2017-07-31 - GLOBEIMPOSTER RANSOMWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-31-GlobeImposter-ransomware-traffic.pcap.zip 164.9 kB (164,889 bytes)
- 2017-07-31-GlobeImposter-email-tracker.csv.zip 1.2 kB (1,205 bytes)
- 2017-07-31-GlobeImposter-ransomware-emails-and-malware.zip 402.9 kB (402,868 bytes)
BLOG AND TWEET RELATED TO THIS WAVE OF MALSPAM:
- 2017-07-28 - @tmmalanalyst: "Voice Message Attached" #malspam campaigns spreading #GlobeImposter ransomware (file extension .725) - (link to tweet)
- 2017-07-31 - @tmmalanalyst: Jul-31,2017(JST). MalSpam attached ZIP -> vbs. Infects #GlobeImposter? #Ransomware. D/W URL: "luczki[.]pl/98wugf56?" - (link to tweet)
- 2025 udpate: The BroadAnalysis[.]com blog I previously referenced here is no longer online. I've removed any references to it in this post, but some of my images here still reference the site.
TODAY'S NOTES:
- I think this is malspam from the Necurs botnet.
- Keep in mind that Globe ransomware and GlobeImposter ransomware are two different ransomware families.
- Thanks to @BleepinComputer and @James_inthe_box, both who helped confirm for me this is GlobeImposter ransomware.
- Today's GlobeImposter ransomware still appended all encrypted files names with .725 as seen on 2017-07-29.
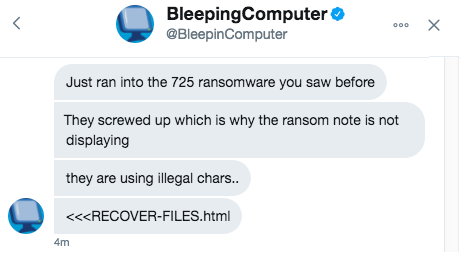
Shown above: Some DMs today on Twitter with @BleepinComputer.
EMAILS
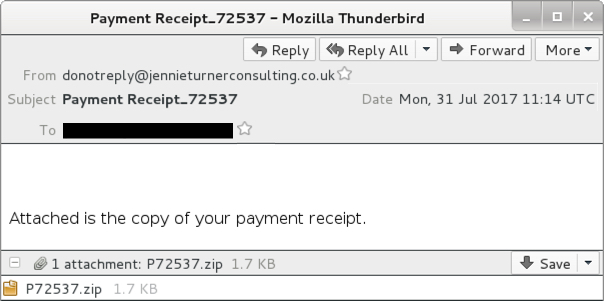
Shown above: Screenshot from one of the emails.
10 SAMPLES FROM TODAY'S MALSPAM:
(Read: Date/Time -- sending address (spoofed) -- Subject -- Attachment name)
- 2017-07-31 11:14:18 UTC -- donotreply@jennieturnerconsulting[.]co[.]uk -- Payment Receipt_72537 -- P72537.zip
