2017-08-02 - MAGNITUDE EK SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-08-02-Magnitude-EK-sends-Cerber-ransomware.pcap.zip 768.1 kB (768,068 bytes)
- 2017-08-02-Magnitude-EK-sends-Cerber-ransomware.pcap (942,407 bytes)
- 2017-08-02-Magnitude-EK-and-Cerber-ransomware-artifacts-and-malware.zip 920.0 kB (919,974 bytes)
- 2017-08-02-Cerber-decryption-instructions.bmp (1,920,054 bytes)
- 2017-08-02-Cerber-decryption-instructions_R_E_A_D___T_H_I_S___0AK861OQ_.txt (1,383 bytes)
- 2017-08-02-Cerber-decryption-instructions_R_E_A_D___T_H_I_S___DSJR_.hta (77,982 bytes)
- 2017-08-02-Magnitude-EK-payload-Cerber.exe (249,856 bytes)
- 2017-08-02-Mangitude-EK-flash-exploit.swf (37,564 bytes)
- 2017-08-02-Mangitude-EK-landing-page.txt (7,315 bytes)
- 2017-08-02-Mangitude-EK-returned-XML-script.txt (1,343 bytes)
- 2017-08-02-response-from-b16eauf5z38u9l.ourspen_com.txt (2,570 bytes)
- 2017-08-02-response-from-gate-domain-leading-to-Magnitude-EK.txt (1,204 bytes)
NOTES:
- I accidentally filtered out the Cerber ransomware post-infection UDP port 6893 traffic from the pcap.
- For more info, see the August 2017 Malwarebytes blog post, Enemy at the gates: Reviewing the Magnitude exploit kit redirection chain
TRAFFIC
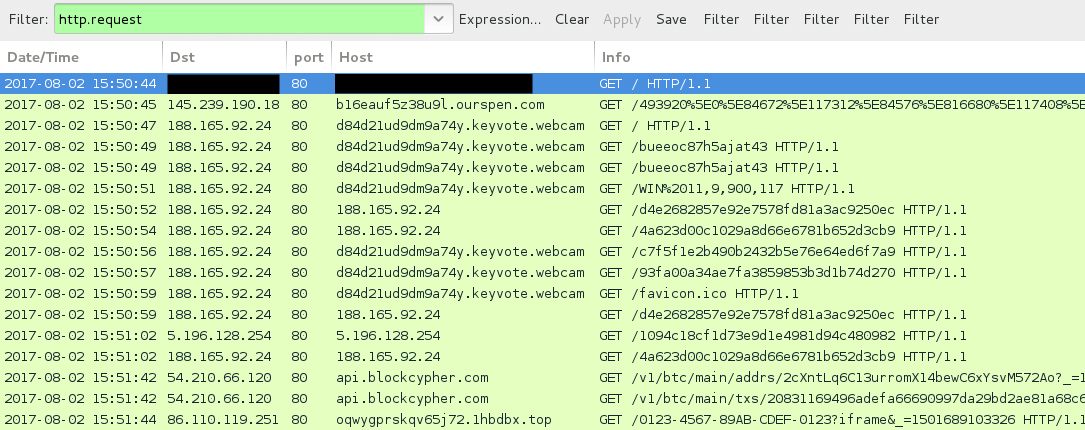
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS:
- [redacted] port 80 - [one of the "magnigate" domains] - GET /
