2017-10-24 - NECURS BOTNET MALSPAM USES DDE ATTACK TO PUSH LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-24-Necurs-botnet-DDE-doc-sends-Locky-ransomware.pcap.zip 854.0 kB (853,993 bytes)
- 2017-10-24-Necurs-botnet-DDE-doc-sends-Locky-ransomware.pcap (967,844 bytes)
- 2017-10-24-files-from-Locky-ransomware-infection.zip 663.1 kB (663,143 bytes)
- 2017-10-24-Locky-Decryptor-style.css (7,206 bytes)
- 2017-10-24-Locky-Decryptor.html (12,790 bytes)
- 2017-10-24-asasin.bmp (5,228,854 bytes)
- 2017-10-24-asasin.htm (9,442 bytes)
- Invoice_file_426550.doc (18,759 bytes)
- K23400jw.exe (713,216 bytes)
- heropad64.exe (183,555 bytes)
BACKGROUND:
- 2017-10-19 - SANS Internet Storm Center (ISC) - Necurs Botnet malspam pushes Locky using DDE attack
- 2017-10-24 - My Online Security - Locky ransomware delivered via DDE exploit Scan Data malspam no-reply@victim domain
NOTES:
- Never got any copies of the emails, but I grabbed one of the Word documents first reported today by MyOnlineSecurity.
- Still seeing the same type of traffic that I reported in the SANS ISC diary last week.
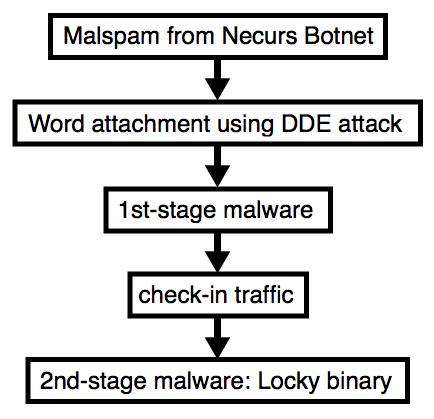
Shown above: First of the messages seen when opening a Word document with a DDE attack.
Shown above: Same chain of events seen last week.
TRAFFIC

Shown above: Infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS:
- 75.98.175[.]70 port 80 - transmercasa[.]com - GET /JHGGsdsw6
- 151.236.60[.]40 port 80 - tatianadecastelbajac[.]fr - GET /kjhgFG
- 178.151.116[.]49 port 80 - gdiscoun[.]org - POST /
- 62.50.190[.]101 port 80 - webhotell.enivest[.]no - POST /cuYT39.enc
OTHER URLS TO RETRIEVE THE 1ST-STAGE DOWNLOADER:
- 85.214.28[.]187 port 80 - video.rb-webdev[.]de - GET /kjhgFG
- 92.48.90[.]34 port 80 - themclarenfamily[.]com - GET /kjhgFG
FILE HASHES
WORD DOCUMENT USING DDE ATTACK:
- SHA256 hash: 46bb448bd849212c1df99cae15984b669dc19cf16fb6ccb28b211a3d21b50f1d
File size: 18,759 bytes
File description: Attachment from one of the Necurs botnet emails on 2017-10-24
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 6106d1b5963feb632eee28aaee5b68e85aef1d090c5e5ef2899b3a0f1a3f7c5b
File size: 183,555 bytes
File location: C:\Users\[username]\AppData\Local\Temp\heropad64.exe
File location: C:\Users\[username]\AppData\Local\Temp\{1730a00d-6230-8a91-c08c-c740a103185a}\mJRrVn2X.exe
File description: Initial malware (generates callback traffic & downloads Locky)
Registry update: KHCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- SHA256 hash: 0f5be64bc9be27c4a9cab972f5a5879337cb8cfd155a84e62399ed34e8d5a1dc
File size: 713,216 bytes
File location: C:\Users\[username]\AppData\Local\Temp\K23400jw.exe
File description: Locky ransomware (.asasin variant)
IMAGES
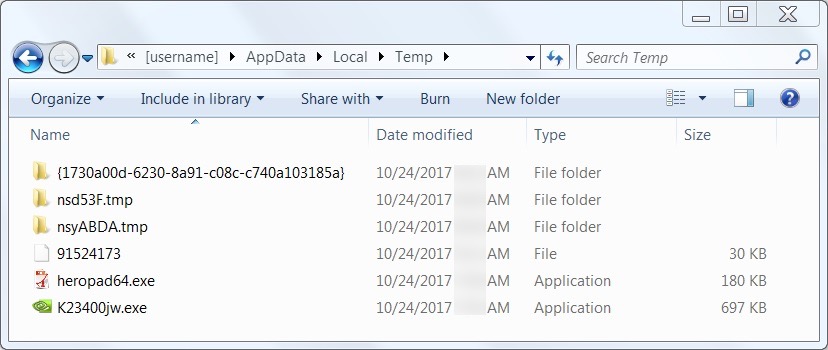
Shown above: Artifacts noted in the user's AppData\Local\Temp directory.
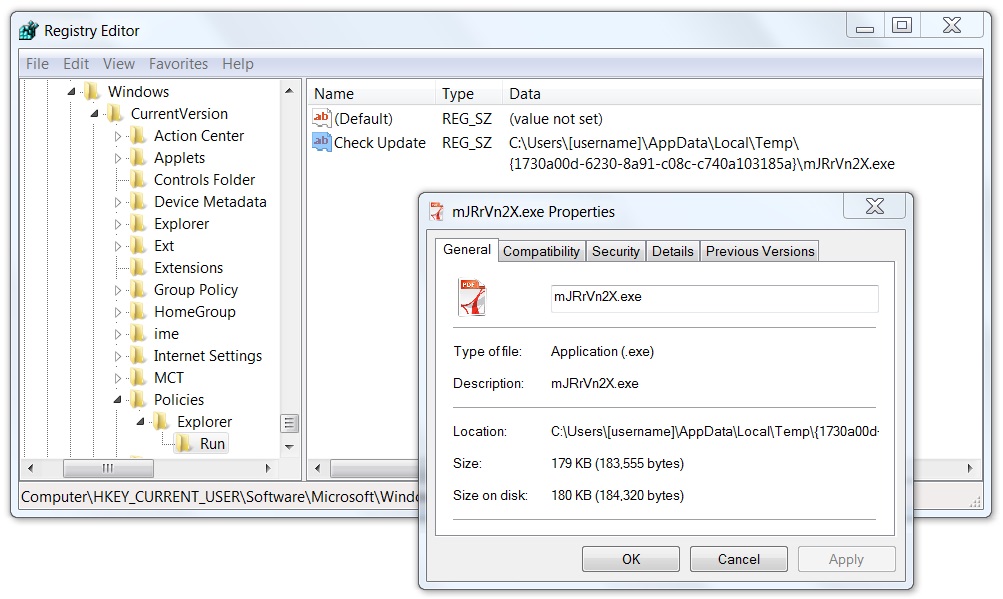
Shown above: Windows registry update found on the infected host.
Click here to return to the main page.