2017-07-12 - INFOSTEALER INFECTION FROM BRAZIL MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-12-Infostealer-infection-from-Brazil-malspam.pcap.zip 7.4 MB (7,411,699 bytes)
- 2017-07-12-Infostealer-infection-from-Brazil-malspam.pcap (7,857,287 bytes)
- 2017-07-12-Brazil-Boleto-malspam-and-associated-malware-and-artifacts.zip 5.6 MB (5,574,281 bytes)
- 2017-07-12-Boleto-malspam-1555-UTC.eml (681 bytes)
- HInteW.exe (1,011,200 bytes)
- Imprimir_Via2.com (2,990,080 bytes)
- Imprimir_Via2.zip (1,077,419 bytes)
- Struct.dll (5,004,288 bytes)
- hP0EFY6CTgqU60MWLaSZFQ.png (35,932 bytes)
- oct.dll (21 bytes)
- readme.txt (613 bytes)
EMAIL HEADER INFO:
- Date: Wednesday 2017-07-12 at 15:55 UTC
- From: Adrianna Financeiro
- Subject: Ultimo aviso da 2a via boleto em Atraso
- Google translation of subject: Last notice of the 2nd via ticket in arrears
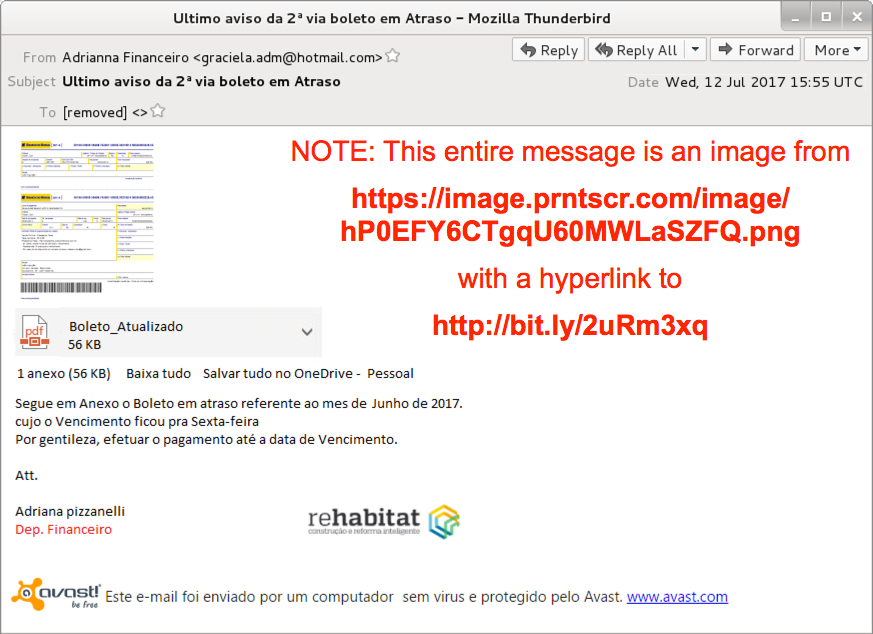
Shown above: Screenshot from the email.
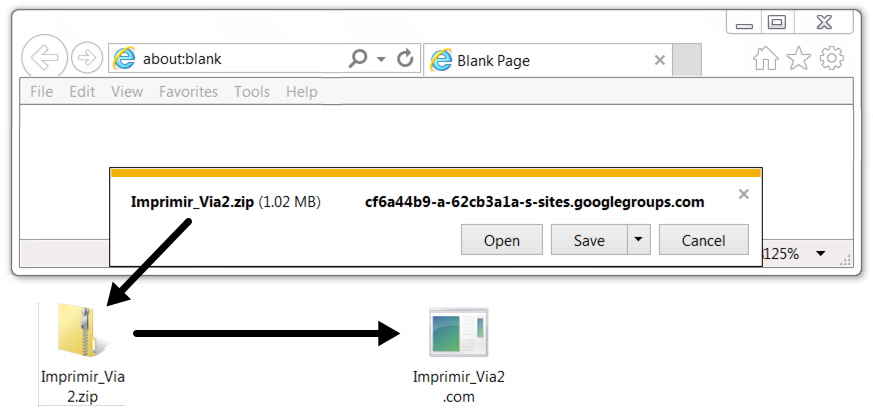
Shown above: Malicious zip archive and extracted binary after clicking link from the malspam.
