2017-09-04 - INFOSTEALER INFECTION FROM BRAZIL MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-04-Brazil-infostealer-infection-traffic.pcap.zip 9.9 MB (9,850,116 bytes)
- 2017-09-04-Brazil-infostealer-infection-traffic.pcap (10,319,541 bytes)
- 2017-09-04-Brazil-malspam-1624-UTC.eml.zip 1.0 kB (963 bytes)
- 2017-09-04-Brazil-malspam-1624-UTC.eml (1,233 bytes)
- 2017-09-04-malware-from-Brazil-infostealer-infection.zip 7.2 MB (7,173,594 bytes)
- 2017-09-04-scheduled-task-for-persistence.txt (3,334 bytes)
- BITCE84.tmp.exe (1,513,064 bytes)
- MD114244.exe (5,485,568 bytes)
- mosdhjkfi.cab (3,976,749 bytes)
- wcntiqav.exe (881,152 bytes)
EMAIL INFORMATION:
- DateTime: Monday, 2017-09-04 as early as 15:14 UTC through at least 16:24 UTC
- Received: from PC-2017PC ([189.63.127[.]9])
- From: (probably spoofed) anne.matos@flexcontact[.]com[.]br
- Link in the email: hxxp[:]//pilateseterapiasmb[.]com[.]br/wp-content/themes/accesspressray-pro/wcntiqav.zip
- Various subject lines, depending on the time sent
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 13:24:06
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 13:21:24
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 13:18:25
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 13:17:09
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 12:52:00
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 13:01:33
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 12:55:25
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 12:47:04
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 12:38:44
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 12:19:00
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 12:18:31
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 12:17:59
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 12:17:39
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 12:16:06
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 12:15:26
- Subject: Crt: 386 / Oper: 2557 / Contrato: 5213706677228235 / Vcto: 31/08/2017 - BV 04/09/2017 12:14:05
MESSAGE TEXT:
Bom Dia/ Boa Tarde
Segue em anexo a solicitação do boleto referente ao Banco Votorantim na data vigente, aguardamos o envio do comprovante a partir deste e-mail ou pelo nosso Whatsapp (11)97154-8482 .
Crt: 386 / Oper: 10514 / Contrato: 5213706677228235
Atenciosamente,
Contact Center . Crédito . Cobrança Anne Matos Backoffice 0800 770 2482 / (11) 2739 – 3007 / Whatsapp (11) 97154-8482
Email: anne.matos@flexcontact[.]com[.]br
GOOGLE TRANSLATION OF MESSAGE TEXT:
Good day/good afternoon
Attached is the request of the ticket for Banco Votorantim on the current date, we await the sending of the receipt from this e-mail or our Whatsapp (11) 97154-8482.
Crt: 386 / Oper: 10514 / Contract: 5213706677228235
Regards,
Contact Center. Credit . Collection Anne Matos Backoffice 0800 770 2482 / (11) 2739 - 3007 / Whatsapp (11) 97154-8482
Email: anne.matos@flexcontact[.]com[.]br
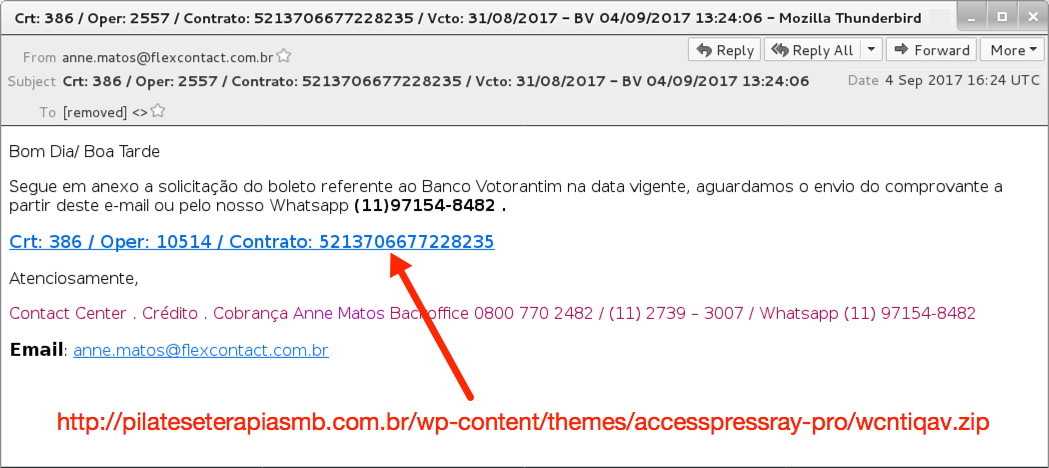
Shown above: Screenshot from the email.
