2017-08-03 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-08-03-Hancitor-infection-with-ZLoader.pcap.zip 9.1 MB (9,145,719 bytes)
- 2017-08-03-Hancitor-infection-with-ZLoader.pcap (9,882,970 bytes)
- 2017-08-03-Hancitor-malspam-3-examples.zip 3.5 kB (3,516 bytes)
- 2017-08-03-Hancitor-malspam-150038-UTC.eml (1,475 bytes)
- 2017-08-03-Hancitor-malspam-153147-UTC.eml (1,464 bytes)
- 2017-08-03-Hancitor-malspam-154120-UTC.eml (1,484 bytes)
- 2017-08-03-malware-from-Hancitor-infection.zip 314.4 kB (314,416 bytes)
- BNAFED.tmp (209,920 bytes)
- Invoice_808290.doc (300,032 bytes)
TODAY'S TWEETS COVERING THE 2017-08-03 WAVE OF #HANCITOR MALSPAM:
- @James_inthe_box: Incoming #hancitor run: "Re: invoice <digits> bullshit", new .doc type. (link)
- @cheapbyte: #hancitor #malspam #phishing Hancitor Aug 3, 2017 fake "Invoice <digits> bullshit" phish. Txt via Ghostbin (link)
EMAILS
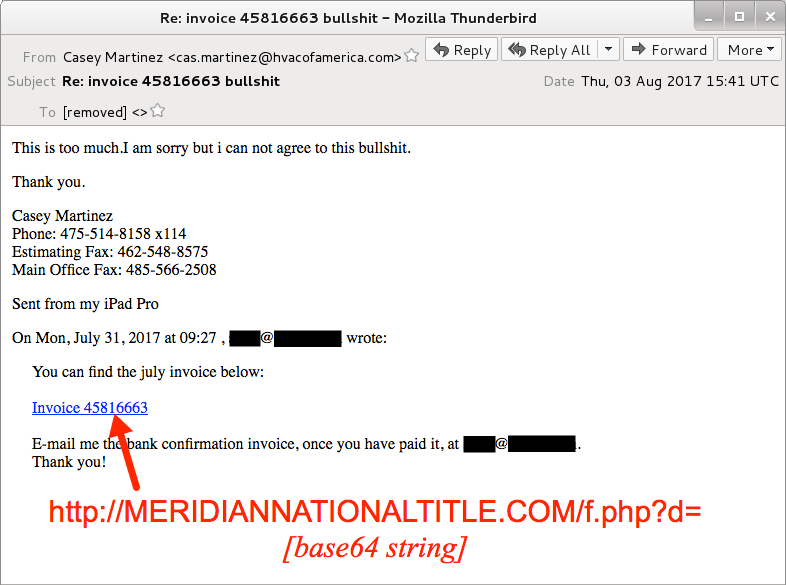
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date: Wednesday 2017-08-03 as early as 15:00 UTC through at least 15:41 UTC
- From: "Casey Martinez" <cas.martinez@hvacofamerica[.]com>
- Re: invoice 37432815 bullshit
- Re: invoice 42585083 bullshit
- Re: invoice 45816663 bullshit
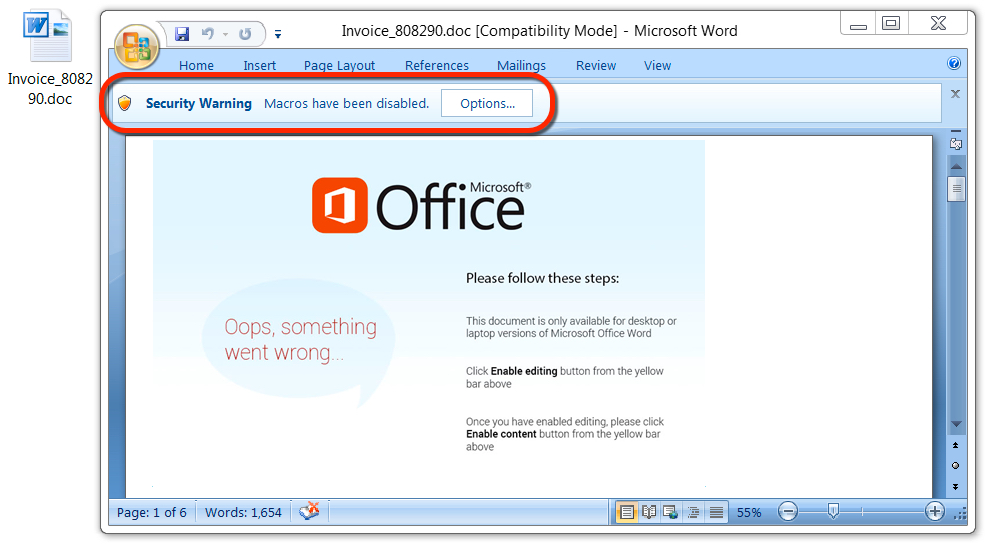
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
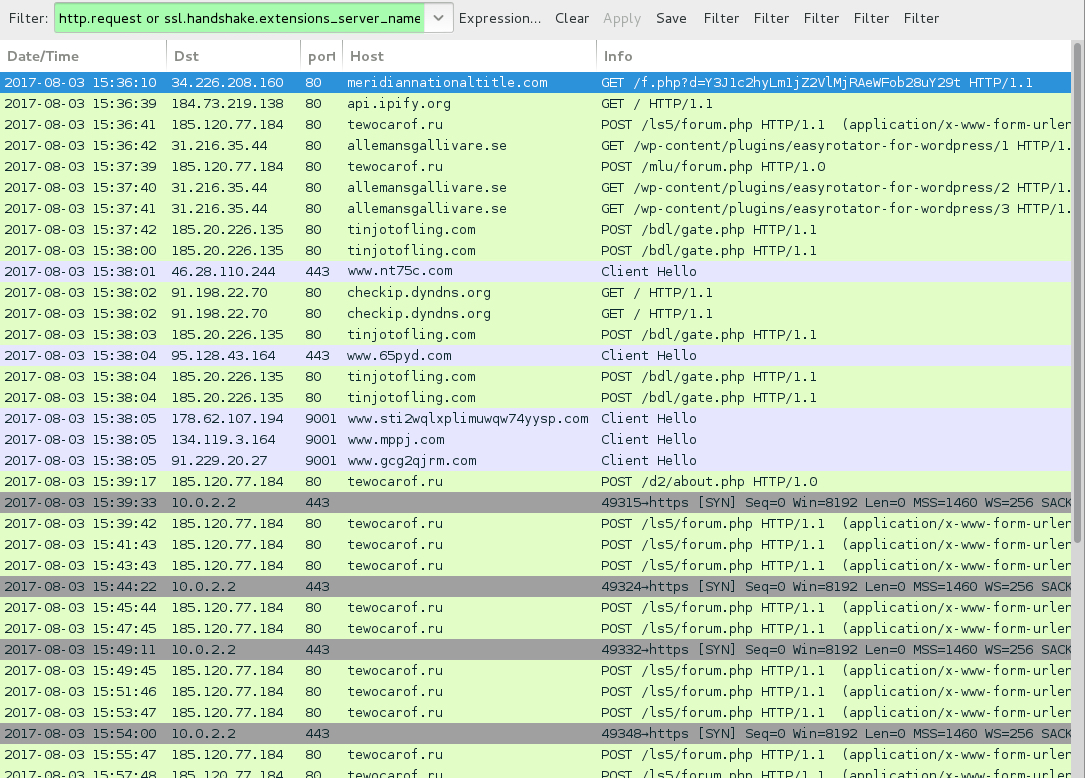
Shown above: Traffic from the infection filtered in Wireshark.
LINKS IN THE EMAILS THE WORD DOCUMENT:
