2017-09-20 - LOKIBOT INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-20-Lokibot-infection-traffic.pcap.zip 158.9 kB (158,939 bytes)
- 2017-09-20-Lokibot-infection-traffic.pcap (398,387 bytes)
- 2017-09-20-Lokibot-malspam-0809-UTC.eml.zip 20.2 kB (20,249 bytes)
- 2017-09-20-Loki-bot-malspam-0809-UTC.eml (53,254 bytes)
- 2017-09-20-malware-from-Lokibot-infection.zip 197.5 kB (197,525 bytes)
- LPO#20092017.xls (36,820 bytes)
- voke.exe (483,328 bytes)
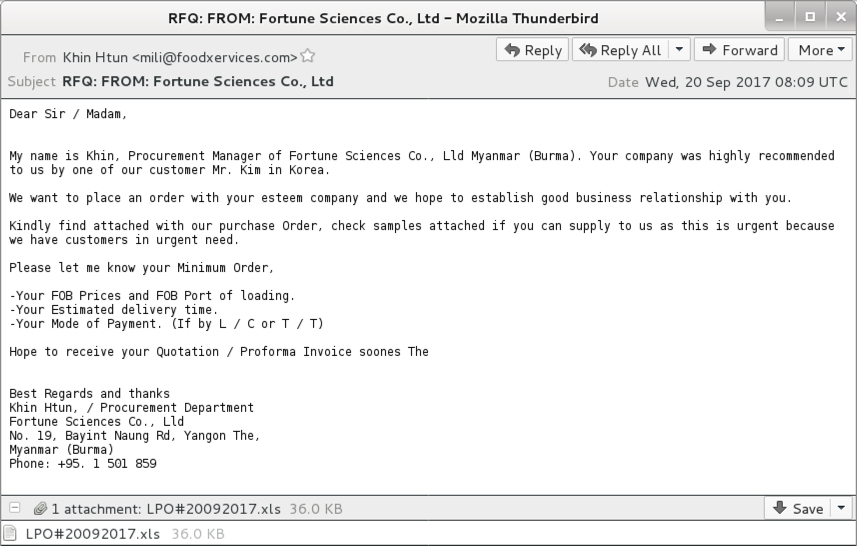
Shown above: Screenshot from the email seen on 2017-09-20.
EMAIL HEADER INFORMATION:
- Date: Wednesday, 2017-09-20 08:09 UTC
- Subject: RFQ: FROM: Fortune Sciences Co., Ltd
- Message-ID: <6e489ba9249990691deade3b19cd839b@foodxervices[.]com>
- From: "Khin Htun" <mili@foodxervices[.]com>
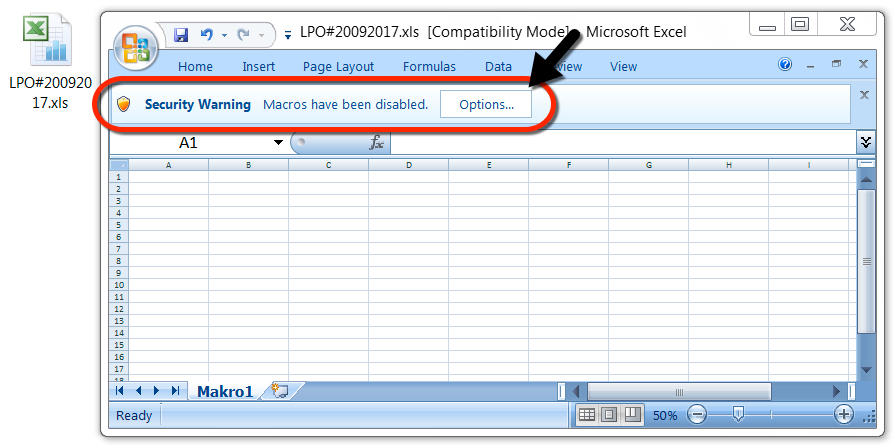
Shown above: Malicious Excel spreadsheet attached to the email.
TRAFFIC
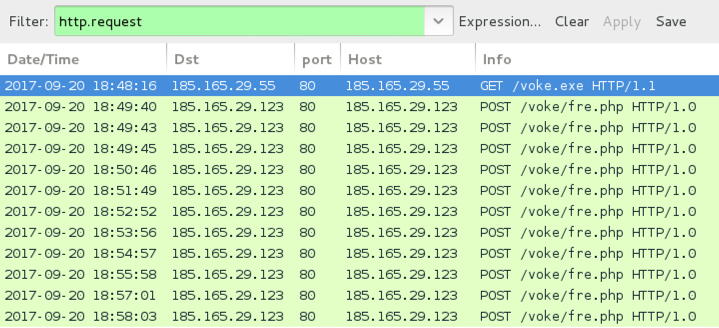
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED TRAFFIC:
- 185.165.29[.]55 port 80 - 185.165.29[.]55 - GET /voke.exe
- 185.165.29[.]123 port 80 - 185.165.29[.]123 - POST /voke/fre.php
MALWARE
EXCEL SPREADSHEET ATTACHED TO THE EMAIL:
- SHA256 hash: e618be36548c349562bbdc6c4d68efcb2c86b4354037e9014fd91eea3ec0a0ca
File size: 36,820 bytes
File name: LPO#20092017.xls
FOLLOW-UP MALWARE (LOKIBOT):
- SHA256 hash: 769bdfc3c5938b42d008937bc91e8959a22caf2fbbd2583c84cca878f96ac6e6
File size: 483,328 bytes
Click here to return to the main page.
