2017-07-17 - RIG EK DATA DUMP (HOOKADS AND SEAMLESS CAMPAIGNS)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-17-Rig-EK-data-dump-6-pcaps.zip 10.2 MB (10,179,016 bytes)
- 2017-07-17-1st-run-HookAds-Rig-EK-sends-Dreambot.pcap (348,094 bytes)
- 2017-07-17-2nd-run-HookAds-Rig-EK-sends-Dreambot-with-post-infection-traffic.pcap (6,668,017 bytes)
- 2017-07-17-3rd-run-HookAds-Rig-EK-sends-Dreambot.pcap (390,804 bytes)
- 2017-07-17-4th-run-Seamless-Rig-EK-sends-Ramnit-with-post-infection-traffic.pcap (2,002,338 bytes)
- 2017-07-17-5th-run-Seamless-Rig-EK-sends-Ramnit-with-post-infection-traffic.pcap (1,794,866 bytes)
- 2017-07-17-6th-run-HookAds-Rig-EK-sends-Dreambot.pcap (562,903 bytes)
- 2017-07-17-Rig-EK-data-dump-artifacts-and-malware.zip 1.6 MB (1,597,114 bytes)
- 2017-07-17-1st-run-HookAds-Rig-EK-payload-Dreambot.exe (232,448 bytes)
- 2017-07-17-1st-run-HookAds-gate-at-experimea_info-countryhits.txt (6,429 bytes)
- 2017-07-17-1st-run-Rig-EK-landing-page.txt (122,643 bytes)
- 2017-07-17-1st-run-popunder.php.txt (1,255 bytes)
- 2017-07-17-2nd-run-HookAds-Rig-EK-payload-Dreambot.exe (231,936 bytes)
- 2017-07-17-2nd-run-HookAds-gate-at-experimea_info-countryhits.txt (6,429 bytes)
- 2017-07-17-2nd-run-Rig-EK-landing-page.txt (61,820 bytes)
- 2017-07-17-2nd-run-popunder.php.txt (1,255 bytes)
- 2017-07-17-3rd-run-HookAds-Rig-EK-payload-Dreambot.exe (310,272 bytes)
- 2017-07-17-3rd-run-HookAds-gate-at-experimea_info-countryhits.txt (6,501 bytes)
- 2017-07-17-3rd-run-Rig-EK-landing-page.txt (61,802 bytes)
- 2017-07-17-3rd-run-popunder.php.txt (1,255 bytes)
- 2017-07-17-4th-run-Rig-EK-landing-page.txt (61,741 bytes)
- 2017-07-17-4th-run-Seamless-Rig-EK-payload-Ramnit.exe (241,664 bytes)
- 2017-07-17-5th-run-Rig-EK-landing-page.txt (122,525 bytes)
- 2017-07-17-5th-run-Seamless-Rig-EK-payload-Ramnit.exe (230,400 bytes)
- 2017-07-17-6th-run-HookAds-Rig-EK-payload-Dreambot.exe (219,136 bytes)
- 2017-07-17-6th-run-HookAds-gate-at-experimea_info-countryhits.txt (6,504 bytes)
- 2017-07-17-6th-run-Rig-EK-landing-page.txt (122,450 bytes)
- 2017-07-17-6th-run-popunder.php.txt (1,255 bytes)
- 2017-07-17-Ramnit-post-infection-binary-from-steelskull_com-AU2_EXEsd.exe (509,952 bytes)
- 2017-07-17-Ramnit-post-infection-binary-from-steelskull_com-satbin.exe (173,056 bytes)
- 2017-07-17-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-07-17-Rig-EK-flash-exploit.swf (15,472 bytes)
ASSOCIATED FILES:
- Yesterday, @VK_Intel tweeted about a change in Rig EK URL patterns, noting base64 strings used in the HTTP GET requests (link).
- I did data dump in case anyone needs a few examples of the new URL patterns.
- Apart from the URL patterns, this is basically more of the same garbage we've seen from Rig EK in the past 2 to 3 months.
Rig EK: New URL patterns, same garbage.
