2017-09-07 - "LUKITUS" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-07-Locky-ransomware-traffic-2-pcaps.zip 1.1 MB (1,100,858 bytes)
- 2017-09-07-Locky-ransomware-email-tracker.csv.zip 1.9 kB (1,863 bytes)
- 2017-09-07-Locky-ransomware-emails-and-malware.zip 1.3 MB (1,262,329 bytes)
EMAILS
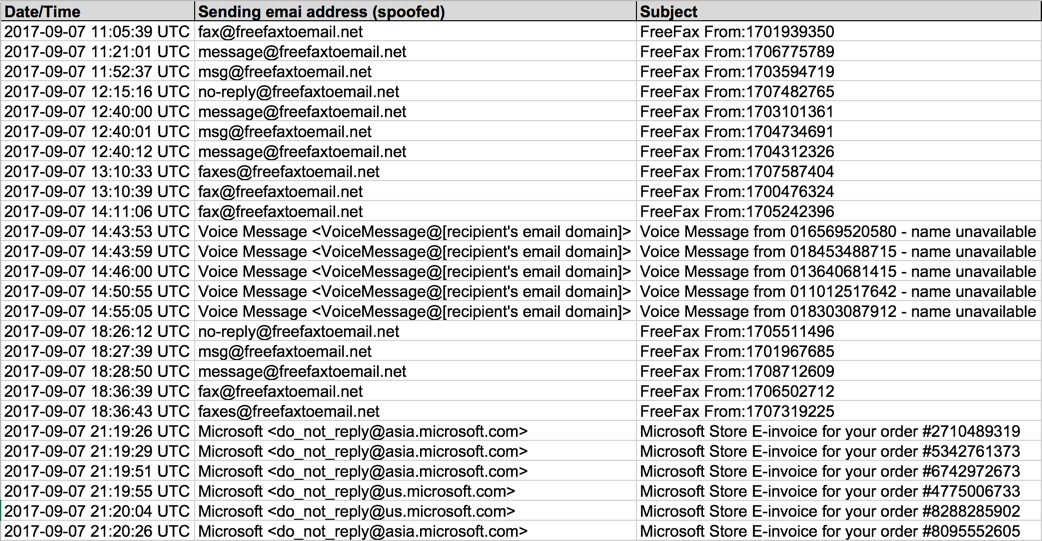
Shown above: Screenshot of the spreadsheet tracker.
EMAILS:
- 2017-09-07 11:05:39 UTC -- From: fax@freefaxtoemail[.]net -- Subject: FreeFax From:1701939350
- 2017-09-07 11:21:01 UTC -- From: message@freefaxtoemail[.]net -- Subject: FreeFax From:1706775789
- 2017-09-07 11:52:37 UTC -- From: msg@freefaxtoemail[.]net -- Subject: FreeFax From:1703594719
- 2017-09-07 12:15:16 UTC -- From: no-reply@freefaxtoemail[.]net -- Subject: FreeFax From:1707482765
- 2017-09-07 12:40:00 UTC -- From: message@freefaxtoemail[.]net -- Subject: FreeFax From:1703101361
- 2017-09-07 12:40:01 UTC -- From: msg@freefaxtoemail[.]net -- Subject: FreeFax From:1704734691
- 2017-09-07 12:40:12 UTC -- From: message@freefaxtoemail[.]net -- Subject: FreeFax From:1704312326
- 2017-09-07 13:10:33 UTC -- From: faxes@freefaxtoemail[.]net -- Subject: FreeFax From:1707587404
- 2017-09-07 13:10:39 UTC -- From: fax@freefaxtoemail[.]net -- Subject: FreeFax From:1700476324
- 2017-09-07 14:11:06 UTC -- From: fax@freefaxtoemail[.]net -- Subject: FreeFax From:1705242396
- 2017-09-07 14:43:53 UTC -- From: Voice Message <VoiceMessage@[recipient's email domain]> -- Subject: Voice Message from 016569520580 - name unavailable
- 2017-09-07 14:43:59 UTC -- From: Voice Message <VoiceMessage@[recipient's email domain]> -- Subject: Voice Message from 018453488715 - name unavailable
- 2017-09-07 14:46:00 UTC -- From: Voice Message <VoiceMessage@[recipient's email domain]> -- Subject: Voice Message from 013640681415 - name unavailable