- MERIDIANNATIONALTITLE[.]COM - GET /f.php?d=[base64 string]
- MERIDIANNATL[.]INFO - GET /f.php?d=[base64 string]
- RHJACK[.]INFO - GET /f.php?d=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENT:
- Invoice_[six random digits].doc
POST-INFECTION TRAFFIC FROM MY INFECTED HOST:
- 185.120.77[.]184 port 80 - tewocarof[.]ru - POST /ls5/forum.php
- 185.120.77[.]184 port 80 - tewocarof[.]ru - POST /mlu/forum.php
- 185.120.77[.]184 port 80 - tewocarof[.]ru - POST /d2/about.php
- 31.216.35[.]44 port 80 - allemansgallivare[.]se - GET /wp-content/plugins/easyrotator-for-wordpress/1
- 31.216.35[.]44 port 80 - allemansgallivare[.]se - GET /wp-content/plugins/easyrotator-for-wordpress/2
- 31.216.35[.]44 port 80 - allemansgallivare[.]se - GET /wp-content/plugins/easyrotator-for-wordpress/3
- 185.20.226[.]135 port 80 - tinjotofling[.]com - POST /bdl/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
- DNS query for ranwashertbi[.]com - Response: No such name
- 10.0.2.2 port 443 - TCP SYN segment approx once avery 5 minutes
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: efe7cfe0c08265e1a4eed68a1e544ba0e98fff98942e0e55941e1899aba71579
File name: Invoice_808290.doc
File size: 300,032 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 998179d7a379783c287dedaabdd537bb359c8c90c70ac69ea13c931f51d8e326
File location: C:\Users\[username]\AppData\Local\Temp\BNAFED.tmp
File size: 209,920 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