TRAFFIC
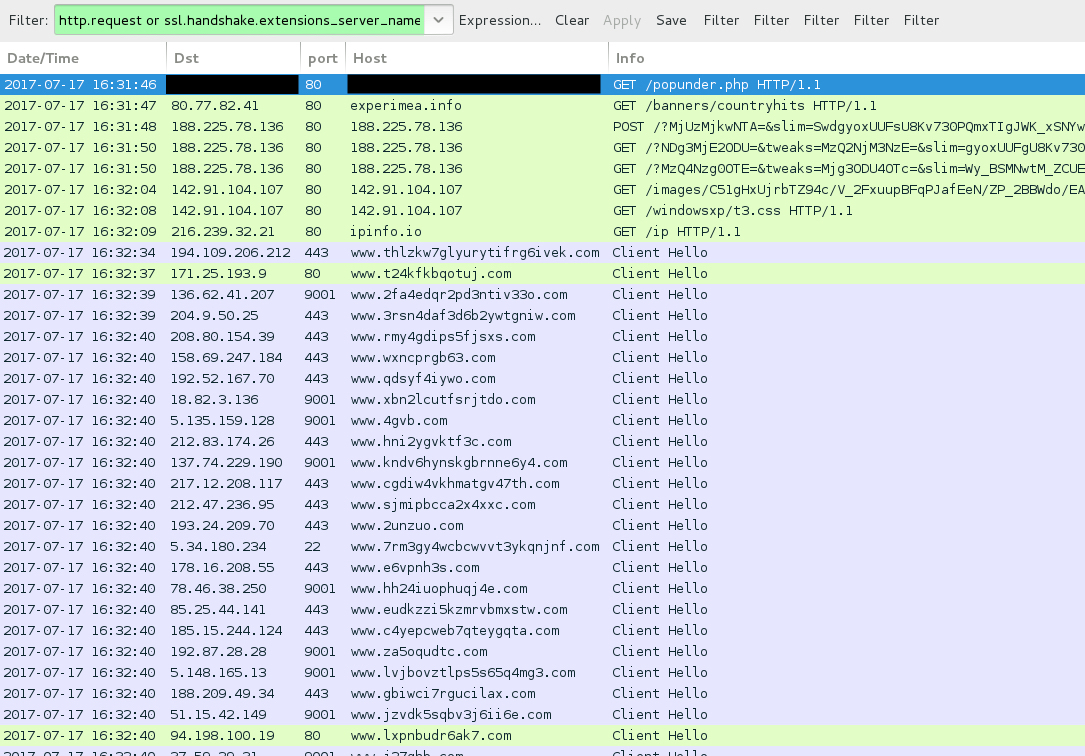
Shown above: Traffic from one of the HookAds Rig EK pcaps, filtered in Wireshark.
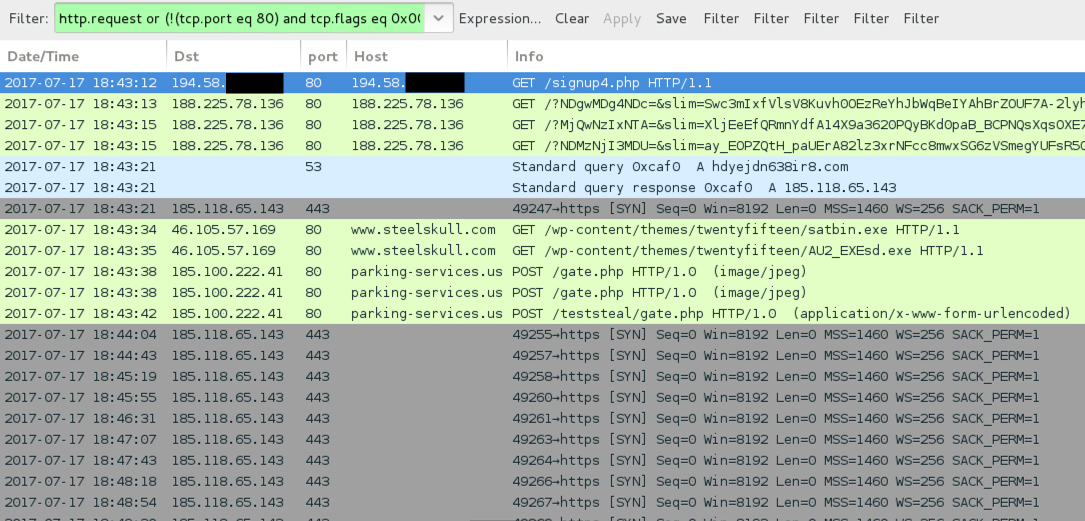
Shown above: Traffic from one of the Seamless Rig EK pcaps, filtered in Wireshark.
