2017-08-12 - TRICKBOT ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-08-12-Trickbot-infections-4-pcaps.zip 2.5 MB (2,512,416 bytes)
- 2017-08-12-Trickbot-malspam-tracker.csv.zip 1.1 kB (1,131 bytes)
- 2017-08-12-Trickbot-emails-and-malware.zip 1.8 MB (1,772,428 bytes)
NOTES:
- Trickbot is a banking Trojan that was first reported sometime in October 2016. It has been described as a successor to Dyreza or Dyre.
EMAILS
8 EXAMPLES FROM 2017-07-26 THROUGH 2017-08-11:
READ: DATE/TIME -- SENDING ADDRESS (SPOOFED) -- SUBJECT -- ATTACHMENT NAME
- 2017-07-26 17:22 UTC -- "HSBC" <noreply@hsbcdocs[.]co[.]uk> -- Account secure documents -- PaymentAdvice.doc
- 2017-08-01 19:08 UTC -- "Santander" <pleasedonotreply@santandersecuremessage[.]com> -- You have a new secure message waiting -- SecureMessage.doc
- 2017-08-02 17:39 UTC -- "HM Revenue & Customs" <donotreply@hmrccommunication[.]co[.]uk> -- You have a new secure communication -- SecureCommunication.doc
- 2017-08-03 17:07 UTC -- "Nationwide" <secured@nationwidesecure[.]co[.]uk> -- Nationwide Secure Email - Secured Message -- Secure.doc
- 2017-08-08 17:51 UTC -- "HM Revenue & Customs" <Gary.Brooks@hrmccommunication[.]co[.]uk> -- Company Excel Documents -- CompanyReport.xlsm
- 2017-08-09 10:31 UTC -- "New post Nat West Bank" <noreply@natwestdocuments6[.]ml> -- Nat West Bank -- West5476754-34.doc
- 2017-08-09 17:07 UTC -- "Lloyds Bank" <noreply@lloydsbacs[.]co[.]uk> -- Incoming BACs -- IncomingBACs.xlsm
- 2017-08-11 19:58 UTC -- "Natwest" <message@securenatwest[.]co[.]uk> -- Secure Message -- NATWESTSecureMessage.html
TRAFFIC
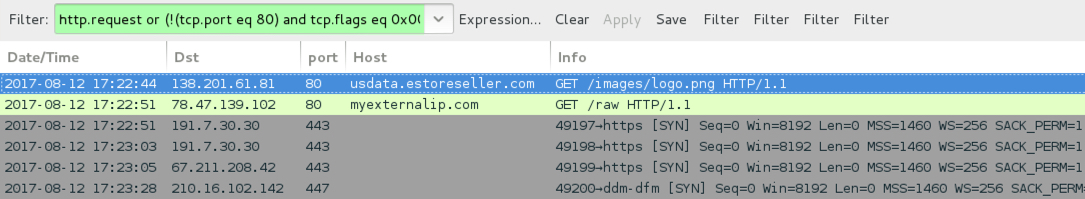
Shown above: Traffic from an infection filtered in Wireshark.
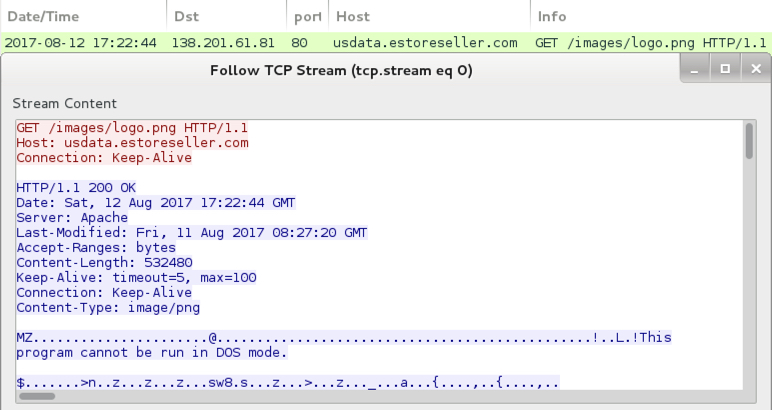
Shown above: Macros from Word or Excel retrieving a Trickbot binary.
