2017-09-04 - GLOBEIMPOSTER RANSOMWARE (..TXT FILE EXTENSIONS)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-04-GlobeImposter-ransomware-infection.pcap.zip 256.3 kB (256,302 bytes)
- 2017-09-04-GlobeImposter-malspam-tracker.csv.zip 1.2 kB (1,229 bytes)
- 2017-09-04-GlobeImposter-ransomware-emails-and-malware.zip 406.3 kB (406,297 bytes)
NOTES:
- Gather here are 10 examples of malicious spam (malspam) from Monday 2017-09-04 pushing GlobeImposter ransomware.
- Many have already seen examples and tweeted about this.
EMAILS
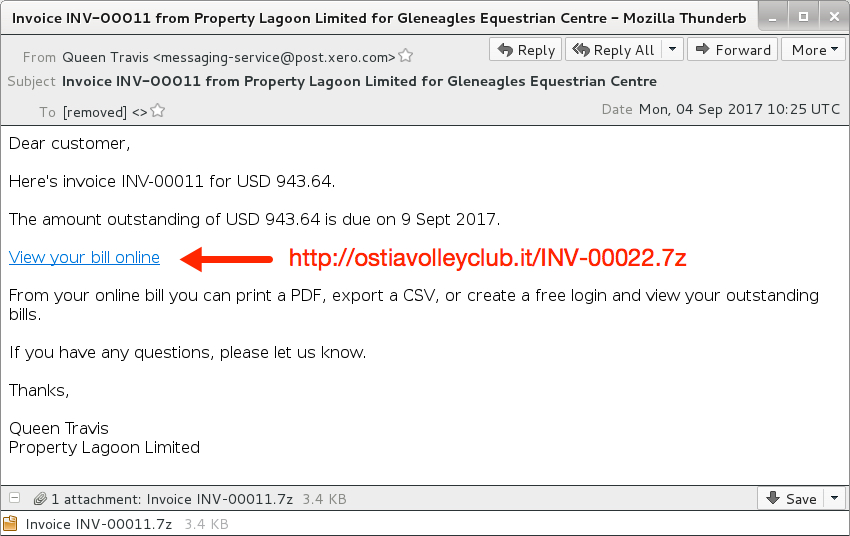
Shown above: Screenshot from one of today's emails in the first wave.
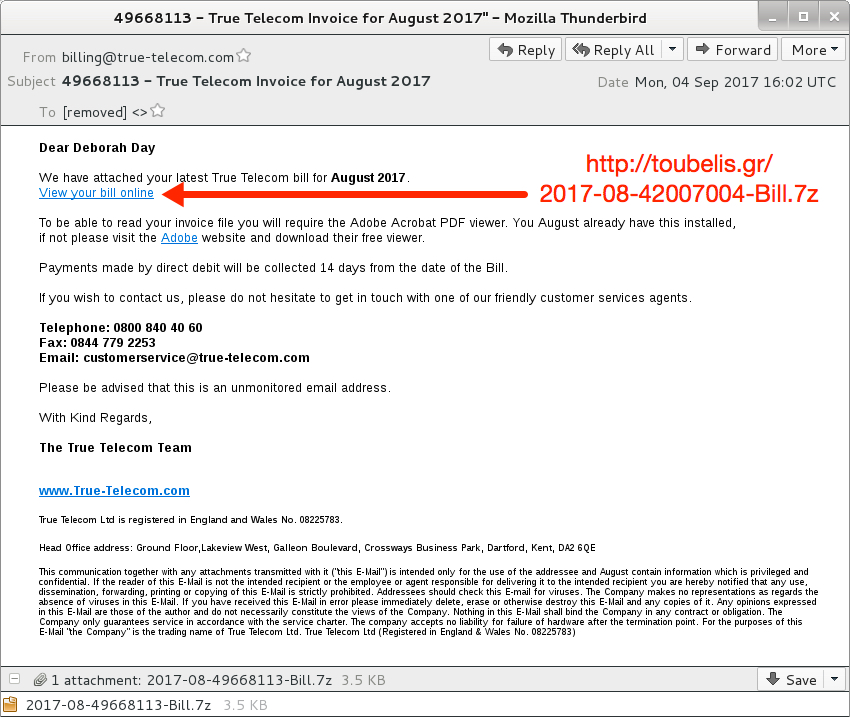
Shown above: Screenshot from one of today's emails in the second wave.
