2017-07-14 - ANOTHER TECH SUPPORT SCAM POPUP MESSAGE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-14-tech-support-scam-traffic.pcap.zip 617.6 kB (617,604 bytes)
- 2017-07-14-tech-support-scam-traffic.pcap (728,331 bytes)
- 2017-07-14-tech-support-scam-artifacts.zip 199.9 kB (199,918 bytes)
- 2017-07-14-audio-message-from-df-th-37.s3.amazonaws_com.mp3 (143,728 bytes)
- 2017-07-14-fake-microsoft-site-from-df-th-37.s3.amazonaws_com-index.txt (127,069 bytes)
- 2017-07-14-jquery.js-from-134.249.116_78.txt (2,698 bytes)
IMAGES
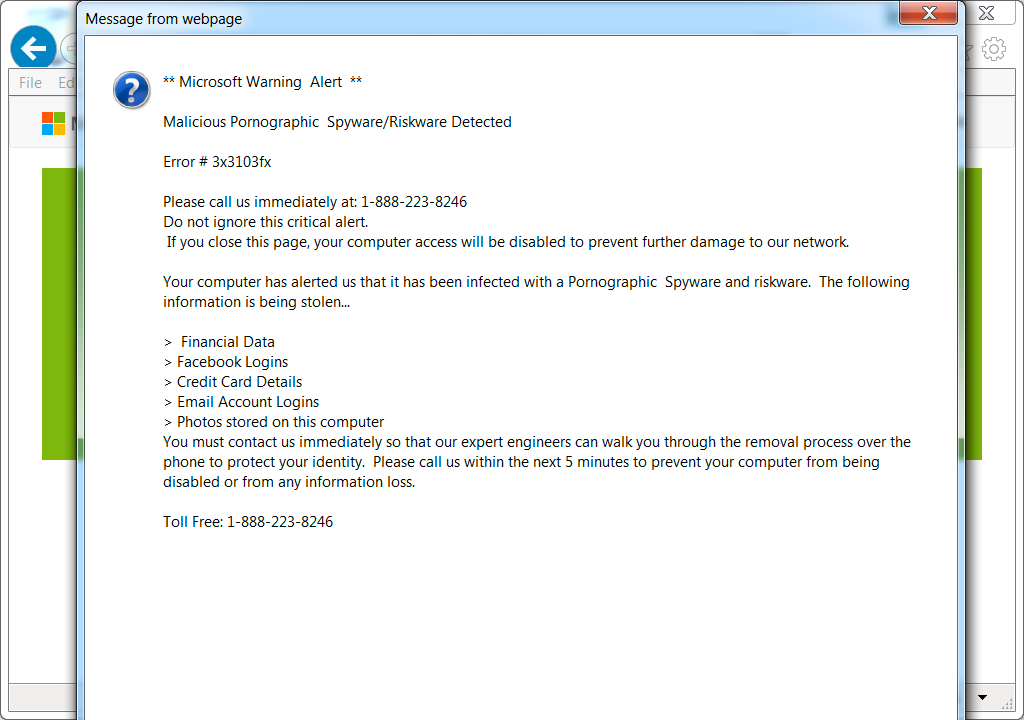
Shown above: Popup seen after trying to view the compromised website.

Shown above: Web page behind the popup.
TRAFFIC
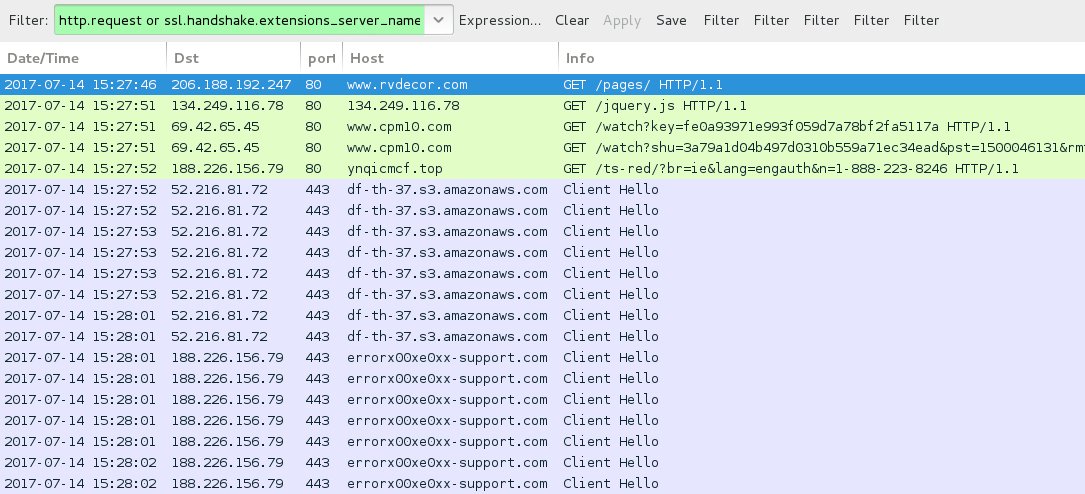
Shown above: Traffic from this activity, filtered in Wireshark.
