2017-10-23 - BANLOAD INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-23-Banload-infection-traffic.saz.zip 12.7 MB (12,690,972 bytes)
- 2017-10-23-Banload-infection-traffic.saz (12,690,084 bytes)
- 2017-10-23-Banload-infection-traffic.pcap.zip 11.9 MB (11,925,742 bytes)
- 2017-10-23-Banload-infection-traffic.pcap (12,729,380 bytes)
- 2017-10-23-Banload-malware-and-artifacts.zip 14.0 MB (13,952,124 bytes)
- 2017-10-23-Brazil-malspam-1513-UTC.txt (2,194 bytes)
- ORCAMEN00017ODB23102017414478005410000048705-1st-run.zip (1,263,870 bytes)
- ORCAMEN00017ODB23102017414478005410000048705-2nd-run.zip (1,189,284 bytes)
- log.txt (96 bytes)
- ta21352362.668 (11,494,246 bytes)
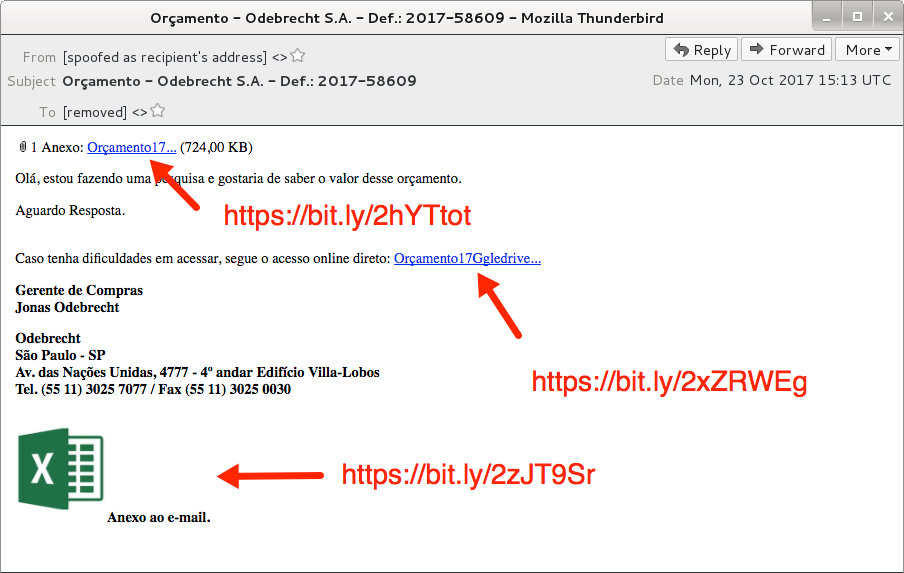
Shown above: Screenshot from the email.
EMAIL INFO:
- Date: Monday, 2017-10-23 15:13 UTC
- From: [spoofed as recipient's address]
- Subject: Orçamento - Odebrecht S.A. - Def.: 2017-58609
- Malicious link for malware (1 of 3): hxxps[:]//bit[.]ly/2hYTtot
- Malicious link for malware (2 of 3): hxxps[:]//bit[.]ly/2xZRWEg
- Malicious link for malware (3 of 3): hxxps[:]//bit[.]ly/2zJT9Sr
TRAFFIC
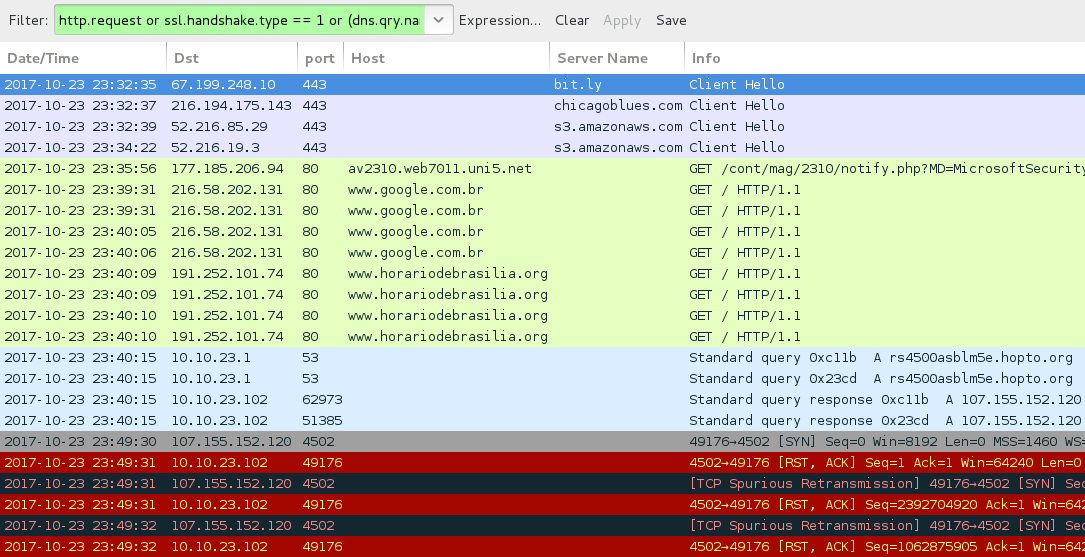
Shown above: Infection traffic filtered in Wireshark.
