2017-10-23 - A RAT'S NEST OF ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-23-RAT-activity.pcap.zip 4.9 MB (4,930,548 bytes)
- 2017-10-23-RAT-activity.pcap (8,719,986 bytes)
- 2017-10-23-RAT-activity-email-and-malware.zip 5.8 MB (5,753,294 bytes)
- 1.exe (850,432 bytes)
- 2.exe (1,149,440 bytes)
- 2017-10-23-RAT-malspam-0716-UTC.eml (454,594 bytes)
- 3.exe (1,149,440 bytes)
- 4.exe (1,477,120 bytes)
- 5.exe (1,509,888 bytes)
- 6.exe (1,362,432 bytes)
- FRTRK.jar (484,834 bytes)
- New Order.exe (879,104 bytes)
- New Order.zip (328,818 bytes)
- rundll.exe (7,680 bytes)
NOTES:
- This malicious spam (malspam) is low-hanging fruit that should easily be caught by most spam filters.
- ETPRO and Snort Subscriber rules had different RAT names for post-infection traffic to 213.183.58[.]34, such as Netwire RAT, NanoCore RAT, DarkKomet RAT, and Babylon RAT.
- With 6 additional executables downloaded during the post-infection activity, this was a real "RAT's nest" of an infection.
Shown above: All you have to do is double-click that innocent-looking executable.
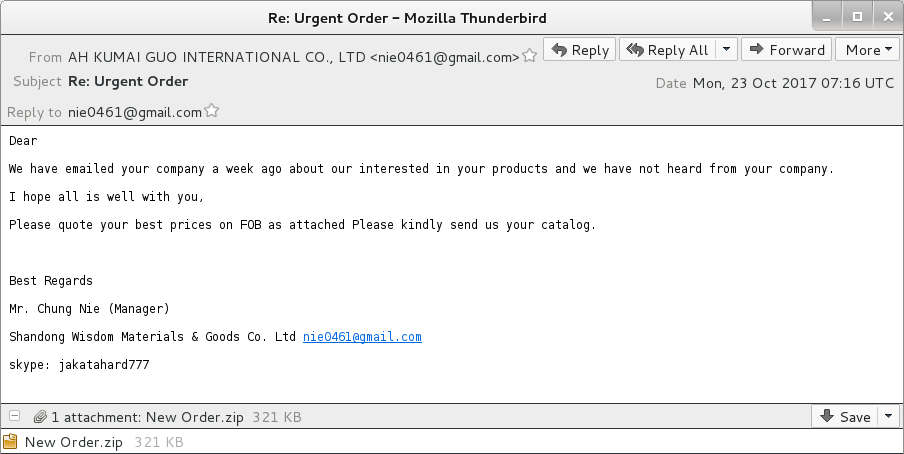
Shown above: Screenshot from the email.
EMAIL INFO:
- Date: Monday, 2017-10-23 07:16 UTC
- From: <nie0461@gmail[.]com> (spoofed)
- Subject: Re: Urgent Order
- Attachment name: New Order.zip
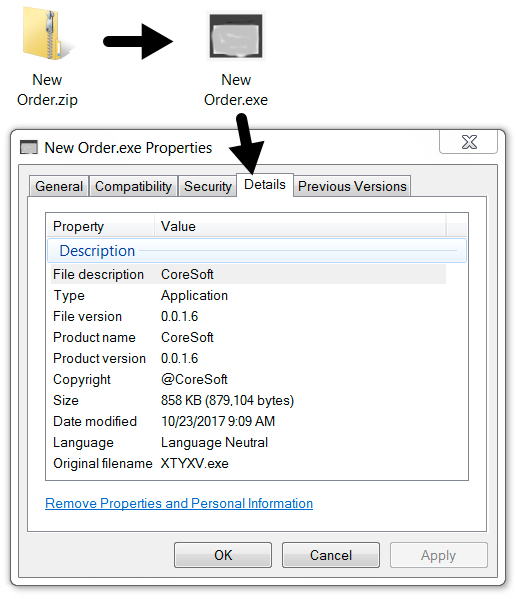
Shown above: Zip attachment and extracted malware.
