2017-10-09 - ADWIND/JRAT INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-09-Adwind-jRAT-infection-traffic.pcap.zip 1.7 MB (1,747,619 bytes)
- 2017-10-09-Adwind-jRAT-infection-traffic.pcap (1,906,937 bytes)
- 2017-10-09-Adwind-jRAT-malspam-1233-UTC.eml.zip 1.4 kB (1,422 bytes)
- 2017-10-09-Adwind-jRAT-malspam-1233-UTC.eml (3,870 bytes)
- 2017-10-09-Adwind-jRAT-malware.zip 1.5 MB (1,501,520 bytes)
- 132_6473_3432_NH89_4984.Pdf.jar (542,676 bytes)
- okPfqKdaTp.AGyqe.jar (968,702 bytes)
NOTES:
- Even though it's been several months since I last examined one of these in-depth, they are a near-daily occurrence, probably caught by many organizations' spam filters.
- No detections on the downloaded .jar file when I first submitted it to VirusTotal (link).
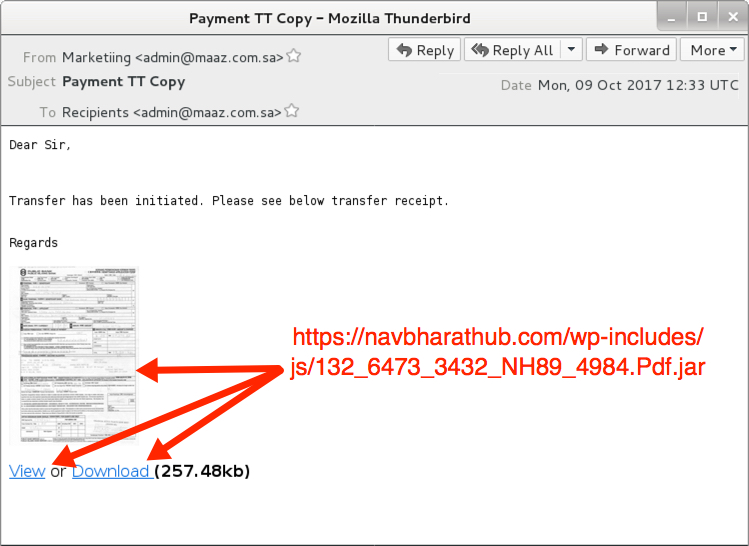
Shown above: Screenshot of the email.
EMAIL HEADERS:
- Received: from vweb2.america.net ([69.60.160[.]146]) by [removed] for [removed];
Mon, 09 Oct 2017 12:33:03 +0000 (UTC) - Recieved: from [82.221.137[.]163] (port=2306 helo=[100.120.232.246])
by vweb2.america[.]net with esmtpa (Exim 4.89)
(envelope-from <admin@maaz[.]com[.]sa>)
id 1e1XEq-0000DK-Po; Mon, 09 Oct 2017 08:32:53 -0400 - Date: Monday, 2017-10-09 12:33 UTC
- Subject: Payment TT Copy
- From: "Marketiing" <admin@maaz[.]com[.]sa>
- To: Recipients <admin@maaz[.]com[.]sa>
- Link from the email: hxxps[:]//navbharathub[.]com/wp-includes/js/132_6473_3432_NH89_4984.Pdf.jar
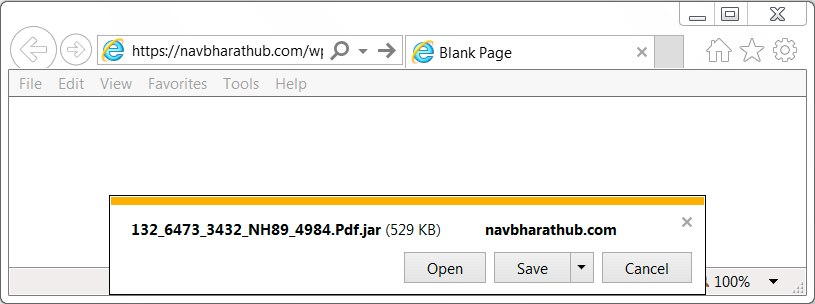
Shown above: Clicking link from the email.
