2017-09-06 - URSNIF INFECTION FROM JAPANESE MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-06-Ursnif-infection-traffic.pcap.zip 3.8 MB (3,781,666 bytes)
- 2017-09-06-Ursnif-infection-traffic.pcap (4,073,396 bytes)
- 2017-09-06-Japanese-malspam-for-Ursnif-4-examples.zip 580 kB (580,265 bytes)
- 2017-09-06-Japanese-malspam-for-Ursnif-0700-UTC.eml (72,052 bytes)
- 2017-09-06-Japanese-malspam-for-Ursnif-0707-UTC.eml (71,931 bytes)
- 2017-09-06-Japanese-malspam-for-Ursnif-0709-UTC.eml (72,040 bytes)
- 2017-09-06-Japanese-malspam-for-Ursnif-0711-UTC.eml (71,970 bytes)
- 2017-09-06-malware-from-Ursnif-infection.zip 580 kB (580,265 bytes)
- 2017-09-06-malicious-spreadsheet-macro.txt (3,241 bytes)
- 2017-09-06-malicious-spreadsheet.xls (51,712 bytes)
- 2017-09-06-Ursnif.exe (562,688 bytes)
RELATED TWEET:
- From @tmmalanalyst: Sep-06,2017(JST). Japanese MalSpam attached xls. Macro enabled infects #Ursnif #Malware. Leads xls file VT: (VT link) - (link to tweet)
EMAILS
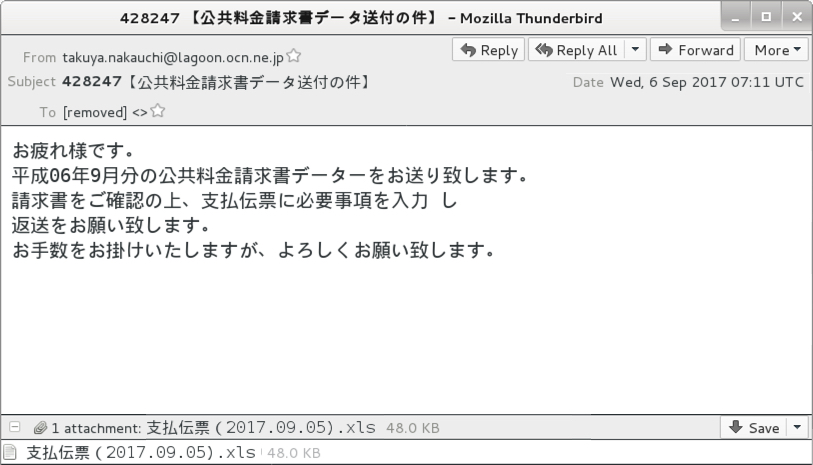
Shown above: Screenshot from one of the emails.
EMAILS GATHERED:
(Read: Date/Time -- Sending address (spoofed) -- Subject)
- 2017-09-06 07:00 UTC -- mina-a-yu.yoshi2t@jupiter.jcom[.]co[.]jp -- 399104 【公共料金請求書データ送付の件】
- 2017-09-06 07:07 UTC -- nckei4@ksf.biglobe[.]ne[.]jp -- 090646 【公共料金請求書データ送付の件】
- 2017-09-06 07:09 UTC -- yamada.masuo@green.ocn[.]ne[.]jp -- 018648 【公共料金請求書データ送付の件】
- 2017-09-06 07:11 UTC -- ntakuya.nakauchi@lagoon.ocn[.]ne[.]jp -- 428247 【公共料金請求書データ送付の件】
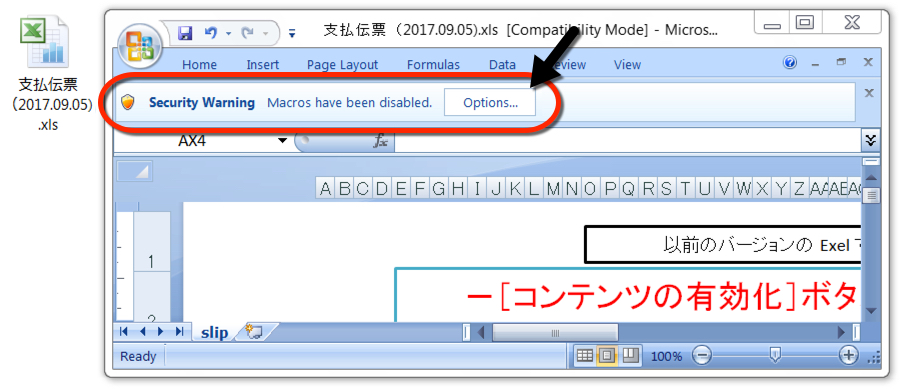
Shown above: One of the Excel spreadsheets.