TRAFFIC
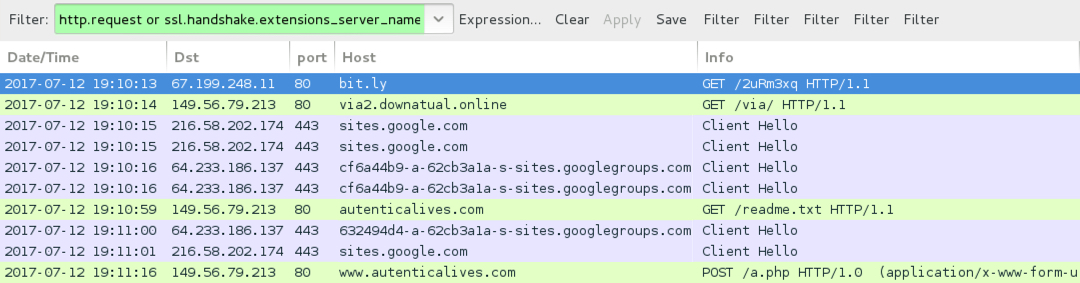
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS:
- port 80 (HTTP) - bit[.]ly - GET /2uRm3xq
- 149.56.79.213 port 80 - via2.downatual[.]online - GET /via/
- port 443 (HTTPS) - sites.google[.]com - GET /site/viaboletosxxx/Imprimir_Via2.zip?attredirects=0&d=1
- port 443 (HTTPS) - cf6a44b9-a-62cb3a1a-s-sites.googlegroups[.]com - GET /site/viaboletosxxx/Imprimir_Via2.zip?attachauth=[long string]
- 149.56.79[.]213 port 80 - autenticalives[.]com - GET /readme.txt
- port 443 (HTTPS) - 632494d4-a-62cb3a1a-s-sites.googlegroups[.]com - GET /site/texasturser/1.png?attachauth=[long string]
- port 443 (HTTPS) - 632494d4-a-62cb3a1a-s-sites.googlegroups[.]com - GET /site/texasturser/f.png?attachauth=[long string]
- 149.56.79[.]213 port 80 - www.autenticalives[.]com - POST /a.php
FILE HASHES
ZIP ARCHIVE AFTER CLICKING LINK FROM THE EMAIL:
- SHA256 hash: ac8c40cfe6a75eba981e39cd6f2d9176be6df2f785e9a746b1d6cf99ef91b7c2
File name: Imprimir_Via2.zip
File size: 1,077,419 bytes
EXTRACTED BINARY FROM ZIP ARCHIVE:
- SHA256 hash: 616026d9bbd86d5672cfd1c664b6eb526bd79a3a3be719f9e54ac77041840e6f
File name: Imprimir_Via2.com
File size: 2,990,080 bytes
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: b14dab1d50ed578ca75c3f352de5fc5a943514b2757aca2640c122097248339b
File location: C:\Users\[username]\AppData\HInteW.exe
File size: 1,011,200 bytes
- SHA256 hash: 100194e632ce71835bcbb48ed63ab422b3b2ae889239a0afb59b12327de578e9
File location: C:\Users\[username]\AppData\Struct.dll
File size: 5,004,288 bytes
IMAGES
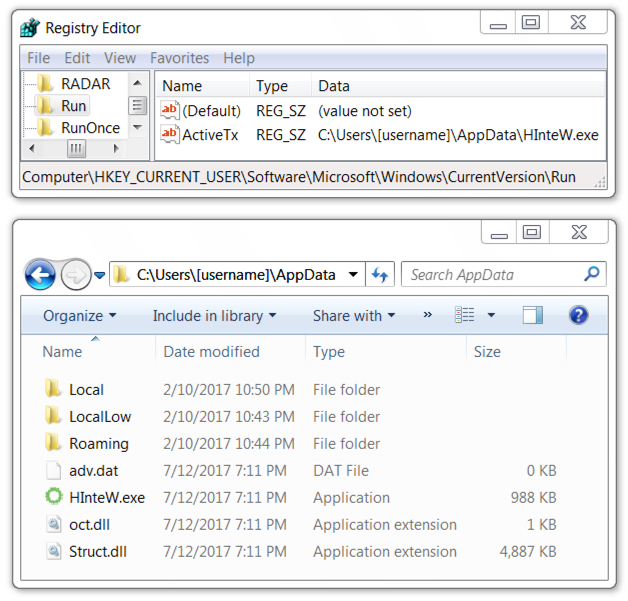
Shown above: Artifacts left on the infected host.
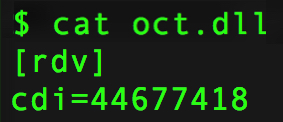
Shown above: oct.dll is a very small text file.
Click here to return to the main page.
