2017-07-05 - MALWARE INFECTION FROM JAPANESE MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-05-malware-infection-from-Japanese-malspam.pcap.zip 207 kB (207,244 bytes)
- 2017-07-05-malware-infection-from-Japanese-malspam.pcap (315,863 bytes)
- 2017-07-05-Japanese-emails-and-malware.zip 413.4 kB (413,472 bytes)
- 2017-07-05-Japanese-malspam-0612-UTC.eml (108,941 bytes)
- 2017-07-05-Japanese-malspam-0622-UTC.eml (109,035 bytes)
- 2017-07-05-Japanese-malspam-0633-UTC.eml (108,996 bytes)
- 2017-07-05-Japanese-malspam-0654-UTC.eml (108,945 bytes)
- 2017-07-05-Japanese-malspam-0657-UTC.eml (109,054 bytes)
- 2017-07-05-Japanese-malspam-0722-UTC.eml (108,955 bytes)
- 2017-07-05-Japanese-malspam-0728-UTC.eml (108,908 bytes)
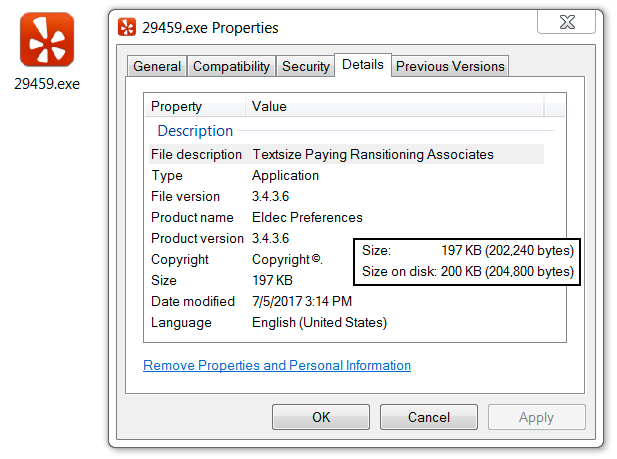
- 29459.exe (202,240 bytes)
- 7428086_2017.xls (79,872 bytes)
RELATED TWEET:
- From @tmmalanalyst - Jul-05,2017(JST) evening. MalSpam attached xls. XLS open download malware. It's considered to be #URLZone? #Bebloh? (VT link) - (link to tweet)
EMAILS
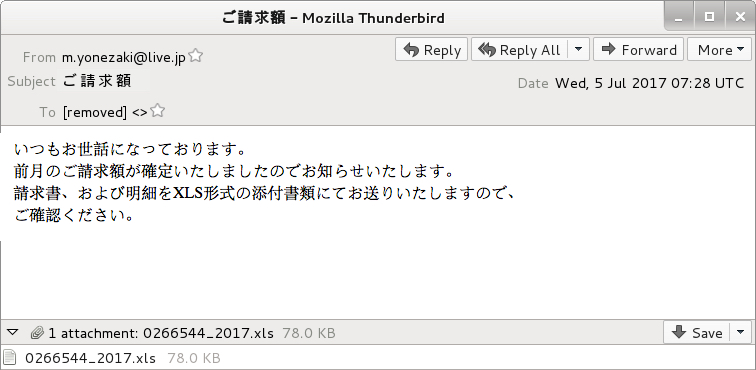
Shown above: Screenshot from one of the emails.