FIRST WAVE:
- From: [random first and last name] <messaging-service@post.xero[.]com>
- Subject: Invoice INV-00031 from Property Lagoon Limited for Gleneagles Equestrian Centre
- Subject: Invoice INV-00024 from Property Lagoon Limited for Gleneagles Equestrian Centre
- Subject: Invoice INV-00011 from Property Lagoon Limited for Gleneagles Equestrian Centre
- Subject: Invoice INV-000757 from Property Lagoon Limited for Gleneagles Equestrian Centre
- Subject: Invoice INV-00077 from Property Lagoon Limited for Gleneagles Equestrian Centre
SECOND WAVE:
- From: billing@true-telecom[.]com
- Subject: 62403078 - True Telecom Invoice for August 2017
- Subject: 52838405 - True Telecom Invoice for August 2017
- Subject: 46483802 - True Telecom Invoice for August 2017
- Subject: 75117968 - True Telecom Invoice for August 2017
- Subject: 46483802 - True Telecom Invoice for August 2017
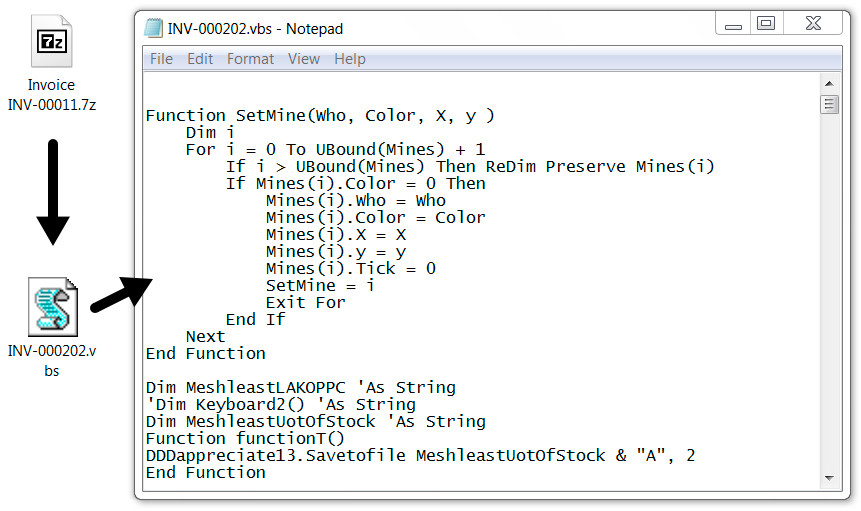
Shown above: An attachment from one of today's emails in the first wave.
TRAFFIC
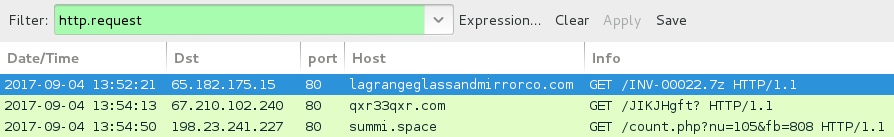
Shown above: Traffic from an infection filtered in Wireshark.
