2017-10-03 - URSNIF INFECTION FROM JAPANESE MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-03-Ursnif-infection-traffic.pcap.zip 398.2 kB (398,196 bytes)
- 2017-10-03-Ursnif-infection-traffic.pcap (550,394 bytes)
- 2017-10-03-Japanese-malspam-pushing-Ursnif-7-examples.zip 151.9 kB (151,898 bytes)
- 2017-10-03-Japanese-malspam-for-Ursnif-0813-UTC.eml (63,890 bytes)
- 2017-10-03-Japanese-malspam-for-Ursnif-0815-UTC.eml (63,980 bytes)
- 2017-10-03-Japanese-malspam-for-Ursnif-0818-UTC.eml (64,049 bytes)
- 2017-10-03-Japanese-malspam-for-Ursnif-0923-UTC.eml (1,748 bytes)
- 2017-10-03-Japanese-malspam-for-Ursnif-0926-UTC.eml (1,693 bytes)
- 2017-10-03-Japanese-malspam-for-Ursnif-0930-UTC.eml (98,935 bytes)
- 2017-10-03-Japanese-malspam-for-Ursnif-0939-UTC.eml (98,822 bytes)
- 2017-10-03-malware-from-Ursnif-infection.zip 423.9 kB (423,858 bytes)
- 2017-10-03-Excel-file-pushing-Ursnif-example-1-of-2.xls (45,568 bytes)
- 2017-10-03-Excel-file-pushing-Ursnif-example-1-of-2.xls (71,680 bytes)
- 2017-10-03-Ursnif-binary-from-nonudoka_top.exe (483,328 bytes)
NOTES:
- From @tmmalanalyst - Oct-03,2017(JST). Japanese malspam attached XLS. Macro enabled infects #Ursnif #Malware. Leads file VT: (VT link) - (link to tweet)
- I saw this much later than @tmmalanalyst, when the domain for post-infection traffic was already off-line.
- Post-infection traffic in my pcap consists of DNS queries and repeated TCP SYN segments to the server that were unanswered.
EMAILS
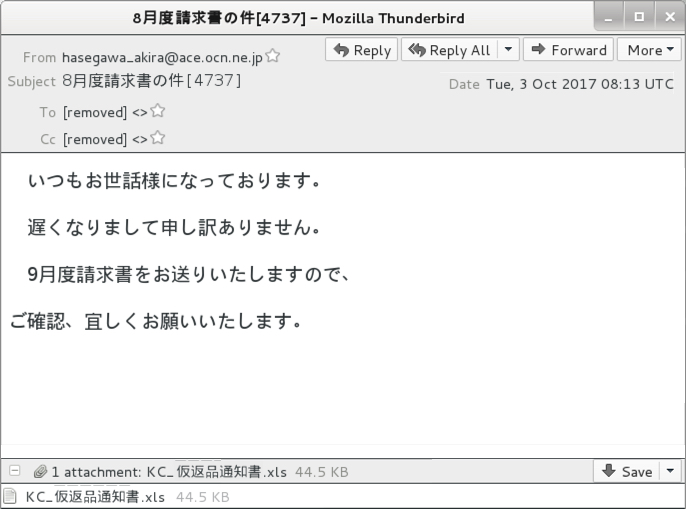
Shown above: Screenshot from an email (1 of 2).
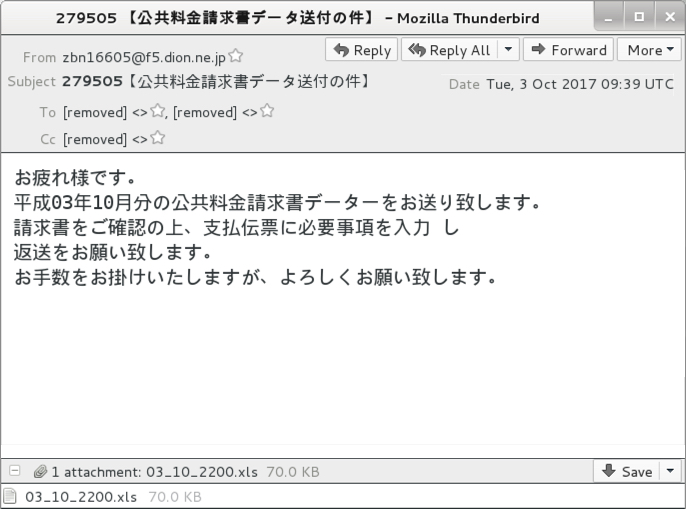
Shown above: Screenshot from an email (2 of 2).
