2017-08-02 - GLOBEIMPOSTER RANSOMWARE (.726 FILE EXTENSION)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-08-02-GlobeImposter-ransomware-traffic.pcap.zip 185.6 kB (185,553 bytes)
- 2017-08-02-GlobeImposter-email-tracker.csv.zip 0.9 kB (884 bytes)
- 2017-08-02-GlobeImposter-ransomware-emails-and-malware.zip 249.6 kB (249,590 bytes)
NOTES:
- Several people tweeting about this today on Twitter.
- Saw this malspam throughout the day, so I grabbed a few examples to document it.
- The malspam switched sometime on 2017-08-02 from VBS files to JavaScript (.js) files to download GlobeImposter.
EMAILS
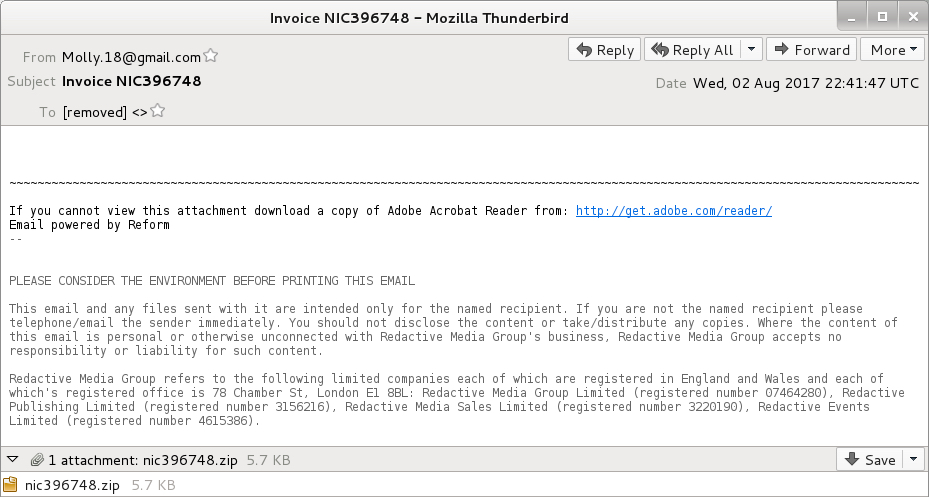
Shown above: Screenshot from one of today's emails.
6 SAMPLES FROM TODAY'S MALSPAM:
(Read: Date/Time -- sending address (spoofed) -- Subject -- Attachment name)
- 2017-08-02 12:51:55 UTC -- Tisha.698@gmail[.]com -- Invoice NIC768729 -- nic768729.zip
- 2017-08-02 13:10:48 UTC -- Lacy.655@gmail[.]com -- Invoice NIC935097 -- nic935097.zip
- 2017-08-02 13:31:22 UTC -- Tia.764@gmail[.]com -- Invoice NIC068752 -- nic068752.zip
- 2017-08-02 16:50:46 UTC -- Claire.205@gmail[.]com -- Invoice NIC390643 -- nic390643.zip
- 2017-08-02 21:51:19 UTC -- Kimberly.6759@gmail[.]com -- Invoice NIC201542 -- nic201542.zip
- 2017-08-02 22:41:47 UTC -- Molly.18@gmail[.]com -- Invoice NIC396748 -- nic396748.zip
6 ATTACHMENTS FROM TODAY'S MALSPAM:
(Read: Attachment name -- Extracted script file)
- nic768729.zip -- VM977387632_20170802.vbs
- nic935097.zip -- VM6921313254_20170802.vbs
- nic068752.zip -- VM9160399795_20170802.vbs
- nic390643.zip -- NIC423519.js
- nic201542.zip -- NIC423520.js
- nic396748.zip -- NIC423527.js
TRAFFIC
URLS GENERATED BY THE EXTRACTED SCRIPT FILES TO GET THE RANSOMWARE:
- akuboweb[.]com - GET /nv44f33f?
- benjamindiggles[.]com - GET/nv44f33f?
- conlin-boats[.]com - GET /nv44f33f?
- expeditiontiger[.]com - GET/nv44f33f?
- fly2[.]com.tw - GET /nv44f33f
- infinityscottsbluff[.]com - GET /nv44f33f?
