2017-10-11 - FTFY: NECURS BOTNET MALSPAM PUSHING ".ASASIN" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-11-Necurs-botnet-malspam-pushes-Locky-ransomware.pcap.zip 446.2 kB (446,172 bytes)
- 2017-10-11-Necurs-Botnet-malspam-tracker.csv.zip 1.4 kB (1,433 bytes)
- 2017-10-11-emails-and-malware-from-Necurs-botnet-and-Locky-ransomware.zip 647.1 kB (647,120 bytes)
NOTES:
- A new variant of Locky ransomware has been using the .asasin file extension since Tuesday 2017-10-10.
- Both yesterday and today, some emails from the Necurs Botnet have had messed up formatting, so they didn't display properly.
- I've included samples of the messed up ones from yesterday and today that I've fixed for this blog post (FTFY = Fixed That For You).
Shown above: This malspam wouldn't do well on the Maury Povich Show.
EMAILS
EMAILS COLLECTED:
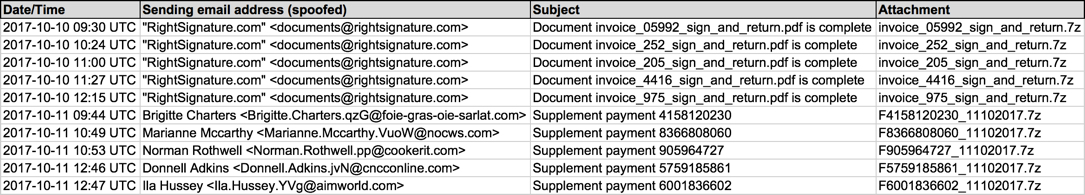
Shown above: Screenshot showing part of the spreadsheet data.
Read: Date/Time -- Sending email address (spoofed) -- Subject
- 2017-10-10 09:30 UTC -- "RightSignature[.]com" <documents@rightsignature[.]com> -- Document invoice_05992_sign_and_return.pdf is complete
- 2017-10-10 10:24 UTC -- "RightSignature[.]com" <documents@rightsignature[.]com> -- Document invoice_252_sign_and_return.pdf is complete
- 2017-10-10 11:00 UTC -- "RightSignature[.]com" <documents@rightsignature[.]com> -- Document invoice_205_sign_and_return.pdf is complete
- 2017-10-10 11:27 UTC -- "RightSignature[.]com" <documents@rightsignature[.]com> -- Document invoice_4416_sign_and_return.pdf is complete
- 2017-10-10 12:15 UTC -- "RightSignature[.]com" <documents@rightsignature[.]com> -- Document invoice_975_sign_and_return.pdf is complete