TRAFFIC
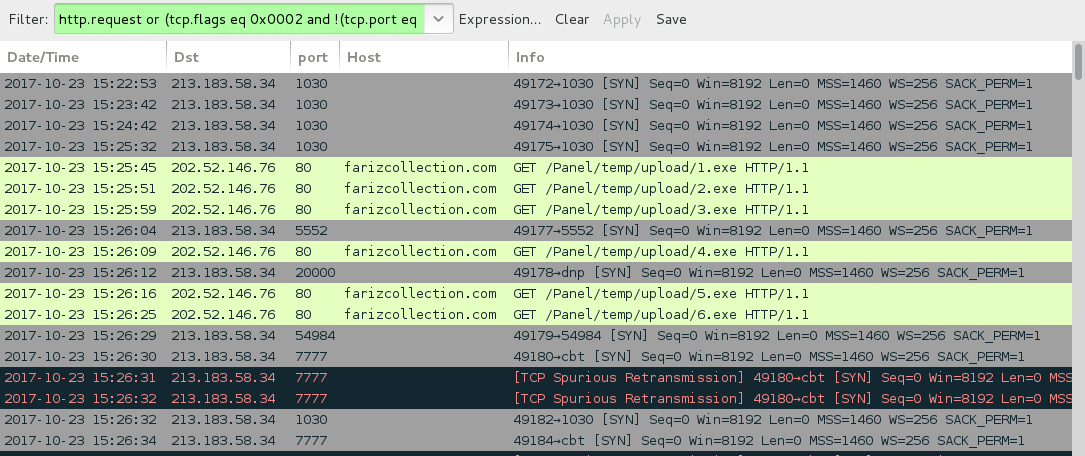
Shown above: Infection traffic filtered in Wireshark.
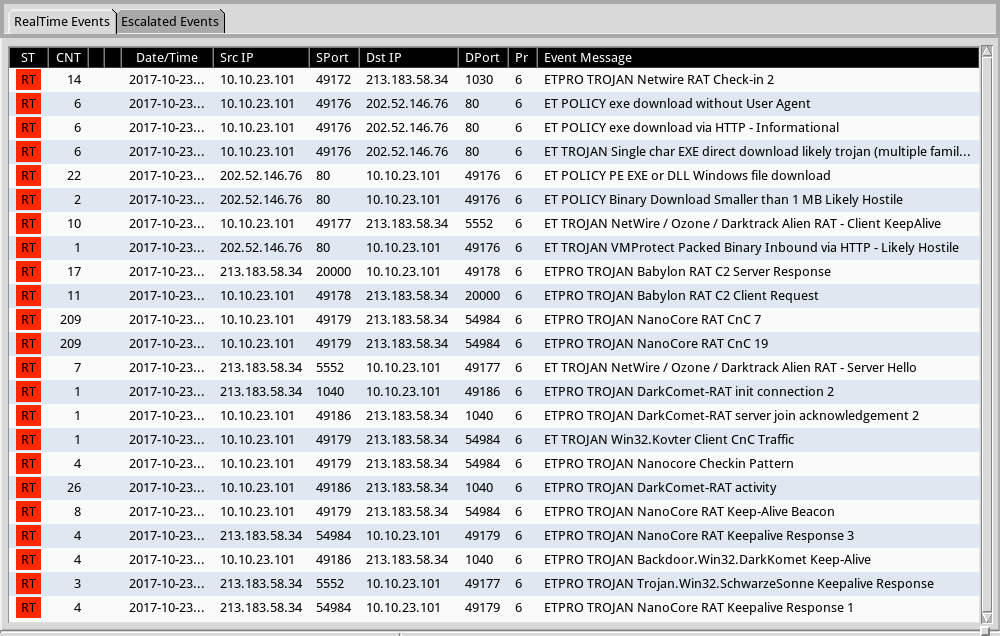
Shown above: Alerts on the infection traffic from the Emerging Threats Pro (ET Pro) ruleset using Sguil on Security Onion.
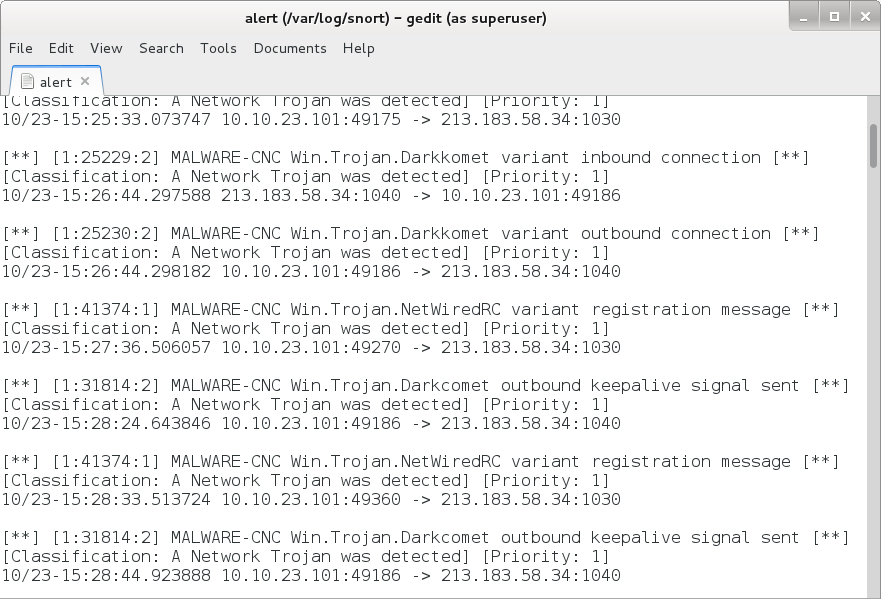
Shown above: Some RAT-based alerts on the infection traffic from the Snort subscriber ruleset on Snort 2.9.11.