- leapfrog-designs[.]com - GET /nv44f33f
- saborplus[.]pt - GET/nv44f33f?
- scoot-mail[.]net - GET /nv44f33f?
- trredfcjrottrdtwwq[.]net - GET /af/nv44f33f
- twi-emailer[.]nl - GET /nv44f33f?
- yourlocalsearch[.]ca - GET /nv44f33f?
POST-INFECTION TRAFFIC WHEN CHECKING THE DECRYPTION INSTRUCTIONS:
- n224ezvhg4sgyamb[.]onion - GET /efwdaq.php
- 198.23.241[.]227 – serv1[.]xyz - GET /counter.php?nu=105&fb=726
SHA256 HASHES
FILE ATTACHMENTS (ZIP ARCHIVES):
- 63a87bbae7cec32e50b78b295831b18ef2cea67054ea3589d3a2dd874bcbeb95 - nic068752.zip
- 0f61d20cfd80cebb4495287bab04f879032630f8362505fbf7cc5a066327d360 - nic201542.zip
- 1ee14afbc027fa411b928b460db7376f0d507fd0da7b9544cec0681cefc46bdd - nic390643.zip
- 9c46df61ae78552af6f2f30385a54c54a8bb365ec3ac1a858f21243268f5ca22 - nic396748.zip
- 21b6a8acc8a8a95a3ebc4ccab06d87c86490a350029f623542b5ea560abf988b - nic768729.zip
- 76d81cd85bfd6d7a52cf456355f15e7094c0ef1f900664e658f4c8d7feb8973c - nic935097.zip
EXTRACTED SCRIPT FILES:
- cfd408fbcf00a5b37f4f7db711d8fc79c0fe81b8c8ccc4a4fec223e2305d6ba2 - NIC423519.js
- 00283ed12058969b05b1aac755775a7cfe5c140b5d225c650e4eb1654e4bf22c - NIC423520.js
- 58ef6e7f5b02a1f3e486f9c8be5c70303564aea2a52d0b4d04103bbb28a4ad1f - NIC423527.js
- b58561530eef94c20edf210d4aac5fcdc36c4722656b649317f40cbc366d6a24 - VM6921313254_20170802.vbs
- 94f22e8a4ca1ff0d3382816715297e6898074d7c7744a1818590491ae7b5241f - VM9160399795_20170802.vbs
- 3b5f00e1a6fd80fc990ba1f086034fcaae099d4963785d71458fec5aa25a2c72 - VM977387632_20170802.vbs
GLOBEIMPOSTER EXE BINARY DOWNLOADED BY SCRIPT FILES:
- SHA256 hash: fe5d565b1f7b0a5b25edf491dafb826ab4270d99e574ba716baa99fd224aa504
File size: 293,888 bytes
File description: GlobeImposter sample from 2017-08-02 (caused .726 file extension)
IMAGES
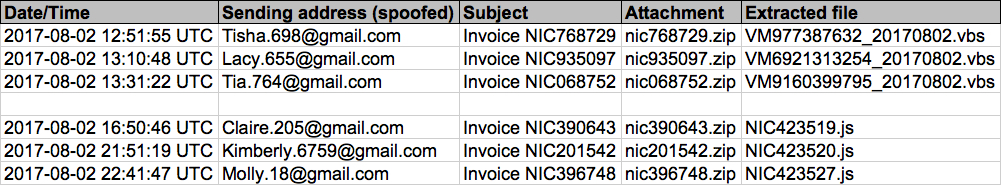
Shown above: Screenshot from the spreadsheet tracker.
