2017-10-05 - HANCITOR INFECTION WITH DELOADER/ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-05-Hancitor-infection-with-ZLoader.pcap.zip 9.2 MB (9,200,298 bytes)
- 22017-10-05-Hancitor-infection-with-ZLoader.pcap (9,860,952 bytes)
- 2017-10-05-Hancitor-malspam-3-examples.zip 4.9 kB (4,925 bytes)
- 2017-10-05-Hancitor-malspam-1619-UTC.eml (14,470 bytes)
- 2017-10-05-Hancitor-malspam-1816-UTC.eml (897 bytes)
- 2017-10-05-Hancitor-malspam-1824-UTC.eml (968 bytes)
- 2017-10-05-malware-from-Hancitor-infection.zip 266.9 kB (266,889 bytes)
- Ymqyod-opdei.exe (209,920 bytes)
- ebook_338683.doc (215,040 bytes)
TWITTER THREAD COVERING THE 2017-10-05 WAVES OF #HANCITOR MALSPAM:
- @James_inthe_box: LoL...props to @theauldfella new #hancitor run: "Make Hacking Difficult": details coming. [Pastebin link] (link to Twitter thread)
- NOTE: The above thread includes tweets from @cheapbyte, @Ring0x0, and @theauldfella. Lots of good information there.
EMAILS
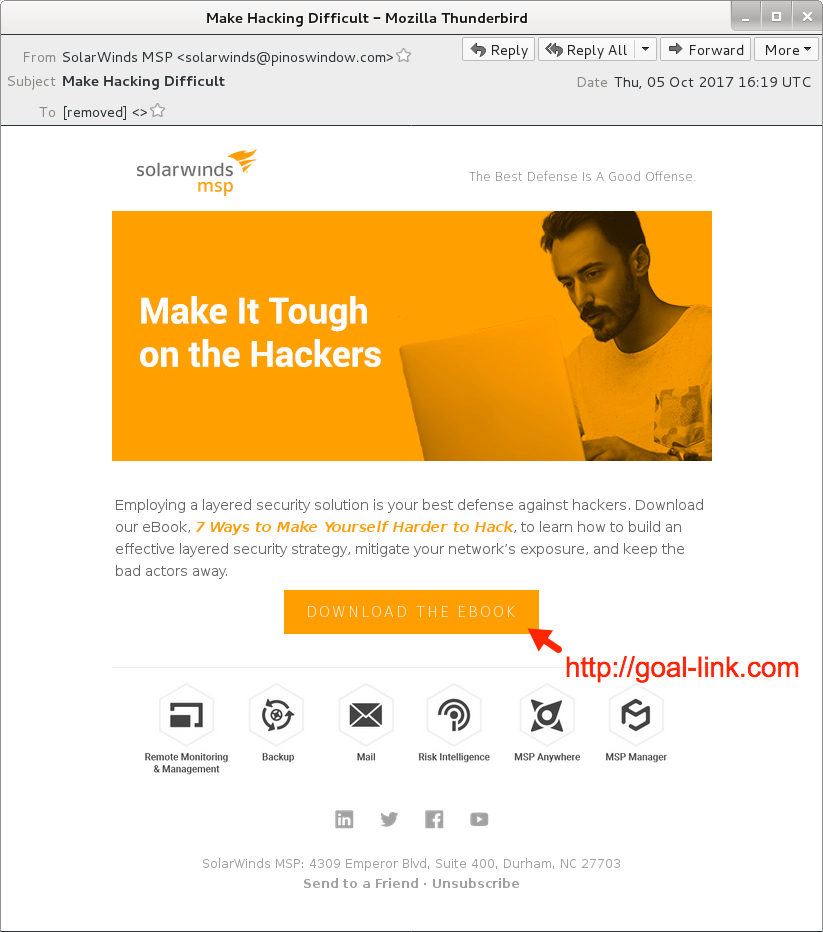
Shown above: Screenshot from an email in the 1st wave.
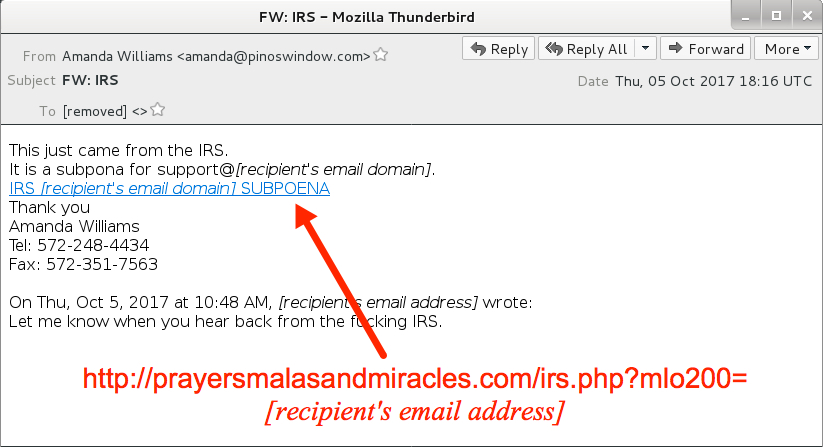
Shown above: Screenshot from an email in the 2nd wave.