- 2017-09-07 14:50:55 UTC -- From: Voice Message <VoiceMessage@[recipient's email domain]> -- Subject: Voice Message from 011012517642 - name unavailable
- 2017-09-07 14:55:05 UTC -- From: Voice Message <VoiceMessage@[recipient's email domain]> -- Subject: Voice Message from 018303087912 - name unavailable
- 2017-09-07 18:26:12 UTC -- From: no-reply@freefaxtoemail[.]net -- Subject: FreeFax From:1705511496
- 2017-09-07 18:27:39 UTC -- From: msg@freefaxtoemail[.]net -- Subject: FreeFax From:1701967685
- 2017-09-07 18:28:50 UTC -- From: message@freefaxtoemail[.]net -- Subject: FreeFax From:1708712609
- 2017-09-07 18:36:39 UTC -- From: fax@freefaxtoemail[.]net -- Subject: FreeFax From:1706502712
- 2017-09-07 18:36:43 UTC -- From: faxes@freefaxtoemail[.]net -- Subject: FreeFax From:1707319225
- 2017-09-07 21:19:26 UTC -- From: Microsoft <do_not_reply@asia.microsoft[.]com> -- Subject: Microsoft Store E-invoice for your order #2710489319
- 2017-09-07 21:19:29 UTC -- From: Microsoft <do_not_reply@asia.microsoft[.]com> -- Subject: Microsoft Store E-invoice for your order #5342761373
- 2017-09-07 21:19:51 UTC -- From: Microsoft <do_not_reply@asia.microsoft[.]com> -- Subject: Microsoft Store E-invoice for your order #6742972673
- 2017-09-07 21:19:55 UTC -- From: Microsoft <do_not_reply@us.microsoft[.]com> -- Subject: Microsoft Store E-invoice for your order #4775006733
- 2017-09-07 21:20:04 UTC -- From: Microsoft <do_not_reply@us.microsoft[.]com> -- Subject: Microsoft Store E-invoice for your order #8288285902
- 2017-09-07 21:20:26 UTC -- From: Microsoft <do_not_reply@asia.microsoft[.]com> -- Subject: Microsoft Store E-invoice for your order #8095552605
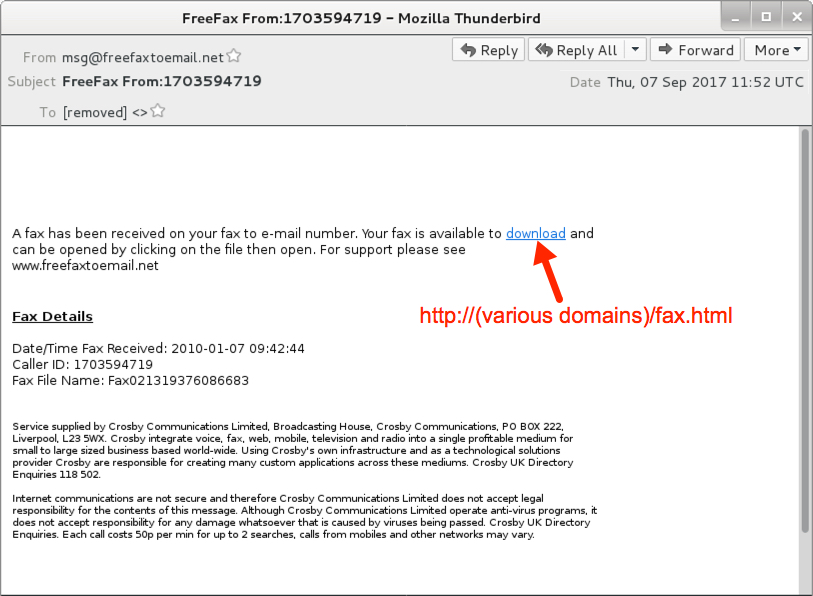
Shown above: Screenshot of the emails (earlier wave 1 of 2).
