2017-08-19 - INFOSTEALER INFECTION FROM BRAZIL MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-08-19-infostealer-infection-from-Brazil-malspam.pcap.zip 7.1 MB (7,124,994 bytes)
- 2017-08-19-infostealer-infection-from-Brazil-malspam.pcap (7,476,902 bytes)
- 2017-08-19-email-and-malware-from-the-infection.zip 5.4 MB (5,388,436 bytes)
- 2017-08-18-Boleto-malspam-1953-UTC.eml (1,365 bytes)
- 2xmsnQhrfv30kvk.dll (2,857,872 bytes)
- BolProa000121594984151521000.exe (1,389,680 bytes)
- BolProa000121594984151521000.zip (1,331,113 bytes)
NOTES:
- Another Brazilian email using a goo[.]gl link to send a banking Trojan.
- This type of malware is often categorized as "Banload" by security vendors.
- Google services are still abused by this campaign.
- Follow-up malware was downloaded over HTTPS, requesting a JPG image that returned the second-stage DLL file.
- No alerts on the network traffic, because the malicious activity is sent over HTTPS.
EMAIL INFORMATION:
Date: Friday, 2017-08-18 at 19:53 UTC
From: [spoofed as recipient's email address]
Subject: Aviso de Inclusao De Protesto - [ 91046614 ]
Google translation of subject: Notice of Prohibition Inclusion - [ 91046614 ]
Link from the email: hxxps[:]//goo[.]gl/vRbyXM
MESSAGE TEXT:
Estimado Cliente(a),
Estou encaminhando para conhecimento a inclusão do protesto em cartório do boleto aqui especificado.
Boleto_PDF Visualizar Boleto
Este email foi escaneado pelo Avast antivirus.
GOOGLE TRANSLATION OF MESSAGE TEXT:
Dear Customer,
I am referring to the inclusion of the protest in the ticket office of the ticket specified here.
Boleto_PDF View Boleto
This email was scanned by Avast antivirus.
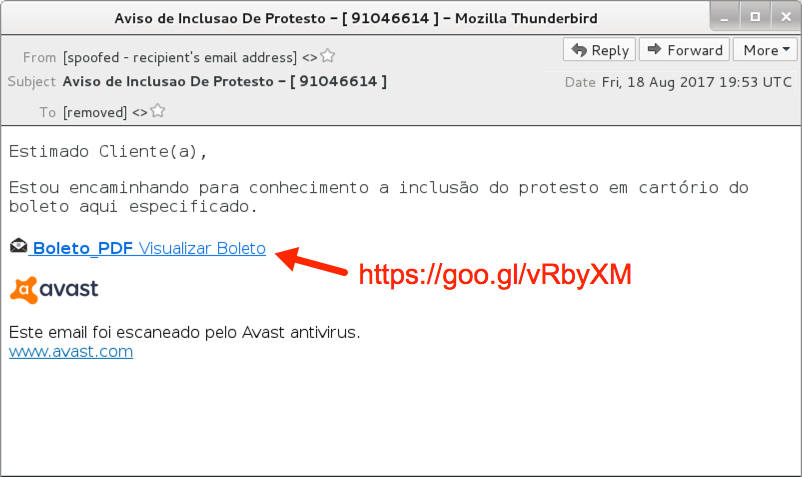
Shown above: Screenshot from the email.
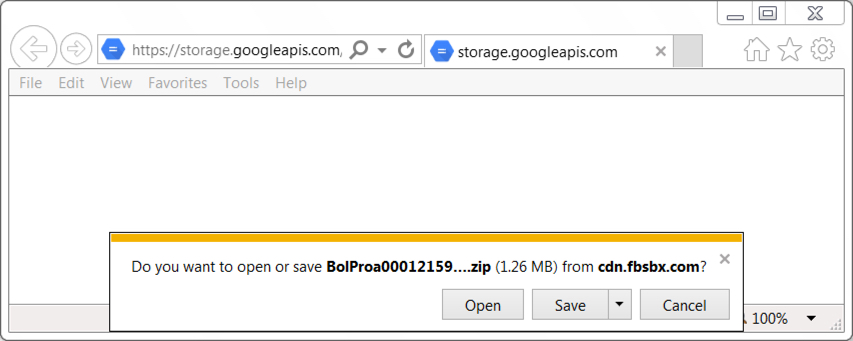
Shown above: Malicious zip archive after clicking link from the malspam.