- 2017-10-11 09:44 UTC -- Brigitte Charters <Brigitte.Charters.qzG@foie-gras-oie-sarlat[.]com> -- Supplement payment 4158120230
- 2017-10-11 10:49 UTC -- Marianne Mccarthy <Marianne.Mccarthy.VuoW@nocws[.]com> -- Supplement payment 8366808060
- 2017-10-11 10:53 UTC -- Norman Rothwell <Norman.Rothwell.pp@cookerit[.]com> -- Supplement payment 905964727
- 2017-10-11 12:46 UTC -- Donnell Adkins <Donnell.Adkins.jvN@cncconline[.]com> -- Supplement payment 5759185861
- 2017-10-11 12:47 UTC -- Ila Hussey <Ila.Hussey.YVg@aimworld[.]com> -- Supplement payment 6001836602
Read: Date/Time -- Attachment name -- Extracted file name
- 2017-10-10 09:30 UTC -- invoice_05992_sign_and_return.7z -- invoice_86616_sign_and_return.vbs
- 2017-10-10 10:24 UTC -- invoice_252_sign_and_return.7z -- invoice_12397_sign_and_return.vbs
- 2017-10-10 11:00 UTC -- invoice_205_sign_and_return.7z -- invoice_64789_sign_and_return.vbs
- 2017-10-10 11:27 UTC -- invoice_4416_sign_and_return.7z -- invoice_45399_sign_and_return.vbs
- 2017-10-10 12:15 UTC -- invoice_975_sign_and_return.7z -- invoice_34679_sign_and_return.vbs
- 2017-10-11 09:44 UTC -- F4158120230_11102017.7z -- F8906797410.vbs
- 2017-10-11 10:49 UTC -- F8366808060_11102017.7z -- F7946586192.vbs
- 2017-10-11 10:53 UTC -- F905964727_11102017.7z -- F7559397046.vbs
- 2017-10-11 12:46 UTC -- F5759185861_11102017.7z -- F8030796365.vbs
- 2017-10-11 12:47 UTC -- F6001836602_11102017.7z -- F6884593454.vbs
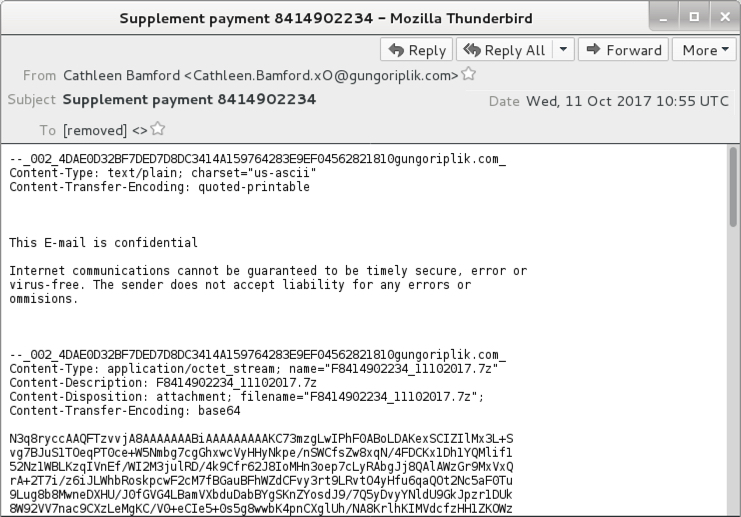
Shown above: One of today's emails as seen with the messed formatting.
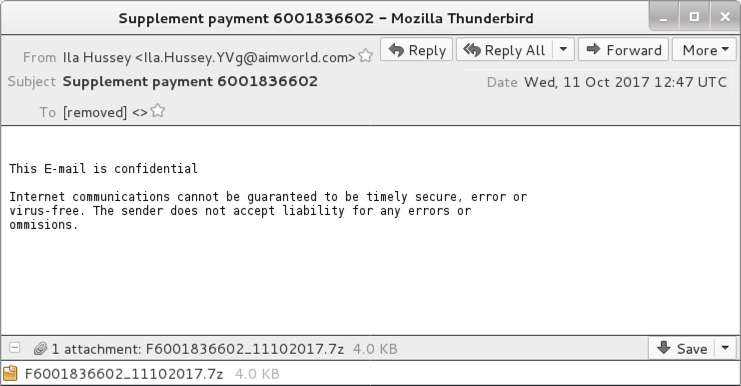
Shown above: One of today's emails after I FTFY.
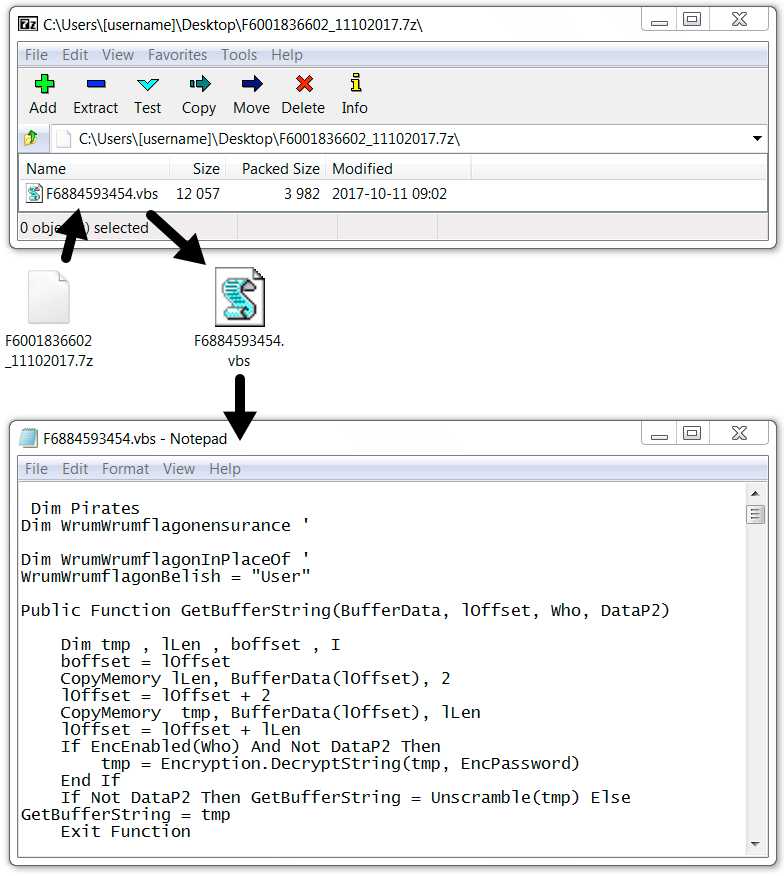
Shown above: An example of today's attachments, extracted from one of the fixed emails.
