2017-09-18 - NECURS BOTNET MALSPAM PUSHES ".YKCOL" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-18-Necurs-Botnet-malspam-pushes-Locky-ransomware-2-pcaps.zip 1.0 MB (1,003,610 bytes)
- 2017-09-18-Necurs-Botnet-malspam-tracker.csv.zip 1.8 kB (1,753 bytes)
- 2017-09-18-Necurs-Botnet-emails-and-Locky-ransomware-files.zip 1.3 MB (1,292,092 bytes)
NOTES:
- Haha! "ykcol" is "locky" spelled backwards.
- As usual, plenty of people have seen this activity and have tweeted about it.
- I've always understood this to be from the Necurs Botnet. If that's not the case, please let me know.
- No post-infection traffic was noted from my infected Windows hosts today.
- Ransom cost is now at 0.25 Bitcoin. Locky used to charge 0.5 Bitcoin for a very long time This change probably reflects the rise in value of Bitcoin during the past few months.
EMAILS

Shown above: Screenshot from the spreadsheet tacker.
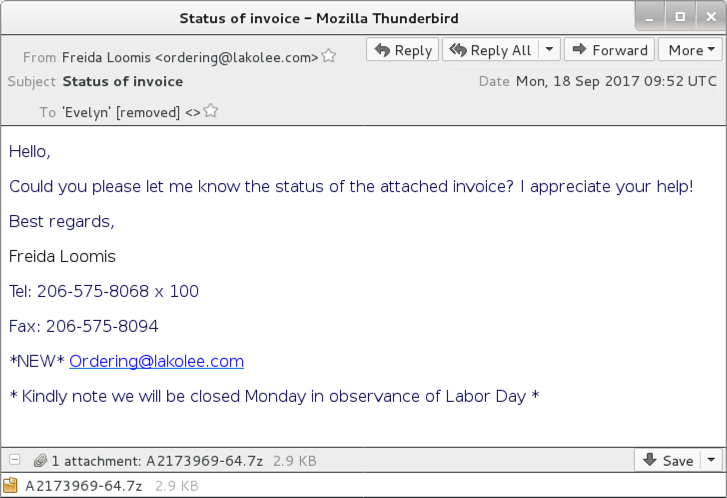
Shown above: Screen shot of an email from the 1st wave.

Shown above: Screen shot of an email from the 2nd wave.
EMAILS COLLECTED:
Read: Date/Time -- Sending email address (spoofed) -- Subject -- Attachment name -- Extracted VBS file name
- 2017-09-18 09:52:41 UTC -- "Freida Loomis" <ordering@lakolee[.]com> -- Status of invoice -- A2173969-64.7z -- 17928541964.vbs
- 2017-09-18 10:38:25 UTC -- "Georgina Catrol" <ordering@germignac[.]fr> -- Status of invoice -- A2175091-78.7z -- 34288202516.vbs
- 2017-09-18 10:39:01 UTC -- "Kaitlin Fergusson" <ordering@tobeef[.]de> -- Status of invoice -- A2179674-51.7z -- 65343042961.vbs
- 2017-09-18 10:51:26 UTC -- "Dorothea Jacks" <ordering@esselman[.]net> -- Status of invoice -- A2178960-44.7z -- 44394795975.vbs
- 2017-09-18 11:29:02 UTC -- "Latonya Bird" <ordering@apuntevirtual[.]com> -- Status of invoice -- A2175814-42.7z -- 26596685195.vbs
- 2017-09-18 11:52:58 UTC -- "Edna Brewer" <ordering@lookatreview[.]com> -- Status of invoice -- A2171888-68.7z -- 38397487470.vbs
- 2017-09-18 13:39:33 UTC -- "Lilian Meager" <ordering@asplanpb[.]com[.]br> -- Status of invoice -- A2179187-37.7z -- 41431435149.vbs
- 2017-09-18 13:41:56 UTC -- "Antoinette Polson" <ordering@yourarray[.]com> -- Status of invoice -- A2174839-17.7z -- 7861468371.vbs
- 2017-09-18 13:55:39 UTC -- "Latisha Hilliard" <ordering@fascinatinglearningfactory[.]org> -- Status of invoice -- A2176576-71.7z -- 32028947946.vbs
- 2017-09-18 16:35:11 UTC -- <copier@[recipient's email domain]> -- Message from KM_C224e -- 20171809_24636829014.7z -- 20170918_77742887162.vbs
- 2017-09-18 16:40:31 UTC -- <copier@[recipient's email domain]> -- Message from KM_C224e -- 20171809_75337529254.7z -- 20170918_52429245866.vbs
- 2017-09-18 16:43:03 UTC -- <copier@[recipient's email domain]> -- Message from KM_C224e -- 20171809_80523513381.7z -- 20170918_24250165030.vbs
- 2017-09-18 18:32:20 UTC -- <copier@[recipient's email domain]> -- Message from KM_C224e -- 20171809_75743414104.7z -- 20170918_87839176078.vbs
- 2017-09-18 19:21:10 UTC -- <copier@[recipient's email domain]> -- Message from KM_C224e -- 20171809_16127286024.7z -- 20170918_17608770693.vbs
- 2017-09-18 19:33:48 UTC -- <copier@[recipient's email domain]> -- Message from KM_C224e -- 20171809_61562124834.7z -- 20170918_84047158233.vbs
TRAFFIC