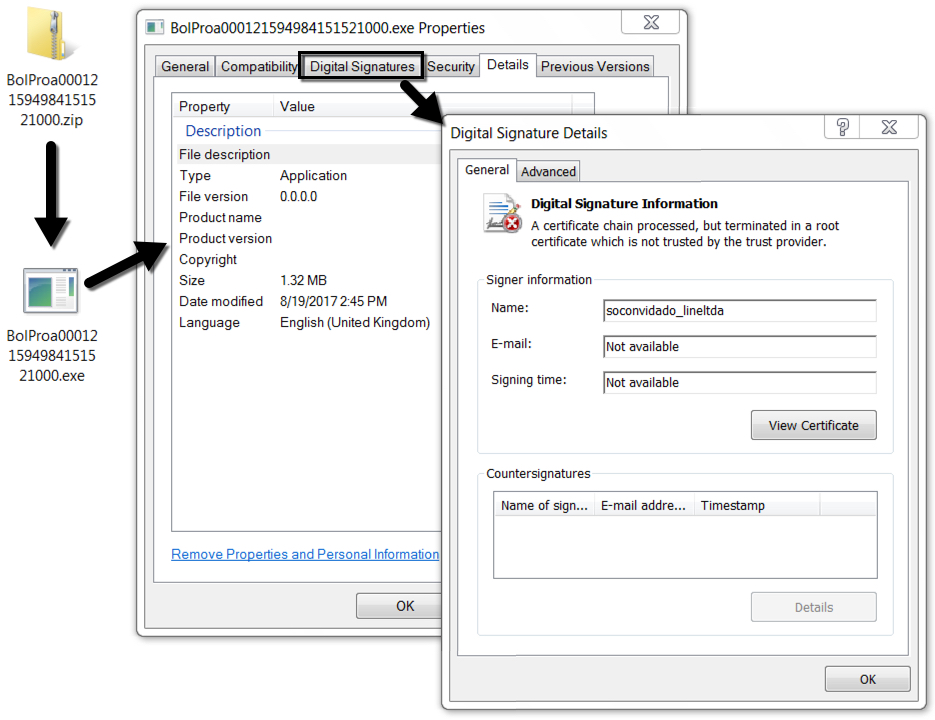
Shown above: Extracted malware from the zip archive.
TRAFFIC
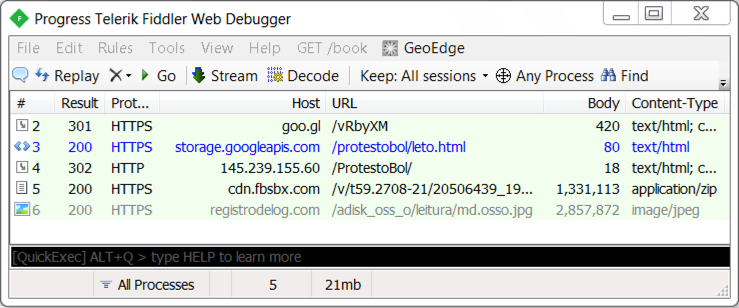
Shown above: Fiddler recording of the traffic.
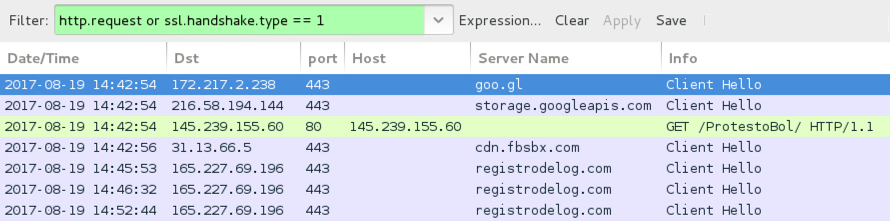
Shown above: Traffic from the infection filtered in Wireshark.