ASSOCIATED DOMAINS FOR HOOKADS CAMPAIGN USING RIG EK TO DELIVER DREAMBOT:
- [recacted] port 80 - [recacted] - GET /popunder.php
- 80.77.82[.]41 port 80 - experimea[.]info - GET /banners/countryhits
- 188.225.78[.]136 port 80 - 188.225.78[.]136 - Rig EK (first few times)
- 185.159.128[.]207 port 80 - 185.159.128[.]207 - Rig EK (last time)
- 142.91.104[.]107 port 80 - 142.91.104[.]107 - GET /images/[long string of characters]/.avi
- 142.91.104[.]107 port 80 - 142.91.104[.]107 - GET /windowsxp/t3.css
- ipinfo[.]io - GET /ip
- various IP addresses - various ports - Tor traffic
ASSOCIATED DOMAINS FOR SEAMLESS CAMPAIGN USING RIG EK TO DELIVER RAMNIT:
- An IP in the range 194.58.0[.]0/16 port 80 - 194.58.??.?? - GET /signup4.php
- 188.225.78[.]136 port 80 - 188.225.78[.]136 - Rig EK (first time)
- 185.159.128[.]207 port 80 - 185.159.128[.]207 - Rig EK (second time)
- google[.]com - Connectivity check - DNS queries and TCP connections, but no HTTP or HTTPS traffic
- 46.105.57[.]169 port 80 - www.steelskull[.]com - GET /wp-content/themes/twentyfifteen/satbin.exe
- 46.105.57[.]169 port 80 - www.steelskull[.]com - GET /wp-content/themes/twentyfifteen/AU2_EXEsd.exe
- 185.100.222[.]41 port 80 - parking-services[.]us - POST /gate.php
- api.ipify[.]org - Connectivity/IP address check over HTTPS/SSL/TLS
- 185.100.222[.]41 port 80 - parking-services[.]us - POST /teststeal/gate.php
- 185.118.65[.]143 port 443 - hdyejdn638ir8[.]com - Ramnit post-infection traffic
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 644b6905a1a1b35620c5dd44bfd30e039bbeaa54799853b4b93ee7ee51bbbe0e
File size: 15,472 bytes
File description: Rig EK flash exploit seen on 2017-07-17
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 8c9566ff0ab6df29f5d879e26d294e5836e3741b269a644ce497440a5e380164 - Dreambot (1st run)
- SHA256 hash: 8bc2a1f203d87c731d036130c419ae6c7ad85eca159fe9c0effa32e5f97514ad - Dreambot (2nd run)
- SHA256 hash: db6c76521f9adfbadd0f8bb54277d81fa784025dc9e0250d50e92f4742f0b669 - Dreambot (3rd run)
- SHA256 hash: 515739205714a47c92e117342abdb1a7afa16747816a935bcb7b4a9ce7405401 - Ramnit (4th run)
- SHA256 hash: 16aa9721fc22325227e041a7bc7a6a32b7523dc986c20a0f62513abe7261a8d9 - Ramnit (5th run)
- SHA256 hash: 46a6356f31fc40cf9d5adc5ded0d56fc595b13154045b11e86882b5fbf62aa5d - Dreambot (6th run)
- SHA256 hash: cf3459cf29125101f5bea3f4206d8e43dbe097dd884ebf3155c49b276736f727 - Post-infection binary after Ramint infection (1st of 2 files)
- SHA256 hash: ec01ef73e22bb706baa87f994397d827b0cfeae0cc6bb8e9d5785e8171ed785c - Post-infection binary after Ramint infection (2nd of 2 files)
Click here to return to the main page.