INFORMATION FROM THE EMAILS:
- Date/Time: Tuesday 2017-10-03 as early as 08:13 UTC through at least 09:39 UTC
- From: apoa-shop@r9.dion[.]ne[.]jp
- From: hasegawa_akira@ace.ocn[.]ne[.]jp
- From: ikuo-nagasaki@jupiter.jcom[.]co[.]jp
- From: resets@docomo[.]ne[.]jp
- From: sato.takashi@dc5.so-net[.]ne[.]jp
- From: seikatsuhogo@kbh.biglobe[.]ne[.]jp
- From: zbn16605@f5.dion[.]ne[.]jp
- Subject: 8月度請求書の件[0430]
- Subject: 8月度請求書の件[4325]
- Subject: 8月度請求書の件[4737]
- Subject: 249647 【公共料金請求書データ送付の件】
- Subject: 279505 【公共料金請求書データ送付の件】
- Subject: 436329 【公共料金請求書データ送付の件】
- Subject: 607225 【公共料金請求書データ送付の件】
- Attachment name: KC_仮返品通知書.xls
- Attachment name: 3V_仮返品通知書.xls
- Attachment name: SJ_仮返品通知書.xls
- Attachment name: 03_10_1452.xls
- Attachment name: 03_10_1765.xls
- Attachment name: 03_10_2200.xls
- Attachment name: 03_10_2783.xls
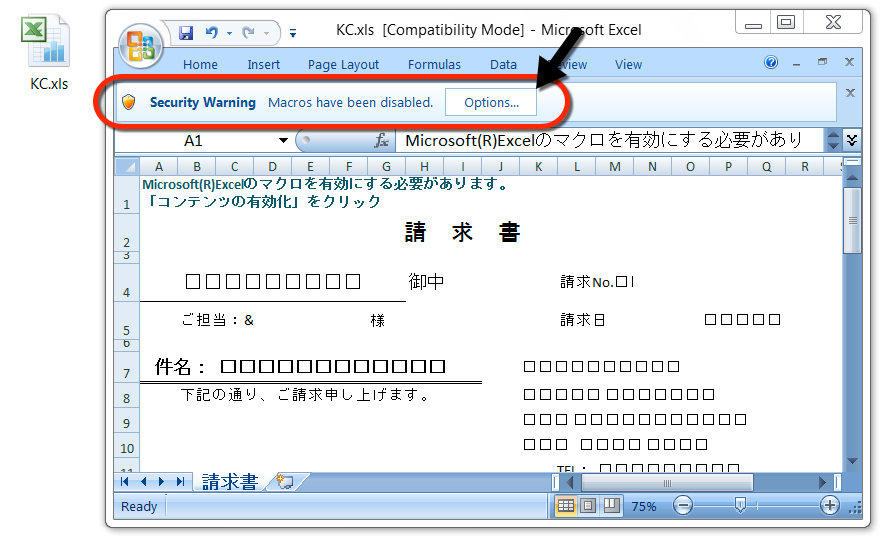
Shown above: Example of an Excel spreadsheet (1 of 2).
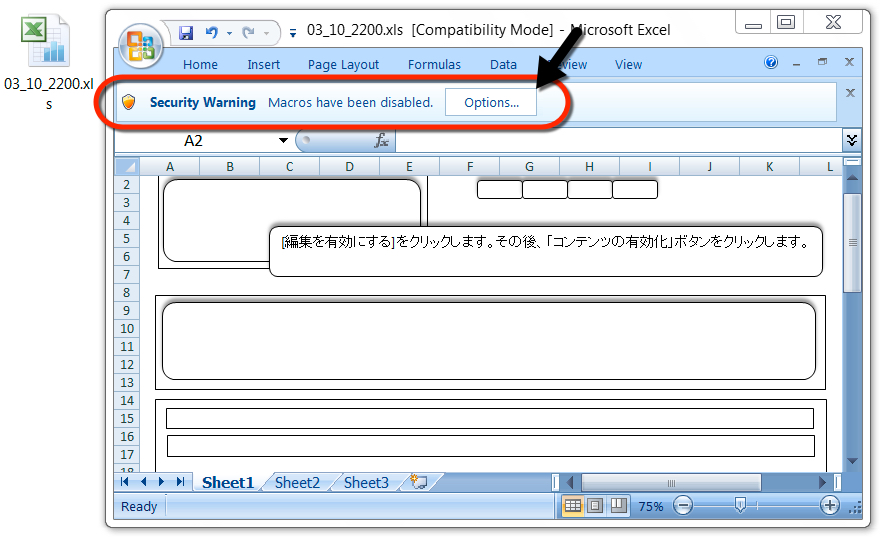
Shown above: Example of an Excel spreadsheet (2 of 2).