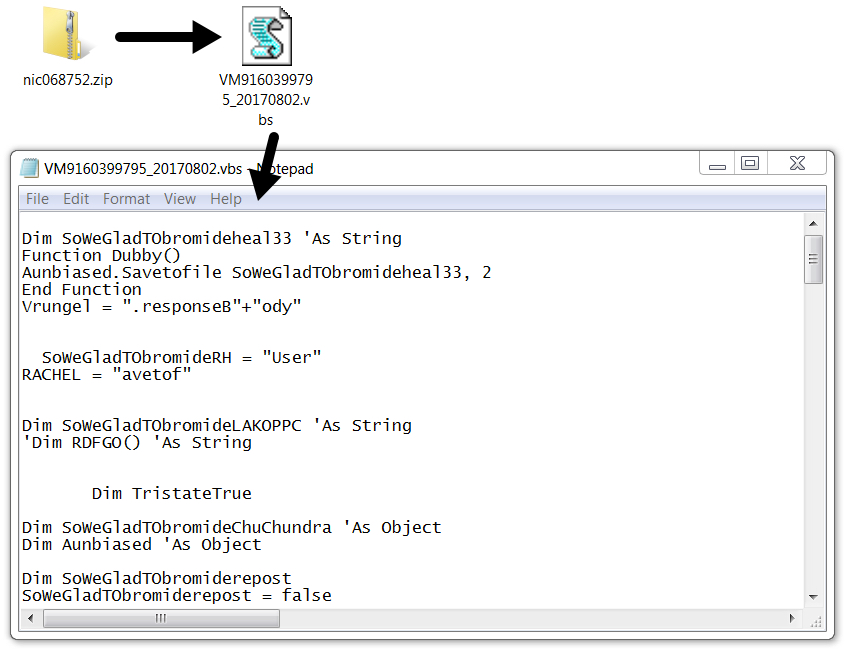
Shown above: Example of the attached zip archives containing a VBS file.
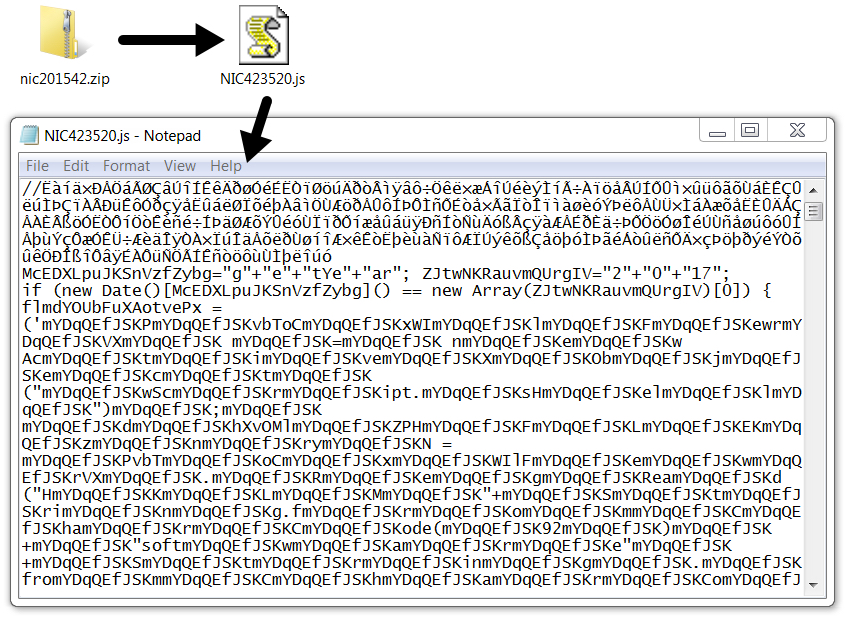
Shown above: Example of the attached zip archives containing a JavaScript (.js) file.