URLS FROM THE INFECTION TRAFFIC:
- hxxps[:]//goo[.]gl/vRbyXM
- hxxps[:]//storage.googleapis[.]com/protestobol/leto.html
- hxxp[:]//145.239.155[.]60/ProtestoBol/
- hxxps[:]//cdn.fbsbx[.]com/v/t59.2708-21/20506439_1939924152913224_6907918802093080576_n.zip/BolProa000121594984151521000.zip?oh=
762d01ee39f764e70d0fee266b70c42e&oe=59991CDB&dl=1 - hxxps[:]//registrodelog[.]com/adisk_oss_o/leitura/md.osso.jpg
FILE HASHES
ZIP ARCHIVE DOWNLOADED AFTER CLICKING LINK FROM THE EMAIL:
- SHA256 hash: 1ac4d7e04208223e039973a09c007340bda446767765abf2961af1128861d407
File name: BolProa000121594984151521000.zip
File size: 1,331,113 bytes
EXTRACTED BINARY FROM ZIP ARCHIVE:
- SHA256 hash: 1c9009663d4acbc9314d429a67365341ab76ce6313967429f8ebfc9113ee7ac3
File name: BolProa000121594984151521000.exe
File size: 1,389,680 bytes
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: e14d5ed13f991a62b911d84a4b762d33c8b28af4c3c5e854d271b9a62c538087
File location: hxxps[:]//registrodelog[.]com/adisk_oss_o/leitura/md.osso.jpg
File location: C:\Users\[username]\AppData\Roaming\2xmsnQhrfv30kvk.dll
File size: 2,857,872 bytes
WINDOWS REGISTRY UPDATE
- Key name: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Value: DGD95I9D
- Type: REG_SZ
- Data: cmd.exe /c start rundll32.exe C:\Users\[username]\AppData\Roaming\2xmsnQhrfv30kvk.dll,PontoEntraKL
IMAGES
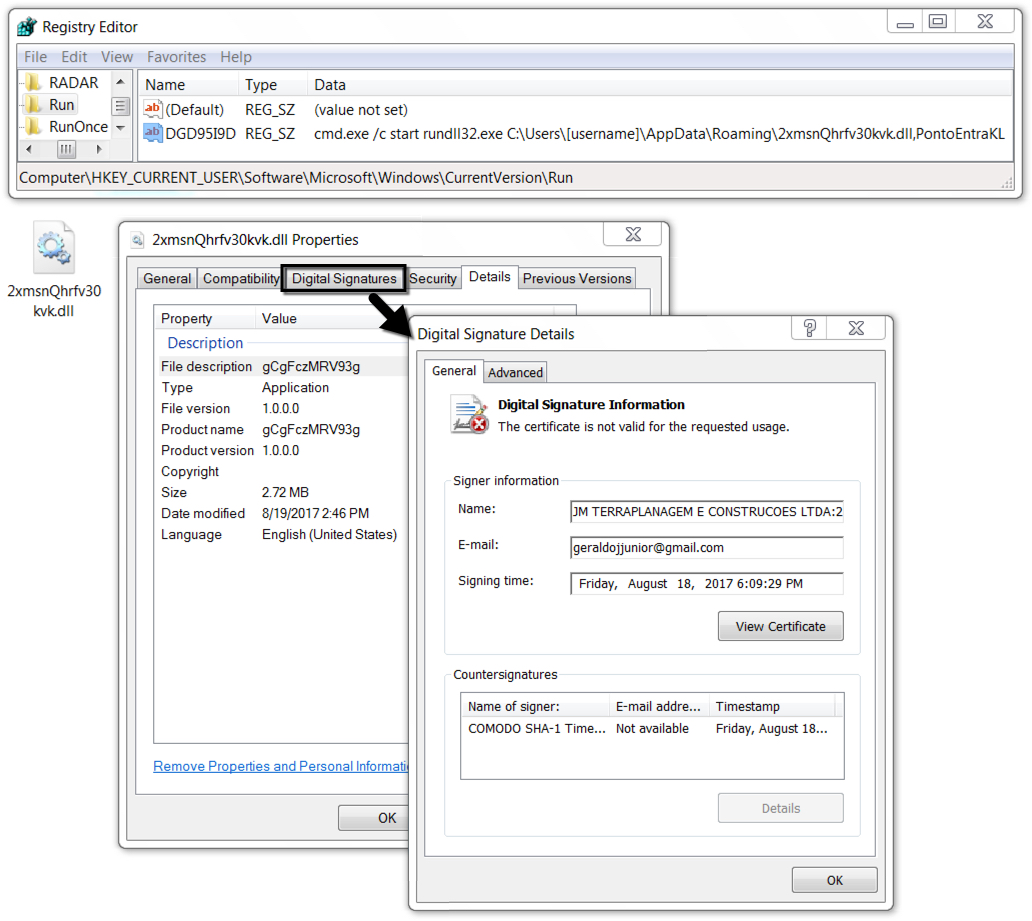
Shown above: Malware persistent on the infected host.
Click here to return to the main page.