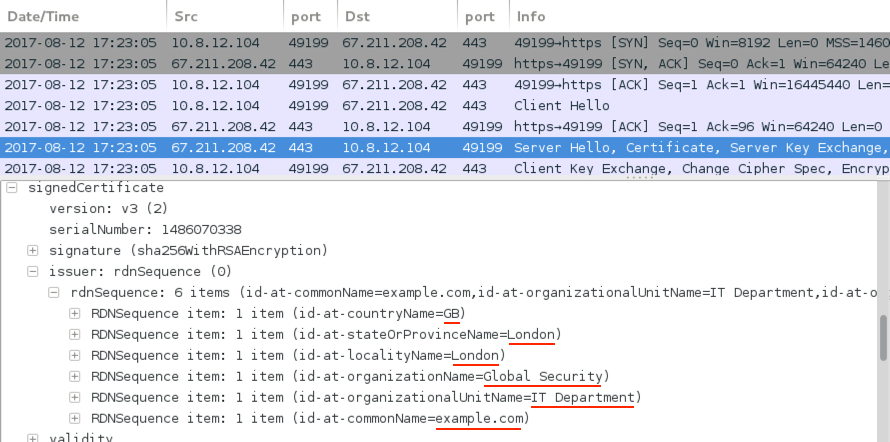
Shown above: Certificate data typical for Trickbot post-infection traffic.
URLS GENERATED BY MACROS FROM THE ASSOCIATED WORD OR EXCEL DOCUMENTS TO RETRIEVE TRICKBOT:
- akustikingenieur[.]de - GET /templates/ewerserber.png
- carriereiserphotography[.]com - GET /logo.png
- carriereiter[.]com - GET /html/logo.png
- casajenty[.]com - GET /logo.png
- casasaotiago[.]com - GET /logo.png
- catterydelacanaille[.]be - GET /logo.png
- cbsiinc[.]com - GET /images/logo.png
- cbsswaarland[.]nl - GET /logo.png
- cbt-sex[.]com - GET /logo.png
- cfsannita[.]com - GET /Socionorari/ewerserber.png
- cwpiper[.]com - GET /logo.png
- hvsglobal[.]co[.]uk - GET /image/nologo.png [HTTPS]
- kartautoeskola[.]com - GET /test/images/logo.png [HTTPS]
- lexpertpret[.]com - GET /fr/nolog.png
- usdata.estoreseller[.]com - GET /images/logo.png
URL FROM HTML ATTACHMENT ON 2017-08-11 EMAIL TO RETRIEVE WORD DOCUMENT:
- natwestsecmsg[.]co[.]uk - GET /SecureMessage.doc [HTTPS]
TRICKBOT POST-INFECTION IP ADDRESSES AND PORTS:
- 23.95.9[.]152 port 443
- 46.160.165[.]31 port 443
- 67.211.208[.]42 port 443
- 72.211.215[.]68 port 449
- 91.247.37[.]112 port 443
- 104.160.176[.]241 port 443
- 185.40.20[.]42 port 447
- 185.82.218[.]118 port 443
- 185.144.156[.]176 port 443
- 186.103.161[.]204 port 443
- 188.165.62[.]62 port 443
- 191.7.30[.]30 port 443
- 193.70.125[.]188 port 443
- 210.16.102[.]142 port 447
- 210.16.102[.]167 port 443
MALWARE
