2017-10-11 - PHISHING WEBSITE TRAFFIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-11-Docusign-themed-phish-traffic.saz.zip 311.1 kB (311,077 bytes)
- 2017-10-11-Docusign-phish-1425-UTC.eml.zip 1.7 kB (1,744 bytes)
- 2017-10-11-phishing-kit-from-compromised-site.zip 1.8 MB (1,808,714 bytes)
NOTES:
- I submitted the associated URLs to PhishTank, so feel free to verify them. Accounts on PhishTank are free, and they only require a working email address.
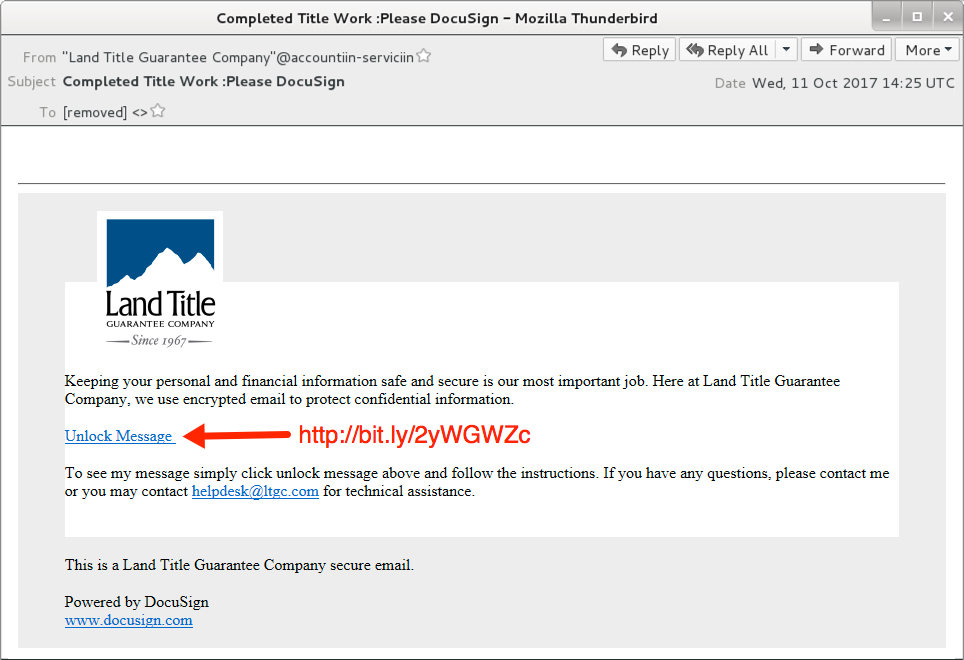
Shown above: Screenshot of the email.
EMAIL HEADERS:
- Date: Wednesday, 2017-10-11 14:25 UTC
- Message-ID: <E1e2HwY-0000sz-2w@SRV-WEB>
- Subject: Completed Title Work :Please DocuSign
- From: <Land Title Guarantee Company@accountiin-serviciin>
- Reply-To: Land Title Guarantee Company@accountiin-serviciin
- Link in the email: hxxp[:]//bit[.]ly/2yWGWZc

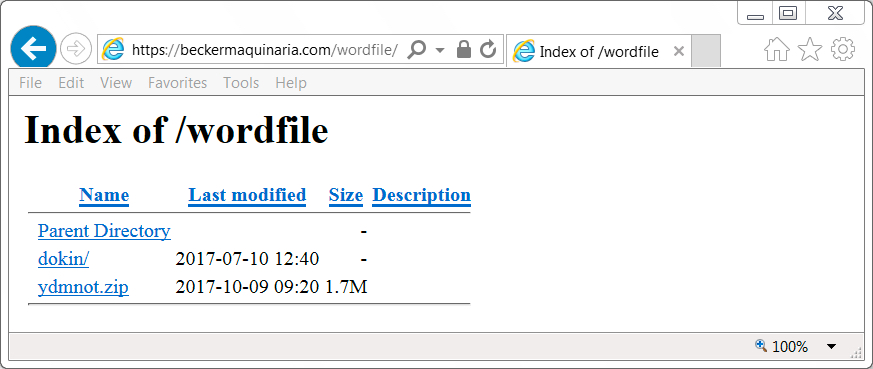
Shown above: Initial phishing page.
