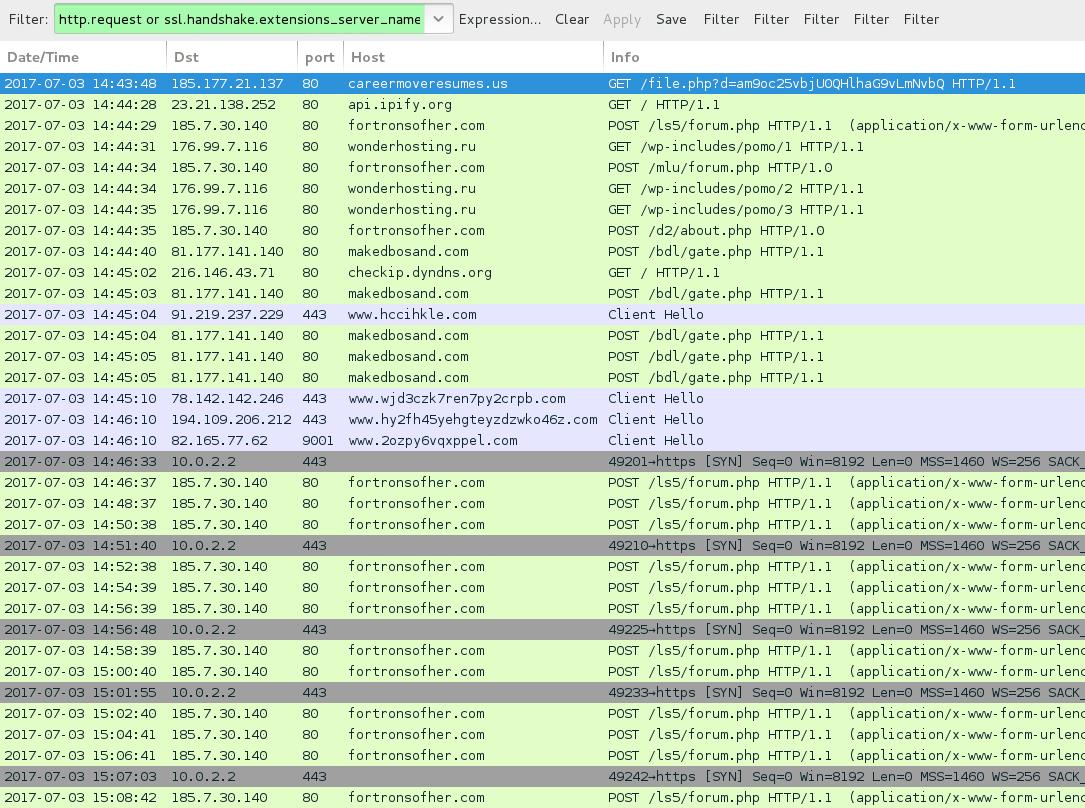
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUESTS FOR THE WORD DOCUMENT:
- auburnmachine[.]com - GET /viewdoc/file.php?d=[base64 string]
- careermoveresumes[.]us - GET /viewdoc/file.php?d=[base64 string]
- GPAC[.]BIZ - GET /viewdoc/file.php?d=[base64 string]
- GPAC-LLC[.]COM - GET /viewdoc/file.php?d=[base64 string]
- GPAC-LLC[.]NET - GET /viewdoc/file.php?d=[base64 string]
- rz-restaurants[.]com - GET /viewdoc/file.php?d=[base64 string]
- tucsonweddingexpo[.]com - GET /viewdoc/file.php?d=[base64 string]
- WOMENSLIFEANDSTYLEEXPO[.]COM - GET /viewdoc/file.php?d=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENTS:
- Invoice_[recipient's email domain minus the suffix].doc
POST-INFECTION TRAFFIC FROM MY ONE INFECTED HOST:
- 185.7.30[.]140 port 80 - fortronsofher[.]com - POST /ls5/forum.php
- 185.7.30[.]140 port 80 - fortronsofher[.]com - POST /mlu/forum.php
- 185.7.30[.]140 port 80 - fortronsofher[.]com - POST /d2/about.php
- 176.99.7[.]116 port 80 - wonderhosting[.]ru - GET /wp-includes/pomo/1
- 176.99.7[.]116 port 80 - wonderhosting[.]ru - GET /wp-includes/pomo/2
- 176.99.7[.]116 port 80 - wonderhosting[.]ru - GET /wp-includes/pomo/3
- 81.177.141[.]140 port 80 - makedbosand[.]com - POST /bdl/gate.php
- 10.0.2.2 port 443 - TCP SYN segment approx once avery 5 minutes
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 5e23a6cb91e82f61d683620c9bdef57241b66e73c3f7a67260e20762bc7a1162
File name: Invoice_yahoo.doc
File size: 359,936 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: cb0714a8342a5092d8c83a5a736dc19b04d8e20d87e6d83f520f9e57882db38b
File location: C:\Users\[username]\AppData\Local\Temp\BN2AE6.tmp
File size: 197,120 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