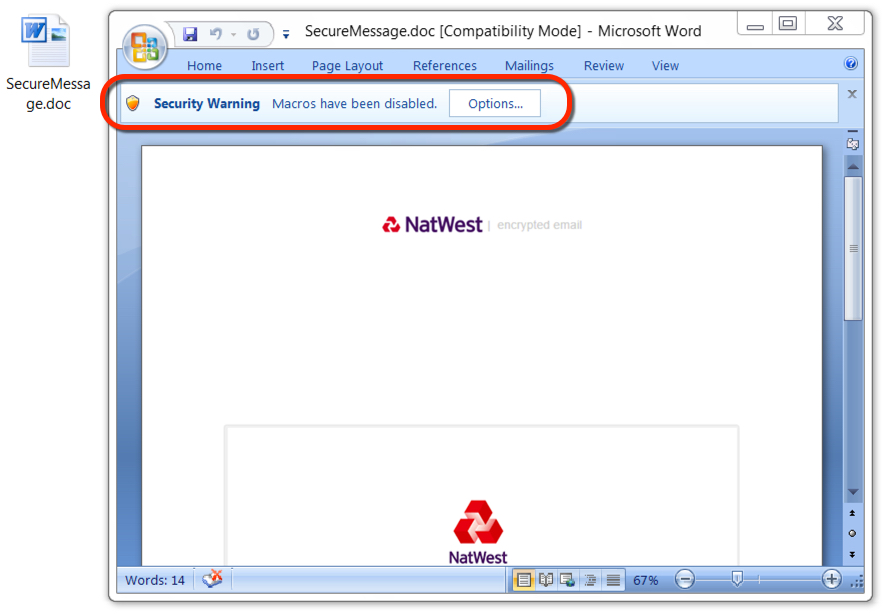
Shown above: One of the malicious Word documents associated with this malspam.
SHA256 HASHES FOR THE MALSPAM ATTACHMENTS:
- 1d457069cb511af47a587287d59817148d404a2a7f39e1032d16094811f648e3 - CompanyReport.xlsm
- 75779e62f9790bd4c2ed449bd20be741f78811fb5ce848a2c5a516af17cdeccf - IncomingBACs.xlsm
- 9f6840709c15d7a2ed5c1d9502c23b122a639daa2c9cb6982a648b61b4789dca - NATWESTSecureMessage.html
- 51fc6482d1ab80010ebfe25d5b2a81c556235f4f541631589be49b3d9ac366af - PaymentAdvice.doc
- aa86a97ed059b08289199a9b9775040313b54b5ada19a501e5cf81553f7d0801 - Secure.doc
- 74f8f48afc7e761fa950e6656f178633f23dd02e207a7d20e0a873ca43778db8 - SecureCommunication.doc
- 08e3da6d2868bb292f81e3580b1686a34fc5c25051f2c9601671f35873688307 - SecureMessage-email-attachment.doc
- f77e4eebda4d50f76a4ad15f59f4f493928555e74fd680dd4a226121498c342d - SecureMessage-from-HTML-attachment.doc
- b9571aec8cc11b0596b02c6f76bc2802ed045be182e8748b904147534bef7e54 - West5476754-34.doc
SHA256 HASHES FOR THE TRICKBOT BINARIES I RECOVERED:
- 8ddad869f3b7bfa555890ee3cf503577e02c8599dd79b51dc458862f6f2843e7 - Trickbot binary from carriereiserphotography[.]com
- 2d40bc08e5b696b523b8ea9fe48cfd8294d279cf745b91a4b68dbed208facf1f - Trickbot binary from carriereiter[.]com
- 5da547e87d6ef12349fb4dbba9cf3146a358e284f72361dd07bbabfc95b0bac3 - Trickbot binary from usdata.estoreseller[.]com
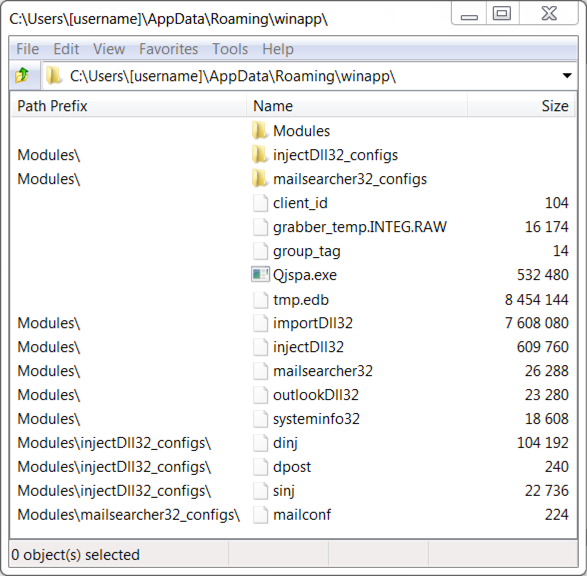
Shown above: Artifacts from an infected Windows host.