Shown above: Infection traffic filtered in Wireshark (no post-infection traffic noted).
URLS FROM THE VBS FILES TO DOWNLOAD LOCKY:
- hxxp[:]//abelfaria[.]pt/87thiuh3gfDGS?
- hxxp[:]//grovecreative[.]co[.]uk/87thiuh3gfDGS?
- hxxp[:]//lanzensberger[.]de/87thiuh3gfDGS?
- hxxp[:]//miliaraic[.]ru/p66/87thiuh3gfDGS
- hxxp[:]//pielen[.]de/87thiuh3gfDGS?
- hxxp[:]//unifiedfloor[.]com/87thiuh3gfDGS?
- hxxp[:]//qstom[.]com/87thiuh3gfDGS?
- hxxp[:]//troyriser[.]com/87thiuh3gfDGS?
- hxxp[:]//w4fot[.]com/87thiuh3gfDGS?
- hxxp[:]//www.elitecommunications[.]co[.]uk/87thiuh3gfDGS?
- hxxp[:]//yildizmakina74[.]com/87thiuh3gfDGS?
- hxxp[:]//accountingservices.apec[.]org/DKndhFG72?
- hxxp[:]//cornyproposals[.]com/DKndhFG72?
- hxxp[:]//dmlex.adlino[.]be/DKndhFG72?
- hxxp[:]//eurecas[.]org/DKndhFG72?
- hxxp[:]//georginabringas[.]com/DKndhFG72?
- hxxp[:]//lasdamas[.]com/DKndhFG72?
- hxxp[:]//montecortelhas[.]com/DKndhFG72?
- hxxp[:]//pnkparamount[.]com/DKndhFG72?
- hxxp[:]//targeter[.]su/p66/DKndhFG72
- hxxp[:]//walkama[.]net/DKndhFG72?
- hxxp[:]//wenger-werkzeugbau[.]de/DKndhFG72?
ASSOCIATED FILES
SHA256 HASHES:
- c46a6a9e5439d27f8625c90c09eacd2e5b680b509cda5ccd39920a949fe1d2f5 - 20171809_16127286024.7z
- 2ba1780ae28500f6e2010240e00556d6fb589961f44895d36da18ee10567644a - 20171809_24636829014.7z
- 374f4e3777f5827b5fb6d8fa263911cf829397df194c073359aa86f2e7030e55 - 20171809_61562124834.7z
- ebcef942ea58289ddea116d7ae3a9e1beeab3299550b98de13666955245767ae - 20171809_75337529254.7z
- 1ccf729a82e0b9b4aa94a8c724c84978a062d49a858a5582670609cf219a7589 - 20171809_75743414104.7z
- 22dabc58b6219e5186e089ae084cd2bd4f91d17346c7e9fff2548e71c897b00a - 20171809_80523513381.7z
- f61a3bd359919d562de81ff5224d5f82f9cbc16c4c3cefa365d7726bc3ba1408 - A2171888-68.7z
- 8f1e51cbfcdaba3401de72c4b3d8a288d5eaed220e9a0987efd7ba9eebe26d87 - A2173969-64.7z
- fc5d2f6326e46467963e65984adc089979cd0b48523997334da6d6f090e836d3 - A2174839-17.7z
- 9d98f8aaf4c33aa0be58a83b2a2d9063555538d0cdc0c559cf2080b904f83c0b - A2175091-78.7z
- 9f3c905921f794c0a2593e6c31cb899e0a2cf7cf0372b1b793caabbc52219ef1 - A2175814-42.7z