- 2017-07-31 11:14:26 UTC -- donotreply@ritson.globalnet[.]co[.]uk -- Payment 0451 -- P0451.zip
- 2017-07-31 11:16:03 UTC -- donotreply@vintageplanters[.]co[.]uk -- Payment Receipt#039 -- P039.zip
- 2017-07-31 11:18:35 UTC -- donotreply@bowker61.fastmail[.]co[.]uk -- Receipt 78522 -- P78522.zip
- 2017-07-31 11:23:06 UTC -- donotreply@satorieurope[.]co[.]uk -- Receipt#6011 -- P6011.zip
- 2017-07-31 11:28:13 UTC -- donotreply@npphotography[.]co[.]uk -- Payment-59559 -- P59559.zip
- 2017-07-31 11:32:29 UTC -- donotreply@anytackle[.]co[.]uk -- Receipt-70724 -- P70724.zip
- 2017-07-31 11:33:18 UTC -- donotreply@gecko-accountancy[.]co[.]uk -- Receipt#374 -- P374.zip
- 2017-07-31 11:47:53 UTC -- donotreply@corbypress[.]co[.]uk -- Payment Receipt#03836 -- P03836.zip
- 2017-07-31 11:58:07 UTC -- donotreply@everythingcctv[.]co[.]uk -- Payment_1479 -- P1479.zip
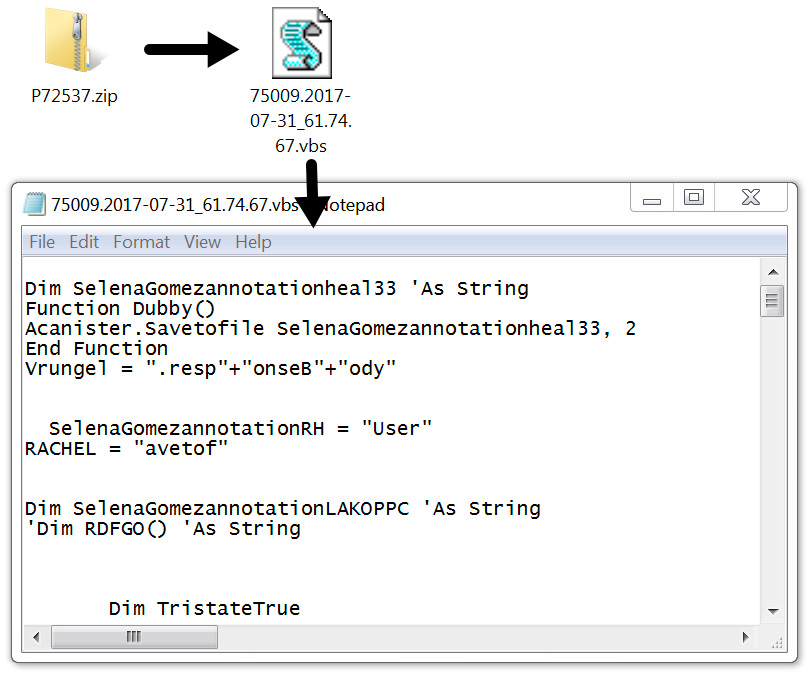
Shown above: One of the attachments and its extracted VBS file.
10 ATTACHMENTS FROM TODAY'S MALSPAM:
(Read: Attachment name -- Extracted VBS file)
- P72537.zip -- 75009.2017-07-31_61.74.67.vbs
- P0451.zip -- 20172.2017-07-31_75.20.68.vbs
- P039.zip -- 65309.2017-07-31_30.97.61.vbs
- P78522.zip -- 18472.2017-07-31_68.36.18.vbs
- P6011.zip -- 18472.2017-07-31_68.36.18.vbs
- P59559.zip -- 68386.2017-07-31_49.72.83.vbs
- P70724.zip -- 19367.2017-07-31_31.97.09.vbs
- P374.zip -- 94780.2017-07-31_55.34.69.vbs
- P03836.zip -- 45677.2017-07-31_69.96.50.vbs
- P1479.zip -- 42421.2017-07-31_15.10.22.vbs
TRAFFIC
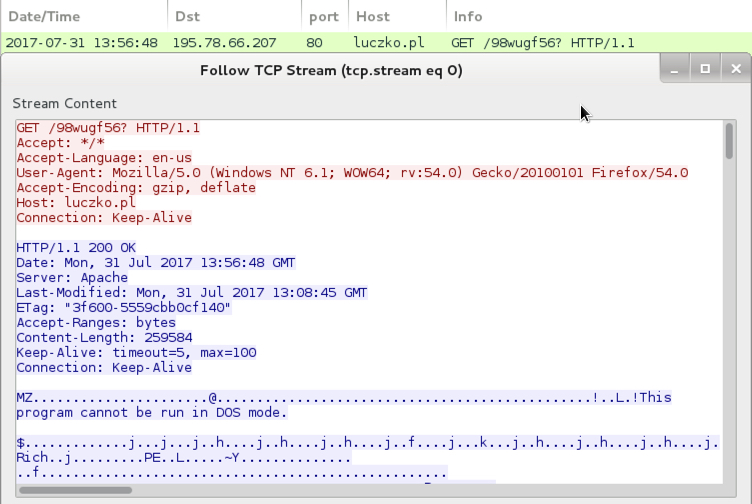
Shown above: Traffic from an infection filtered in Wireshark.