LINKS FROM THE EMAILS TO DOWNLOAD 7-ZIP ARCHIVE:
- aac-autoecole[.]com - GET /2017-08-42007004-Bill.7z
- activ-conduite[.]eu - GET /2017-08-42007004-Bill.7z
- allsexfinder[.]com - GET /INV-00022.7z
- autoecolecarnot[.]com - GET /2017-08-42007004-Bill.7z
- brandingforbuyout[.]com - GET /INV-00022.7z
- dev.lowndespartnership[.]co[.]uk - GET /INV-00022.7z
- montessibooks[.]com - GET /2017-08-42007004-Bill.7z
- ostiavolleyclub[.]it - GET /INV-00022.7z
- rogames[.]ro - GET /2017-08-42007004-Bill.7z
- studiotoscanosrl[.]it - GET /2017-08-42007004-Bill.7z
- weekendjevliegen[.]nl - GET /2017-08-42007004-Bill.7z
- yamanashi-jyujin[.]jp - GET /INV-00022.7z
URLS TO DOWNLOAD GLOBEIMPOSTER RANSOMWARE:
- animatoon[.]be - GET /JIKJHgft?
- aquavista[.]org[.]nz - GET /JIKJHgft?
- awholeblueworld[.]com - GET /JIKJHgft?
- brownpa[.]net - GET /JIKJHgft?
- cabbiemail[.]com - GET /JIKJHgft?
- clubdeautores[.]es - GET /JIKJHgft?
- dueeffepromotion[.]com - GET /JIKJHgft?
- hellonwheelsthemovie[.]com - GET /JIKJHgft?
- jimaylor[.]net - GET /JIKJHgft?
- m-tensou[.]net - GET /JIKJHgft?
- naturofind[.]org/p66 - GET /JIKJHgft
- n1xua[.]com - GET /JIKJHgft?
- prescottinternet[.]net - GET /JIKJHgft?
- qxr33qxr[.]com - GET /JIKJHgft?
- uvitacr[.]com - GET /JIKJHgft?
- world-tour2000[.]com - GET /JIKJHgft?
DOMAINS/URLS ASSOCIATED WITH THE POST-INFECTION TRAFFIC:
- summi[.]space
- n224ezvhg4sgyamb[.]onion - GET /sup.php
SHA256 HASHES
tATTACHMENTS OR FILES DOWNLOADED FROM EMAIL LINKS (7-ZIP ARCHIVES):
- d37a63c7aae785fb712ffe3b449493f103730b28b40b693dac383407bcfea715 - 2017-08-42007004-Bill.7z
- 46b565c7c71e97d78d8a386dbcc9a5fea9fcd00580ae6a36e0ac819aa882a7f6 - 2017-08-46483802-Bill.7z
- 7bb4204d103eafd78402f6c2574c7db4ecc0508fbcc07425912827f4721458a9 - 2017-08-49668113-Bill.7z
- 60b6f8dade147659b677373a0ac4397df0e20399d2f15ed4a8a507810ebab1e9 - 2017-08-52838405-Bill.7z
- 8173a961cce2022ab961d2915dc6e520868bc5dc6708b0028ebe5e1b8a1b6ca9 - 2017-08-62403078-Bill.7z