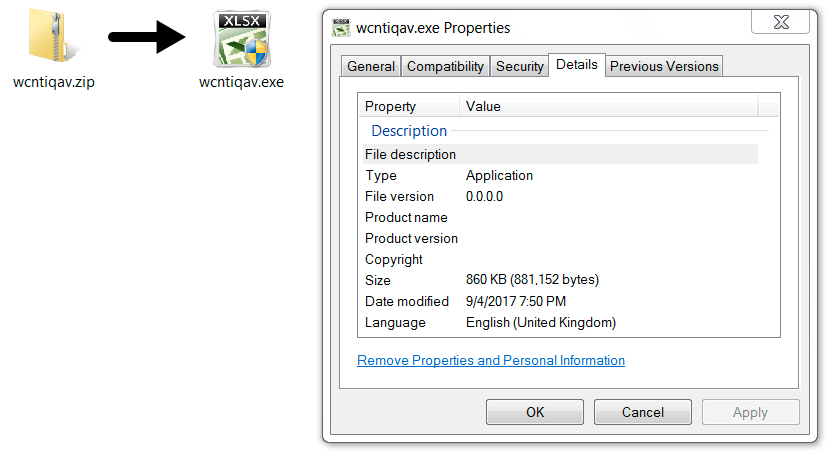
Shown above: Malicious zip archive from link in the malspam.
TRAFFIC
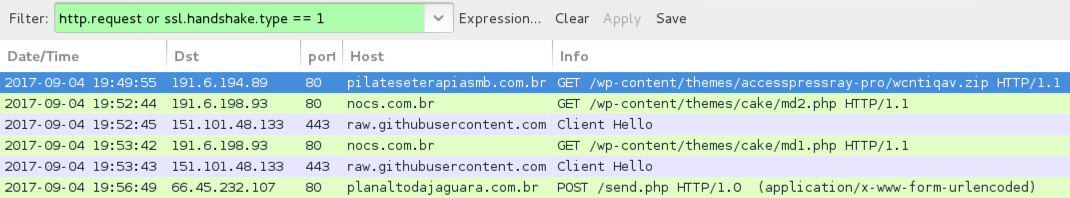
Shown above: Pcap of the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- 191.6.194[.]89 port 80 - pilateseterapiasmb[.]com[.]br - GET /wp-content/themes/accesspressray-pro/wcntiqav.zip
- 191.6.198[.]93 port 80 - nocs[.]com[.]br - GET /wp-content/themes/cake/md2.php
- port 443 - raw.githubusercontent[.]com - GET /mozdevfirefox/installf/master/install.exe [HTTPS]
- 191.6.198[.]93 port 80 - nocs[.]com[.]br - GET /wp-content/themes/cake/md1.php
- port 443 - raw.githubusercontent[.]com - GET /mozdevfirefox/installf/master/mosdhjkfi.cab [HTTPS]
- 66.45.232[.]107 port 80 - planaltodajaguara[.]com[.]br - POST /send.php
FILE HASHES
ZIP ARCHIVE AFTER CLICKING LINK FROM THE EMAIL:
- SHA256 hash: eb733018f77568d479df2feab4e85b7f33933727975bff1e2aeb4af976751327
File name: wcntiqav.zip
File size: 452,379 bytes
EXTRACTED BINARY FROM ZIP ARCHIVE:
- SHA256 hash: 6976a258f48310f03a6318ece87edb9d0d2f34f87cf2dcdcc6d77e5b83d744d6
File name: wcntiqav.exe
File size: 881,152 bytes