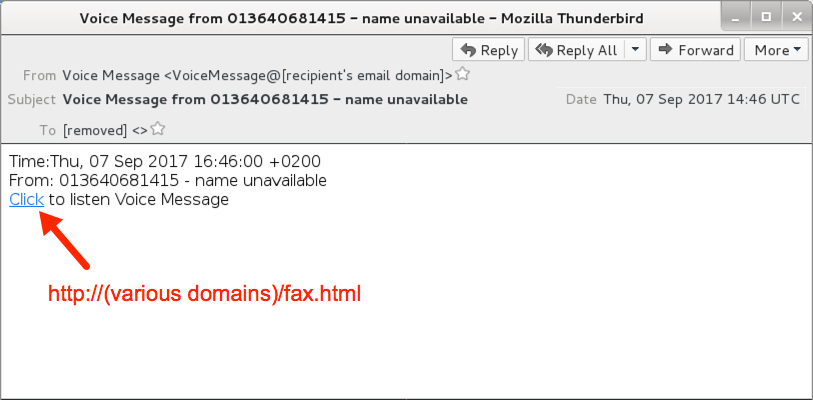
Shown above: Screenshot of the emails (earlier wave 2 of 2).
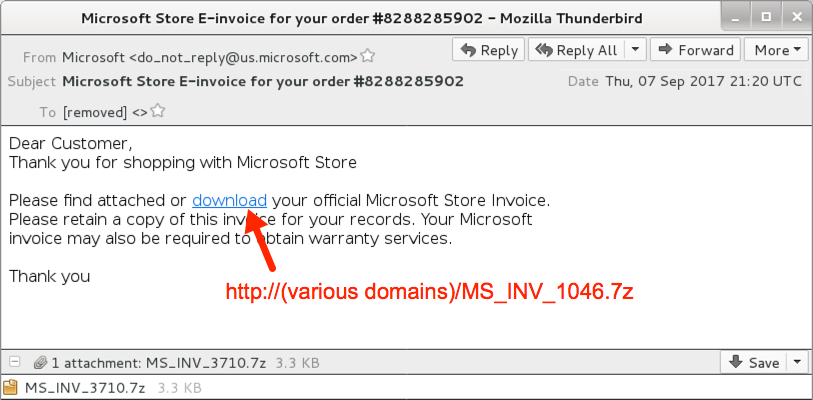
Shown above: Screenshot of the emails (later wave).
TRAFFIC
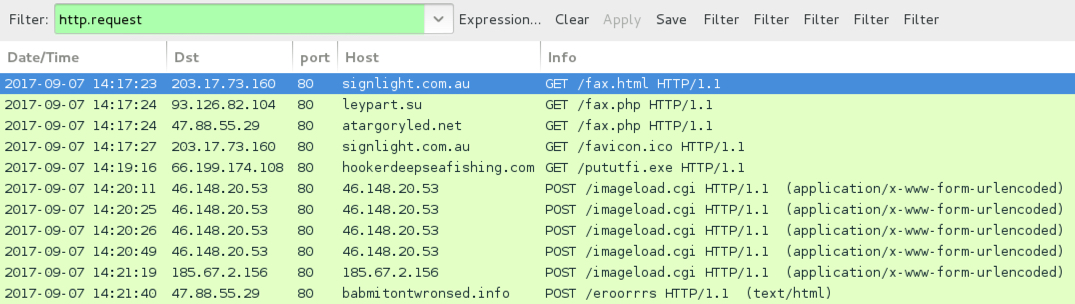
Shown above: Traffic from an earlier infection filtered in Wireshark.
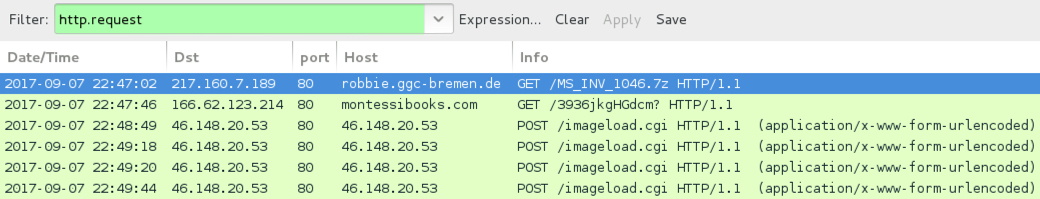
Shown above: Traffic from a later infection filtered in Wireshark.
