2017-10-03 - INFOSTEALER INFECTION VIA DLL SIDE-LOADING FROM BRAZIL MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-03-infostealer-infection-traffic.pcap.zip 2.1 MB (2,086,451 bytes)
- 2017-10-03-infostealer-infection-traffic.pcap (2,200,771 bytes)
- 2017-10-03-Brazil-malspam-1527-UTC.eml.zip 1.3 kB (1,261 bytes)
- 2017-10-03-Brazil-malspam-1527-UTC.eml (10,696 bytes)
- 2017-10-03-malware-from-infostealer-infection.zip 4.4 MB (4,433,417 bytes)
- Image05.zip (619,728 bytes)
- Fot0002.exe (1,494,016 bytes)
- 01.zip (1,595,257 bytes)
- CRYPTUI.dll (3,176,960 bytes)
- Yjnqqk.exe (32,856 bytes)
EMAIL INFORMATION:
- Date/Time: Tuesday, 2017-10-03 at 15:26 UTC
- From: [spoofed as recipient's email address]
- Subject: Fotos Enviadas via WhatsApp Messenger WEB 03/10/2017 12:26:50
- Link in the email: hxxps[:]//storage.googleapis[.]com/whatsap/web.html
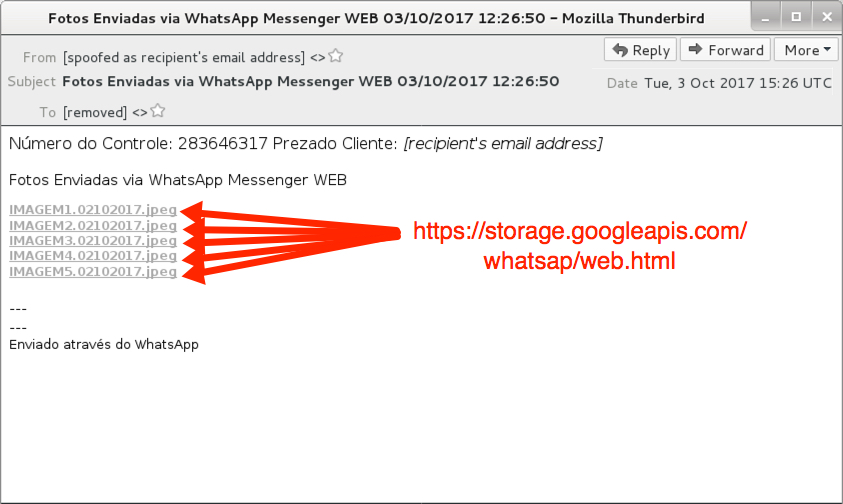
Shown above: Screenshot from the email.
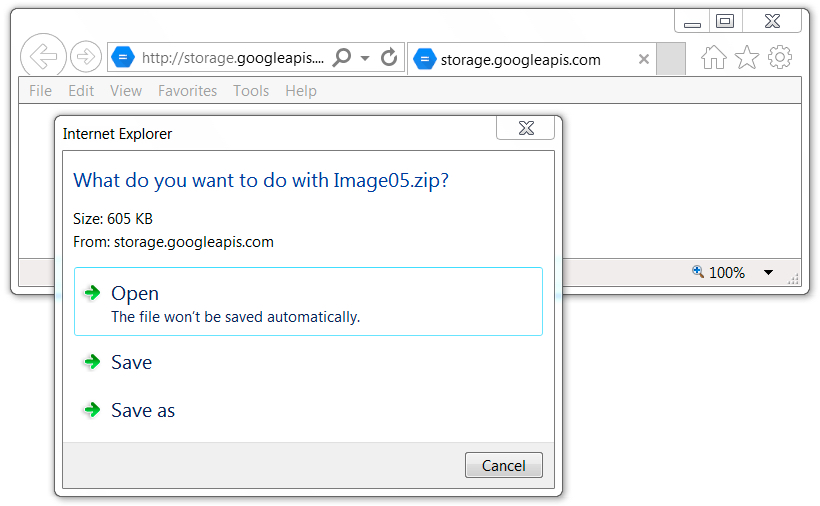
Shown above: Malicious zip archive from link in the malspam.
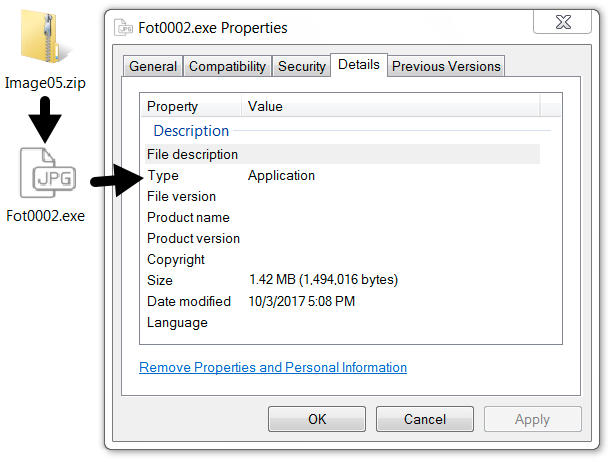
Shown above: Extracted malware from the downloaded zip archive.