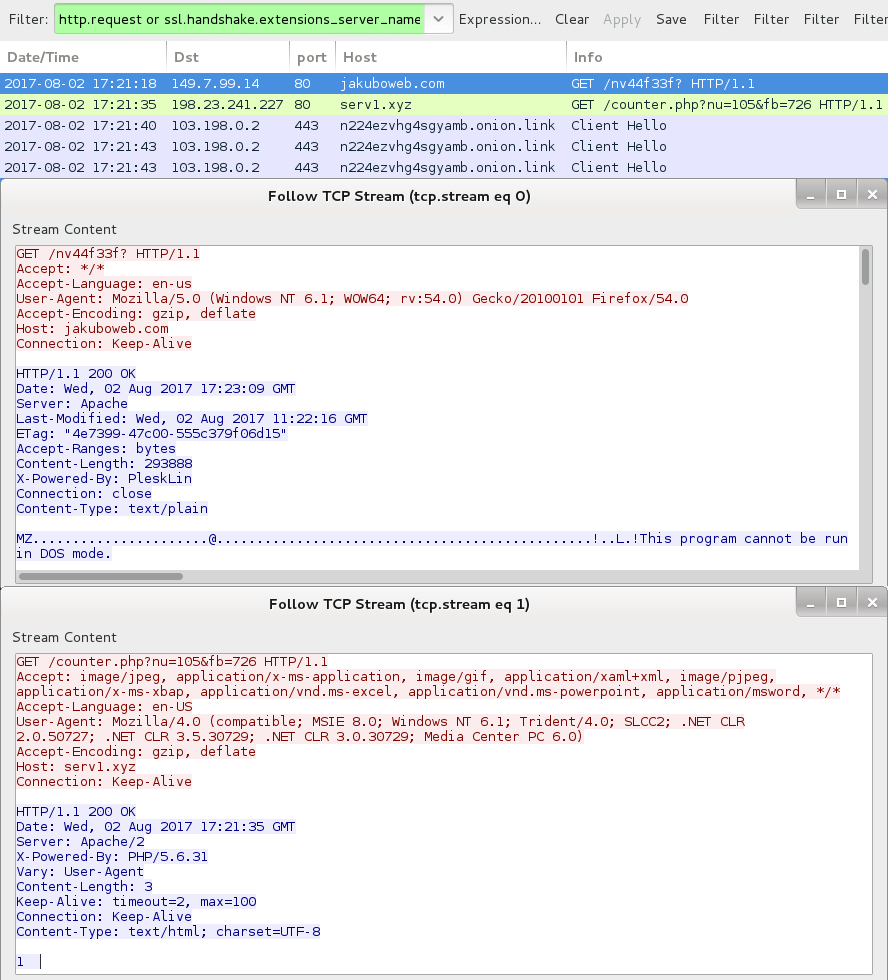
Shown above: Traffic seen during one of today's GlobeImposter ransomware infections.
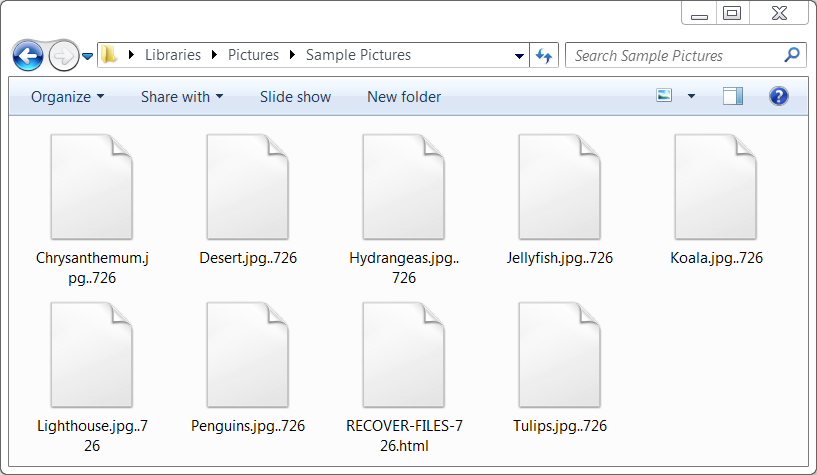
Shown above: Encrypted files all have a .726 file extension on an infected Windows host.