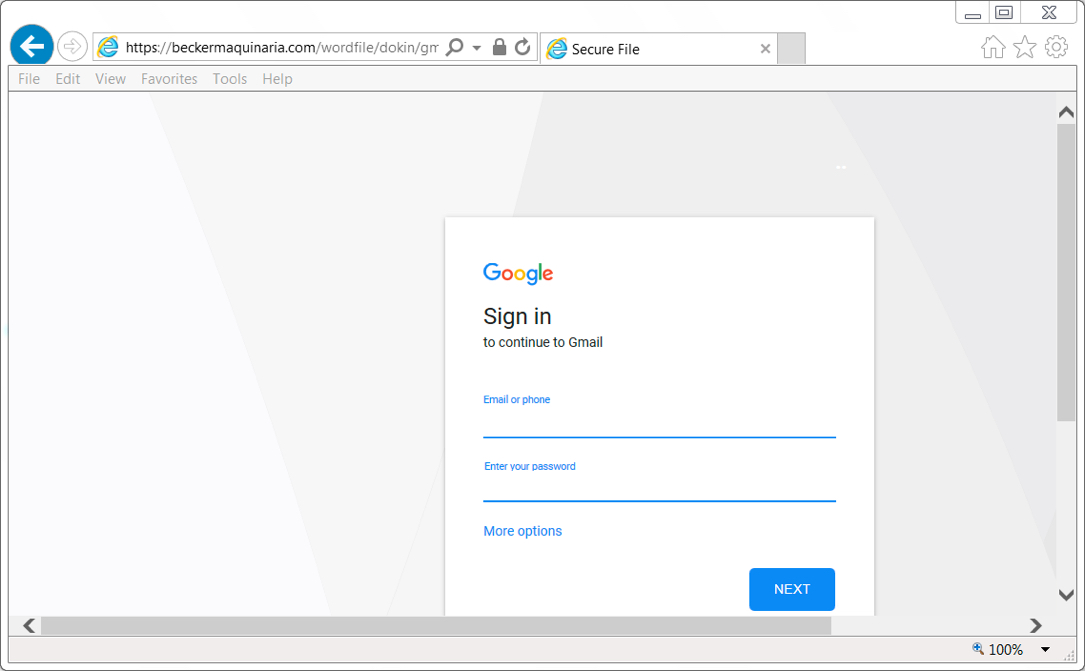
Shown above: Fake gmail login (one of many different login options).

Shown above: Fake recovery email and phone.
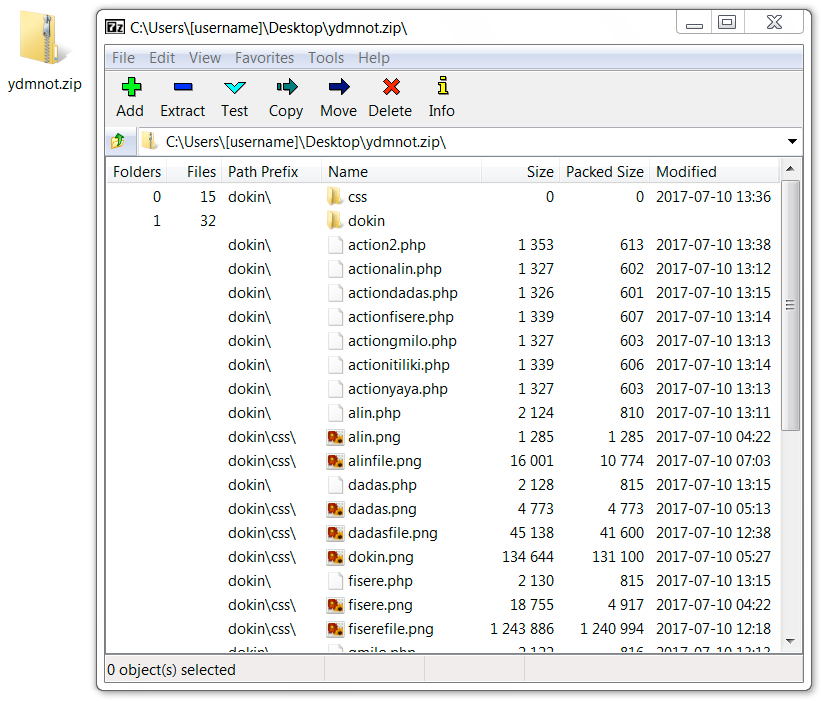
Shown above: Phishing kit zip archive from the compromised website.