URLS GENERATED BY THE EXTRACTED VBS FILES TO GET THE RANSOMWARE:
- cattolica2000[.]it - GET /98wugf56?
- colorglobe[.]in - GET /98wugf56?
- delwishealthcare[.]com - GET /98wugf56?
- etiennevermeersch[.]be - GET /98wugf56?
- gentemergente[.]com - GET /98wugf56?
- healthbynature[.]co[.]nz - GET /98wugf56?
- imexltd[.]eu - GET /98wugf56?
- koewege[.]de - GET /98wugf56?
- lauchdapper[.]de - GET /98wugf56?
- luczko[.]pl - GET /98wugf56?
- okdomvrn[.]ru - GET /98wugf56?
- ortigra[.]com - GET /98wugf56?
- premiermusicals[.]com - GET /98wugf56?
- psmsas[.]com - GET /98wugf56?
- puzniak[.]eu - GET /98wugf56?
- rhinelanderrabbits[.]com - GET /98wugf56?
- szymanowicz[.]eu - GET /98wugf56?
- tdtuusula[.]com - GET /98wugf56?
- trredfcjrottrdtwwq[.]net - GET /af/98wugf56
ASSOCIATED URLS FROM THE 2017-07-29 SAMPLE NOTED TODAY:
- n224ezvhg4sgyamb[.]onion - GET /efwdaq.php
- 198.23.241[.]227 - serv1[.]xyz - GET /counter.php?nu=105&fb=725
SHA256 HASHES
FILE ATTACHMENTS (ZIP ARCHIVES):
- 666cb642cafcfe2d38f2ccce6481c6404120b7f3c3ea4b3e8bed30374bcfdfff - P039.zip
- 3a5fefdf055eb60ff9b779156b39293182363b836abb5780f3691773f14bf2d3 - P0451.zip
- 165c3e3c543068721b3295a2864fc3846cc7f337c91a55496d2da998a2df59ca - P03836.zip
- c15f6314a8664405b8faefab7ab8a26e8968cc896bc527fa031c28928de7e448 - P374.zip
- 1fe2a6f68010021220b8a470bd820f2f35d1ef4b24d2a28af9663549bc31f49e - P6011.zip
- cb0ae6ebefd3cccb2a76452a4d6139361d2b7b41f132e6187ab6956b5355bc4a - P1479.zip
- 10ed1fda3be6de33c7d71c4672e8c464a73388d5904f5a01aab4a3fc5d764203 - P59559.zip
- 3e52dc310920741c05e38645badfcfa6bfe5ad25ba34c18abac04e2c508c3dbe - P70724.zip
