2017-08-10 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-08-10-Hancitor-infection-with-ZLoader.pcap.zip 7.5 MB (7,477,233 bytes)
- 2017-08-10-Hancitor-infection-with-ZLoader.pcap (8,099,283 bytes)
- 2017-08-10-Hancitor-malspam-5-examples.zip 14.1 kB (14,066 bytes)
- 2017-08-10-Hancitor-malspam-173651-UTC.eml (16,543 bytes)
- 2017-08-10-Hancitor-malspam-174331-UTC.eml (16,542 bytes)
- 2017-08-10-Hancitor-malspam-174559-UTC.eml (16,552 bytes)
- 2017-08-10-Hancitor-malspam-180101-UTC.eml (16,549 bytes)
- 2017-08-10-Hancitor-malspam-182715-UTC.eml (16,551 bytes)
- 2017-08-10-Hancitor-malspam-190329-UTC.eml (16,541 bytes)
- 2017-08-10-malware-from-Hancitor-infection.zip 248.4 kB (248,441 bytes)
- Fedex_Invoice_598791.doc (232,960 bytes)
- defil.exe (173,568 bytes)
EMAILS
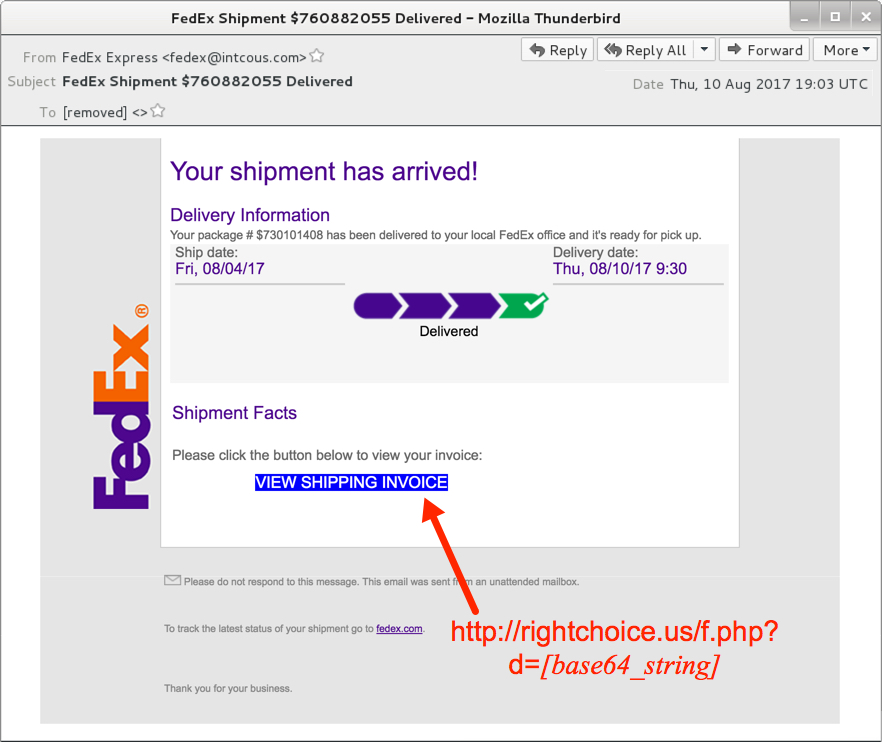
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date: Thursday 2017-08-10 as early as 17:36 UTC through at least 19:03 UTC
- From: "FedEx Express" <fedex@intcous[.]com>
- FedEx Shipment $080316662 Delivered
- FedEx Shipment $146564485 Delivered
- FedEx Shipment $374737114 Delivered
- FedEx Shipment $520013241 Delivered
- FedEx Shipment $637381061 Delivered
- FedEx Shipment $760882055 Delivered
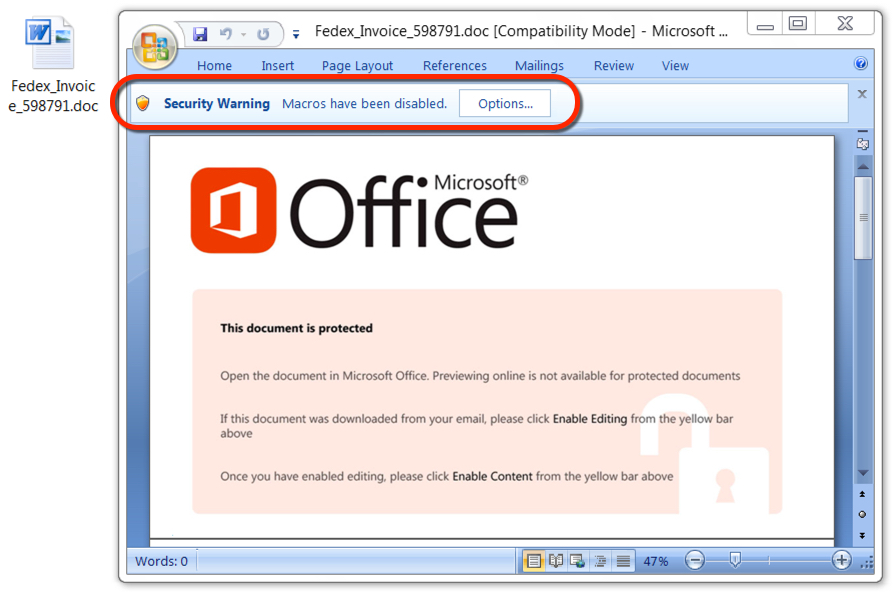
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
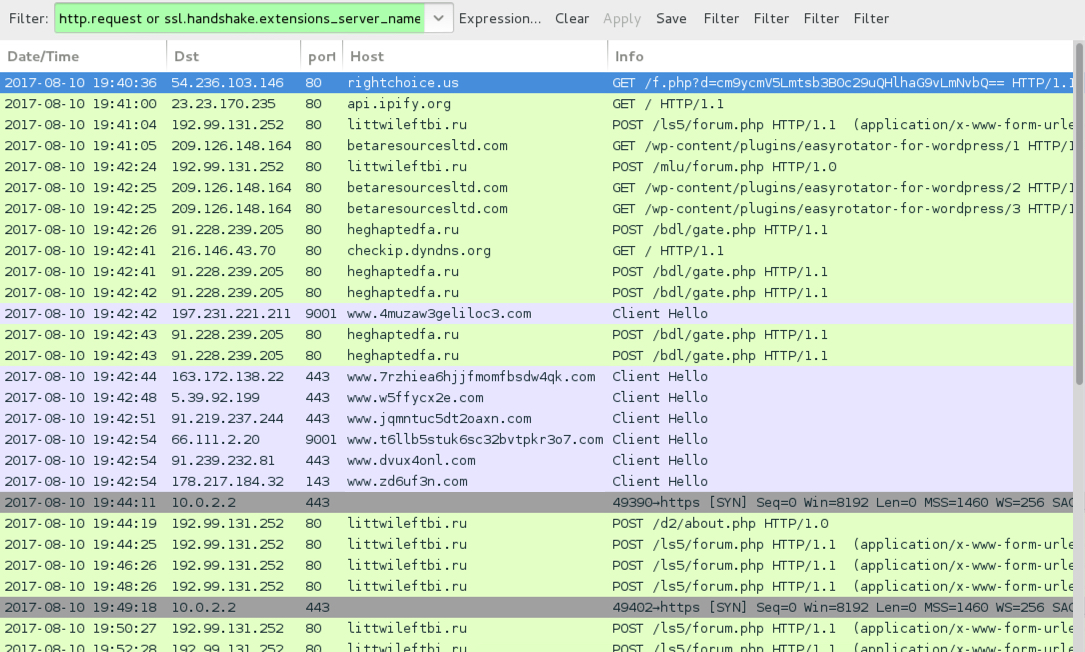
Shown above: Traffic from the infection filtered in Wireshark.
LINKS IN THE EMAILS THE WORD DOCUMENT:
- enviroluxgrowlights[.]com - GET /f.php?d=[base64 string]
- enviroluxlighting[.]net - GET /f.php?d=[base64 string]
