2017-08-01 - RIG EK FROM THE HOOKADS CAMPAIGN SENDS DREAMBOT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-08-01-HookAds-Rig-EK-pcaps.zip 10.1 MB (10,089,198 bytes)
- 2017-08-01-1st-run-HookAds-Rig-EK-sends-Dreambot.pcap (393,266 bytes)
- 2017-08-01-2nd-run-HookAds-Rig-EK-sends-Drembot-with-post-infection-traffic.pcap (8,660,170 bytes)
- 2017-08-01-3rd-run-HookAds-Rig-EK-sends-Dreambot.pcap (420,082 bytes)
- 2017-08-01-4th-run-HookAds-Rig-EK-sends-Dreambot.pcap (728,508 bytes)
- 2017-08-01-5th-run-HookAds-Rig-EK-sends-Dreambot.pcap (758,882 bytes)
- 2017-08-01-HookAds-Rig-EK-malware-and-artifacts.zip 496.9 kB (496,937 bytes)
- 2017-08-01-1st-run-Rig-EK-landing-page.txt (61,659 bytes)
- 2017-08-01-1st-run-amand_info-banners-countryhits.txt (6,417 bytes)
- 2017-08-01-1st-run-popunder.php-from-HookAds-related-site.txt (1,251 bytes)
- 2017-08-01-2nd-run-Rig-EK-landing-page.txt (122,407 bytes)
- 2017-08-01-2nd-run-amand_info-banners-countryhits.txt (6,417 bytes)
- 2017-08-01-2nd-run-popunder.php-from-HookAds-related-site.txt (1,251 bytes)
- 2017-08-01-3rd-run-Rig-EK-landing-page.txt (122,496 bytes)
- 2017-08-01-3rd-run-amand_info-banners-countryhits.txt (6,421 bytes)
- 2017-08-01-3rd-run-popunder.php-from-HookAds-related-site.txt (1,251 bytes)
- 2017-08-01-4th-run-Rig-EK-landing-page.txt (61,573 bytes)
- 2017-08-01-4th-run-amand_info-banners-countryhits.txt (6,445 bytes)
- 2017-08-01-4th-run-popunder.php-from-HookAds-related-site.txt (1,251 bytes)
- 2017-08-01-5th-run-Rig-EK-landing-page.txt (122,590 bytes)
- 2017-08-01-5th-run-amand_info-banners-countryhits.txt (6,421 bytes)
- 2017-08-01-5th-run-popunder.php-from-HookAds-related-site.txt (1,251 bytes)
- 2017-08-01-HookAds-payload-from-Rig-EK-Dreambot.exe (315,392 bytes)
- 2017-08-01-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-08-01-Rig-EK-flash-exploit.swf (13,747 bytes)
BACKGROUND ON THE HOOKADS CAMPAIGN:
- 2016-11-01 - Malwarebytes Blog: The HookAds malvertising campaign (link)
- 2017-05-14 - Zerophage Malware: Rig EK delivers Chthonic (link)
- 2017-06-14 - Zerophage Malware: Rig EK via malvertising drops Dreambot (link)
- And I've got a handful of previous blog posts on this site for HookAds.
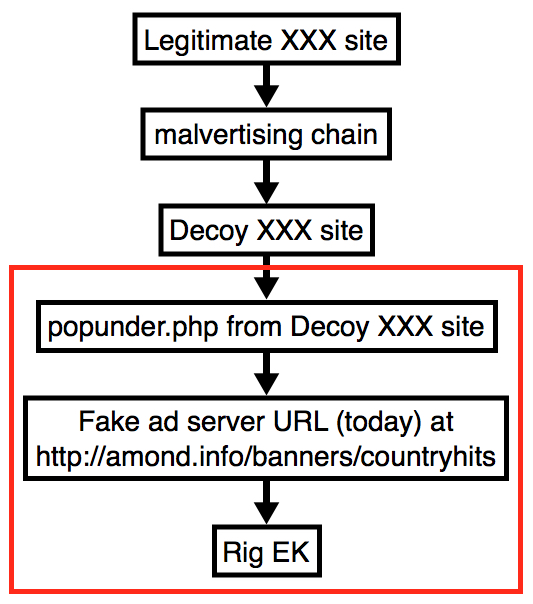
Shown above: Chain of events for today's infection traffic. The portion outlined in red
represents what I have in today's pcaps.
