2017-07-20 - HANCITOR INFECTION WITH ZLOADER
ASSOCIATED FILES:
- 2017-07-20-Hancitor-infection-with-ZLoader.pcap.zip 7.9 MB (7,909,536 bytes)
- 2017-07-20-Hancitor-infection-with-ZLoader.pcap (8,654,555 bytes)
- 2017-07-20-Hancitor-malspam-8-examples.zip 16.0 kB (15,995 bytes)
- 2017-07-20-Hancitor-malspam-1456-UTC.eml (5,787 bytes)
- 2017-07-20-Hancitor-malspam-1531-UTC.eml (5,793 bytes)
- 2017-07-20-Hancitor-malspam-1547-UTC.eml (5,782 bytes)
- 2017-07-20-Hancitor-malspam-1609-UTC.eml (5,787 bytes)
- 2017-07-20-Hancitor-malspam-1650-UTC.eml (5,786 bytes)
- 2017-07-20-Hancitor-malspam-1714-UTC.eml (5,783 bytes)
- 2017-07-20-Hancitor-malspam-1817-UTC.eml (5,792 bytes)
- 2017-07-20-Hancitor-malspam-1852-UTC.eml (5,787 bytes)
- 2017-07-20-malware-from-Hancitor-infection.zip 290.6 kB (290,614 bytes)
- BN9A1C.tmp (194,048 bytes)
- Intuit_Invoice_649272.doc (296,960 bytes)
TWEETS COVERING THE 2017-07-20 WAVE OF #HANCITOR MALSPAM:
- @cheapbyte: And #hancitor #malspam #phishing Hancitor IOC July 20, 2017 Fake QUickbooks email. URLs via Ghostbin (link)
EMAILS
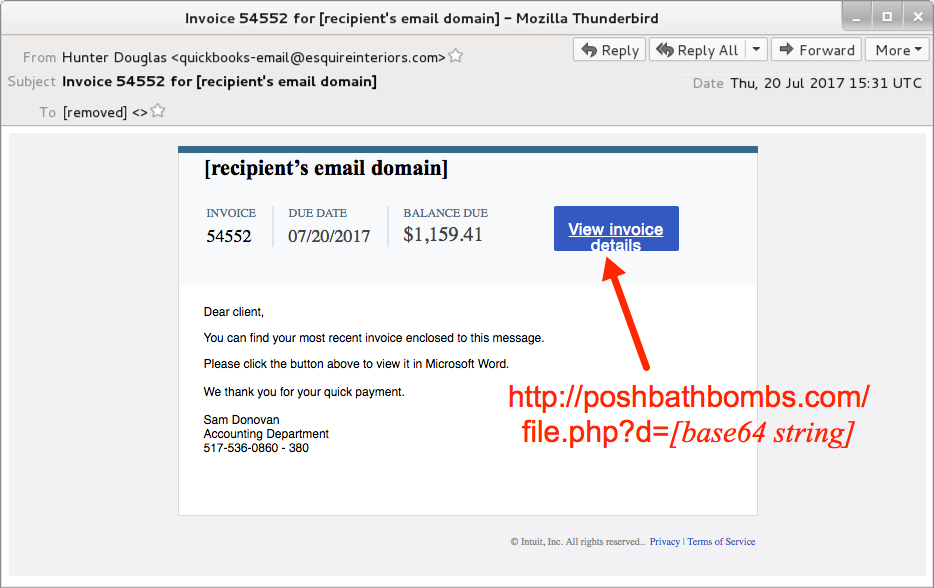
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date: Thursday 2017-07-20 as early as 14:56 UTC through at least 18:52 UTC
- From: "Hunter Douglas" <quickbooks-email@esquireinteriors[.]com>
- Subject: Invoice 13800 for [recipient's email domain]
- Subject: Invoice 31138 for [recipient's email domain]
- Subject: Invoice 40341 for [recipient's email domain]
- Subject: Invoice 47474 for [recipient's email domain]
- Subject: Invoice 54552 for [recipient's email domain]
- Subject: Invoice 74716 for [recipient's email domain]
- Subject: Invoice 83618 for [recipient's email domain]

Shown above: Malicious Word document from link in the malspam.
TRAFFIC
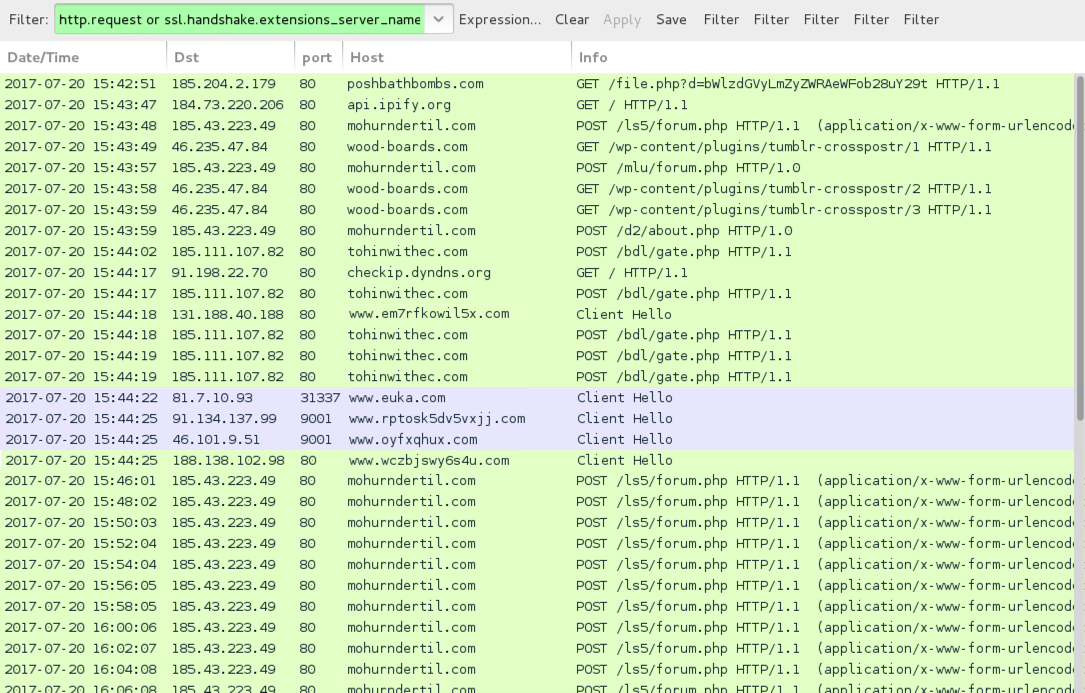
Shown above: Traffic from the infection filtered in Wireshark.