- govprostore[.]com - GET /f.php?d=[base64 string]
- rightchoice[.]us - GET /f.php?d=[base64 string]
- tommyvapor[.]com - GET /f.php?d=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENT:
- Fedex_Invoice_[six random digits].doc
POST-INFECTION TRAFFIC FROM MY INFECTED HOST:
- 192.99.131[.]252 port 80 - littwileftbi[.]ru - POST /ls5/forum.php
- 192.99.131[.]252 port 80 - littwileftbi[.]ru - POST /mlu/forum.php
- 192.99.131[.]252 port 80 - littwileftbi[.]ru - POST /d2/about.php
- 209.126.148[.]164 port 80 - betaresourcesltd[.]com - GET /wp-content/plugins/easyrotator-for-wordpress/1
- 209.126.148[.]164 port 80 - betaresourcesltd[.]com - GET /wp-content/plugins/easyrotator-for-wordpress/2
- 209.126.148[.]164 port 80 - betaresourcesltd[.]com - GET /wp-content/plugins/easyrotator-for-wordpress/3
- 91.228.239[.]205 port 80 - heghaptedfa[.]ru - POST /bdl/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
- 86.110.117[.]167 port 80 - betwassjusthen[.]com - TCP SYN segments but no response from the server
- 10.0.2.2 port 443 - TCP SYN segment approx once avery 5 minutes
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 87a10cc169f9ffd0c75bb9846a99fb477fc4329840964b02349ae44a672729c2
File name: Fedex_Invoice_598791.doc
File size: 232,960 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 1ed3a443b17d3bd3825f8289735f059dd655fb24d628125c0204bdcdadc7865c
File location: C:\Users\[username]\AppData\Local\Temp\BN8979.tmp
File location: C:\Users\[username]\AppData\Roaming\Isaq\defil.exe
File size: 173,568 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