- 4b26ebceadd798ee3ef428cfac13a7d2d804c2c11330652b74b5b33e1f863256 - P72537.zip
- 5f69e1d33255abb782b20f5719e49eab88a5cfa4c61bf637d2d6a6e3907052d3 - P78522.zip
EXTRACTED VBS FILES:
- 595d433edbb5f5bc5e2de12721c696c8f6ec9150cbe20a55cc764db3ee0d1139 - 18472.2017-07-31_68.36.18.vbs
- e650a11bfe30c8e116f077c8bb12baddd4527f2a3a08cc97637f49af84392db6 - 19367.2017-07-31_31.97.09.vbs
- 9f476dccaa8ed2d8ee30cea0232413c236197ad7fff59b77d266b55dbcd711d6 - 20172.2017-07-31_75.20.68.vbs
- 543554fd3a46dd6ac23b71222247467920d84bb7f462610acb99f71ba0abd3d6 - 42421.2017-07-31_15.10.22.vbs
- 9a8470fb20324d4abb9d6f672ed17e6edcd111f4864c41584a47d4d687bd6504 - 45677.2017-07-31_69.96.50.vbs
- 8ae32d966276d7637b0fa6b9a98e85064f7f0b19b7035fff5bcf0695a26c7380 - 65309.2017-07-31_30.97.61.vbs
- d2240033ca49f6dd5d7fbeea990bd2b296a346226d780cae7f684c83aa667ef6 - 68386.2017-07-31_49.72.83.vbs
- acd5a05a4ab2afc58b78319a2ff25632354f90adb682b45ebf136b6dcd5f66f9 - 75009.2017-07-31_61.74.67.vbs
- db295c027237c511bd17683b35bc9458b20dc0f1ec2113278914a7b0d10b857f - 94680.2017-07-31_80.86.74.vbs
- 706b55d7b8b74631d57ed185093f555e23272bf1792ff3ed29316ee2caa36bc0 - 94780.2017-07-31_55.34.69.vbs
GLOBEIMPOSTER EXE BINARIES DOWNLOADED BY VBS FILES:
- SHA256 hash: 72ddceebe717992c1486a2d5a5e9e20ad331a98a146d2976c943c983e088f66b
File size: 274,432 bytes
File description: GlobeImposter sample from 2017-07-28
- SHA256 hash: be345c3beea2f6e489a9541361fc50221088ca166504a3beae237004fcb9ac5a
File size: 259,584 bytes
File description: GlobeImposter sample from today (2017-07-31)
IMAGES
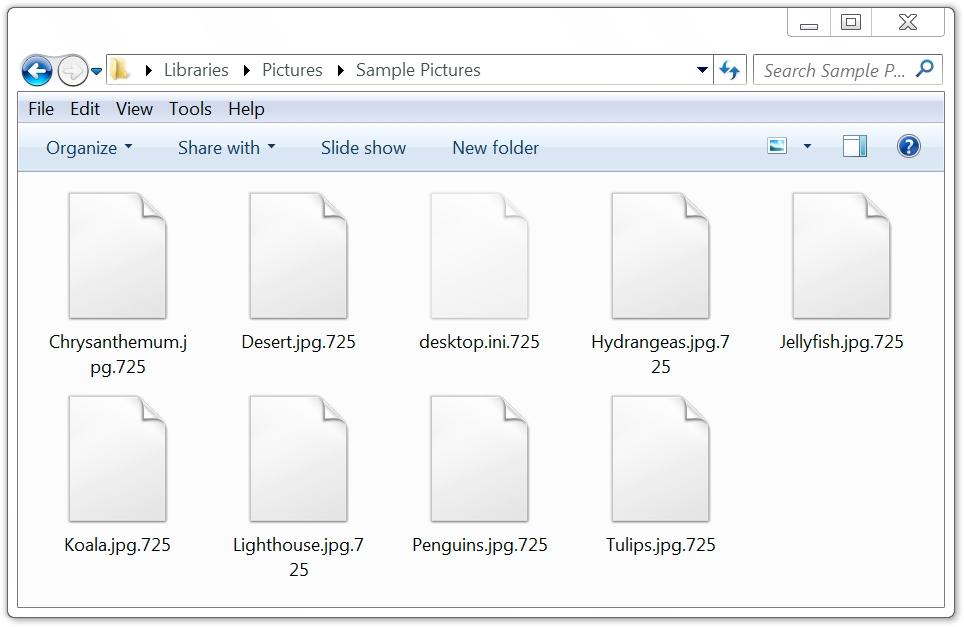
Shown above: Desktop of a Windows host infected with today's BTCware sample.