EMAILS GATHERED:
(Read: Date/Time -- Sending address (spoofed) -- Subject -- Attachment name)
- 2017-07-05 06:12 UTC -- cr045@ybb[.]ne[.]jp -- ご請求額 -- 0017857_2017.xls
- 2017-07-05 06:33 UTC -- okaere3@f2.dion[.]ne[.]jp -- ご請求額 -- 1794411_2017.xls
- 2017-07-05 06:54 UTC -- h_sakamoto@sepia.ocn[.]ne[.]jp -- ご請求額 -- 7038863_2017.xls
- 2017-07-05 06:57 UTC -- nakamura-masahiko@kbh.biglobe[.]ne[.]jp -- ご請求額 -- 1159287_2017.xls
- 2017-07-05 07:22 UTC -- ayanoshiotani@kfa.biglobe[.]ne[.]jp -- ご請求額 -- 5174352_2017.xls
- 2017-07-05 07:28 UTC -- m.yonezaki@live[.]jp -- ご請求額 -- 0266544_2017.xls
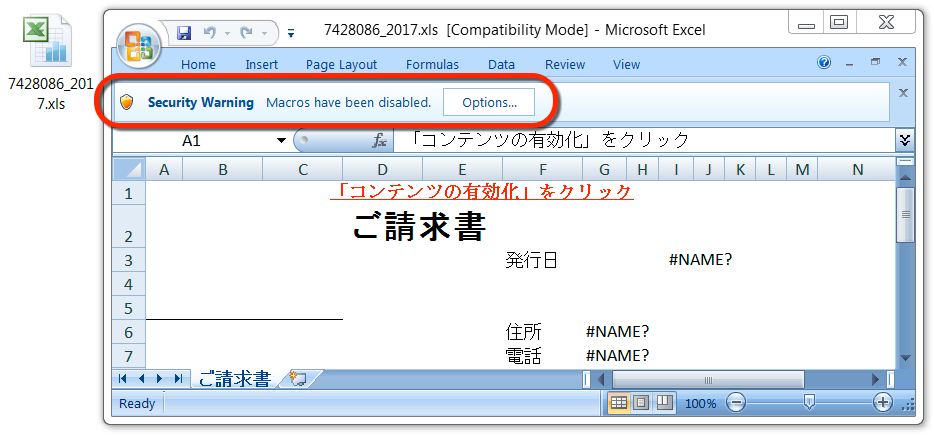
Shown above: One of the Excel spreadsheets.
TRAFFIC
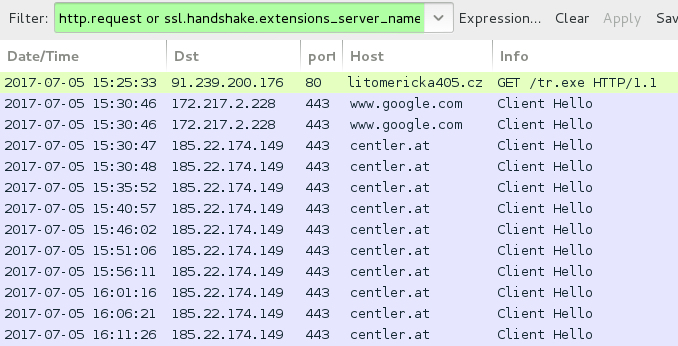
Shown above: Traffic from an infection filtered in Wireshark.
POST-INFECTION TRAFFIC:
- 91.239.200[.]176 port 80 - liomericka504[.]cz - GET /tr.exe - URL to retrieve follow-up binary after enabling macros in .xls file
- 46.183.166[.]84 port 80 - bifoop[.]com - GET /oko.exe - alternate URL to retrieve follow-up binary
- www.google[.]com - post-infection connectivity check
- 185.22.174[.]149 port 443 - centler[.]at - HTTPS/SSL/TLS post-infection traffic
FILE HASHES
EMAIL ATTACHMENT:
- SHA256 hash: a2602b9c94a2bdbcac75b95d4430d4cda3a79986c016ac2ef2211afb00420f24
File name: 1234567_2017.xls [7 random digits before _2017.xls]
File size: 79,872 bytes
FOLLOW-UP MALWARE:
- SHA256 hash: a7d74a1baab262eb697cd8b8c812a459b6e4265f73fa74f4c657e8d4482db7f8
File location: C:\Users\[username]\Roaming\29459.exe [random digits before .exe]
File size: 202,240 bytes
Shown above: Binary downloaded by .xls attachment.
Click here to return to the main page.