TRAFFIC
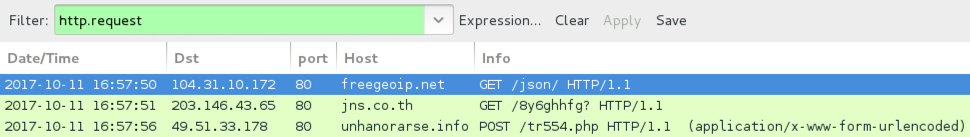
Shown above: Infection traffic filtered in Wireshark.
URLS FROM THE VBS FILES TO DOWNLOAD LOCKY (2017-10-10 & 2017-10-11):
- hxxp[:]//agrourbis[.]com/iugftrs2?
- hxxp[:]//axtes[.]com/iugftrs2?
- hxxp[:]//bdbl[.]com[.]np/jhbfvg7?
- hxxp[:]//deltasec[.]net/iugftrs2?
- hxxp[:]//demopowerindo[.]com/jhbfvg7?
- hxxp[:]//fetchstats[.]net/p66/8y6ghhfg
- hxxp[:]//fetchstats[.]net/p66/jhbfvg7
- hxxp[:]//georginabringas[.]com/8y6ghhfg?
- hxxp[:]//highlandfamily[.]org/jhbfvg7?
- hxxp[:]//highpressurewelding[.]co[.]uk/8y6ghhfg?
- hxxp[:]//jns[.]co[.]th/8y6ghhfg?
- hxxp[:]//louisawong[.]net/jhbfvg7?
- hxxp[:]//old.tuttoggi[.]info/8y6ghhfg?
- hxxp[:]//ostiavolleyclub[.]it/iugftrs2?
- hxxp[:]//pdj[.]co[.]id/8y6ghhfg?
- hxxp[:]//pinkyardflamingos[.]com/8y6ghhfg?
- hxxp[:]//pragmaticinquiry[.]org/8y6ghhfg?
- hxxp[:]//resortphotographics[.]com/8y6ghhfg?
- hxxp[:]//sergiocarfagna[.]it/jhbfvg7?
- hxxp[:]//shahanabiomedicals[.]com/iugftrs2?
- hxxp[:]//supremocartuchos[.]com/jhbfvg7?
- hxxp[:]//t-plesk[.]com/8y6ghhfg?
- hxxp[:]//teracom[.]co[.]id/jhbfvg7?
- hxxp[:]//wiskundebijles[.]nu/8y6ghhfg?
- hxxp[:]//xploramail[.]com/iugftrs2?