LINKS IN THE EMAILS THE WORD DOCUMENT THAT I SAW:
- bestbrokerageever[.]com - GET /file.php?d=[base64 string]
- bestbrokerever[.]net - GET /file.php?d=[base64 string]
- bestbrokerever[.]org - GET /file.php?d=[base64 string]
- poshbathbombs[.]com - GET /file.php?d=[base64 string]
- poshbathbombs[.]net - GET /file.php?d=[base64 string]
- YOURSTRATEGICGUIDE[.]NET - GET /file.php?d=[base64 string]
ADDITIONAL LINKS FOR THE WORD DOCUMENT REPORTED BY @CHEAPBYTE:
- bestbrokerever[.]info - GET /file.php?d=[base64 string]
- byobfranchise[.]com - GET /file.php?d=[base64 string]
- hutsonrental[.]com - GET /file.php?d=[base64 string]
- poshbathbomb[.]net - GET /file.php?d=[base64 string]
- yourstrategicguide[.]info - GET /file.php?d=[base64 string]
- yourstrategicguide[.]org - GET /file.php?d=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENT:
- Intuit_Invoice_[six random digits].doc
POST-INFECTION TRAFFIC FROM MY INFECTED HOST:
- 185.43.223[.]49 port 80 - mohurndertil[.]com - POST /ls5/forum.php
- 185.43.223[.]49 port 80 - mohurndertil[.]com - POST /mlu/forum.php
- 185.43.223[.]49 port 80 - mohurndertil[.]com - POST /d2/about.php
- 46.235.47[.]84 port 80 - wood-boards[.]com - GET /wp-content/plugins/tumblr-crosspostr/1
- 46.235.47[.]84 port 80 - wood-boards[.]com - GET /wp-content/plugins/tumblr-crosspostr/2
- 46.235.47[.]84 port 80 - wood-boards[.]com - GET /wp-content/plugins/tumblr-crosspostr/3
- 185.111.107[.]82 port 80 - tohinwithec[.]com - POST /bdl/gate.php
- 10.0.2.2 port 443 - TCP SYN segment approx once avery 5 minutes
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
ADDITIONAL POST-INFECTION URLS REPORTED BY @CHEAPBYTE:
- mohurndertil[.]com - POST /ls5/forum.php
- nyorcalning[.]ru - POST /ls5/forum.php
- hadsitguled[.]ru - POST /ls5/forum.php
- porthia.com[.]br - GET /wp-content/plugins/insert-pages/1
- porthia.com[.]br - GET /wp-content/plugins/insert-pages/2
- porthia.com[.]br - GET /wp-content/plugins/insert-pages/3
- questscopeduurzaam[.]nl - GET /wp-content/plugins/really-simple-captcha/1
- questscopeduurzaam[.]nl - GET /wp-content/plugins/really-simple-captcha/2
- questscopeduurzaam[.]nl - GET /wp-content/plugins/really-simple-captcha/3
- nmultra2014[.]no - GET /.tmb/1
- nmultra2014[.]no - GET /.tmb/2
- nmultra2014[.]no - GET /.tmb/3
- yana-k-design[.]com - GET /wp-content/plugins/menu-social-icons/1
- yana-k-design[.]com - GET /wp-content/plugins/menu-social-icons/2
- yana-k-design[.]com - GET /wp-content/plugins/menu-social-icons/3
- lvpar[.]com[.]br - GET /wp-content/plugins/wordpress-seo/1
- lvpar[.]com[.]br - GET /wp-content/plugins/wordpress-seo/2
- lvpar[.]com[.]br - GET /wp-content/plugins/wordpress-seo/3
ADDITIONAL POST-INFECTION URL NOTED IN REVERSE.IT ANALYSIS OF DELOADER/ZLOADER:
- 92.63.106[.]180 port 80 - nofocalen[.]com - POST /bdl/gate.php
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 643951eee2dac8c3677f5ef7e9cb07444f12d165f6e401c1cd7afa27d7552367
File name: Intuit_Invoice_649272.doc
File size: 296,960 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 206d7fe28230cced9110517c401f72e11ce68bb2dc617d476f6a935f8be4da97
File location: C:\Users\[username]\AppData\Local\Temp\BN9A1C.tmp
File size: 194,048 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