TRAFFIC
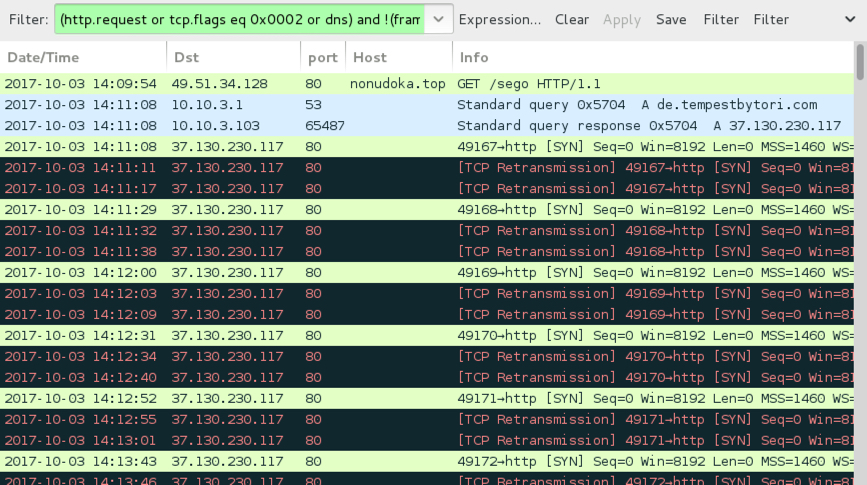
Shown above: Traffic from an infection filtered in Wireshark (only DNS queries and TCP SYN segments for post-infection activity).

Shown above: Screenshot of Fiddler capture when @tmmalanalyst checked it out earlier (link to tweet).
TRAFFIC FROM AN INFECTION:
- 49.51.34[.]128 port 80 - nonudoka[.]top - GET /index [generated by first Excel spreadsheet]
- 49.51.34[.]128 port 80 - nonudoka[.]top - GET /sego [generated by second Excel spreadsheet]
- 49.51.34[.]128 port 80 - nonudoka[.]top - GET /sato [seen by @tmmalanalyst earlier]
POST-INFECTION TRAFFIC:
- 37.130.230[.]117 port 80 - de.tempestbytori[.]com - GET /images/[long string].[image-based file extension]
- 37.130.230[.]117 port 80 - de.tempestbytori[.]com - POST /images/[long string].[image-based file extension]
FILE HASHES
EMAIL ATTACHMENT 1 OF 2:
- SHA256 hash: f6e22dc206adda972b4b92ccd7461cf8a269cc991bbde8890aa3a348f667c22e
File size: 45,568 bytes
File name: [2 random English letters]_仮返品通知書.xls
EMAIL ATTACHMENT 2 OF 2:
- SHA256 hash: d9cf40c30220b575e8a3a5c31e95a37dc5439474663f4d5bf3271c8adaa9489b
File size: 71,680 bytes
File name: 03_10_[4-digit number].xls
FOLLOW-UP MALWARE - URSNIF:
- SHA256 hash: 16f6b86ef2e83aa4acefe9a46af19ead99887f845f3c79987c3d039354e657c4
File size: 562,688 bytes
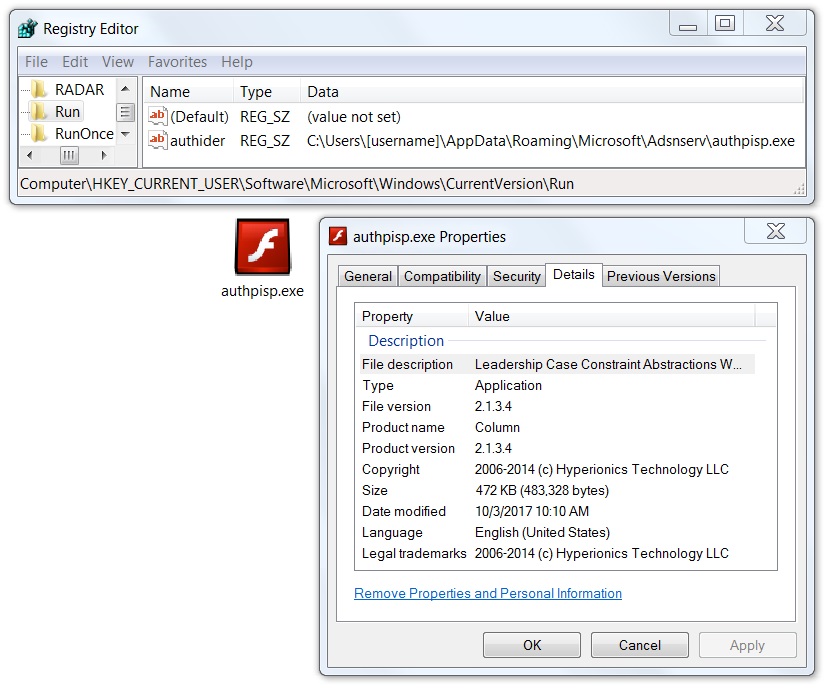
File location: C:\Users\[username]\AppData\Roaming\Microsoft\Adsnserv\authpisp.exe
Shown above: Malware persistent on the infected Windows host.
Click here to return to the main page.