LINKS FROM THE EARLIER EMAILS:
- hxxp[:]//areanuova[.]it/fax.html
- hxxp[:]//brillantelimpieza[.]com/fax.html
- hxxp[:]//brovalbox[.]net/fax.html
- hxxp[:]//computertechnicians[.]net/fax.html
- hxxp[:]//fortcollins-accounting[.]com/fax.html
- hxxp[:]//imblog[.]de/fax.html
- hxxp[:]//itsmaterial[.]us/fax.html
- hxxp[:]//jeangurunlian[.]com/fax.html
- hxxp[:]//kedemcapital[.]com/fax.html
- hxxp[:]//lacosturera[.]es/fax.html
- hxxp[:]//malvapraha[.]cz/fax.html
- hxxp[:]//nekkeveldecoplus[.]nl/fax.html
- hxxp[:]//oscarbuitron[.]com/fax.html
- hxxp[:]//pki.jwo[.]com/fax.html
- hxxp[:]//rmrcreative[.]com/fax.html
- hxxp[:]//scottborthwick[.]com/fax.html
- hxxp[:]//signlight[.]com[.]au/fax.html
- hxxp[:]//theceocforeporter[.]com/fax.html
- hxxp[:]//themaninroom306[.]com/fax.html
- hxxp[:]//toldoslidia[.]es/fax.html
URLS TO DOWNLOAD LOCKY RANSOMWARE CAUSED BY EARLIER EMAILS:
- hxxp[:]//leypart[.]su/fax.php
- hxxp[:]//atargoryled[.]net/fax.php
- hxxp[:]//hookerdeepseafishing[.]com/pututfi.exe
LINKS IN LATER EMAILS:
- hxxp[:]//intelicalls[.]com/MS_INV_1046.7z
- hxxp[:]//labkonstrukt[.]com/MS_INV_1046.7z
- hxxp[:]//mercaropa[.]es/MS_INV_1046.7z
- hxxp[:]//pesonamas[.]co[.]id/MS_INV_1046.7z
- hxxp[:]//robbie.ggc-bremen[.]de/MS_INV_1046.7z
- hxxp[:]//schwellenwertdaten[.]de/MS_INV_1046.7z
URLS TO DOWNLOAD LOCKY RANSOMWARE CAUSED BY LATER EMAILS:
- hxxp[:]//aac-autoecole[.]com/3936jkgHGdcm?
- hxxp[:]//awholeblueworld[.]com/3936jkgHGdcm?
- hxxp[:]//etforhartohat[.]info/af/3936jkgHGdcm
- hxxp[:]//lp-usti[.]cz/3936jkgHGdcm?
- hxxp[:]//montessibooks[.]com/3936jkgHGdcm?
- hxxp[:]//weekendjevliegen[.]nl/3936jkgHGdcm?
LOCKY RANSOMWARE POST-INFECTION TRAFFIC:
- hxxp[:]//46.148.20[.]53/imageload.cgi
- hxxp[:]//185.67.2[.]156/imageload.cgi
- hxxp[:]//babmitontwronsed[.]info/eroorrrs
- g46mbrrzpfszonuk[.]onion
FILE HASHES
SHA256 hash: b6a6c9746694e4aa7081c1fc4b3c54e7716b80ef438b069a906fb852c89a7923
- File name: Fax_Message_4910872563.js
- File description: JavaScript (.js) file downloaded from links in earlier emails