- 654c207016188074ed6087b9c03c678437855418166d488f87210407715d4c1b - 2017-08-75117968-Bill.7z
- 133ea29b57557971961634ae8e478c475b7fae796607a88b100f014d9ad53888 - INV-00022.7z
- dc015e4d0677fabf508f34db3dd1c3f7a8a21b9646f1d2da37a2c2ef14cc6441 - Invoice INV-00011.7z
- d9c2b465d78843894f47a800146acbe90b68fc3baae2f0ae29a9ef0030806d72 - Invoice INV-00024.7z
- c72623f685d4b8a9495d9dacb25cd8cdf702a6bb84b5f95392c0c34a8c4b4e3f - Invoice INV-00031.7z
- b8cb0014419bd473aeaa365ac057ab9c5e196d44ea3601630d3177346f46b627 - Invoice INV-000757.7z
- e33624b52f8c3e9bab0debf9a204189fe16368837063472766387d2381ecfa35 - Invoice INV-00077.7z
EXTRACTED VBS FILES:
- 02d21039f8a1ffe8788edca8d01acd1f6d0561826322089ce64d37ee173bcfe2 - 2017-08-22312958-Bill.vbs
- 5c6df934315ae00fd743316bb7fb9eaa6d92d4eebf6c2143cdc2ec104d66b111 - 2017-08-38858815-Bill.vbs
- 39256f126bba17770310c2115586b9f22b858cf15c43ab36bd7cfb18ad63a0c2 - 2017-08-42007004-Bill.vbs
- a93b0a27fb994d3ad87fd86b0a43c93544b6b19fbad7a168ffa5106281a53532 - 2017-08-57344042-Bill.vbs
- 14f4aeedf83280c6ae57300e88c30f1594f9f4a3062cf6d757ff0a527a5fe28c - 2017-08-62810134-Bill.vbs
- c7a9b86a4d0c4e8771e07c04acd7cdb919e7942c6a4591a80d14c10044a80c6c - 2017-08-66176566-Bill.vbs
- 544ee491d507cef91c68e3cd71ff5201a3b57b98fe3b4fa5191e78e6984cd754 - INV-000176.vbs
- 6324a66785b164fa41fc43d7fb181d45a1d63de706eb78b1fde83904015db3fc - INV-000202.vbs
- 0f6ae637a9d15503a0af42be649388f01f8637ca16b15526e318a94b7f34bf6e - INV-00022.vbs
- 2d2412670ad4e59dc67fdfaa4c37e93f5c71ba4c8ed0b4dfabae032e939cdb99 - INV-000471.vbs
- ff86b878d7a458fb54c67aad2bb3eea0fa688992bf9e756670483a704669f1d9 - INV-000751.vbs
- be16144c57d8161b93551bf73b39ad03d43c0139ab2040b84fe0318504ec166e - INV-000913.vbs
GLOBEIMPOSTER EXE SAMPLE DOWNLOADED BY VBS FILES:
- SHA256 hash: bb1df4a93fc27c54c78f84323e0ea7bb2b54469893150e3ea991826c81b56f47
File size: 253,440 bytes
File description: GlobeImposter sample from 2017-09-04
IMAGES
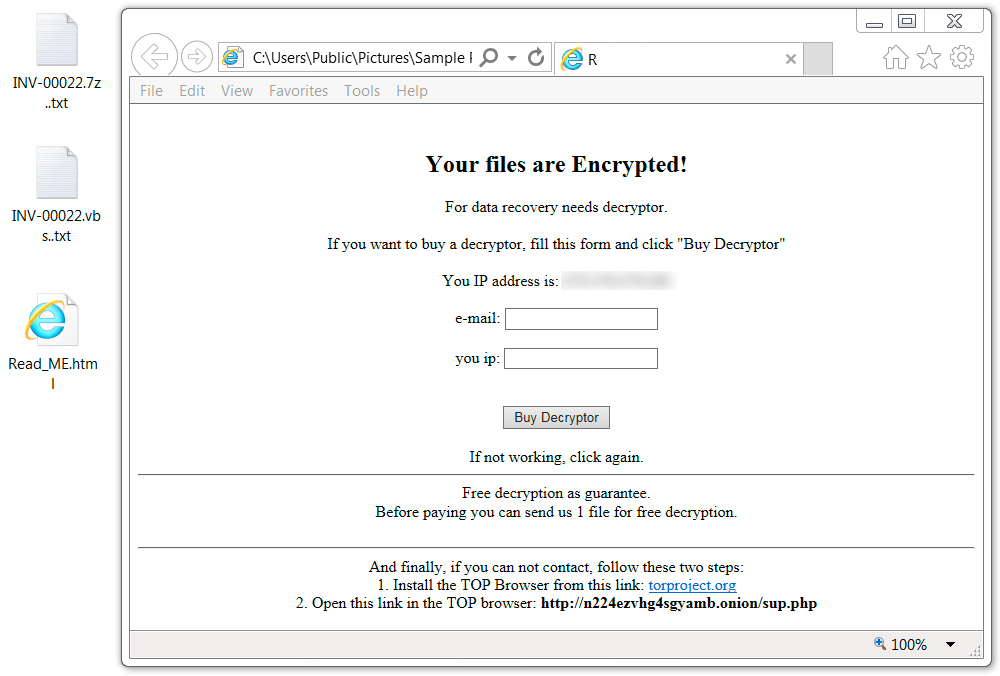
Shown above: All encrypted files ended with ..txt.