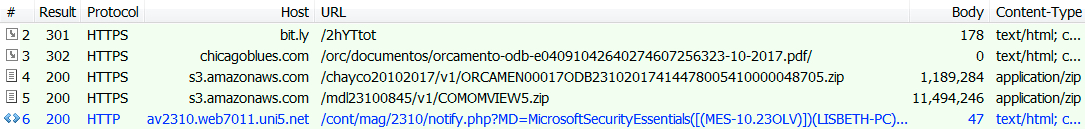
Shown above: Infection traffic filtered in Fiddler.
URLS FROM THE INFECTION TRAFFIC - 1ST DOWNLOADED FILE:
- hxxps[:]//bit[.]ly/2zJT9Sr
- hxxp[:]//thirdculture[.]tv/orc/documentos/orcamento-odb-e04091042640274607256323-10-2017.pdf/
- [see below for a full infection chain]
- hxxps[:]//bit.ly/2xZRWEg
- hxxp[:]//comunicamob[.]com[.]br/orc/documentos/orcamento-odb-e04091042640274607256323-10-2017.pdf/
- [see below for a full infection chain]
- hxxps[:]//bit[.]ly/2hYTtot
- hxxps[:]//chicagoblues[.]com/orc/documentos/orcamento-odb-e04091042640274607256323-10-2017.pdf/
- hxxps[:]//s3.amazonaws[.]com/chayco20102017/v1/ORCAMEN00017ODB23102017414478005410000048705.zip
- hxxps[:]//s3.amazonaws[.]com/mdl23100845/v1/COMOMVIEW5.zip
- hxxp[:]//av2310.web7011.uni5[.]net/cont/mag/2310/notify.php?MD=[Computer & Anti-Virus info]
POST-INFECTION TRAFFIC FROM THE 2ND DOWNLOADED FILE:
- https[:]//s3.amazonaws[.]com/clrnsmoths2310/COMOMVIEW5.zip
- hxxp[:]//av2310.web7011.uni5[.]net/cont/mag/2310/notify.php?MD=[Computer & Anti-Virus info]
MALWARE
DOWNLOADED MALWARE:
- SHA256 hash: 5e56b7ba440d2d995f0225e2599e4bd5fbb5cb71b5c12c3d9d2b4482208496b5
File size: 1,263,870 bytes
File name: ORCAMEN00017ODB23102017414478005410000048705.zip
File description: Zip archive downloaded after clicking any of the bit.ly links from the malspam (1st downloaded file)
- SHA256 hash: 696e35704ed94b799d774782669461deadf92226d97c1a28881576dc754454c8
File size: 2,693,632 bytes
File name: ORCAMEN00017ODB23102017414478005410000048705.exe
File description: Extracted exectuable from downloaded zip archive (1st downloaded file)
- SHA256 hash: 9be6ceb049996d2c231d2687b341f5eb8fe16a4b7732a3e7269db50fd73c5966
File size: 1,189,284 bytes
File name: ORCAMEN00017ODB23102017414478005410000048705.zip
File description: File downloaded after clicking any of the bit.ly links from the malspam (2nd downloaded file)
- SHA256 hash: 772f5a0a275971e51bd390ec928408a6d10d59b43b00388be7401ae0a3e4d609
File size: 2,567,168 bytes
File name: ORCAMEN00017ODB23102017414478005410000048705.exe
File description: Extracted exectuable from downloaded zip archive (2nd downloaded file)
POST-INFECTION MALWARE:
- SHA256 hash: d29b3d1c1528c4cfe5fdeb5569ff0389d56555b2e67dc5caf5935d9f90376d37
File size: 11,494,246 bytes
File location: C:\Users\[username]\AppData\Roaming\LALDREANSZ\ta21352362.668
File location: hxxps[:]//s3.amazonaws[.]com/clrnsmoths2310/COMOMVIEW5.zip (called by EXE from 1st downloaded file)
File location: hxxps[:]//s3.amazonaws[.]com/mdl23100845/v1/COMOMVIEW5.zip (called by EXE from 2nd downloaded file)
File description: Follow-up zip archive after running the extracted executable from either of the downloaded files
- SHA256 hash: 0a229c7728b9bfd77b706b8316a1843e3e32633ad0a096d8e0761a3f8966a161
File size: 15 bytes
File location: C:\Users\[username]\AppData\Roaming\LALDREANSZ\COMOMVIEW0.dat
File description: Text file from the follow-up zip archive
- SHA256 hash: a05fcf02f92d5b9887e547e87e4f98c18b62d5c414263eceb1ca6fce8c730314
File size: 348,273,152 bytes
File location: C:\Users\[username]\AppData\Roaming\LALDREANSZ\COMOMVIEW0.exe
File description: Exectuable from the follow-up zip archive
IMAGES

Shown above: Clicking on one of the email links.