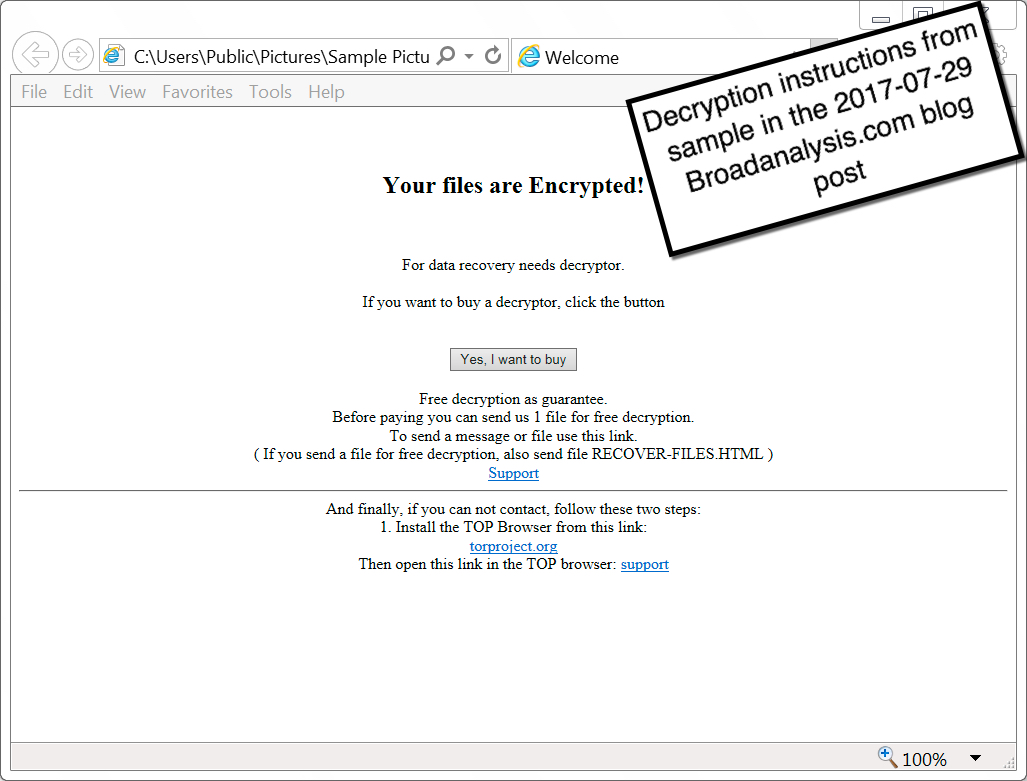
Shown above: Decryption instructions for the 2017-07-28 GlobeImposter sample.
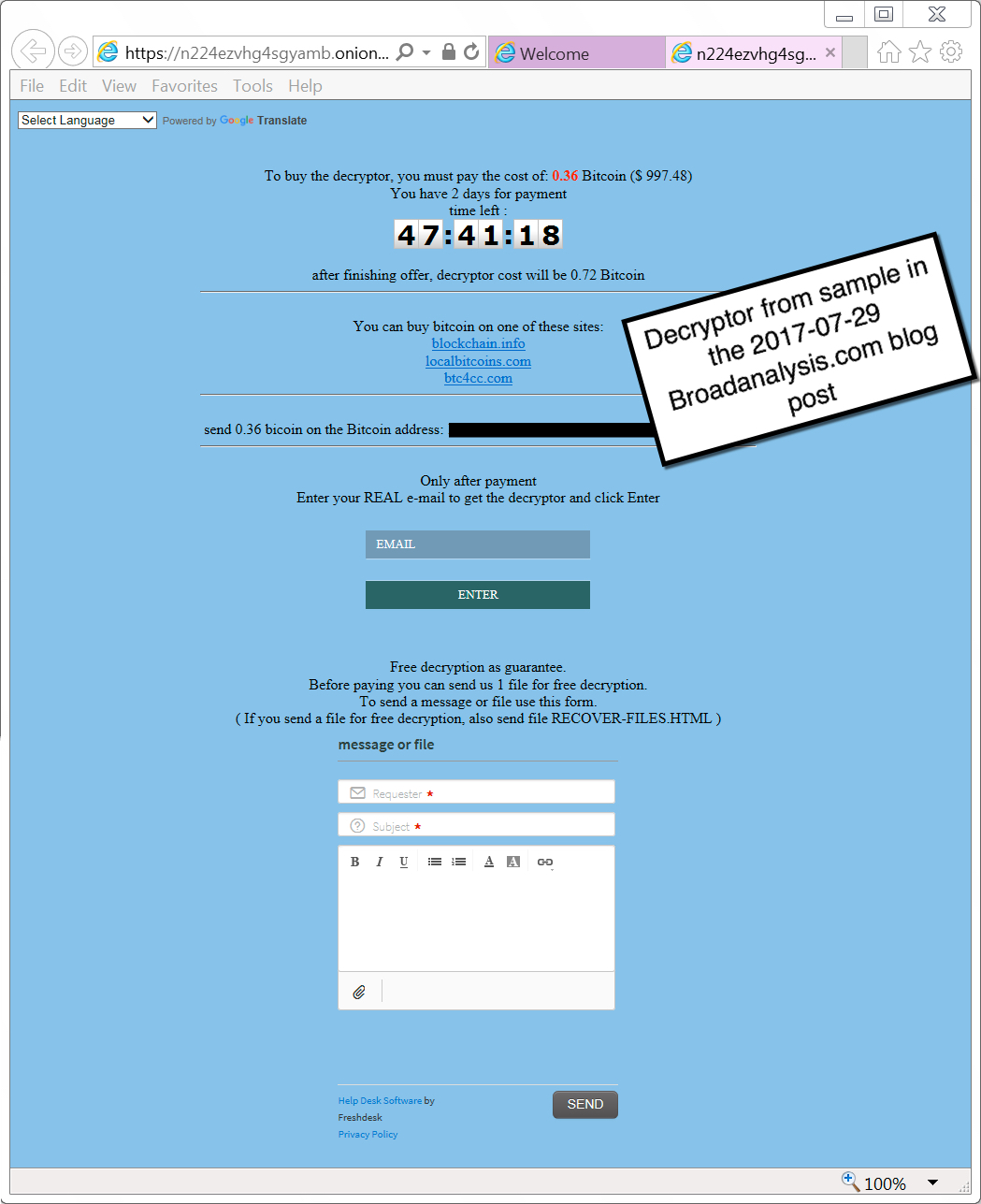
Shown above: Decryptor for the 2017-07-28 GlobeImposter sample.