TRAFFIC
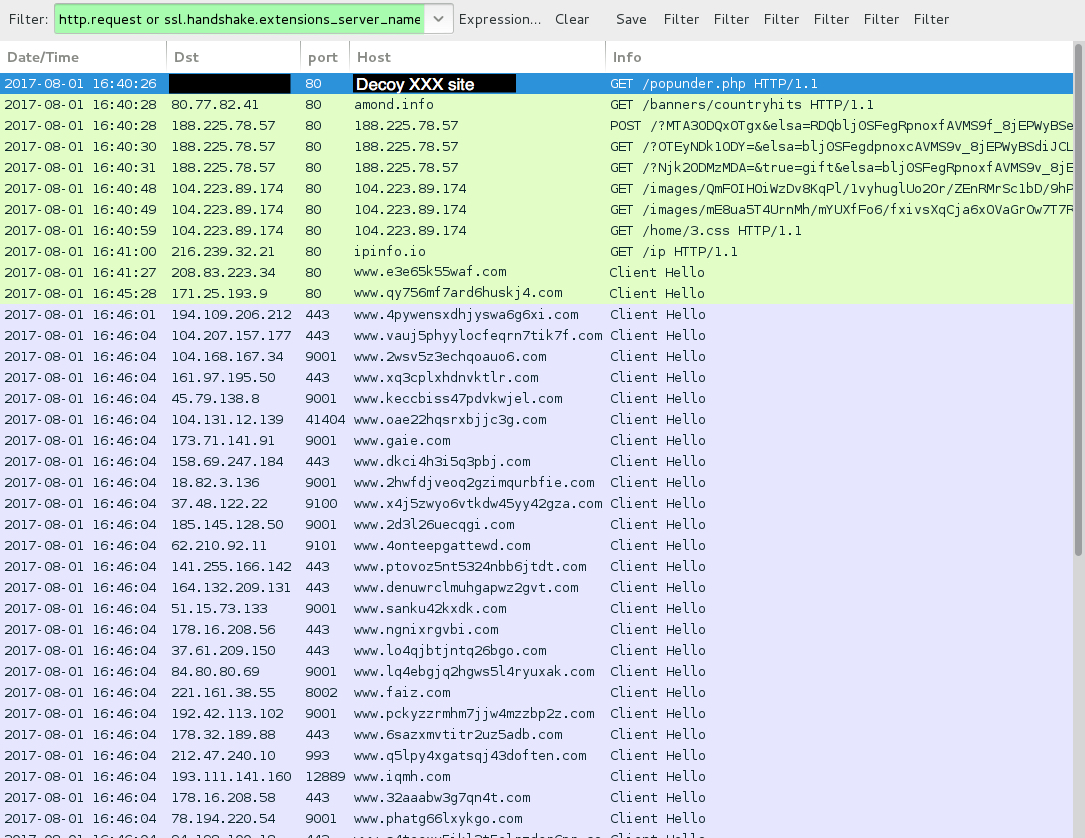
Shown above: Traffic from the one of the pcaps filtered in Wireshark.
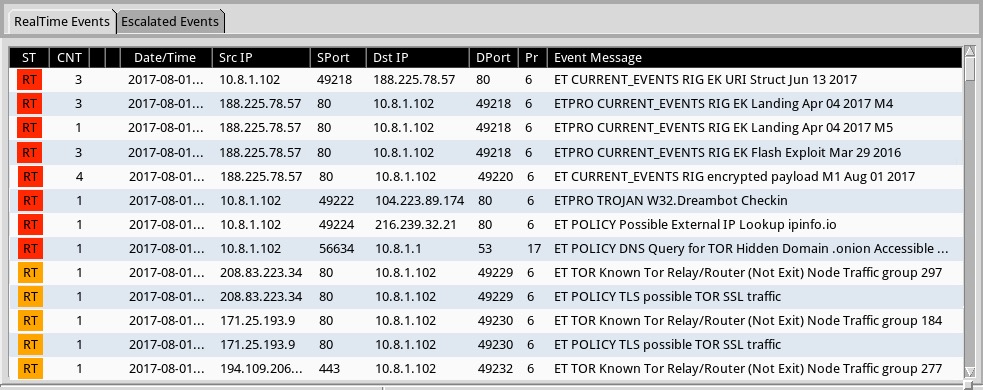
Shown above: Alerts on the above pcap in Security Onion with Sguil using Suricata and the Emerging Threats Pro (ETPRO) ruleset.