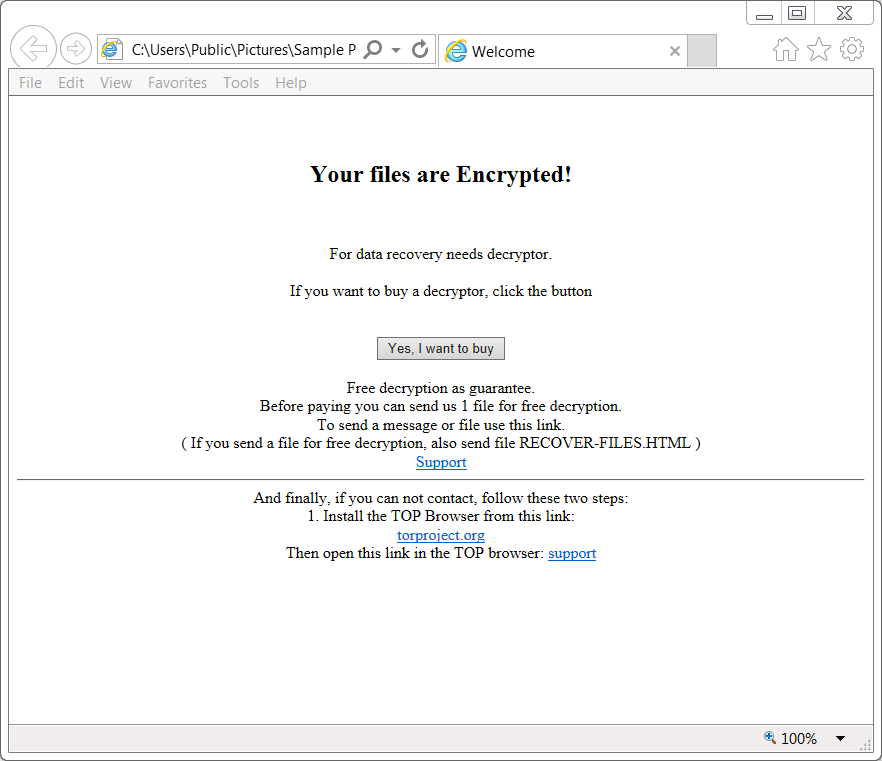
Shown above: GlobeImposter decryption instructions.
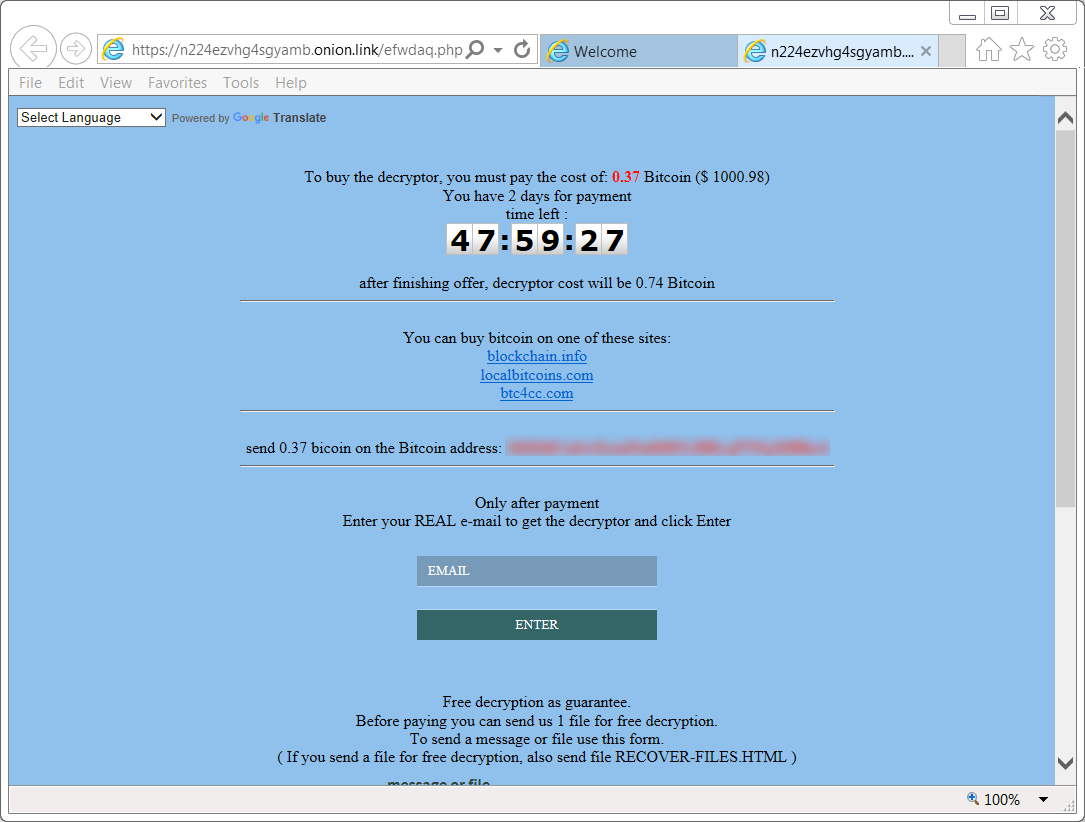
Shown above: GlobeImposter decryptor.
Click here to return to the main page.