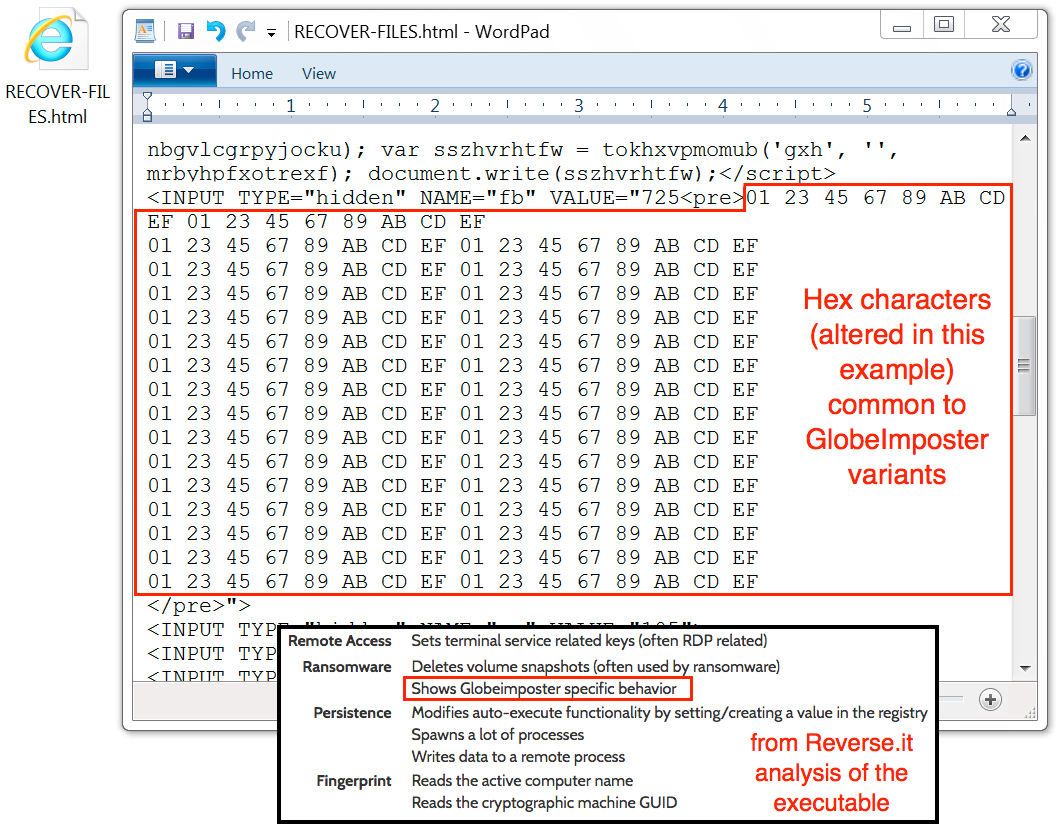
Shown above: Some indicators this is GlobeImposter ransomware.
Click here to return to the main page.