INFECTION TRAFFIC:
- 213.183.58[.]34 port 1030 - RAT-based post-infection callback traffic
- 213.183.58[.]34 port 5552 - RAT-based post-infection callback traffic
- 213.183.58[.]34 port 20000 - RAT-based post-infection callback traffic
- 213.183.58[.]34 port 54984 - RAT-based post-infection callback traffic
- 213.183.58[.]34 port 7777 - attempted TCP connections (no response from the server)
- 202.52.146[.]76 port 80 - farizcollection[.]com - GET /Panel/temp/upload/1.exe
- 202.52.146[.]76 port 80 - farizcollection[.]com - GET /Panel/temp/upload/2.exe
- 202.52.146[.]76 port 80 - farizcollection[.]com - GET /Panel/temp/upload/3.exe
- 202.52.146[.]76 port 80 - farizcollection[.]com - GET /Panel/temp/upload/4.exe
- 202.52.146[.]76 port 80 - farizcollection[.]com - GET /Panel/temp/upload/5.exe
- 202.52.146[.]76 port 80 - farizcollection[.]com - GET /Panel/temp/upload/6.exe
MALWARE
ZIP ATTACHMENT FROM THE EMAIL:
- SHA256 hash: 7d14025275fbcd277f74aaaa0533bfe02f22c070a954c813d75140a8c352b36d
File name: New Order.zip
File size: 328,818 bytes
EXTRACTED MALWARE:
- SHA256 hash: f5118f6534b0bb265f563421697bdcb29fed31267f75a71d7dd0da7a31be662a
File name: New Order.exe
File name: C:\Users\[username]\AppData\Local\Temp\svchost.exe
File size: 879,104 bytes
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- 7a141eba6dc8b7e6a27bdcf067e1c45fc9e35aa2f699b3b526f44be6b47a54d5 - 1.exe
- 1520fb831f4c77f57f663e393b0ba0f2edc8bc0455b86e0641485432acd1bfe8 - 2.exe
- c15d6ce3051ecb4a4aa1e128ea85c0b4159de3d36430578b5bacdb074cca0d2d - 3.exe
- a68083aaddbba3d8e23f607aee07cc1b4ace727c9f0539ad9edda594b0ae0b1d - 4.exe
- 93f1b692dc95fc9d1fe0fbb68b82841bc5ad02561a90d5e081ae00e08e02c350 - 5.exe
- 25437f103f7ccbc444d8703bbf7a08d7691c5d00066bdeb80bd60883bfb16327 - 6.exe
- fea9e7094bc95dc152f595f7b45c78ec15a76fc6ceec9812d38de6c601c4170e - FRTRK.jar
- d142c0342a9540a8b78fe649c92a0e960da4cda5f45d3d54d0502abc41e29fef - rundll.exe
IMAGES
Most of the malware I found in the infected user's AppData\Local\Temp directory also copied itself to other locations. Too many to list here, so I just kept copies from that initial location.
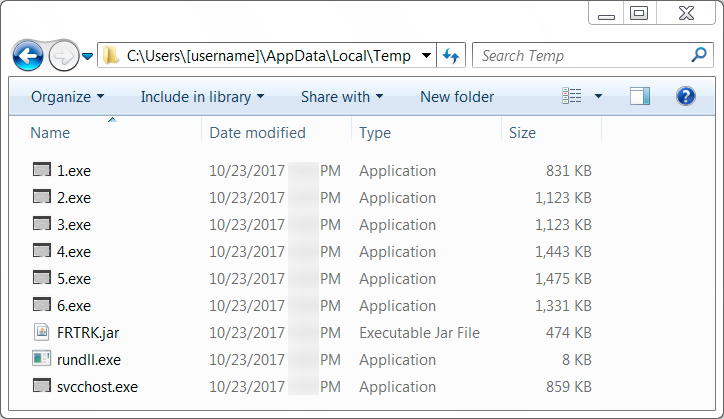
Shown above: Malware retrieved from the infected user's AppData\Local\Temp directory.