ASSOCIATED DOMAINS AND URLS:
- [information removed] port 80 - [fake porn domain] - GET /popunder.php [injected script from HookAds-related decoy porn site]
- 80.77.82[.]41 port 80 - amond[.]info - GET /banners/counterhits [HookAds gate/redirect]
- 188.225.79[.]167 port 80 - 188.225.78[.]57 - Rig EK - 1st and 2nd runs
- 188.225.35[.]56 port 80 - 188.225.35[.]56 - Rig EK - 3rd and 4th runs
- 188.225.78[.]226 port 80 - 188.225.78[.]226 - Rig EK - 5th run
- 104.223.89[.]174 port 80 - 104.223.89[.]174 - GET /images/[long string of characters].avi - Dreambot post-infection traffic
- 104.223.89[.]174 port 80 - 104.223.89[.]174 - GET /home/3.css - Dreambot post-infection traffic
- port 80 - ipinfo[.]io - GET /ip [Dreambot post-infection IP address check]
- DNS query for wdwefwefwwfewdefewfwefw[.]onion - did not resolve
- Various IP addresses and over various ports - Tor traffic
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: adc668371b43cbd6711a01a49015e3f2f52de6ed6080bbe873bc7366593f235b
File size: 13,747 bytes
File description: Rig EK flash exploit seen on 2017-08-01
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 6e7f74fb50217ee363622f8e70976342638049499523325df4c03c340e64bb15
File size: 315,392 bytes
File location: C:\Users\[username]\AppData\Local\Temp\[random characters].exe
File location: C:\Users\[username]\AppData\Roaming\Microsoft\[random folder name]\[random file name].exe
File description: Dreambot from HookAds campaign sent using Rig EK on 2017-08-01
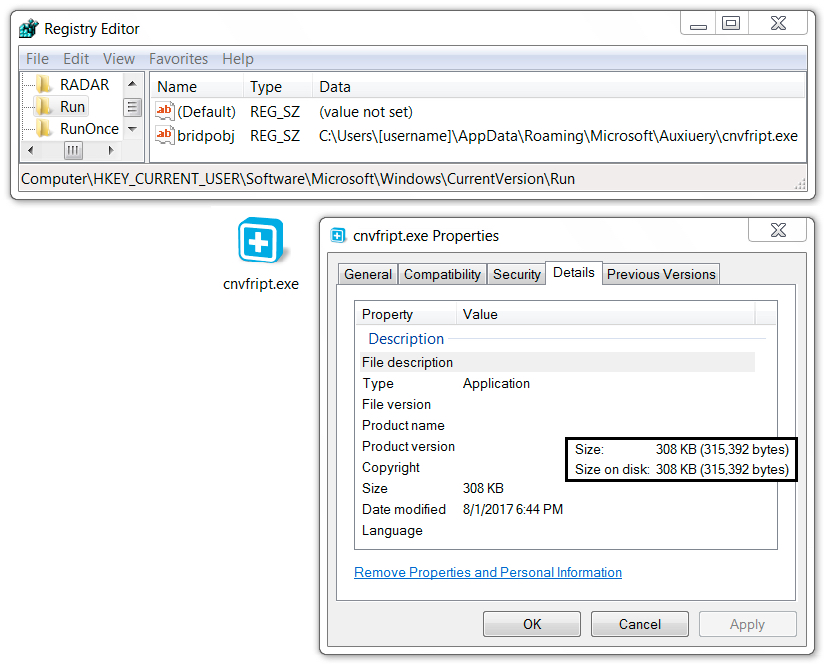
Shown above: Dreambot made persistent on the infected Windows host.
Click here to return to the main page.