2017-10-17 - TERROR EK SENDS SMOKE LOADER, SMOKE LOADER SENDS MORE MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-17-Terror-EK-pcaps.zip 3.4 MB (3,351,674 bytes)
- 2017-10-17-Terror-EK-example.pcap (354,352 bytes)
- 2017-10-17-post-infection-traffic-from-Terror-EK-payload.pcap (3,870,836 bytes)
- 2017-10-17-Terror-EK-artifacts-and-malware.zip 2.5 MB (2,503,304 bytes)
- 2017-10-17-AppData-Local-Temp-3458.tmp.exe (205,144 bytes)
- 2017-10-17-AppData-Local-Temp-4A97.tmp.exe (471,515 bytes)
- 2017-10-17-AppData-Local-Temp-65A7.tmp.exe (631,472 bytes)
- 2017-10-17-AppData-Local-Temp-8C4A.tmp.dll (517,632 bytes)
- 2017-10-17-AppData-Local-Temp-C14F.tmp.exe (791,280 bytes)
- 2017-10-17-Terror-EK-HTML-for-CVE-2015-5119.txt (4,964 bytes)
- 2017-10-17-Terror-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-10-17-Terror-EK-flash-exploit-1-of-2.swf (44,396 bytes)
- 2017-10-17-Terror-EK-flash-exploit-2-of-2.swf (17,662 bytes)
- 2017-10-17-Terror-EK-landing-page.txt (111,371 bytes)
- 2017-10-17-Terror-EK-payload-Smoke-Loader.exe (117,711 bytes)
NOTES:
- It's been a while since I looked at Terror EK. Last time I looked into it on 2017-08-29, Terror EK had briefly tried HTTPS (link).
- Seems like that was a short-lived phase, and Terror EK has been using regular HTTP for a while now.
- In this case, Terror EK sent Sharik/Smoke Loader, which kicked off additional malware downloads.
- I generated the original infection on a VM, but SmokeLoader didn't work on that, so I had to run it on a physical host.
TRAFFIC
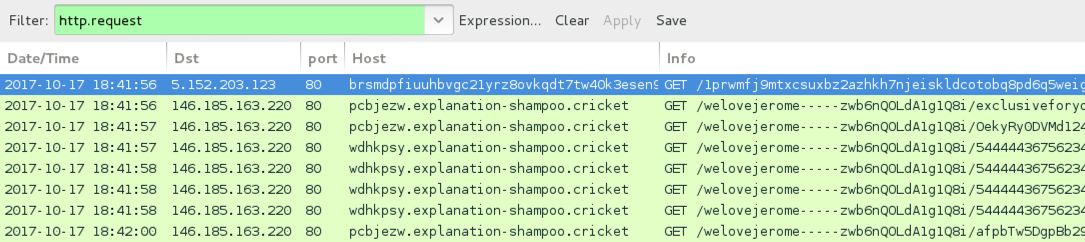
Shown above: Traffic from the original infection filtered in Wireshark.
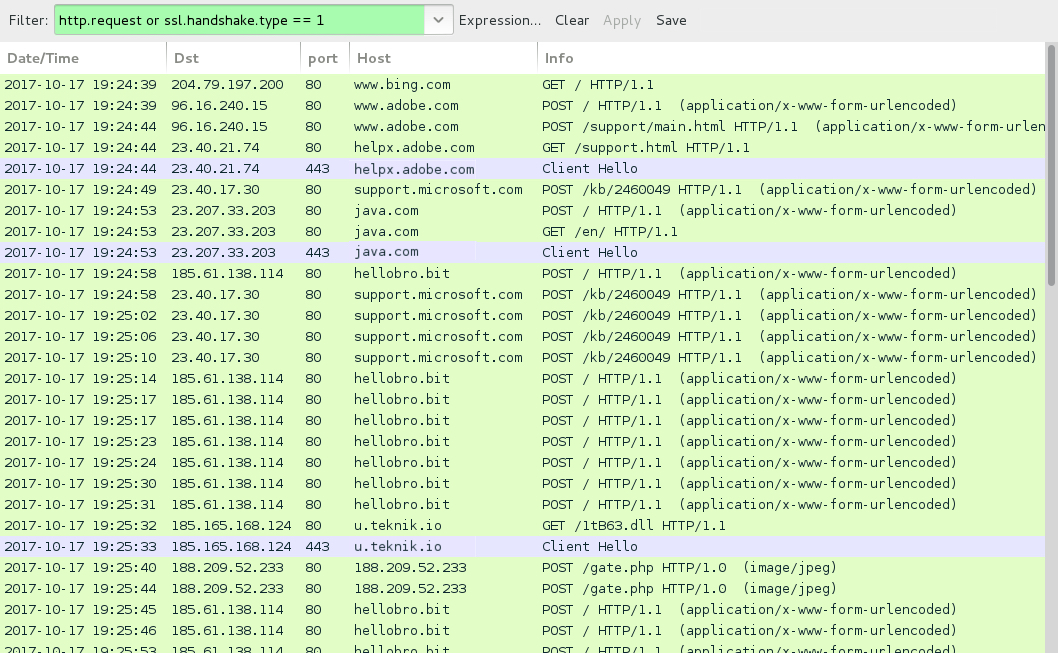
Shown above: Post-infection traffic filtered in Wireshark (1 of 2).
