2017-08-28 - FOBOS CAMPAIGN RIG EK SENDS BUNITU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcap: 2017-08-28-Fobos-campaign-Rig-EK-sends-Bunitu.pcap.zip 527.1 kB (527,142 bytes)
- 2017-08-28-Fobos-campaign-Rig-EK-sends-Bunitu.pcap (595,648 bytes)
- Zip archive of the malware: 2017-08-28-Fobos-campaign-Rig-EK-malware-and-artifacts.zip 178.0 kB (178,031 bytes)
- 2017-08-28-Fobos-campaing-Rig-EK-payload-Bunitu.exe (252,928 bytes)
- 2017-08-28-Rig-EK-flash-exploit.swf (14,673 bytes)
- 2017-08-28-Rig-EK-landing-page.txt (61,637 bytes)
- 2017-08-28-gamebingfree.info.txt (17,123 bytes)
- 2017-08-28-text-returned-from-212jhhhvvhhvvhv_cf.txt (540 bytes)
TRAFFIC
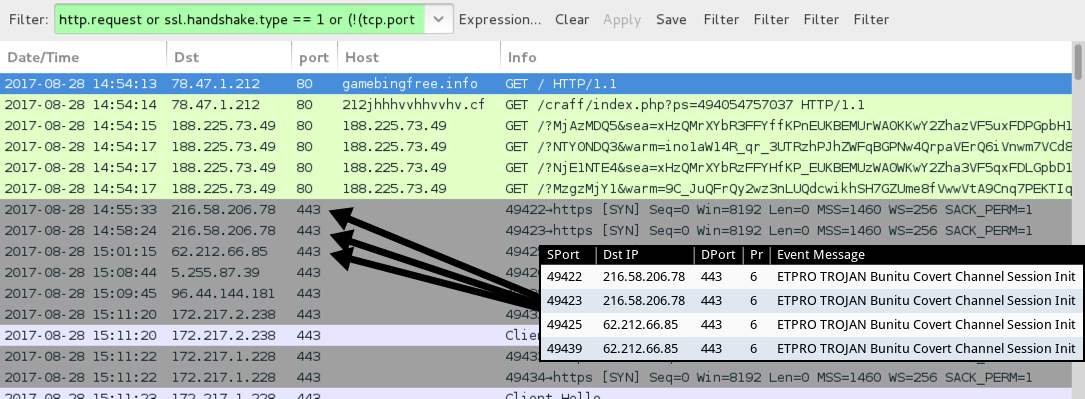
Shown above: Traffic from the infection filtered in Wireshark focusing on Bunitu post-infection traffic.
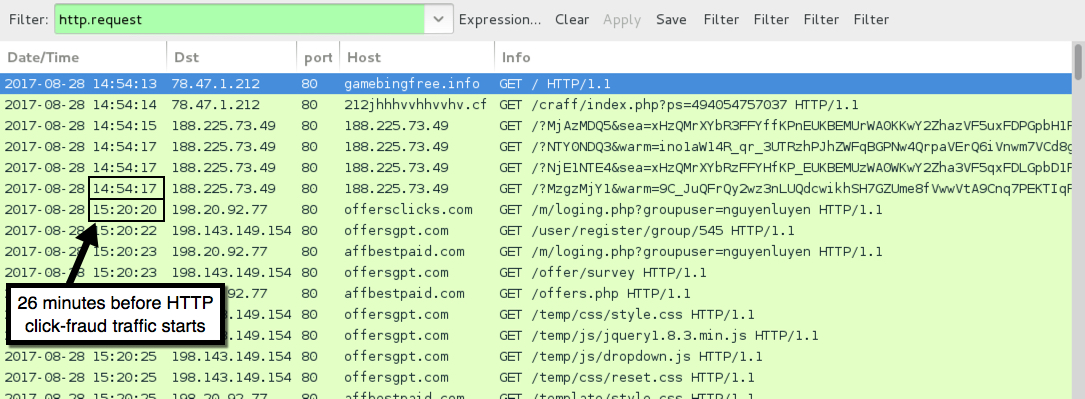
Shown above: Traffic from the infection filtered in Wireshark showing HTTP click-fraud traffic.
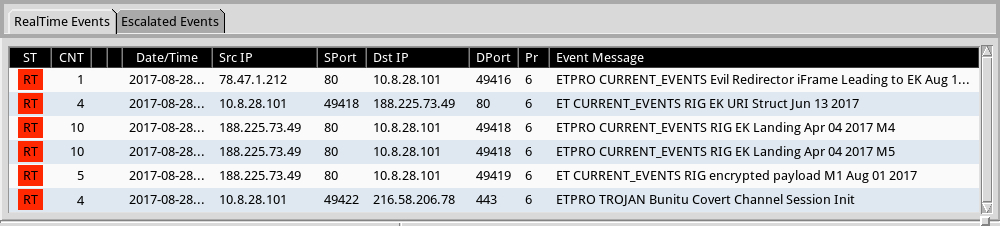
Shown above: Some alerts on the traffic from the Emerging Threats and ETPRO rulesets using Sguil and tcpreplay on Security Onion.
ASSOCIATED DOMAINS:
- 78.47.1[.]212 port 80 - gamebingfree[.]info - Domain used by Fobos campaign
- 78.47.1[.]212 port 80 - 212jhhhvvhhvvhv[.]cf - GET /craff/index.php?ps=494054757037 [redirect/gate]
- 188.225.73[.]49 port 80 - 188.225.73[.]49 - Rig EK
- 216.58.206[.]78 port 443 - 216.58.206[.]78 - Bunitu post-infection traffic (encrypted)
- 62.212.66[.]85 port 443 - 62.212.66[.]85 - Bunitu post-infection traffic (encrypted)
- Various IP addresses port 80 and 443 - various domains - Post-infection click-fraud traffic
FILE HASHES
RIG EK FLASH EXPLOIT:
- SHA256 hash: 79110cca9c884606f8c753c76a6a25ba1933ff2f98add2f2f8977b020baf9aab
File size: 14,673 bytes
File description: Rig EK flash exploit seen on 2017-08-28
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 9b7a49b36e7900286e9f371894557f081204b313085a7e03199ede054cfbf6c0
File location: C:\Users\[username]\AppData\Local\Temp\[random characters].exe
File size: 252,928 bytes
File description: Bunitu
Click here to return to the main page.
