2017-08-21 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcap: 2017-08-21-Hancitor-infection-with-ZLoader.pcap.zip 8.5 MB (8,486,810 bytes)
- 2017-08-21-Hancitor-infection-with-ZLoader.pcap (9,174,063 bytes)
- 2017-08-21-Hancitor-malspam-3-examples.zip 3.7 kB (3,653 bytes)
- 2017-08-21-Hancitor-malspam-1640-UTC.eml (1,836 bytes)
- 2017-08-21-Hancitor-malspam-1709-UTC.eml (1,832 bytes)
- 2017-08-21-Hancitor-malspam-1902-UTC.eml (1,836 bytes)
- 2017-08-21-malware-from-Hancitor-infection.zip 233.9 kB (233,911 bytes)
- UPS_Slip_623040.doc (200,192 bytes)
- gokes.exe (180,224 bytes)
TODAY'S TWEETS COVERING THE 2017-08-21 WAVE OF #HANCITOR MALSPAM:
- @cheapbyte: #hancitor #ioc #malspam Hancitor Fake UPS phishing email August 21, 2017 URLs via Ghostbin (link)
- @Ring0x0: Receiving #Hancitor variant v4 #malspam with subject "Delivery stopped for shipment #[0-9]{6}" downloads UPS_Slip_xxxxxx.doc (link)
- @James_inthe_box: Incoming varient 4 #hancitor run "Your document Invoice <digits> is ready to be signed!" [Ghostbin link] (link)
EMAILS
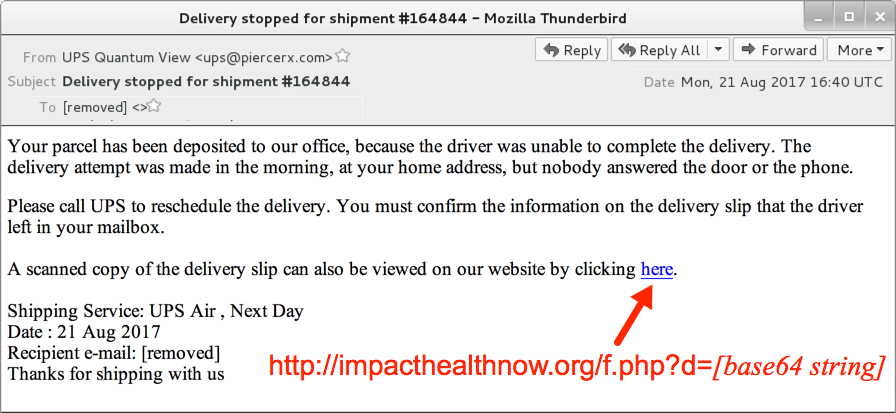
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date: Monday 2017-08-21 as early as 16:40 UTC through at least 19:02 UTC
- From: "UPS Quantum View" <ups@piercerx[.]com>
- Delivery stopped for shipment #142384
- Delivery stopped for shipment #164844
- Delivery stopped for shipment #650321
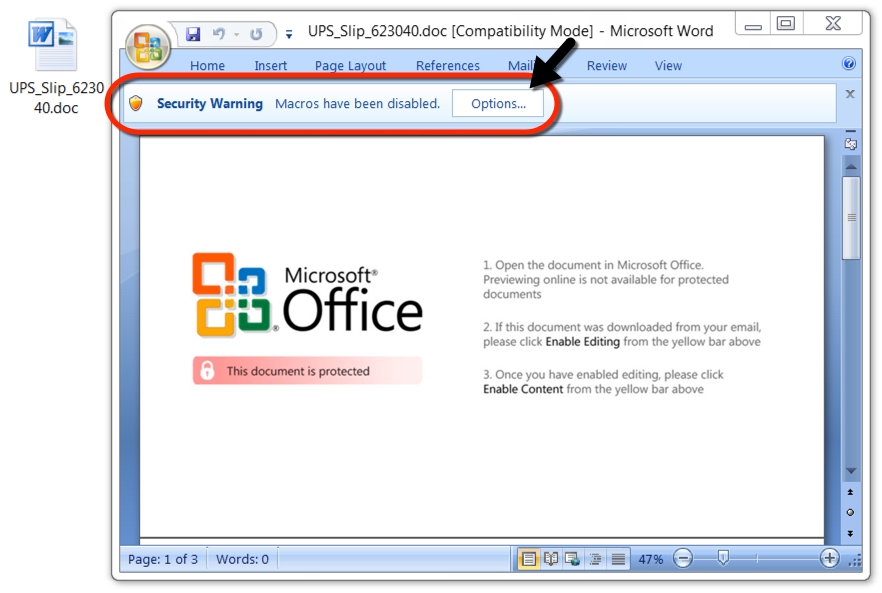
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
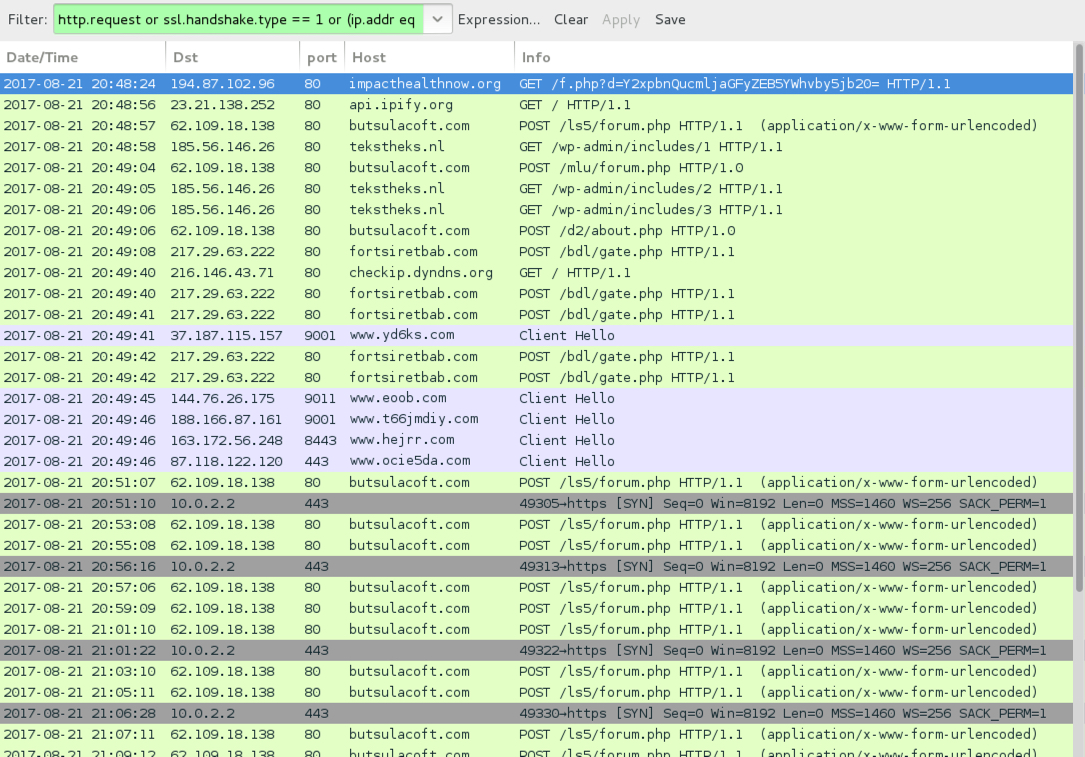
Shown above: Traffic from the infection filtered in Wireshark.
