2017-07-29 - "BLANK SLATE" CAMPAIGN PUSHES BTCWARE (ALETA VARIANT) RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-29-BTCware-ransomware-from-cabeiriscout_faith.pcap.zip 139 kB (138,830 bytes)
- 2017-07-29-Blank-Slate-email-tracker.csv.zip 0.8 kB (806 bytes)
- 2017-07-29-Blank-Slate-emails-and-BTCware-files.zip 305.0 kB (304,950 bytes)
BACKGROUND:
- 2017-03-02 - Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- 2017-03-22 - Internet Storm Center (ISC): "Blank Slate" malspam still pushing Cerber ransomware.
- 2017-06-29 - ISC: Catching up with Blank Slate: a malspam campaign still going strong.
TODAY'S NOTES:
- In the past two or three weeks, I've seen a lot of BTCware ransomware from the Blank Slate campaign.
- This is the Aleta variant of BTCware, using the .aleta file extension for encrypted files.
- More information on this "Aleta" variant of BTCware can be found here.
- No post-infection traffic for this ransomware.
EMAILS
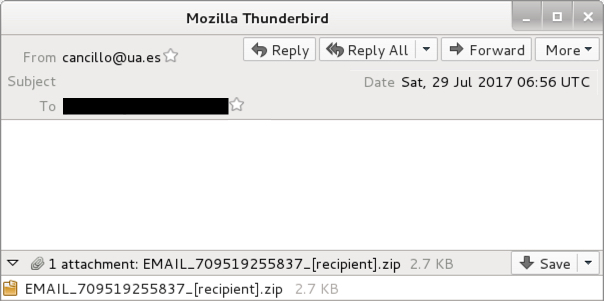
Shown above: Example of the emails seen.
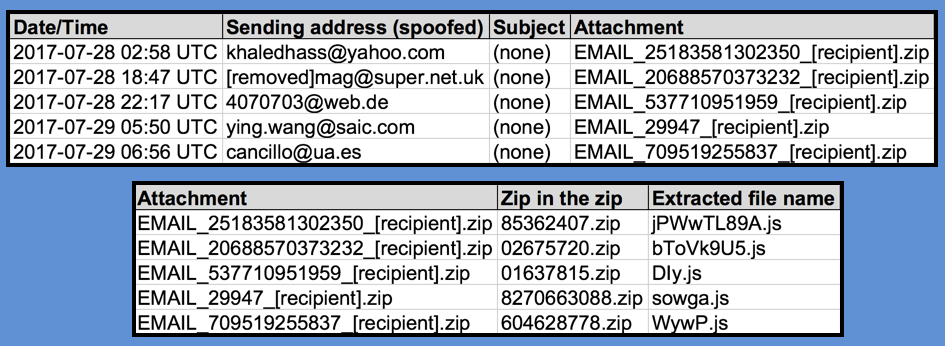
Shown above: Samples collected as noted in the spreadsheet tracker.
TRAFFIC
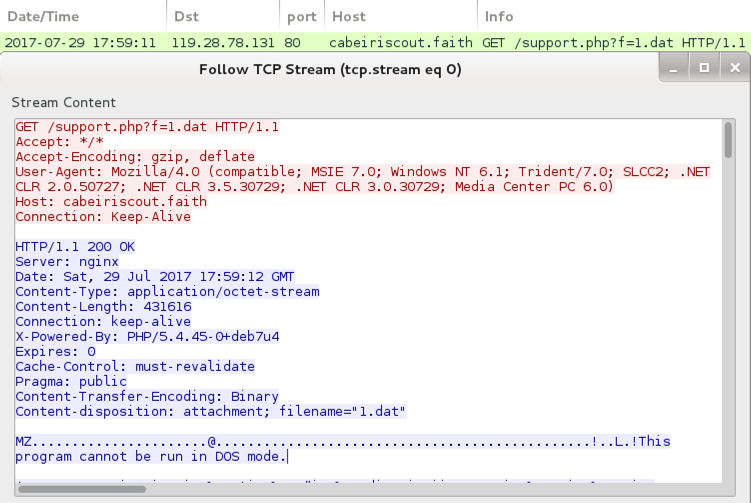
Shown above: Traffic from an infection filtered in Wireshark.