IMAGES
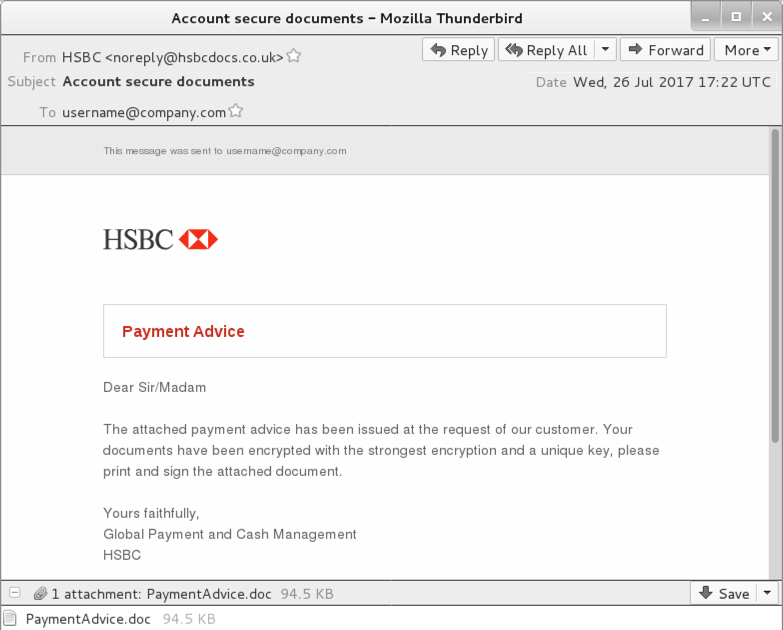
Shown above: Screenshot from one of the emails (1 of 8).
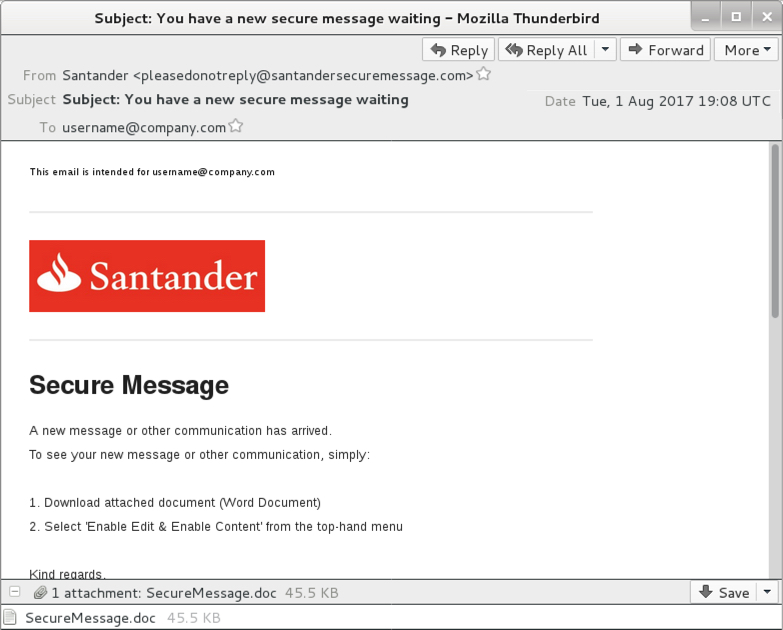
Shown above: Screenshot from one of the emails (2 of 8).
