2017-09-18 - EMOTET INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-18-Emotet-infection-traffic.pcap.zip 598.9 kB (598,989 bytes)
- 2017-09-18-Emotet-infection-traffic.pcap (691,065 bytes)
<
- 2017-09-18-Emotet-malspam-1433-UTC.eml.zip 1.0 kB (1,039 bytes)
- 2017-09-18-Emotet-malspam-1433-UTC.eml (1,318 bytes)
- 2017-09-18-malware-from-Emotet-infection.zip 98.5 kB (98,529 bytes)
- Invoice_5499.doc (65,024 bytes)
- MIKxorREXp.exe (90,112 bytes)
TWEETS NOTED ABOUT TODAY'S WAVE OF #EMOTET MALSPAM:
- @pollo290987: Twitter thread discussing one of these emails seen today (link)
- @certbund: [English translation] Caution, currently again fake billing emails are in circulation. The Trojan horse #Emotet is distributed via the included link. (link)
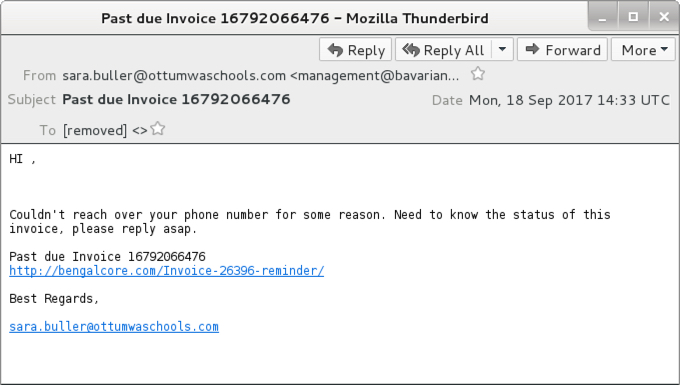
Shown above: Screenshot from an email seen on 2017-09-18.
HEADER INFORMATION:
- Date: Monday, 2017-09-18 14:33 UTC
- Subject: Past due Invoice 16792066476
- Message-ID: <27654500143.2017918133324@[recipient's email domain]>
- From: sara.buller@ottumwaschools[.]com <management@bavarianmotorcars[.]com>
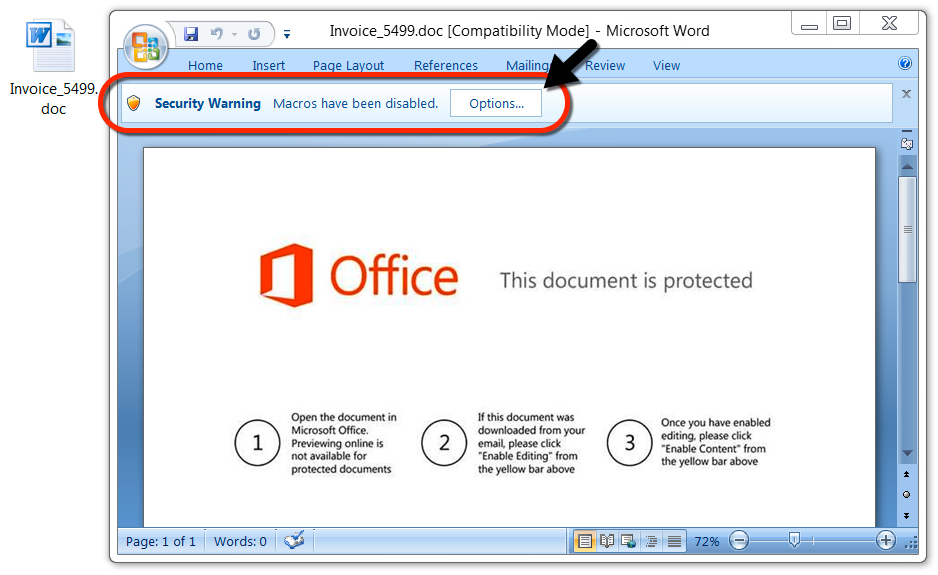
Shown above: Malicious Word document downloaded from link in the email.
TRAFFIC
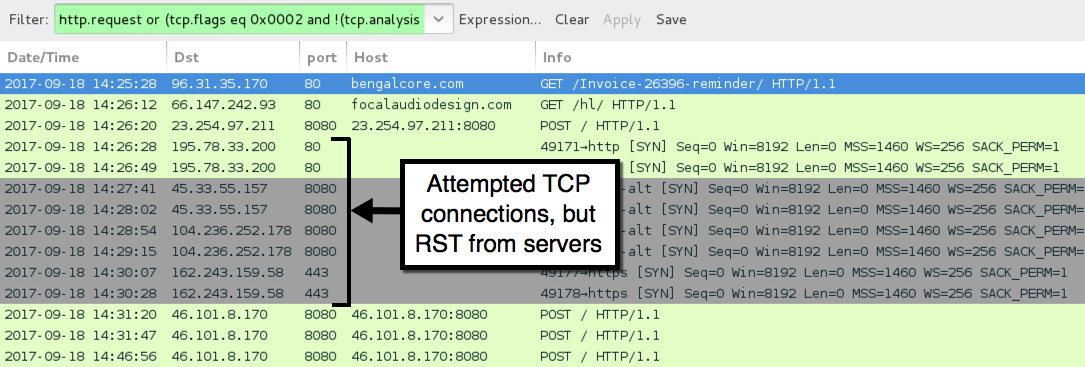
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED TRAFFIC:
- 96.31.35[.]170 port 80 - bengalcore[.]com - GET /Invoice-26396-reminder/
- 66.147.242[.]93 port 80 - focalaudiodesign[.]com - GET /hl/
- 23.254.97[.]211 port 8080 - 23.254.97[.]211:8080 - POST /
- 46.101.8[.]170 port 8080 - 46.101.8[.]170:8080 - POST /
- 45.33.55[.]157 port 8080 - attempted TCP connection, but RST from server
- 104.236.252[.]178 port 8080 - attempted TCP connection, but RST from server
- 162.243.159[.]58 port 443 - attempted TCP connection, but RST from server
- 195.78.33[.]200 port 80 - attempted TCP connection, but RST from server
MALWARE
WORD DOCUMENT DOWNLOADED FROM EMAIL LINK:
- SHA256 hash: e77ff24ea71560ffcb9b6e63e9920787d858865ba09f5d63a7e44cb86a569a6e
File size: 65,024 bytes
File name: Invoice_5499.doc (random file names seen from the email URL)
FOLLOW-UP MALWARE (EMOTET):
- SHA256 hash: 69ae78447015ded9b7c4d78b103cb1db8d7149a2a3f6ffed79b41e1f6e0dbceb
File size: 90,112 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\shedulecart.exe
Click here to return to the main page.