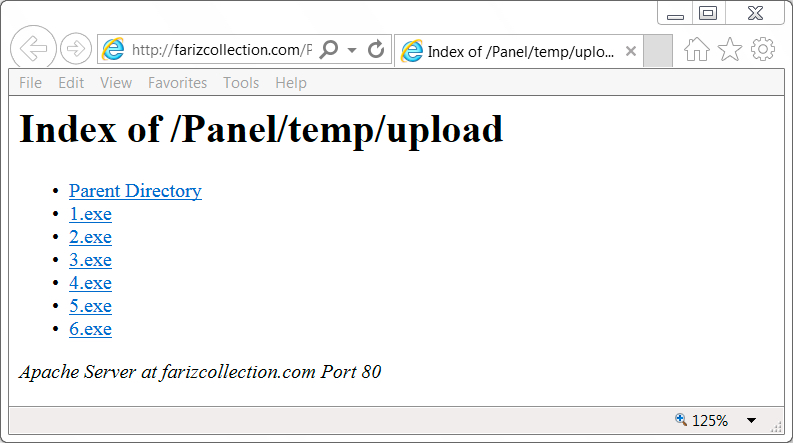
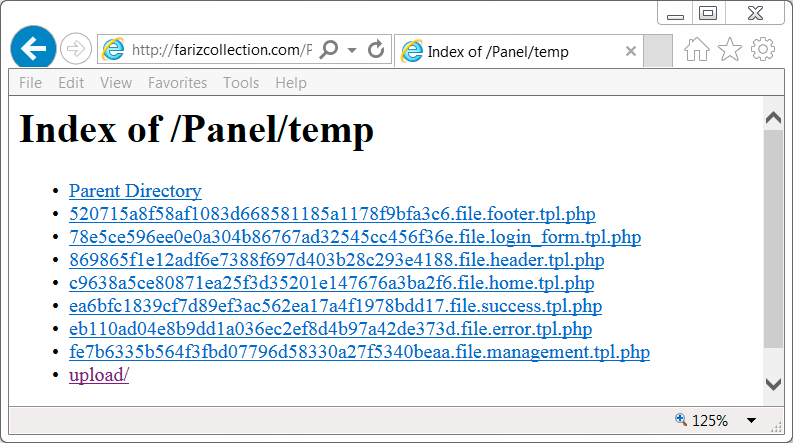
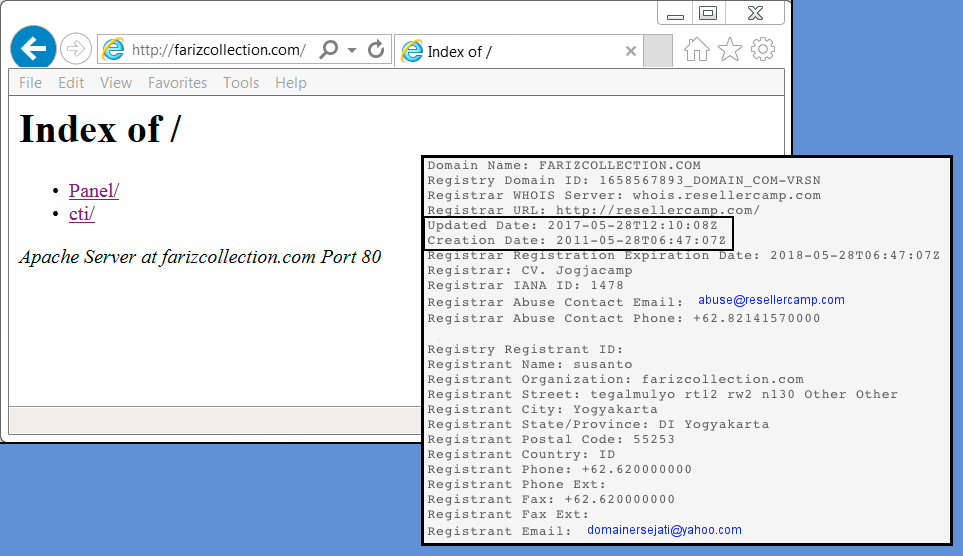
Hey, look! Directories are all open on the server hosting the post-infection malware.
Click here to return to the main page.