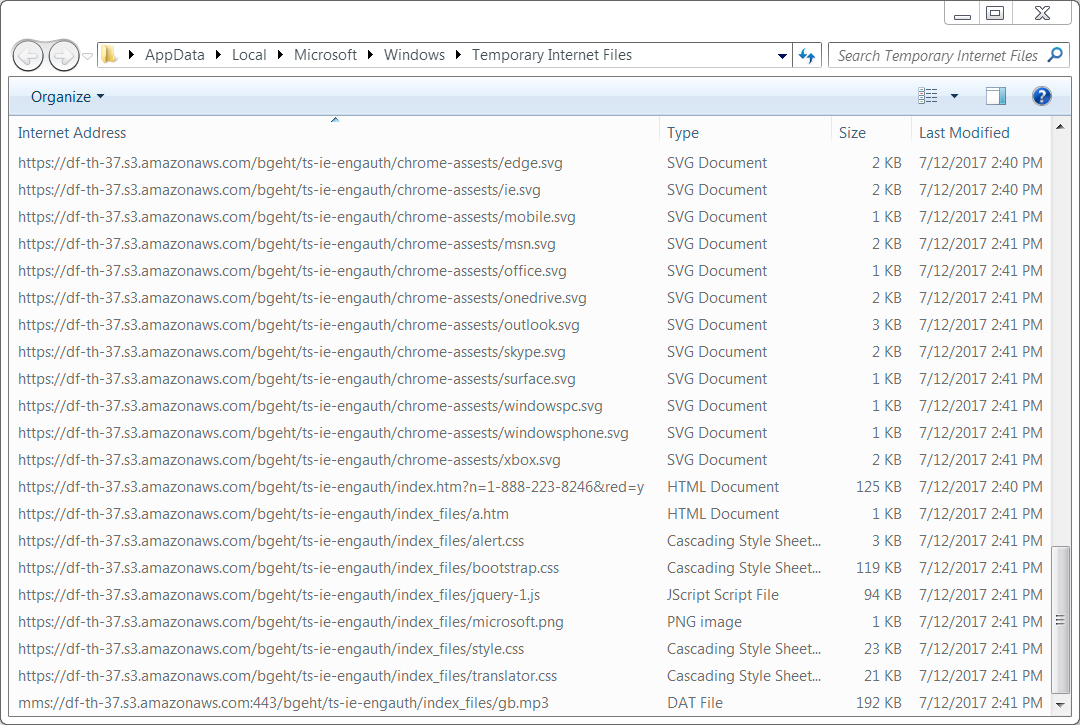
Shown above: HTTPS urls from the Internet Explorer cache.
ASSOCIATED DOMAINS AND URLS:
- 206.188.192[.]247 port 80 - www.rvdecor[.]com - GET /pages/ [legitimate site that kicks off this chain of events]
- 134.249.116[.]78 port 80 - 134.249.116[.]78 - GET /jquery.js
- 69.42.65[.]45 port 80 - www.cpm10[.]com - GET /watch?key=fe0a93971e993f059d7a78bf2fa5117a
- 69.42.65[.]45 port 80 - www.cpm10[.]com - GET /watch?shu=[long string of characters]
- 188.226.156[.]79 port 80 - ynqicmcf[.]top - GET /ts-red/?br=ie&lang=engauth&n=1-888-223-8246
- 52.216.81[.]72 port 443 - df-th-37.s3.amazonaws[.]com - GET /ts-ie-engauth/index.htm?n=1-888-223-8246&red=y [HTTPS]
- 188.226.156[.]79 port 443 - errorx00xe0xx-support[.]com - HTTPS/SSL/TLS traffic
Click here to return to the main page.