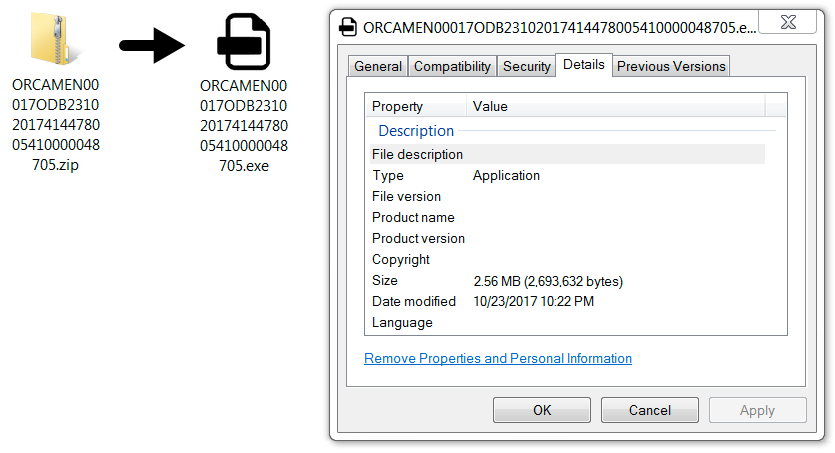
Shown above: 1st downloaded file.
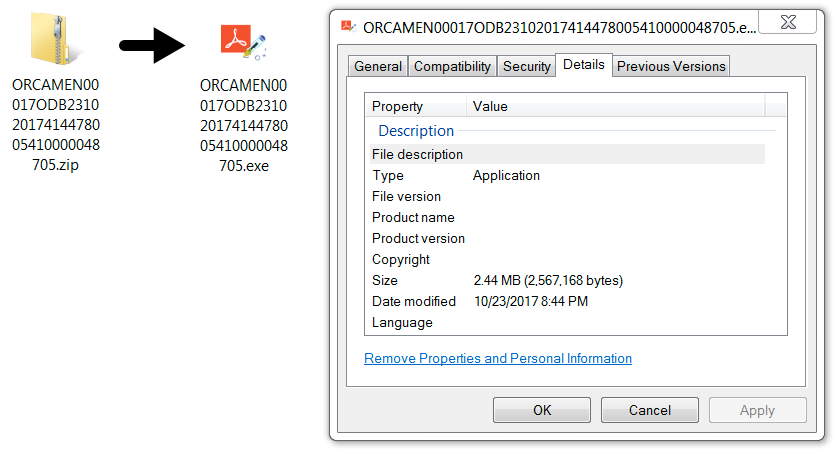
Shown above: 2nd downloaded file an hour or so later from the same email links.
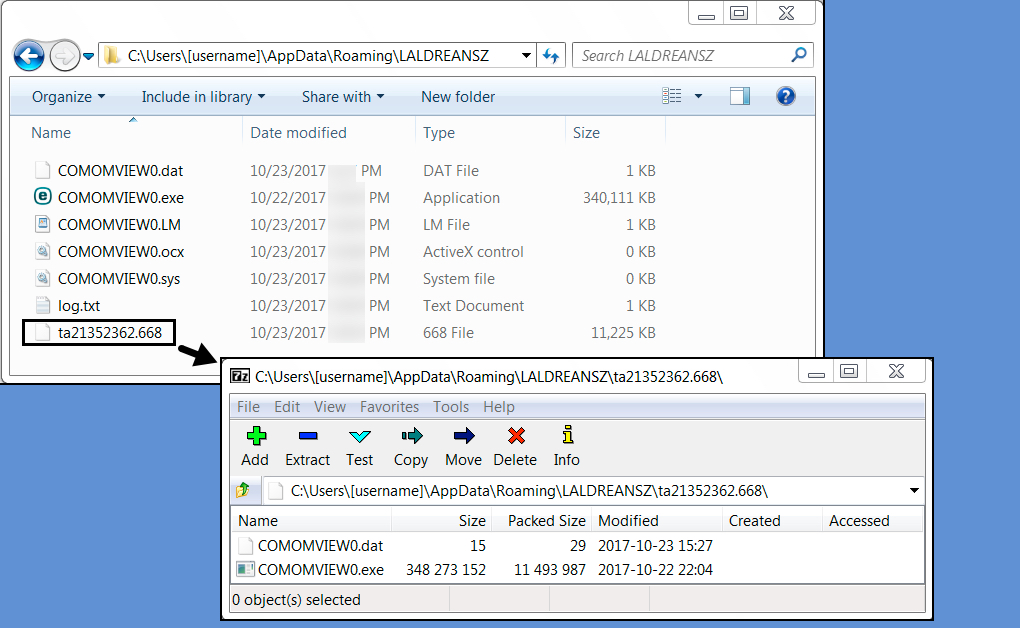
Shown above: Post-infection artifacts (some items deleted after the initial infection).
Click here to return to the main page.