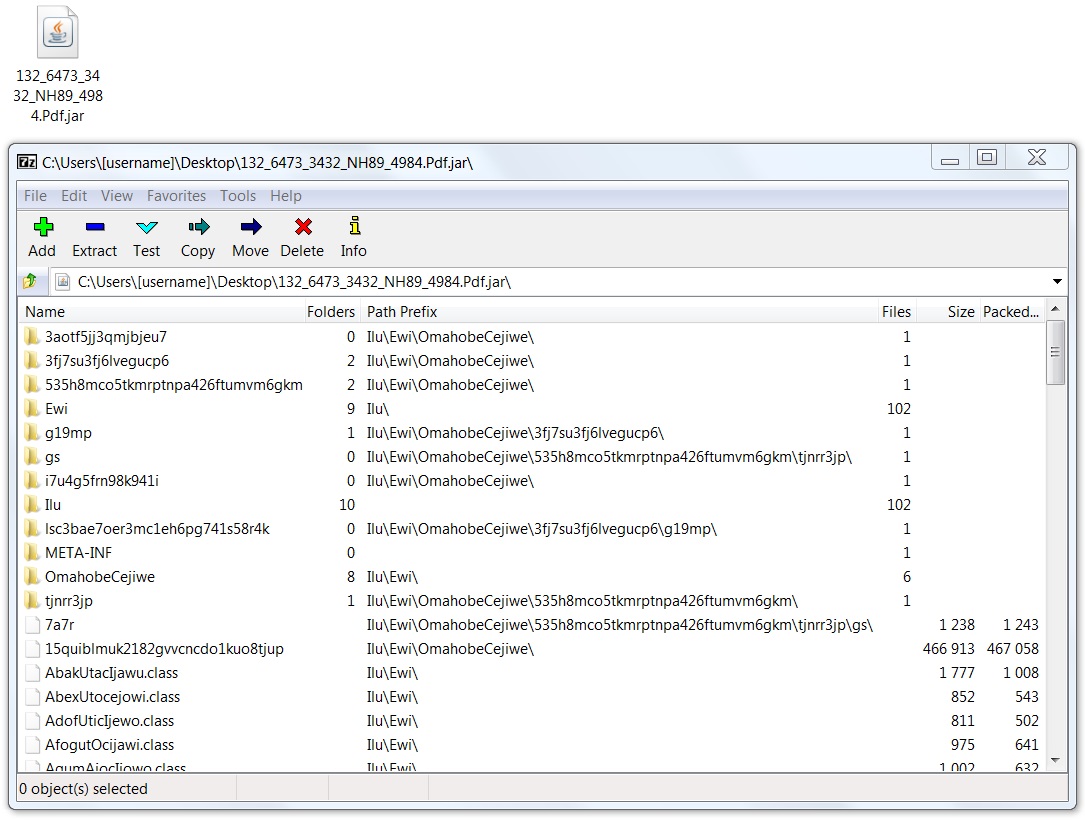
Shown above: The downloaded Java archive (.jar) file.
TRAFFIC
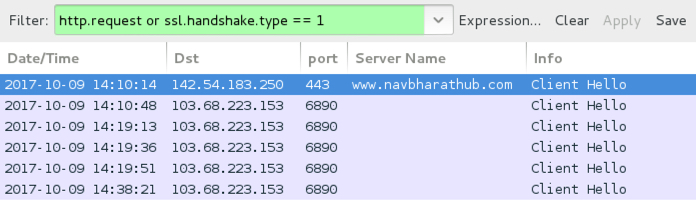
Shown above: Traffic from this infection filtered in Wireshark.