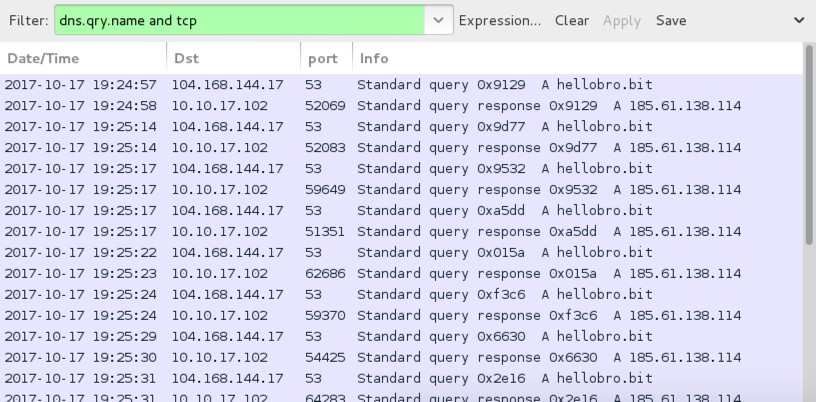
Shown above: Post-infection traffic filtered in Wireshark (2 of 2).
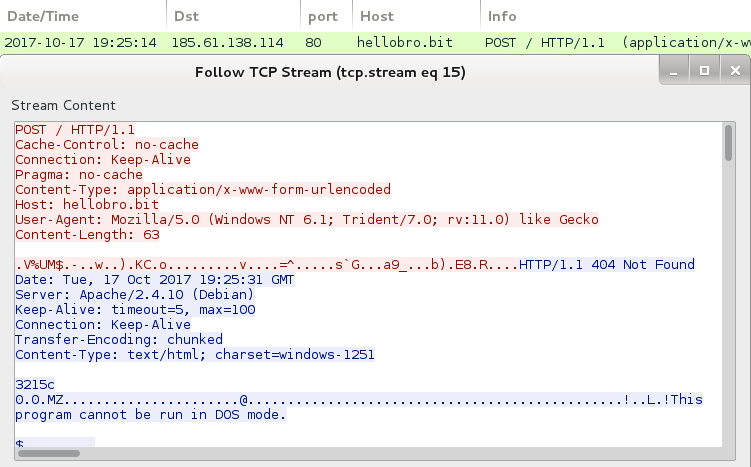
Shown above: Post-infection traffic to hellobro.bit returning more malware.
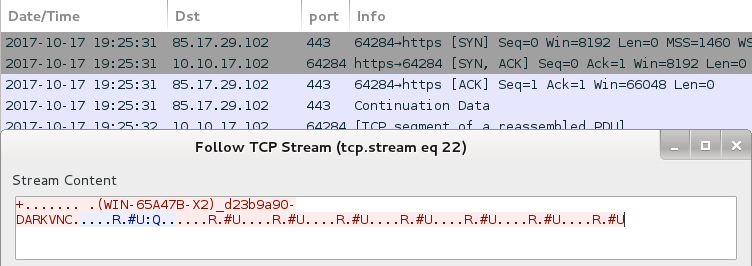
Shown above: Post-infection traffic caused by DarkVNC malware.
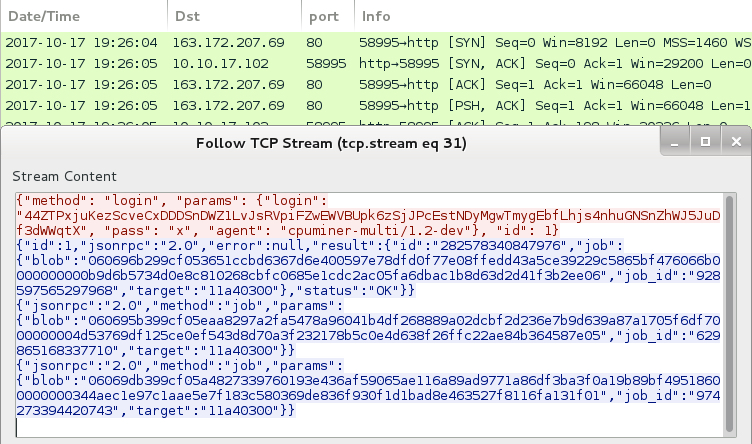
Shown above: Post-infection traffic caused by CoinMiner malware.