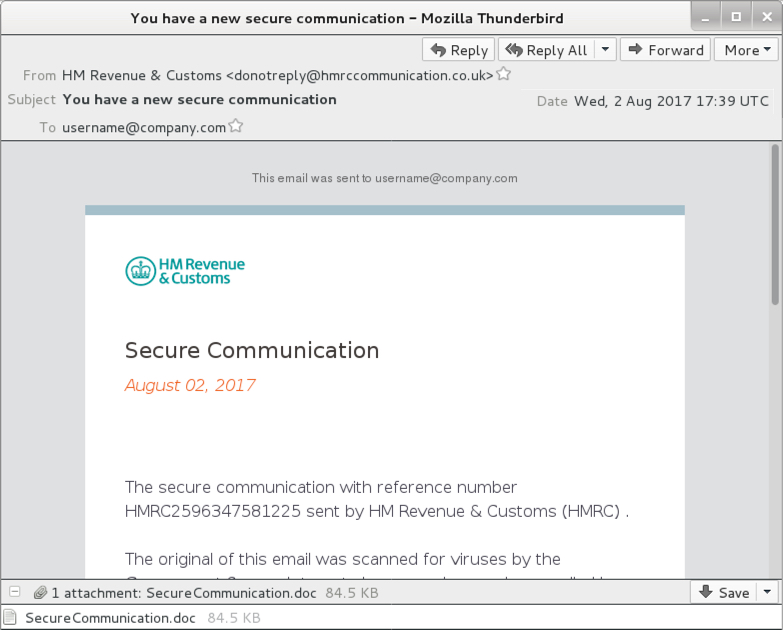
Shown above: Screenshot from one of the emails (3 of 8).
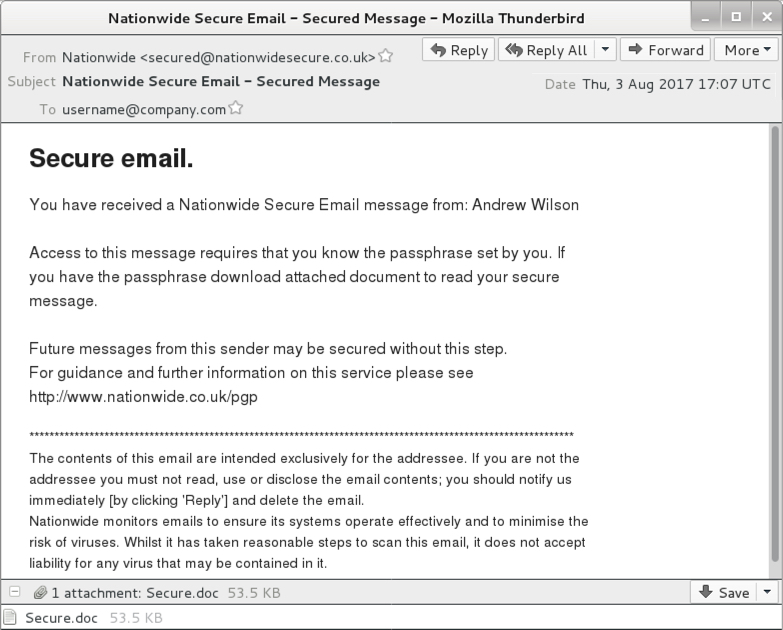
Shown above: Screenshot from one of the emails (4 of 8).

Shown above: Screenshot from one of the emails (5 of 8).
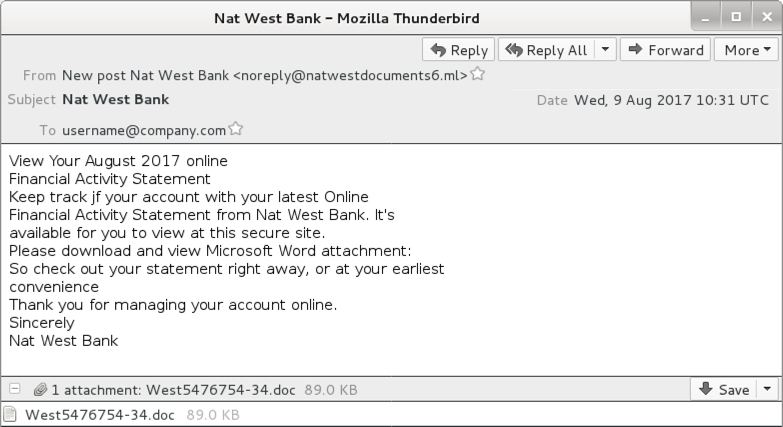
Shown above: Screenshot from one of the emails (6 of 8).