SHA256 hash: ba573c9c097ff7ec0f9c24a11f17c6de24133a214183ec1e21d443c525271dfd
- File name: Fax_Message_6310542798.js
- File description: JavaScript (.js) file downloaded from links in earlier emails
SHA256 hash: 958569e5942e3e4aa2df592f1c2cdd24cf187a237a0073c6ef1462a6c89a8590
- File name: MS_INV_1046.7z
- File description: 7-Zip (.7z) archive downloaded from links in later emails
SHA256 hash: f31aee58fc2dfde26a4d40fe081ce467ce31d4955212a53f93f717e1f1c5f4c1
- File names: MS_INV_3015.7z and MS_INV_3710.7z
- File description: 7-Zip (.7z) archives as file attachments in later emails
SHA256 hash: 1db77f180460ae8be542c5e392e1c2ceed47f420f3831685babebdc038a99446
- File names: MS_INV_5989.7z, MS_INV_6712.7z, MS_INV_7512.7z, and MS_INV_7526.7z
- File description: 7-Zip (.7z) archives as file attachments in later emails
SHA256 hash: 39d986b3a62f4d1b2e43c8295a2a645187e08417b6c0d2d8b08a9f7e75343936
- File name: MS_INV_1046.vbs
- File description: Visual Basic Script (VBS) file extracted from .7z archive
SHA256 hash: f34c4bc6bca63d3c18b3a570d602a7d513594dc6c563ace7372ed3046b3d567f
- File name: MS_INV_7493.vbs
- File description: Visual Basic Script (VBS) file extracted from .7z archive
SHA256 hash: 24ca332249210bec427078f877e8c1b942fb469387428682ff421de7e68d0582
- File name: MS_INV_8448.vbs
- File description: Visual Basic Script (VBS) file extracted from .7z archive
SHA256 hash: e9981527fade0266ec18c73bf3cb066738ed12c3c3530a30a2e56a790d180107
- File location: C:\Users\[username]\AppData\Roaming\scareGT.exe
- File description: Locky ransomware binary from earlier emails
SHA256 hash: 278e5503f777b0fec03cff2acddedb67f8b62bb14f34a9e761408aaf3ce5450f
- File location: C:\Users\[username]\AppData\Local\Temp\vQqEpFK.exe
- File description: Locky ransomware binary from later emails
IMAGES
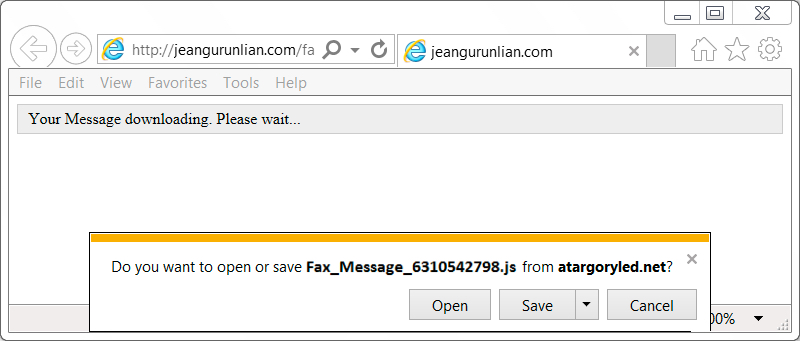
Shown above: Downloading a JavaScript (.js) file from the earlier waves.
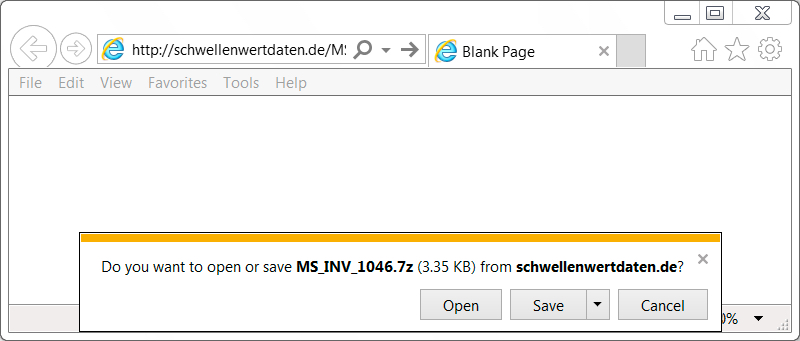
Shown above: Downloading a 7-Zip archive (.7z) from the later wave.