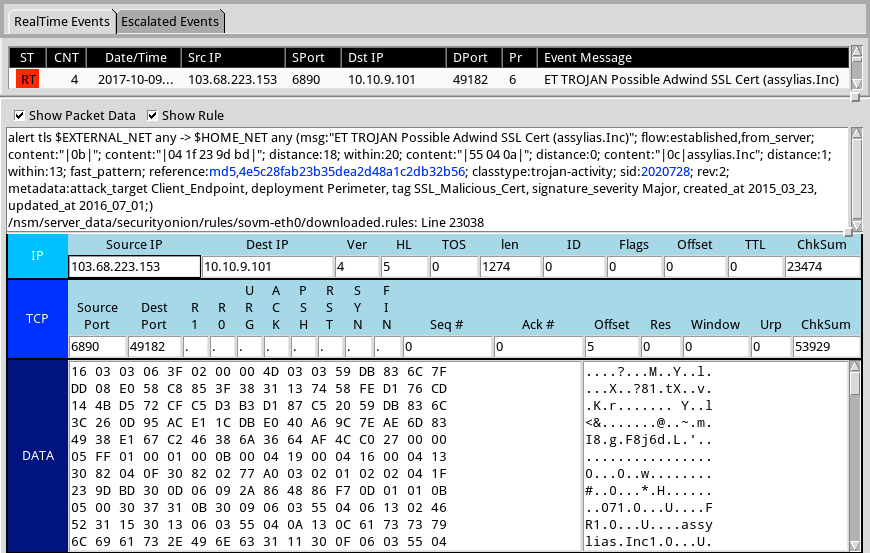
Shown above: Alerts on the infection traffic using the Emerging Threats and ETPRO rulesets in Sguil on Security Onion.
ASSOCIATED DOMAINS AND URLS:
- 142.54.183[.]250 port 443 (HTTPS) - navbharathub[.]com - GET /wp-includes/js/132_6473_3432_NH89_4984.Pdf.jar
- 103.68.223[.]153 port 6890 - post-infection encrypted HTTPS/SSL/TLS traffic
FILE HASHES
DOWNLOADED .JAR FILE:
- SHA256 hash: c3a3ac48b3c6e0f7e48c7a2bb2dc3fa4f2c8d5fd0fcf1e0bce096b6b0f50eccf
File size: 542,676 bytes
File name: 132_6473_3432_NH89_4984.Pdf.jar
Post-infection location: C:\Users\[username]\hTBSbSQOSVI\YwTcLBZyPPH.PETGfB
ADDITIONAL .JAR FILE FROM THE INFECTED HOST:
- SHA256 hash: c5387a9af9ee4ee5809d59680161059c03c029794dec391b142a97baa8d5d42c
File size: 968,702 bytes
File location: C:\Users\[username]\hTBSbSQOSVI\RpWUQqBarwJ\okPfqKdaTp.AGyqe
NOTE: possibly a corrupt archive.