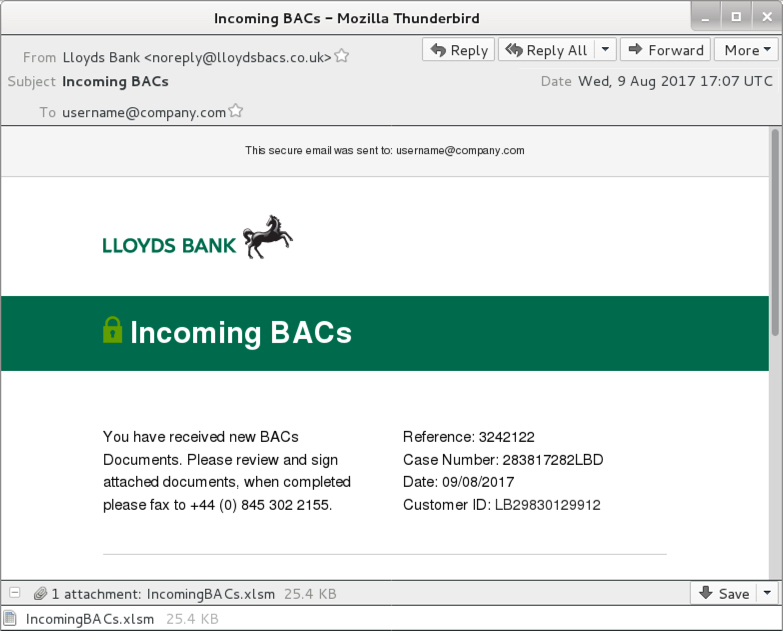
Shown above: Screenshot from one of the emails (7 of 8).
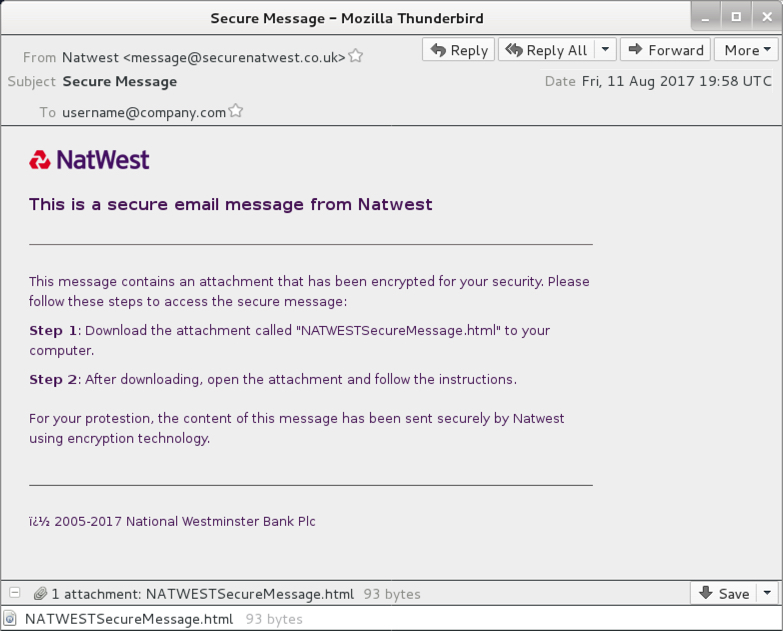
Shown above: Screenshot from one of the emails (8 of 8).
Click here to return to the main page.