TERROR EK-RELATED TRAFFIC:
- 5.152.203[.]123 port 80 - brsmdpfiuuhbvgc21yrz8ovkqdt7tw40k3esen9xagw5laflcyjonxzmpi6hqj.2pih5uvlsgjomgy4zuxx81adce3oj7dkv9qtcbnasnw6rqiryfl
fwtzphmk0eb. zhmhptkstakixgobldls4viyw1jeuno9gj6wb02enury7vra5dcqfpfxc8z3qm.explanation-brother-in-law[.]cricket - redirect from malvertising gate
- 146.185.163[.]220 port 80 - pcbjezw.explanation-shampoo[.]cricket - Terror EK
POST-INFECTION TRAFFIC:
- 104.168.144[.]17 port 53 - TCP-based DNS query for hellobro[.]bit
- 185.61.138[.]114 port 80 - hellobro[.]bit - POST /
- 185.165.168[.]124 port 80 - u.teknik[.]io - GET /1tB63.dll
- 188.209.52[.]233 port 80 - 188.209.52[.]233 - POST /gate.php
- 85.17.29[.]102 port 443 - DarkVNC checkin
- 163.172.207[.]69 port 80 - Coinminer traffic
LEGITIMATE DOMAINS SEEN DURING POST-INFECTION TRAFFIC:
- www.adobe[.]com - GET /support/flashplayer/
- www.adobe[.]com - POST /
- www.adobe[.]com - POST /go/flashplayer_support/
- www.adobe[.]com - POST /support/main.html
- www.bing[.]com - GET /
- helpx.adobe[.]com - GET /flash-player.html
- helpx.adobe[.]com - GET /support.html
- java[.]com - GET /en/
- java[.]com - GET /en/download/help/
- java[.]com - GET /en/download/help/index.xml
- java[.]com - POST /
- java[.]com - POST /help
- go.microsoft[.]com - POST /fwlink/?LinkId=133405
- msdn.microsoft[.]com - GET /vstudio
- support.microsoft[.]com - POST /kb/2460049
FILE HASHES
MALWARE FROM TERROR EK INFECTION:
- SHA2565 hash: c9f3397340e3671a47c6f15f9e6b1697265cecbb37b3c9c29d1eeae3b4312497
- File size: 44,396 bytes
- File description: Terror EK Flash exploit seen on 2017-10-17 (1 of 2)
- SHA2565 hash: 2090456737a6b44f2c16943662c9cb42acf05b1db6d63f89253a39f33e0ec02c
- File size: 17,662 bytes
- File description: Terror EK Flash exploit seen on 2017-10-17 (2 of 2)
- SHA2565 hash: e6516d2911fc3378903b396b1b3ec97ddd497a1e8b974b531b1f140a485d39ca
- File size: 117,711 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\[random characters].exe
- File location: C:\Users\[username]\AppData\Roaming\Microsoft\vfuggwhu\rvfwteia.exe
- File description: Terror EK payload (Sharik/Smoke Loader)
POST-INFECTION MALWARE:
- SHA2565 hash: 07e96eb325ef315ede680eca649426d6a4516e03a859926d651fda669a98873a
- File size: 205,144 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\3458.tmp.exe
- File location: C:\Users\[username]\AppData\Roaming\reserved\reserv.exe
- SHA256 hash: dda0f5b8759220bdbd8e5dba8bff49868b12e1d5e3bd273b366050dab0c8dd4f
- File size: 471,515 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\4A97.tmp.exe
- SHA256 hash: a5bb96d731ef58cf17cc579578ab89c7c46f275982be8eb137ff64268dff1efc
- File size: 631,472 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\65A7.tmp.exe
- SHA256 hash: bdf3c4e804ebffad9f7ba9a3e3e467d0251c16f57e41095b593d226d2e7f399d
- File size: 517,632 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\8C4A.tmp.dll
- SHA256 hash: e70e429aa051017432921f4cdf2b8492c5cff9465ffdc3aabad2a865ecd2b326
- File size: 791,280 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\C14F.tmp.exe
- File location: C:\Users\[username]\AppData\LocalkHYLfEPyyR\svchost.exe
- File description: CoinMiner
IMAGES
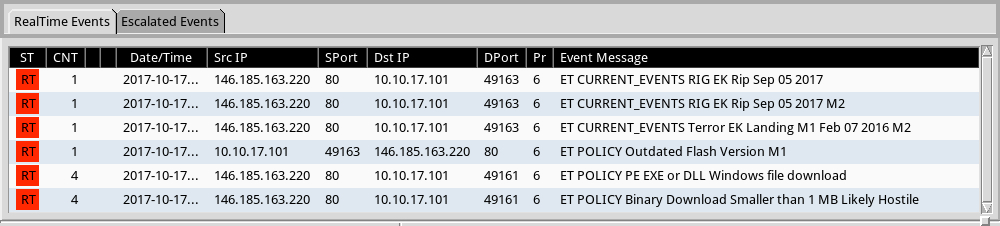
Shown above: Alerts on Terror EK activity from the Emerging Threats (ET) ruleset using Sguil on Security Onion.