URLS GENERATED BY THE EXTRACTED .JS FILES TO GET THE RANSOMWARE:
- 119.28.78[.]131 port 80 - cabeiriscout[.]faith - GET /support.php?f=1.dat
EMAIL FROM THE DECRYPTION INSTRUCTIONS:
- chines34@protonmail[.]ch
SHA256 HASHES
FILE ATTACHMENTS (ZIP ARCHIVES):
- 45c0a3a39459334c25bc82f2c9da40f7837750f28414d4ab667fd619c225e36e - EMAIL_20688570373232_[recipient].zip
- e4a210b6a0c9b3bcb5d43880ec150a5f3a42206c31ec553c9309c4b336419a24 - EMAIL_25183581302350_[recipient].zip
- fd474697a5a81c82589012a859318f0232717575476f7819af8b4c7f50acc21f - EMAIL_29947_[recipient].zip
- a23cb27fd3354d2e0f5ad898ad482196ab32fb571ab7edb02fba50fe35f718b5 - EMAIL_537710951959_[recipient].zip
- a52b3db623f2b2a9cedf0e4c0a6358a0791d65e50cb0229425c4bacd0888f361 - EMAIL_709519255837_[recipient].zip
EXTRACTED .JS FILES:
- 9b5697e2341ccb16a9c70f15daf3e0b6d890e974ccd3c6a594daa7753aec050e - DIy.js
- b335f7e2416d76f457147ce1550560890e7582840a246d95cdf08d64f0384056 - WywP.js
- d5afe2e525f2d8810cfbdec709353e79a21b5f7b2c9999fc108a4a0bbb0ceb45 - bToVk9U5.js
- ef1f4c5a5581333f3091fa13cec4a1fc94609bad92e2de3c7cd045329e34bf45 - jPWwTL89A.js
- 5141a89e6fed2838a8107c83b218b2dd158a03623cd12b3e781bdb3342d559c8 - sowga.js
BTCWARE (ALETA VARIANT) RANSOMWARE SAMPLE:
- SHA256 hash: 8c137b7ea011e0ecd9e7ad76536e6c50c29bea3a0f277a132bfe48af1b7b8958
File size: 431,616 bytes
File description: BTCware from cabeiriscout[.]faith on 2017-07-29
IMAGES
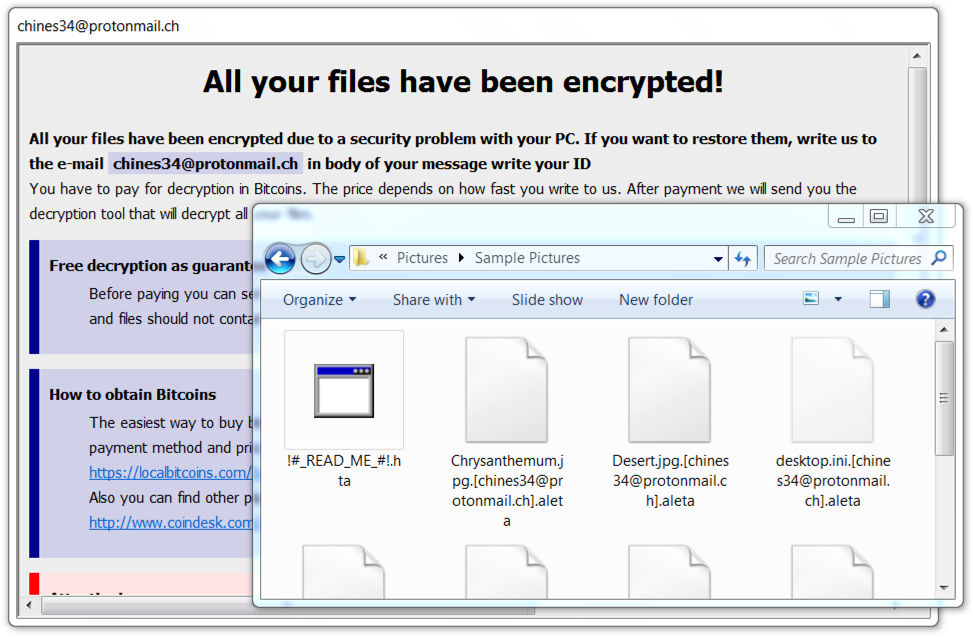
Shown above: Desktop of a Windows host infected with today's BTCware sample.
Click here to return to the main page.