IMAGES
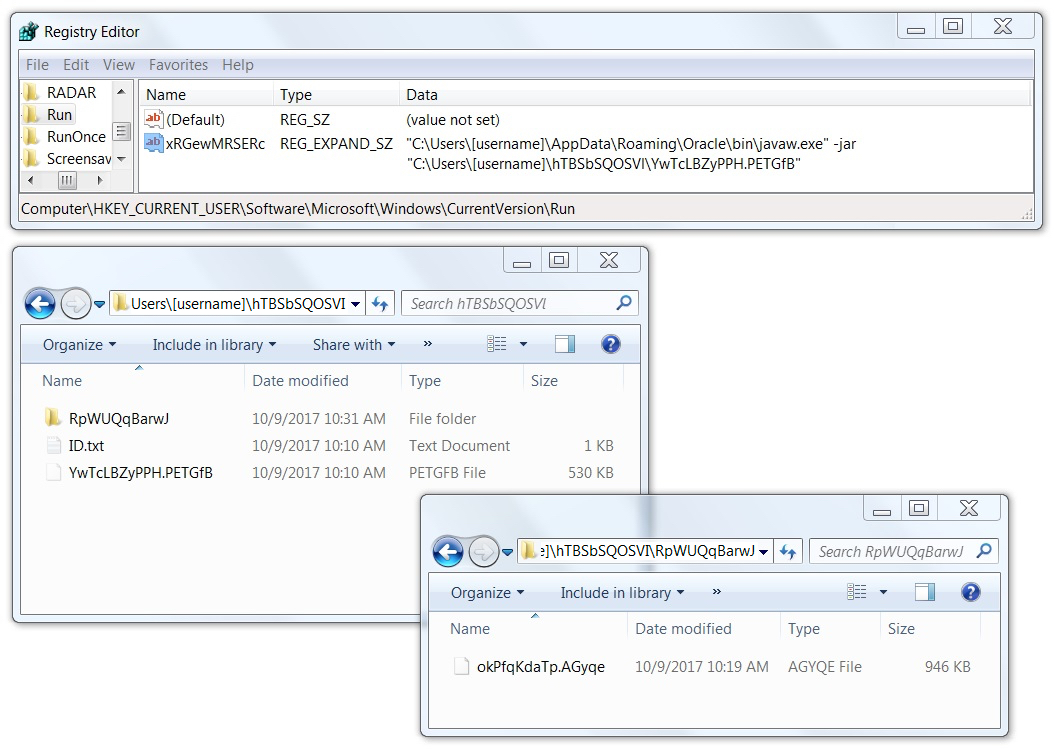
Shown above: Windows Registry updates and associated files on the infected host.
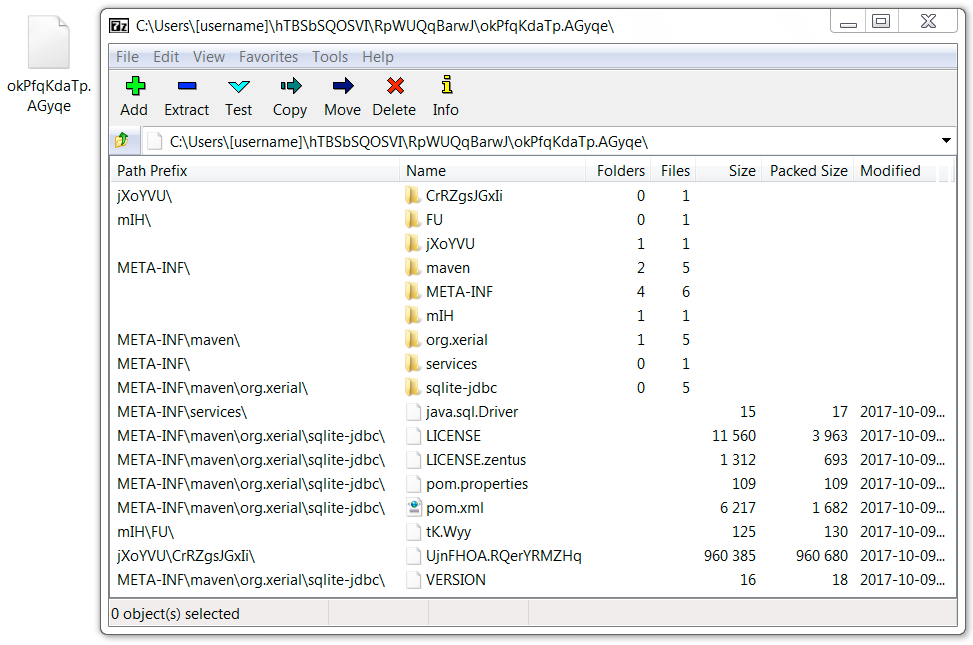
Shown above: Content of the other .jar archive from the infected Windows host.
Click here to return to the main page.