OTHER RELATED TRAFFIC GENERATED BY THE 2017-10-11 ATTACHMENTS:
- IP address check at: hxxp[:]//freegeoip[.]net/json/
- or: hxxp[:]//www.geoplugin[.]net/json.gp
- or: hxxps://ipinfo[.]io/json
- 49.51.33.178 port 80 unhanorarse[.]info - POST /tr554.php
- g46mbrrzpfszonuk[.]onion - Tor domain for the decryption instructions (same for a long time now)
ASSOCIATED FILES
SHA256 HASHES FOR ATTACHMENTS:
- 7744255c6d2ec9d1269867bb6804c663e4b0608056e9f5a9cbdfdc70d9b2d40a - invoice_05992_sign_and_return.7z
- 6853fae2acd6ed56c961d69301c907c01d3d2da6a7989b8b4a6eeb900067f748 - invoice_205_sign_and_return.7z
- c4a5bb496388a17c963d856dcf0d194ce3c6f96d68199c6b3144ad3fa13ed5ce - invoice_252_sign_and_return.7z
- 057b9e96272f96685485a720ce962e093fd7d57360b312c114cc44096ec87695 - invoice_4416_sign_and_return.7z
- a51797f0078315e11a23b02c910a2161fc59e2dc85e5ab5c659075a2c9d8bf1d - invoice_975_sign_and_return.7z
- 4df150f7e3f8ca7cbbccf6df90dd47cab0ab89b8a3dda1e91102a36364604ee6 - F4158120230_11102017.7z
- ff0655d51206a6393b9e8d2a6db0c5cd68d5eaf16d21a2e88b7202e99185b405 - F5759185861_11102017.7z
- 4074ff22a842725dd1f5ee40248e3d8acd4e912f8cf82edfe763713e49581d5b - F6001836602_11102017.7z
- ec28311fd20e719ad532bd829bfa65440e012c7db5d0fb0fefb80ea7e06e9a6b - F8366808060_11102017.7z
- 6c4b647c7c408bd78a8454d8a137139fc5f0456d6d606146030fe6f0e61c7942 - F905964727_11102017.7z
SHA256 HASHES FOR EXTRACTED FILES:
- 1cc9aecf2ad534384206c9053313b25cbbc5fdb2e7b6416c8ce787ee0f52b31c - invoice_12397_sign_and_return.vbs
- 17b212795b83ed46a92024e518d56d0a58f2883b92de44b60be075f4bfcaddc3 - invoice_34679_sign_and_return.vbs
- 33429ef1afcc915f1ab56a4529095bee95db57c8652f1e9b3494dea4a9963bd0 - invoice_45399_sign_and_return.vbs
- c93f4c03f19c77ceee865e374b7041f564844e4f84087dc707029fed93c3bb17 - invoice_64789_sign_and_return.vbs
- 93411496f416c73aa4c3b26f8dafe1896f55f1d09d1ca1f1b1efba8240480beb - invoice_86616_sign_and_return.vbs
- 4168de4f25c8da640cc6feac13fc32e1e82d830fed5935656e06019379ab8ddd - F6884593454.vbs
- a89a288bc22e401530fb38e360f1f9bb6b3b56c45a32f23d0fb7e5e96d98d8c1 - F7559397046.vbs
- dc32a9a5231d2fc7f22459771e5e9ffeb5083c682b0ed710176e63f27d0a5690 - F7946586192.vbs
- d2d447e3a6a48bde58a717f7018622b80c1baee2dd8e8a2c041042a162b04250 - F8030796365.vbs
- b077523185d4de51a6dfb3eeb8809b39e558f862a5a96219978559cc6287a75f - F8906797410.vbs
SHA256 HASH FOR THE LOCKY BINARY I RETRIEVED TODAY:
- c35f705df9e475305c0984b05991d444450809c35dd1d96106bb8e7128b9082f - C:\Users\[username]\AppData\Local\Temp\zGqIPBC.exe
IMAGES
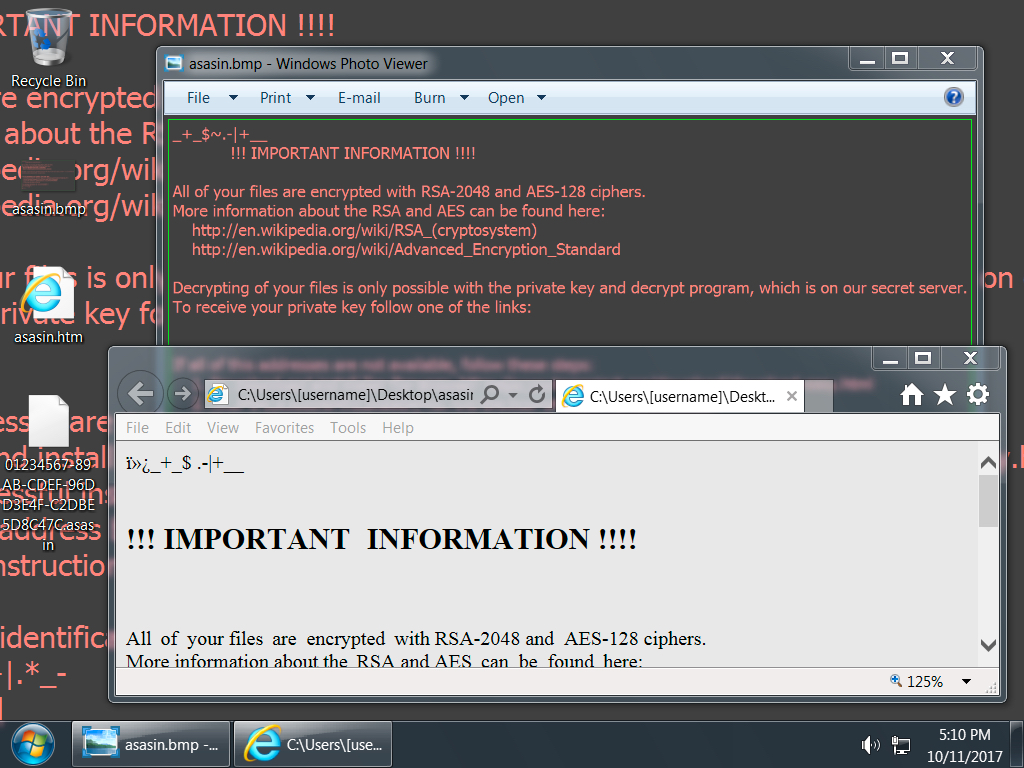
Shown above: Screenshot from an infected Windows desktop--Encrypted files all have a .asasin file extension.
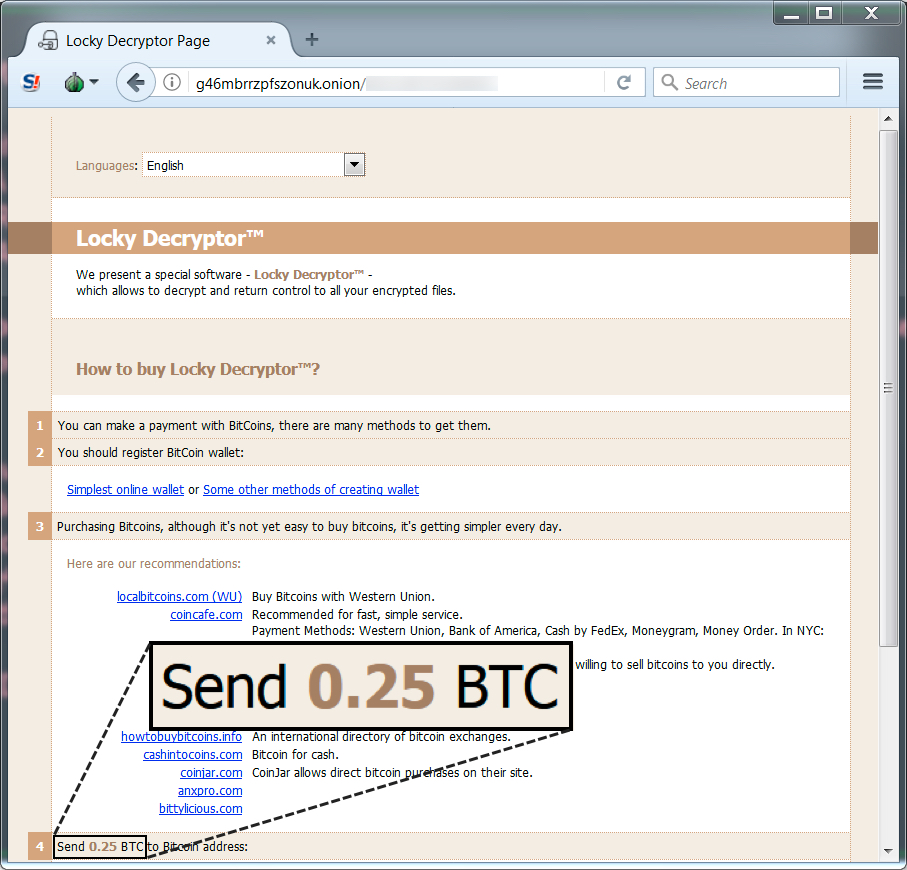
Shown above: Locky Decryptor, where the ransom cost was .25 Bitcoin.
Click here to return to the main page.

