2017-10-03 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-03-Hancitor-infection-with-ZLoader.pcap.zip 9.2 MB (9,199,3022 bytes)
- 2017-10-03-Hancitor-infection-with-ZLoader.pcap (10,109,051 bytes)
- 2017-10-03-Hancitor-malspam-3-examples.zip 3.3 kB (3,324 bytes)
- 2017-10-03-Hancitor-malspam-1610-UTC.eml (1,662 bytes)
- 2017-10-03-Hancitor-malspam-1630-UTC.eml (1,660 bytes)
- 2017-10-03-Hancitor-malspam-1641-UTC.eml (1,624 bytes)
- 2017-10-03-malware-from-Hancitor-infection.zip 267.7 kB (267,712 bytes)
- fax_672511.doc (335,360 bytes)
- iqry.exe (202,752 bytes)
TWEET ABOUT THE 2017-10-03 WAVE OF #HANCITOR:
- @cheapbyte: #malspam #Hancitor Ring Central New Incoming Fax phish Oct 3, 2017 URLs at https://pastebin.com/8G5kbpS6 updates as I get them (link to tweet)
EMAILS
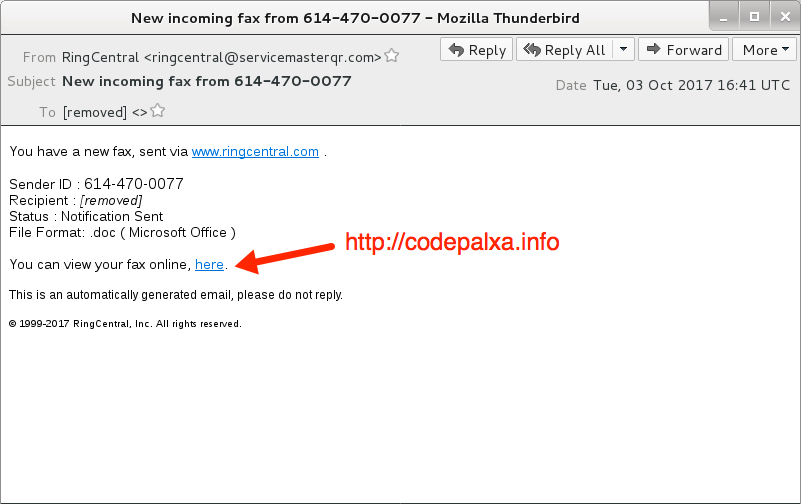
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date: Monday 2017-10-03 as early as 16:10 UTC through at least 16:41 UTC
- From: "RingCentral" <ringcentral@servicemasterqr[.]com>
- Subject: New incoming fax from 616-427-2464
- Subject: New incoming fax from 611-464-7872
- Subject: New incoming fax from 614-470-0077
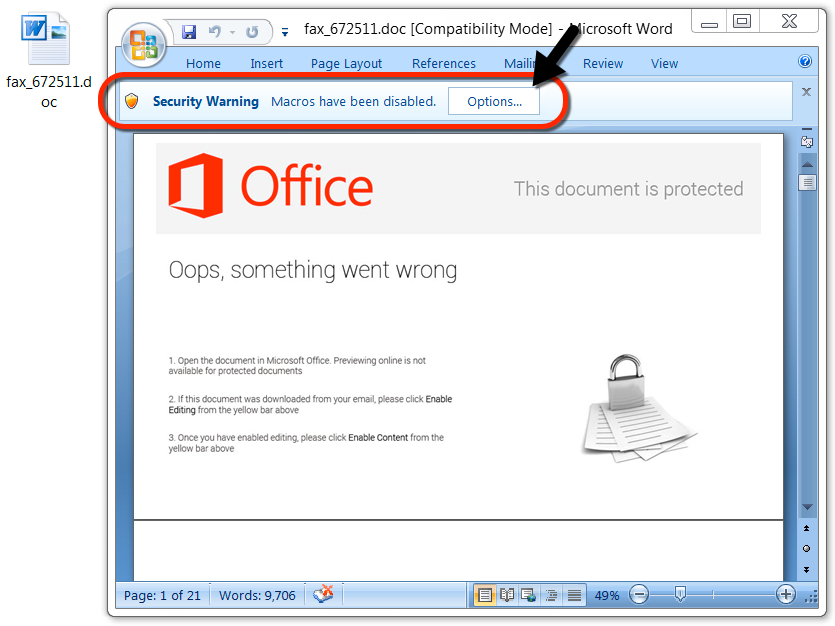
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
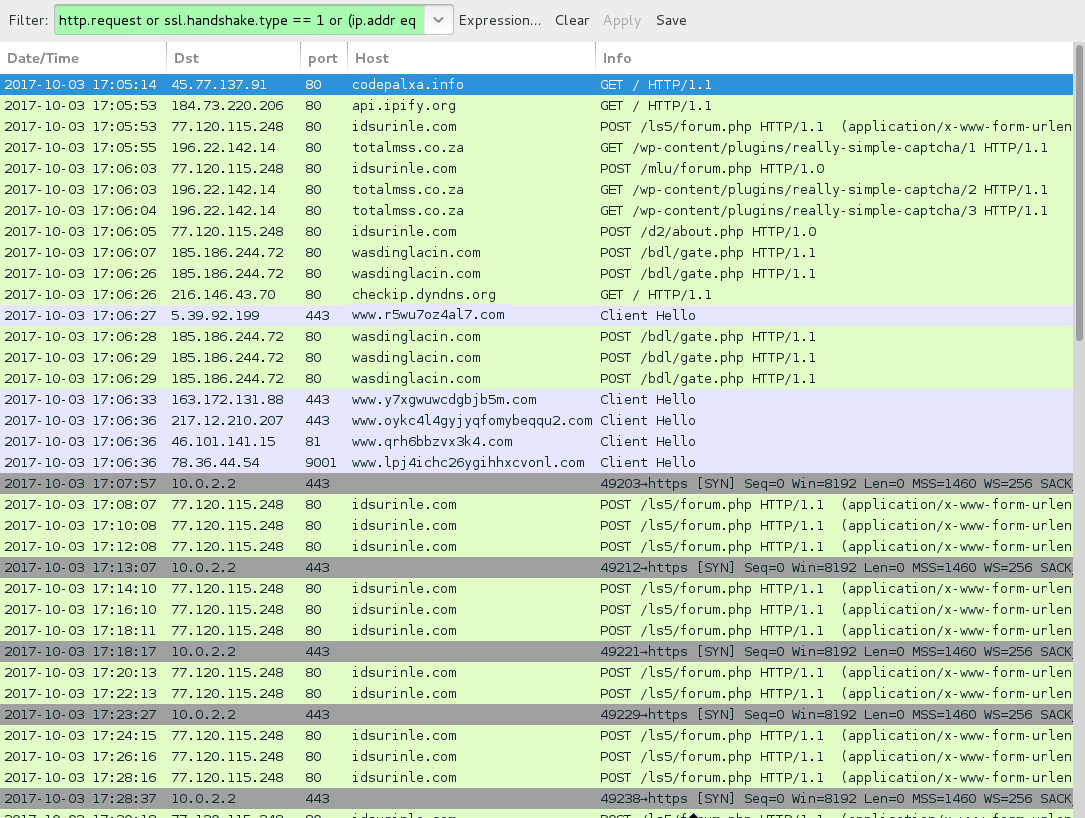
Shown above: Traffic from the infection filtered in Wireshark.
LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- codepalpreplanviewer[.]info - GET /
- codepalpreplanviewer[.]net - GET /
- codepalxa[.]info - GET /
NAME FOR THE MALICIOUS WORD DOCUMENT:
- fax_[six random digits].doc
POST-INFECTION TRAFFIC FROM MY INFECTED HOST:
- 77.120.115[.]248 port 80 - idsurinle[.]com - POST /ls5/forum.php
- 77.120.115[.]248 port 80 - idsurinle[.]com - POST /mlu/forum.php
- 77.120.115[.]248 port 80 - idsurinle[.]com - POST /d2/about.php
- 196.22.142[.]14 port 80 - totalmss[.]co[.]za - GET /wp-content/plugins/really-simple-captcha/1
- 196.22.142[.]14 port 80 - totalmss[.]co[.]za - GET /wp-content/plugins/really-simple-captcha/2
- 196.22.142[.]14 port 80 - totalmss[.]co[.]za - GET /wp-content/plugins/really-simple-captcha/3
- 185.186.244[.]72 port 80 - wasdinglacin[.]com - POST /bdl/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
- 10.0.2[.]2 port 443 - TCP SYN segment approx once avery 5 minutes
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 435c0c15f9fde201c221cdd60c25843230b0be00c5e84c35a23b2482d95e4d78
File name: fax_672511.doc
File size: 335,360 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 2d7f00766f24d453a31781ff25326bfa5f9fa9abea77239f3625df43e1b723a4
File location: C:\Users\[username]\AppData\Local\Temp\BN8C95.tmp
File location: C:\Users\[username]\AppData\Roaming\Abipeg\iqry.exe
File size: 202,752 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