FOLLOW-UP MALWARE (1 OF 4):
- SHA256 hash: e14d5ed13f991a62b911d84a4b762d33c8b28af4c3c5e854d271b9a62c538087
File location: hxxps://raw.githubusercontent[.]com/mozdevfirefox/installf/master/install.exe
File location: C:\Users\[username]\AppData\Roaming\MD114244.exe
File size: 5,485,568 bytes
FOLLOW-UP MALWARE (2 OF 4):
- SHA256 hash: 6cd4e5f07cabb644b244e73828bf5cf4a4e89b587b25dc0b25dc95ef1f59a068
File location: C:\Users\[username]\AppData\Local\Temp\BITCE84.tmp
File size: 3,976,749 bytes
FOLLOW-UP MALWARE (3 OF 4):
- SHA256 hash: 5b6be1e57a204ca050e0abbd43e341f1b23054417413e6236ed7b9a532cd4b62
File location: hxxps://raw.githubusercontent[.]com/mozdevfirefox/installf/master/mosdhjkfi.cab
File size: 3,976,749 bytes
FOLLOW-UP MALWARE (4 OF 4):
- SHA256 hash: f3538e1e6d37a8f4a22e37e89e6c997683d48e3ba723498ab31a029a58ed37c1
File location: C:\Users\[username]\AppData\Local\_SFDNHUI34IU5H4UI6GH4IU\MD195340.exe
File size: 144,210,776 bytes
File description: Executable from the above .cab file
IMAGES
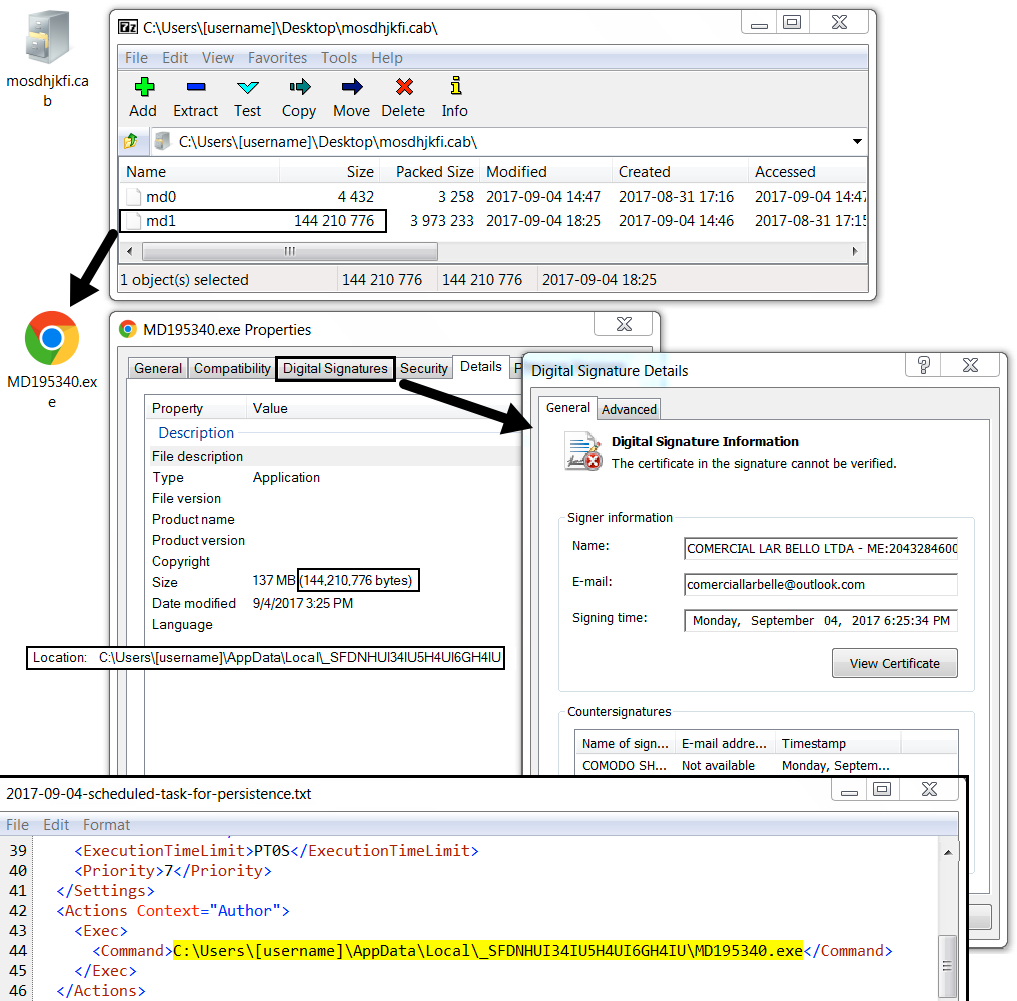
Shown above: Malware persistent on the infected host.
Click here to return to the main page.