LINKS IN THE EMAILS THE WORD DOCUMENT:
- impacthealthnow[.]net - GET /f.php?d=[base64 string]
- impacthealthnow[.]org - GET /f.php?d=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENT:
- UPS_Slip_[six random digits].doc
POST-INFECTION TRAFFIC FROM MY INFECTED HOST:
- 62.109.18[.]138 port 80 - butsulacoft[.]com - POST /ls5/forum.php
- 62.109.18[.]138 port 80 - butsulacoft[.]com - POST /mlu/forum.php
- 62.109.18[.]138 port 80 - butsulacoft[.]com - POST /d2/about.php
- 185.56.146[.]26 port 80 - tekstheks[.]nl - GET /wp-admin/includes/1
- 185.56.146[.]26 port 80 - tekstheks[.]nl - GET /wp-admin/includes/2
- 185.56.146[.]26 port 80 - tekstheks[.]nl - GET /wp-admin/includes/3
- 217.29.63[.]222 port 80 - fortsiretbab[.]com - POST /bdl/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
- 10.0.2.2 port 443 - TCP SYN segment approx once every 5 minutes
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: ab90ed6cb461f17ce1f901097a045aba7c984898a0425767f01454689698f2e9
File name: UPS_Slip_623040.doc
File size: 200,192 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 879b244120400083f562ce530c87001b46de4fc96b38a6b12a5afea22ef6efef
File location: C:\Users\[username]\AppData\Local\Temp\BN6A37.tmp
File location: C:\Users\[username]\AppData\Roaming\Goom\gokes.exe
File size: 180,224 bytes
File description: DELoader/ZLoader
IMAGES
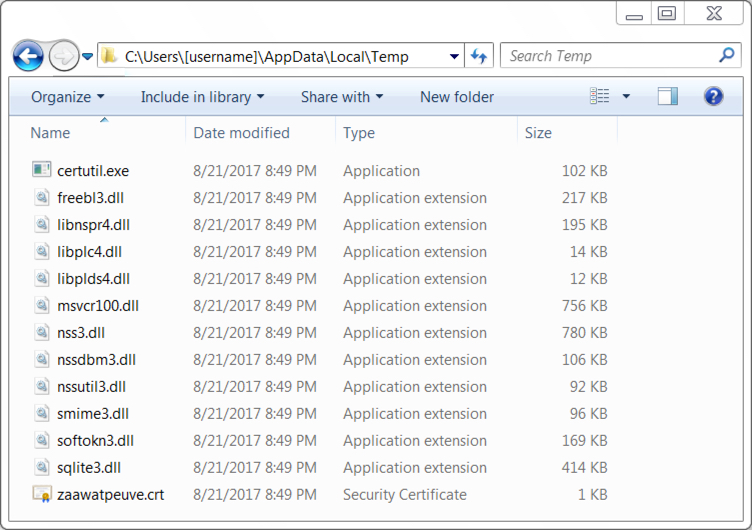
Shown above: Artifacts from the infected host in the user's AppData\Local\Temp directory.
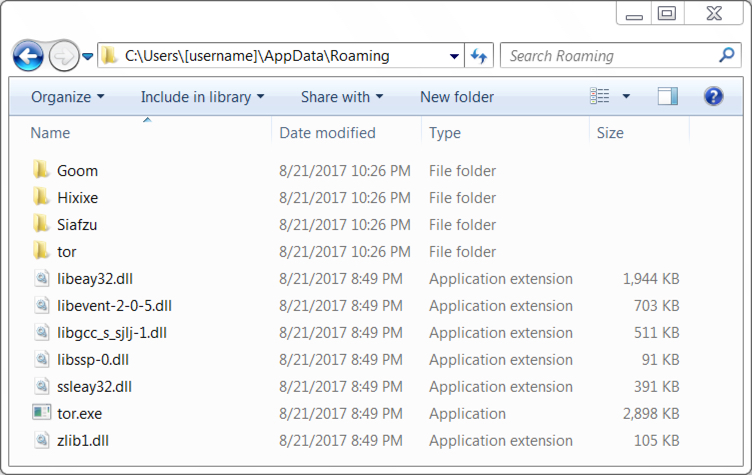
Shown above: Artifacts from the infected host in the user's AppData\Roaming directory.
Click here to return to the main page.