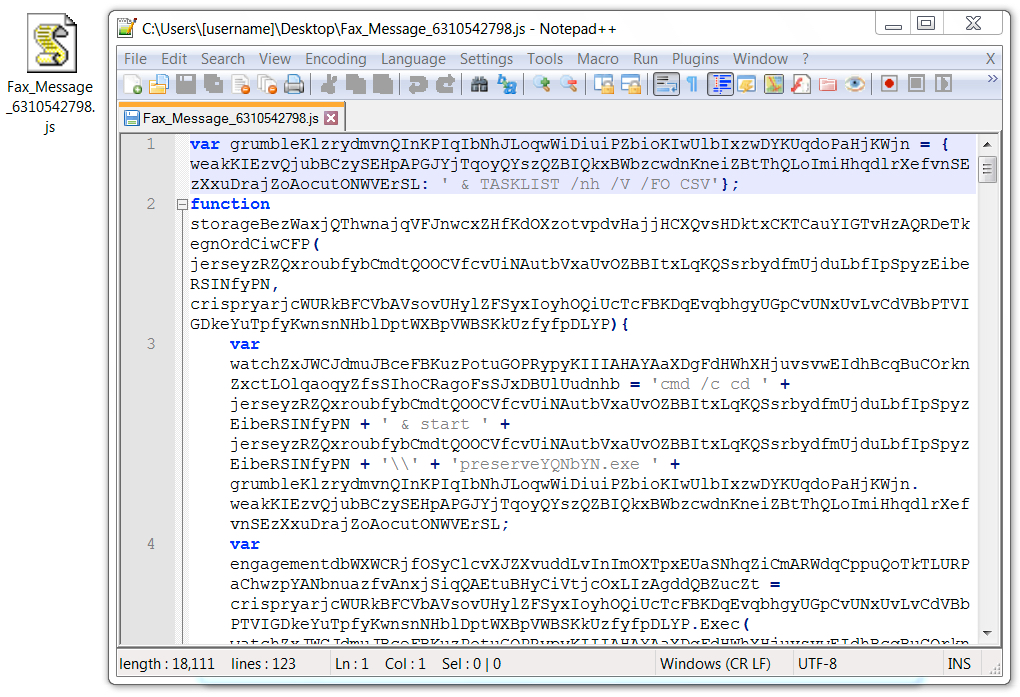
Shown above: JavaScript (.js) example from the earlier waves.
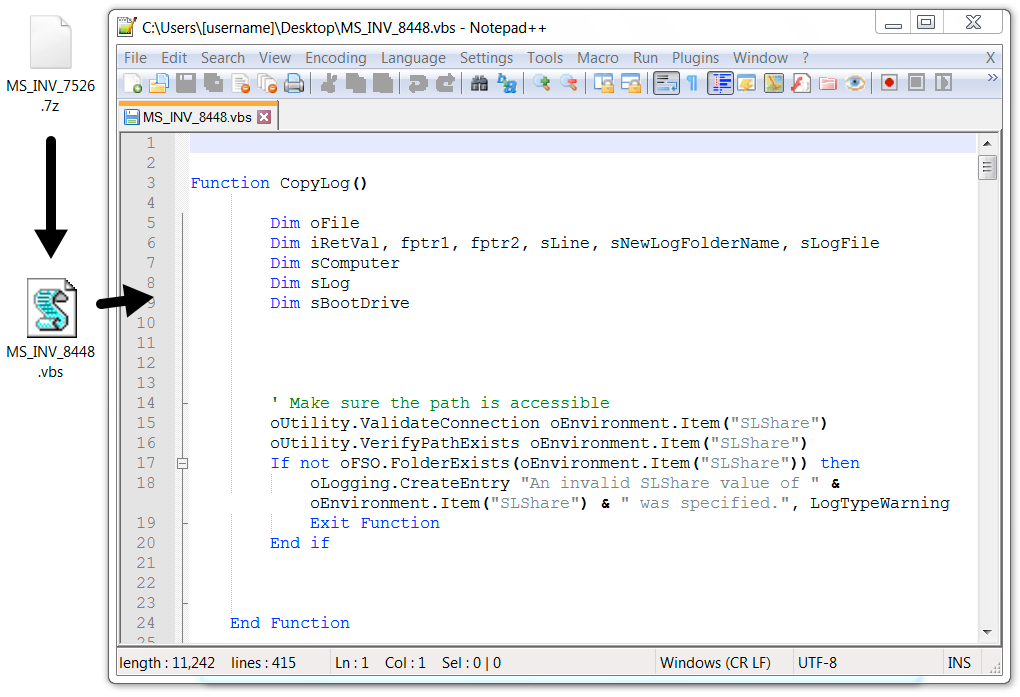
Shown above: 7-Zip archive (.7z) example from the later wave.