EMAIL HEADERS - EXAMPLE FROM 1ST WAVE:
- Received: from pinoswindow[.]com ([98.121.97[.]230])
- Message-ID: <90A5FF8C.69178186@pinoswindow[.]com>
- X-Mailer: Apple Mail (2.1084)
- Date: Thursday, 2017-10-05 16:19 UTC
- Subject: Make Hacking Difficult
- From: "SolarWinds MSP" <solarwinds@pinoswindow[.]com>
EMAIL HEADERS - EXAMPLES FROM 2ND WAVE:
- Received: from pinoswindow[.]com ([74.194.10[.]145])
- Message-ID: <D5826C13.86826E22@pinoswindow[.]com>
- X-Mailer: iPad Mail (12A405)
- Date: Thursday, 2017-10-05 18:16 UTC
- Subject: FW: IRS
- From: "Amanda Williams" <amanda@pinoswindow[.]com>
- Received: from pinoswindow[.]com ([66.192[.]5.38])
- Message-ID: <1B5D6051.685F45BD@pinoswindow[.]com>
- X-Mailer: iPhone Mail (13A452)
- Date: Thursday, 2017-10-05 18:24 UTC
- Subject: FW: IRS
- From: "Amanda Williams" <amanda@pinoswindow[.]com>
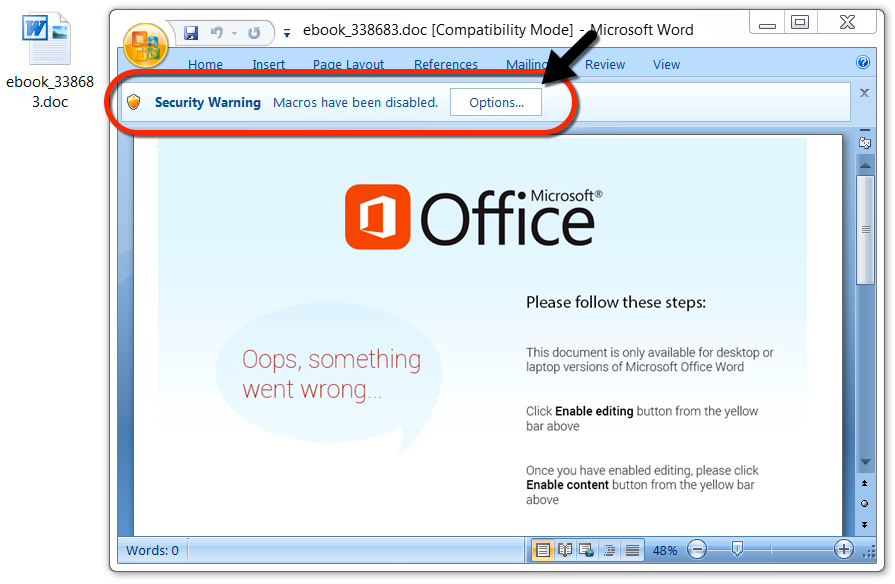
Shown above: Malicious Word document from one of the malspam links.
TRAFFIC
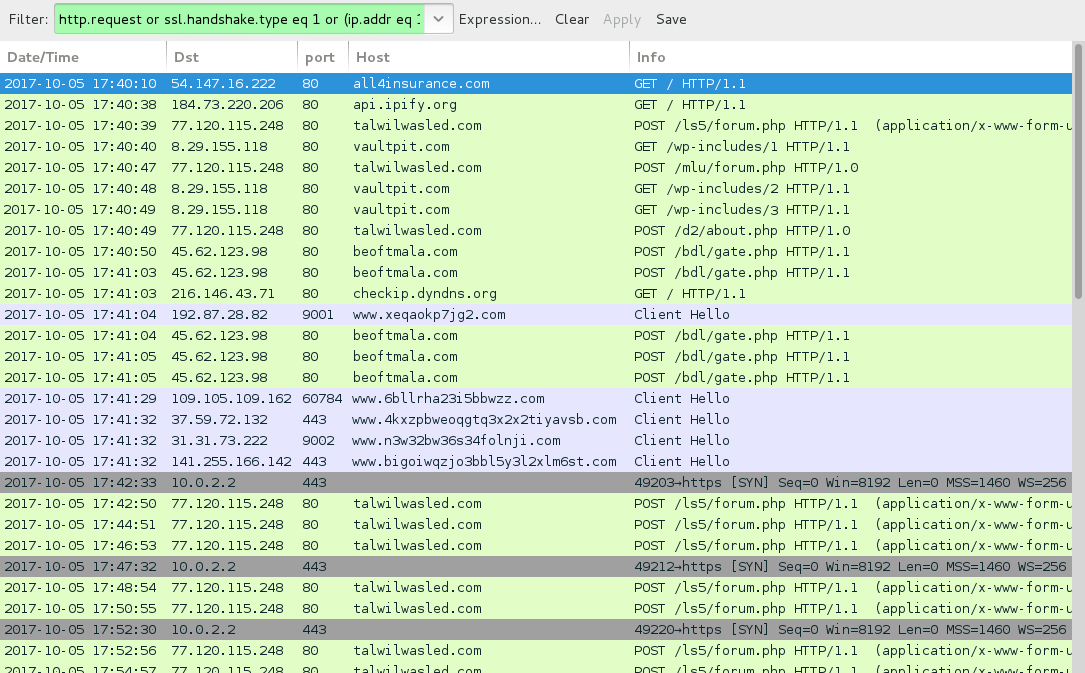
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- all4insurance[.]com - GET /
- goal-link[.]com - GET /
- prayersmalasandmiracles[.]com - GET /irs.php?mlo200=[recipient's email address]
- satyainstitute[.]info - GET /irs.php?mat027=[recipient's email address]
NAME FOR THE MALICIOUS WORD DOCUMENT:
- ebook_[six random digits].doc
POST-INFECTION TRAFFIC FROM MY INFECTED HOST:
- 77.120.115[.]248 port 80 - talwilwasled[.]com - POST /ls5/forum.php
- 77.120.115[.]248 port 80 - talwilwasled[.]com - POST /mlu/forum.php
- 77.120.115[.]248 port 80 - talwilwasled[.]com - POST /d2/about.php
- 8.29.155[.]118 port 80 - vaultpit[.]com - GET /wp-includes/1
- 8.29.155[.]118 port 80 - vaultpit[.]com - GET /wp-includes/2
- 8.29.155[.]118 port 80 - vaultpit[.]com - GET /wp-includes/3
- 45.62.123[.]98 port 80 - beoftmala[.]com - POST /bdl/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
- 10.0.2.2 port 443 - TCP SYN packet approx once avery 5 minutes
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 3ab1f686ce7355bd4405e66aacb148cea198ceb26cd1c0b15b9ddd7c3d68a682
File name: ebook_338683.doc
File size: 215,040 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM AN INFECTED HOST:
- SHA256 hash: 6dfdfdc18b93c0805417a4aa850da17fe352d9d7a8e774f9398b581addd228ef
File location: C:\Users\[username]\AppData\Local\Temp\BN1016.tmp
File location: C:\Users\[username]\AppData\Roaming\Ymqyod\opdei.exe
File size: 209,920 bytes
File description: DELoader/ZLoader
IMAGES
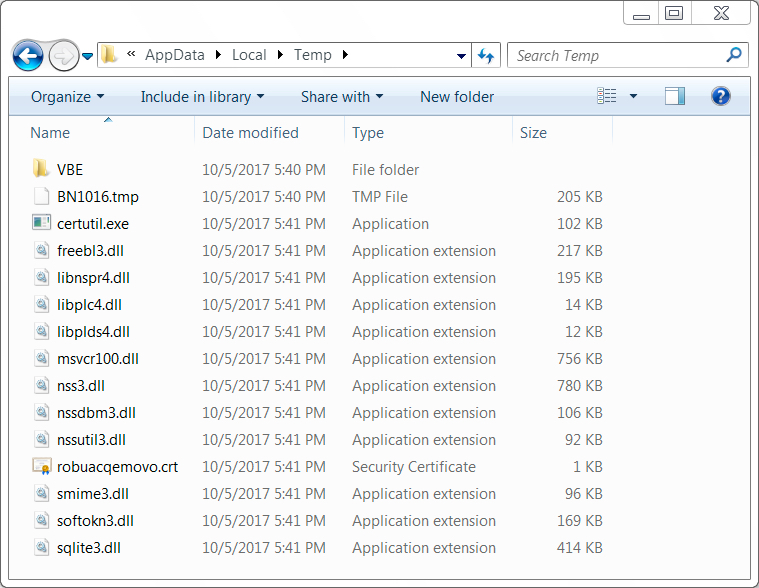
Shown above: Artifacts from an infected host in the user's AppData\Local\Temp directory.
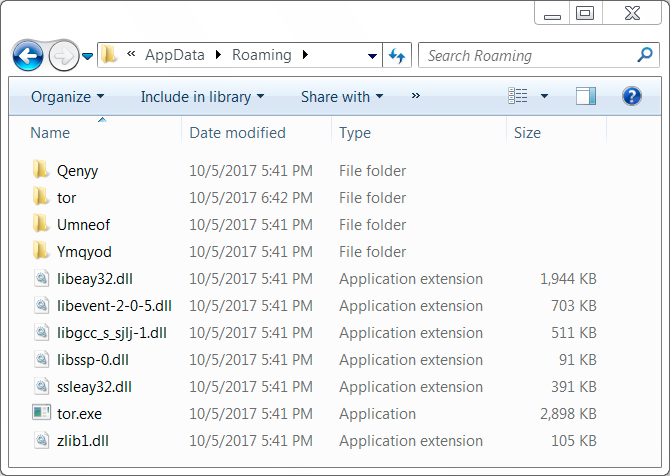
Shown above: Artifacts from an infected host in the user's AppData\Roaming directory.
Click here to return to the main page.