- 4526321bb37ab45bf48cf67518d01eb6bdbd19c45c964c4cee0cbdd47989b095 - A2176576-71.7z
- 0e0b7e4eb2641ea3639a9b53ee171b4cf0318874e72da060035f6bc411c345c1 - A2178960-44.7z
- 7a933e557afadaef1c324de5aa840ddc3ebcf117aad2de188dd8577228a060c0 - A2179187-37.7z
- f9b1a20ea2673a99837753122bdd00d27c3605d31bde73ec7b843fb35a26ae70 - A2179674-51.7z
- 8694235ec13de942c7a256e3c3e66a424cffd6157fe94c2d09835fc7b8702dc8 - 17928541964.vbs
- 157a6ef43898a3ee9703fc86153316d8785cc5d8f6a56323452ed7b2dda06921 - 20170918_17608770693.vbs
- 80ea8b0a4bed6616a3cbfda27447c924f46d50d0041577bb87cf00f89e620a8a - 20170918_24250165030.vbs
- 047a98117c6937b13d4f86790832ef443159d3264c0e98ff79c276b9296a43d2 - 20170918_52429245866.vbs
- c686da75010eafb5f4343b874fcb5d1575aee8062706ff0bdadf0ab4a6116be0 - 20170918_77742887162.vbs
- a83145819df3083fb0172e042403797c48a4ffb5dce4da3c7502a433ecbb6160 - 20170918_84047158233.vbs
- 54b92f4ba6a0f6a2142ddda293e5da2a0361fd4253d4a583fb187f420b9dba7b - 20170918_87839176078.vbs
- ea62b4d5644336c5c7bd3085dbd5eb51500a51371f7fc4be0b278bf3911ee30f - 26596685195.vbs
- 63b40dfa616dd5e999da04c570a3fcdb95591b03e476a958d8444198ae9195a0 - 32028947946.vbs
- 848a60dd696db861154c1b6d174f2a93dd8cc2acc523cee3885c328291bd2ceb - 34288202516.vbs
- d49a897d9b1d062dd58123803a9da35d73199d0b84f470ef1c942e2c1eda99f5 - 38397487470.vbs
- 8d3d172b64a7154c425c5a4bd2963ff551d5c3ab6f947a0d778e5dd16dd47d7a - 41431435149.vbs
- f0ad1db9d5384c14a409f59b997091a37fee2f190b086dac5cc38038ab69aaa6 - 44394795975.vbs
- a0ea5d6b907887442163bd89765c50df29930a60d632e99b15d0b8217fa0b140 - 65343042961.vbs
- 684fd9baa1702e0478f9449053bc5d03bfffab0b12f94aaa8443bb4a98ab2ebd - 7861468371.vbs
- 3ebb3c50ea81e6897f130cd5582981ca6ee0a5432ebfe85fa522dc25fc462aaf - Locky ransomware binary from 1st wave
- 8bf303dda84a1e0552f98370dd5dbfdf127d7ec9b5caab948874a897771ce142 - Locky ransomware binary from 2nd wave
IMAGES

Shown above: Screenshot from an infected Windows desktop--Encrypted files all have a .ykcol file extension.

Shown above: Locky Decryptor, where is looks like the ransom cost is .25 Bitcoin now.
Click here to return to the main page.