TRAFFIC
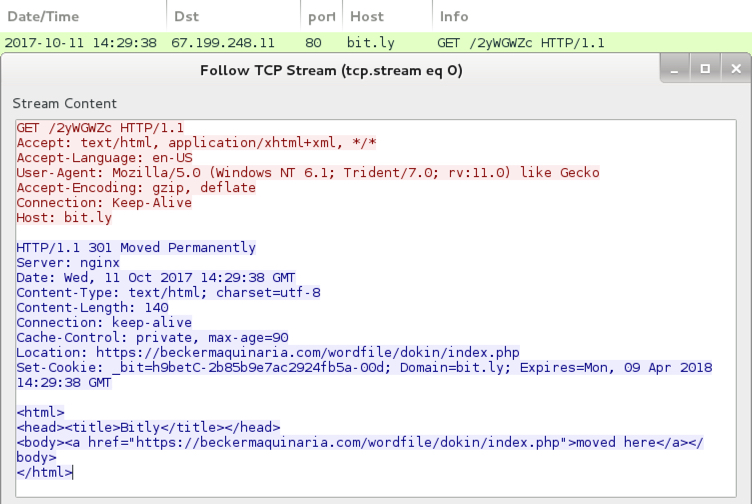
Shown above: Traffic in Wireshark shows Bit[.]ly link going to HTTPS URL.
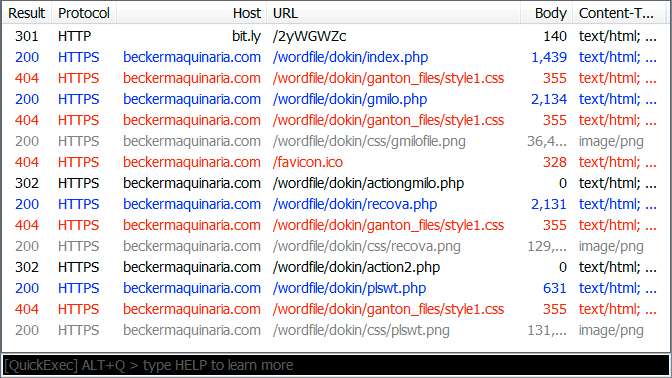
Shown above: HTTPS URLs as recorded in Fiddler.
ASSOCIATED URLS:
- port 80 - bit[.]ly - GET /2yWGWZc
- port 443 (HTTPS) - beckermaquinaria[.]com - GET /wordfile/dokin/index.php
- port 443 (HTTPS) - beckermaquinaria[.]com - GET /wordfile/dokin/ganton_files/style1.css
- port 443 (HTTPS) - beckermaquinaria[.]com - GET /wordfile/dokin/gmilo.php
- port 443 (HTTPS) - beckermaquinaria[.]com - GET /wordfile/dokin/css/gmilofile.png
- port 443 (HTTPS) - beckermaquinaria[.]com - GET /wordfile/dokin/actiongmilo.php
- port 443 (HTTPS) - beckermaquinaria[.]com - GET /wordfile/dokin/recova.php
- port 443 (HTTPS) - beckermaquinaria[.]com - GET /wordfile/dokin/css/recova.png
- port 443 (HTTPS) - beckermaquinaria[.]com - GET /wordfile/dokin/action2.php
- port 443 (HTTPS) - beckermaquinaria[.]com - GET /wordfile/dokin/plswt.php
- port 443 (HTTPS) - beckermaquinaria[.]com - GET /wordfile/dokin/css/plswt.png
MALWARE
PHISHING KIT FROM COMPROMISED SITE:
- SHA256 hash: 3d7e7ee432f5c9843f48bce7a4b42a25bcdfc5f4083598ef40ff59c10a01bd0d
File size: 1,808,204 bytes
File name: ydmnot.zip
Shown above: Contents of the phishing kit.
Click here to return to the main page.