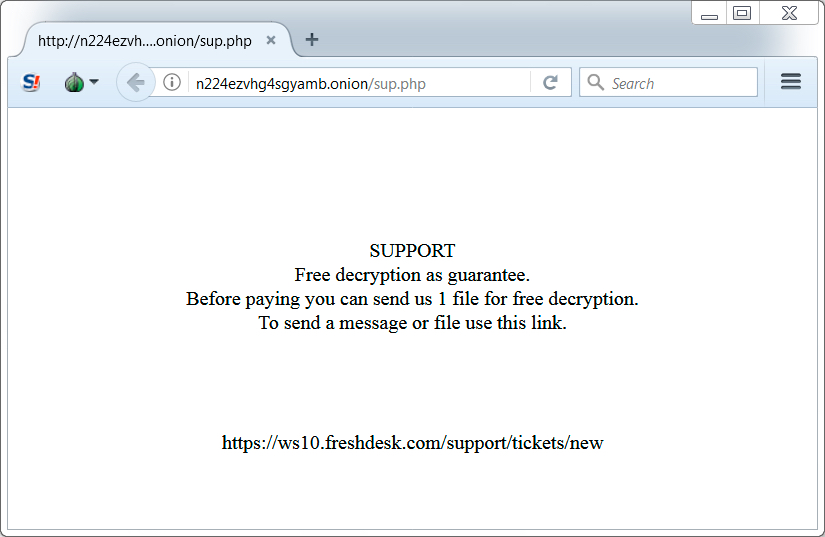
Shown above: Tor URL from the decryption instructions.
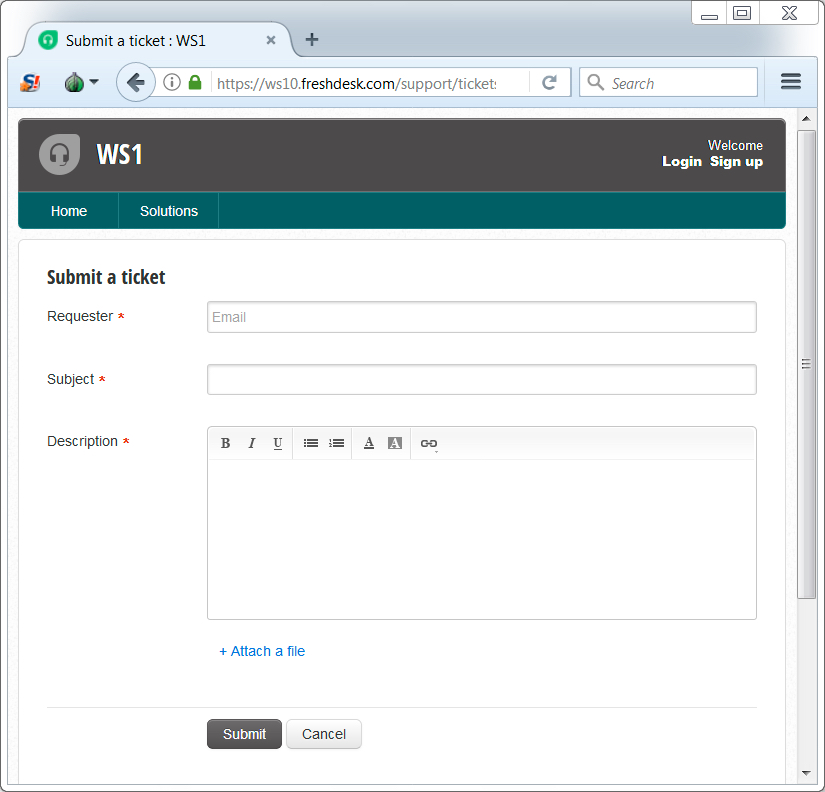
Shown above: Freshdesk support ticket the criminals are using, so you can send them a sample to decrypt.
Click here to return to the main page.