TRAFFIC
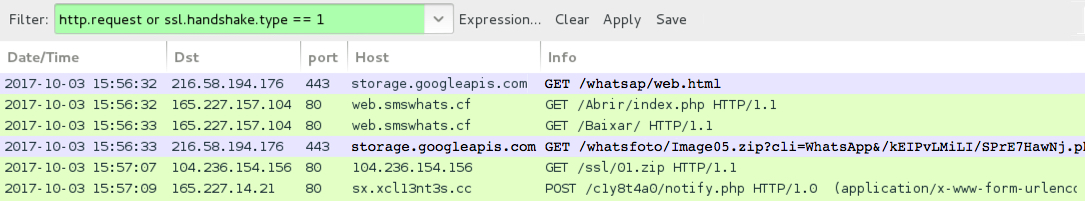
Shown above: Infection traffic filtered in Wireshark (image edited to show HTTPS URLs).
TRAFFIC FROM AN INFECTION:
- port 443 (HTTPS) - storage.googleapis[.]com - GET /whatsap/web.html
- 165.227.157[.]104 port 80 - web.smswhats[.]cf - GET /Abrir/index.php
- 165.227.157[.]104 port 80 - web.smswhats[.]cf - GET /Baixar/
- port 443 (HTTPS) - storage.googleapis[.]com - GET /whatsfoto/Image05.zip?cli=WhatsApp&/kEIPvLMiLI/SPrE7HawNj.php
- 104.236.154[.]156 port 80 - 104.236.154[.]156 - GET /ssl/01.zip
- 165.227.14[.]21 port 80 - sx.xcl13nt3s[.]cc - POST /c1y8t4a0/notify.php
FILE HASHES
ZIP ARCHIVE AFTER CLICKING LINK FROM THE EMAIL:
- SHA256 hash: e2215de00191f2a784d2000ab3978beed5e99f34f5b900fbf8fbcc6018a6b67c
File name: Image05.zip
File size: 619,728 bytes
EXTRACTED MALWARE FROM ZIP ARCHIVE:
- SHA256 hash: 57d411028a4859ec1cb3a2a198127382e479256a582f498215550318ae5f2d77
File name: Fot0002.exe
File size: 1,494,016 bytes
FOLLOW-UP MALWARE (1 OF 3):
- SHA256 hash: 19108623284d27fdc06c6165f9b8994d38f6a1823d8fa57f3e6622bf22ec5798
File location: hxxp[:]//104.236.154[.]156/ssl/01.zip
File size: 1,595,257 bytes
File description: Malicious zip archive downloaded from 104.236.154[.]156 by the initial malware
FOLLOW-UP MALWARE (2 OF 3):
- SHA256 hash: 8aba2557feffc7ef42e38d4fcd01ac89e01037e05056e4d1e0037478fadcc4b1
File location: C:\Users\[username]\AppData\Roaming\zJoeWmKgyp\CRYPTUI.dll
File size: 3,176,960 bytes
File description: DLL from follow-up malware archive, side-loaded by copy of legitimate Windows file for PVK/SPC to PFX file converter (pvk2pfx.exe)
FOLLOW-UP MALWARE (3 OF 3):
- SHA256 hash: f38a0519768ac094b635e4b4b6fbc836a04d87b1944f57499bd02404bfe670d9
File location: C:\Users\[username]\AppData\Roaming\zJoeWmKgyp\Yjnqqk.exe
File size: 32,856 bytes
File description: Copy of legitimate Windows file for PVK/SPC to PFX file converter (pvk2pfx.exe) to side-load malicious DLL named CRYPTUI.dll
IMAGES
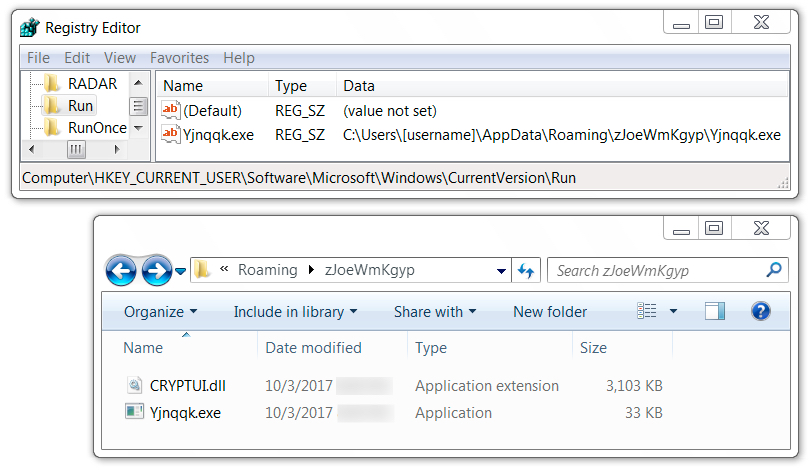
Shown above: Malware persistent on the infected host.
Click here to return to the main page.