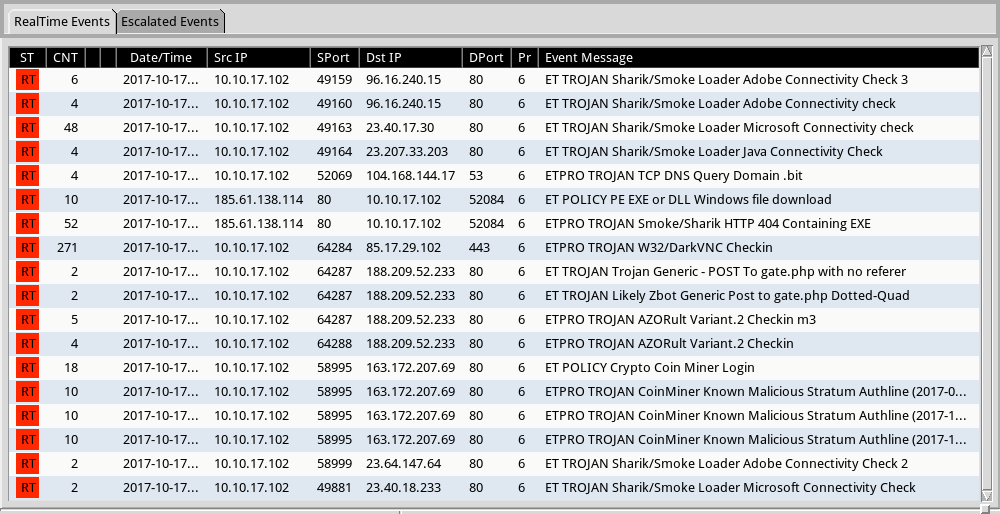
Shown above: Alerts on post-infection activity from the Emerging Threats Pro (ET Pro) ruleset using Sguil on Security Onion.
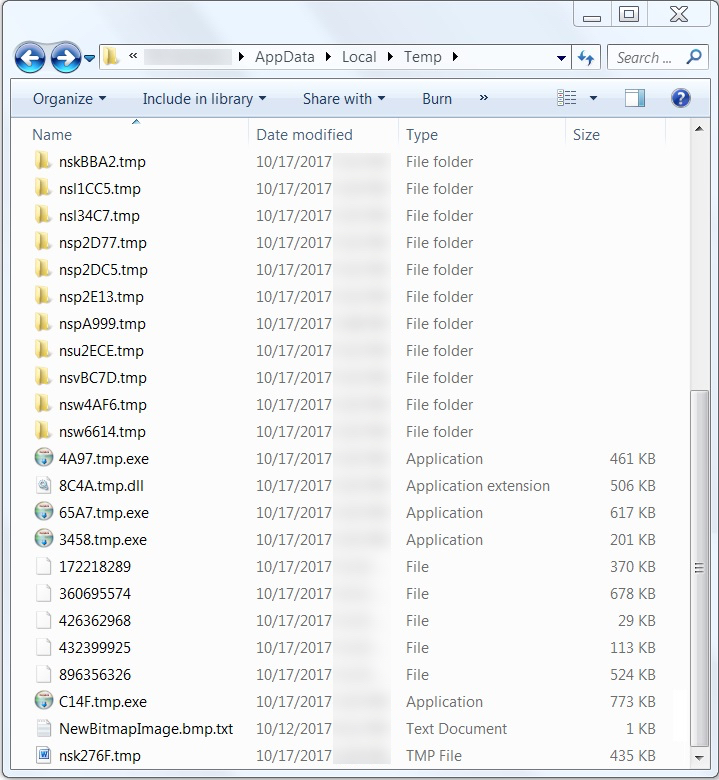
Shown above: Some artifacts seen in the infected user's AppData\Local\Temp folder.
Click here to return to the main page.