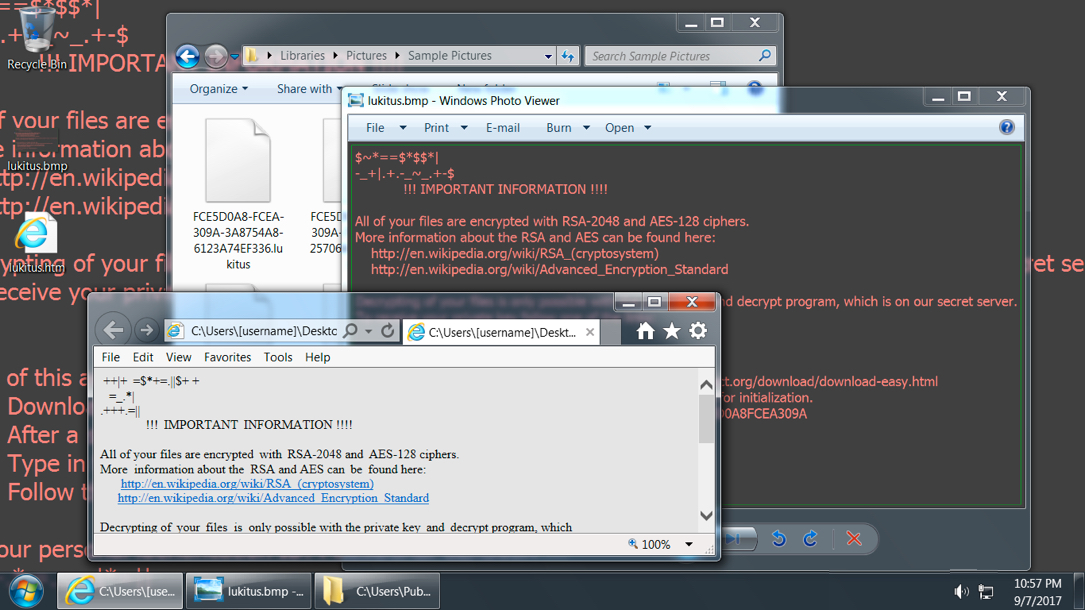
Shown above: If you've seen one Windows desktop infected with Lukitus variant Locky, you've seen them all.
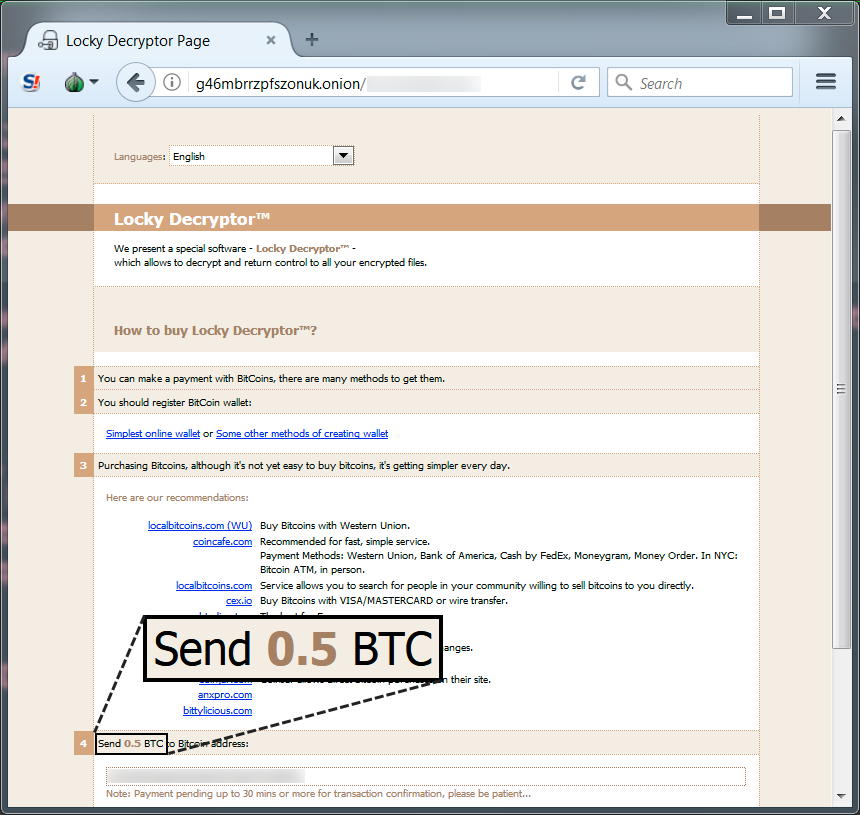
Shown above: 0.5 Bitcoin seems a little steep for the ransom cost.
Click here to return to the main page.