- 145.239.190[.]18 port 80 - b16eauf5z38u9l.ourspen[.]com - [another "magnigate" URL]
- 188.165.92[.]24 port 80 - d84d21ud9dm9a74y.keyvote[.]webcam - [Magnitude EK]
- 188.165.92[.]24 port 80 - 188.165.92[.]24 - [Magnitude EK sending payload]
- 5.196.128[.]254 port 80 - 5.196.128[.]254 - [Magnitude EK sending payload - 404 not found]
- 73.107.12[.]0 - 73.107.12[.]31 (73.107.12[.]0/27) UDP port 6893 [Cerber post-infection UDP scan]
- 75.1.200[.]0 - 75.1.200[.]31 (75.1.200[.]0/27) UDP port 6893 [Cerber post-infection UDP scan]
- 87.98.176[.]0 - 87.98.179[.]255 (87.98.176[.]0/22) UDP port 6893 [Cerber post-infection UDP scan]
- 86.110.119[.]251 port 80 - oqwygprskqv65j72.1hbdbx[.]top - [Cerber post-infection HTTP traffic]
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 9cf8ed1111cb5b04b040ad57dcf87225659a6cb4ac10e7cf4381d397b5f67c89
File size: 37,564 bytes
File description: Flash exploit seen from Magnitude EK on 2017-08-02
MAGNITUDE EK PAYLOAD (CERBER RANSOMWARE):
- SHA256 hash: cee87e61f13e50217169e338342370aa94e31f0bacdf3d1b901e1dd79c9f8d87
File size: 249,856 bytes
File description: Cerber ransomware sent by Magnitude EK on 2017-08-02
IMAGES
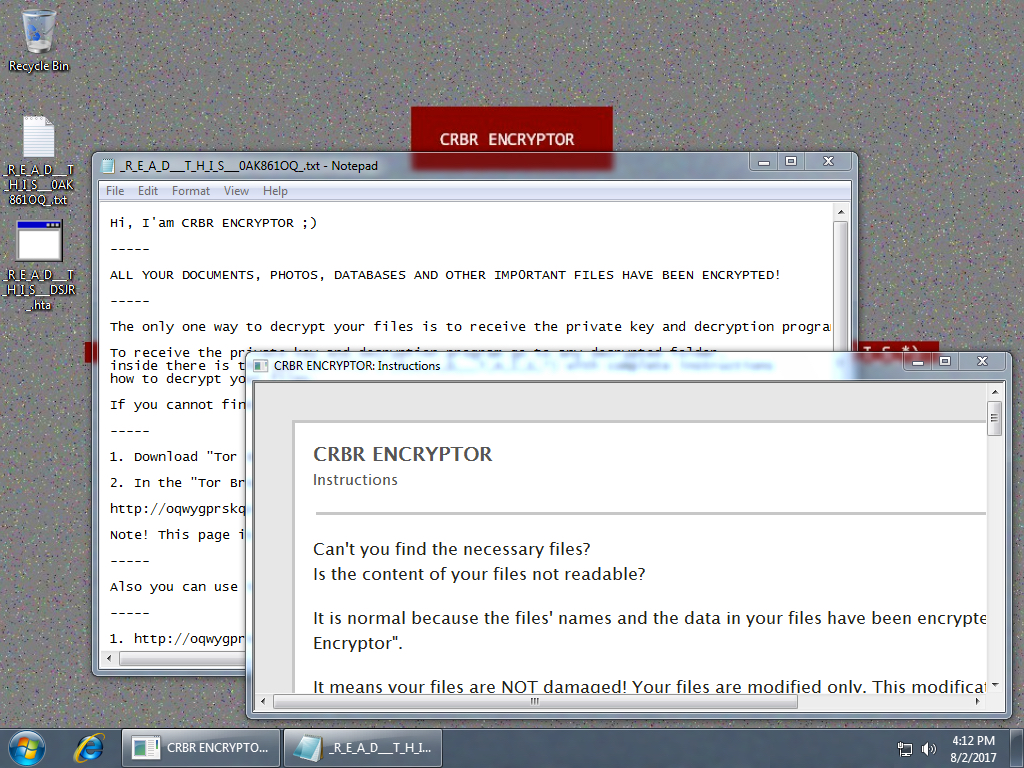
Shown above: Desktop of the infected Windows host.
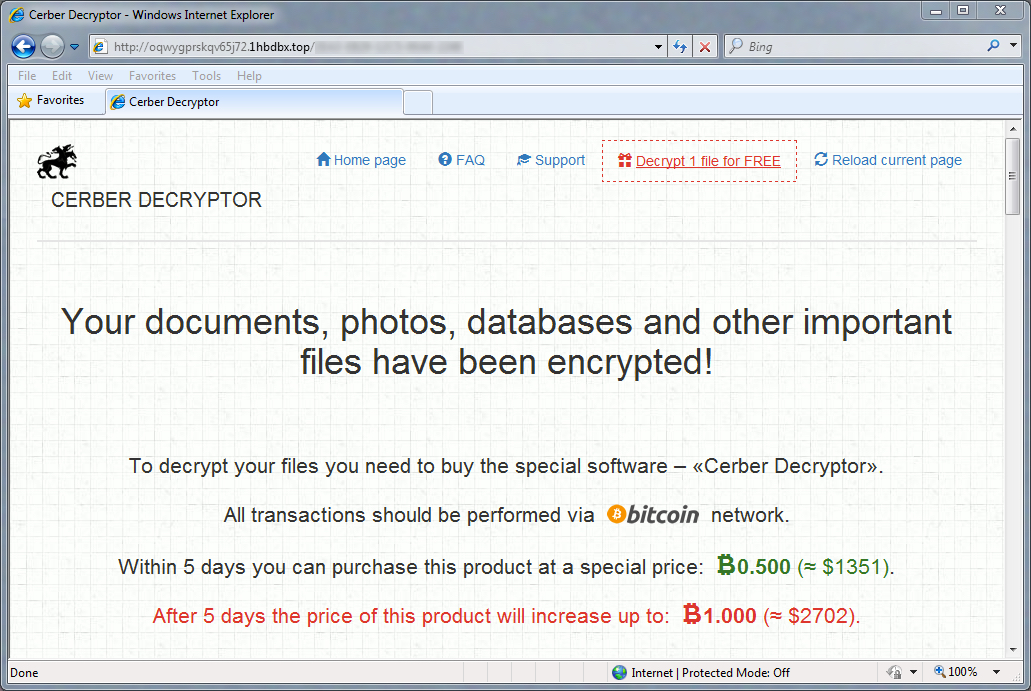
Shown above: Cerber decryption instructions.
Click here to return to the main page.