TRAFFIC
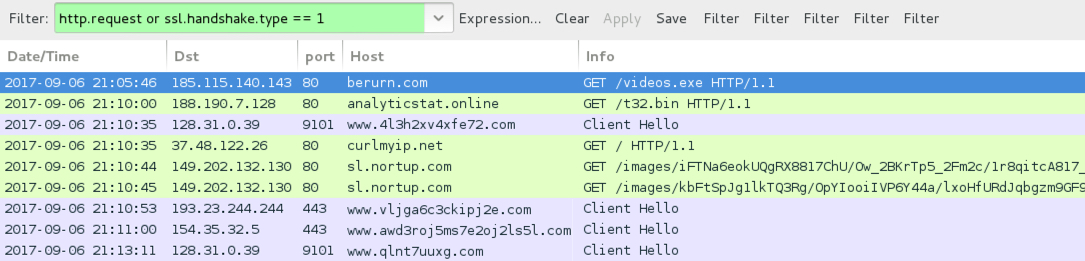
Shown above: Traffic from an infection filtered in Wireshark.
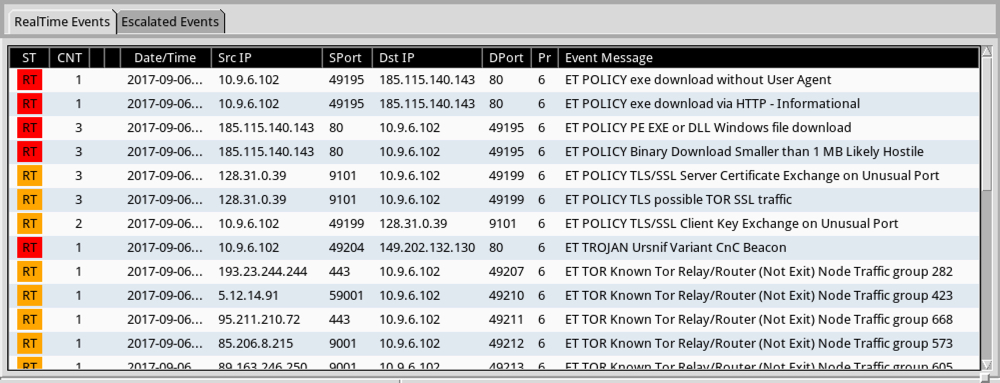
Shown above: Some alerts on the traffic from the Emerging Threats and ETPRO rulesets using Sguil and tcpreplay on Security Onion.
ASSOCIATED DOMAINS:
- 185.115.140[.]143 port 80 - berurn[.]com - GET /videos.exe
- 188.190.7[.]128 port 80 - analyticstat[.]online - GET /t32.bin
- curlmyip[.]net - GET /
- 149.202.132[.]130 port 80 - sl.nortup[.]com - GET /images/[long string of characters].jpeg
- 149.202.132[.]130 port 80 - sl.nortup[.]com - GET /images/[long string of characters].gif
- Various IP addresses, various ports - various domains - Tor traffic
FILE HASHES
EMAIL ATTACHMENT:
- SHA256 hash: 3f415553b7b22919c75f733c3403aa6f4396d8d62d1178e9b3a4ba54ac53300e
File size: 51,712 bytes
File name: 支払伝票 (2017.09.05).xls
FOLLOW-UP URSNIF MALWARE:
- SHA256 hash: 46da8289c027a187b14826f3648d61c187398ad170ef60ec3311b5dae3b52d61
File size: 562,688 bytes
File location: C:\Users\[username]\AppData\Roaming\11565.exe
File location: C:\Users\[username]\AppData\Roaming\Microsoft\Aecaider\avicbrkr.exe
Click here to return to the main page.
