2017-08-25 - SEAMLESS CAMPAIGN RIG EK SENDS RAMNIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-08-25-Seamless-campaign-Rig-EK-sends-Ramnit.pcap.zip 894 kB (893,960 bytes)
- 2017-08-25-Seamless-campaign-Rig-EK-sends-Ramnit.pcap (959,167 bytes)
- 2017-08-25-Seamless-campaign-Rig-EK-malware-and-artifacts.zip 283.6 kB (283,567 bytes)
- 2017-08-25-194.58.40_48-signu4.php.txt (328 bytes)
- 2017-08-25-Rig-EK-artifacts-o32.tmp.txt (1,141 bytes)
- 2017-08-25-Rig-EK-flash-exploit.swf (14,679 bytes)
- 2017-08-25-Rig-EK-landing-page.txt (122,438 bytes)
- 2017-08-25-Seamless-campaign-Rig-EK-payload-Ramnit.exe (288,256 bytes)
TRAFFIC
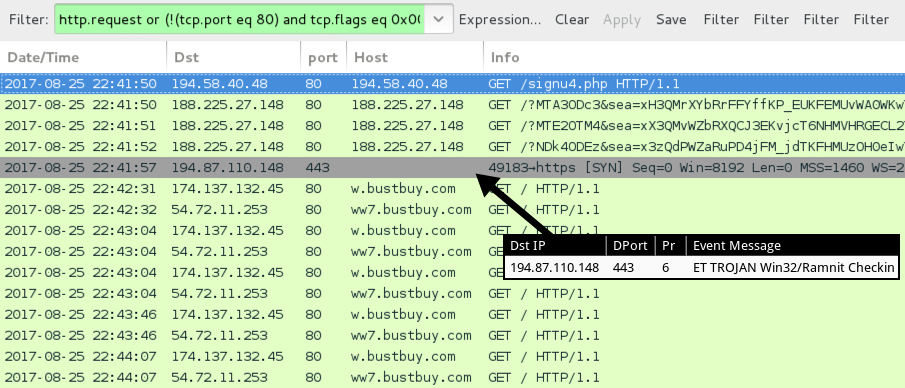
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 194.58.40[.]48 port 80 - 194.58.40[.]48 - GET /signu4.php [Seamless campaign gate]
- 188.225.27[.]148 port 80 - 188.225.27[.]148 - Rig EK
- 194.87.110[.]148 port 443 - encrypted traffic (not HTTPS/SSL/TLS) [Ramnit post-infection traffic]
- 174.137.132[.]45 port 80 - w.bustbuy[.]com - GET / [post-infection traffic from the infected Windows host]
- 54.72.11[.]253 port 80 - ww7.bustbuy[.]com - GET / [post-infection traffic from the infected Windows host]
FILE HASHES
RIG EK FLASH EXPLOIT:
- SHA256 hash: 0f6a98038d73293c55e551d14751ec99ebf03d197a299a7bedc53cc5f9f059e1
File size: 14,679 bytes
File description: Rig EK flash exploit seen on 2017-08-25
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 48d89a7362109171bcb16ac5e851f17807fe7b0cc855082d1069b6521906582d
File location: C:\Users\[username]\AppData\Local\Temp\[random characters].exe
File size: 288,256 bytes
File description: Ramnit
Click here to return to the main page.
