2017-10-27 - REMCOS RAT INFECTION
ASSOCIATED FILES:
- 2017-10-27-Remcos-RAT-infection-traffic.pcap.zip 2.5 kB (2,471 bytes)
- 2017-10-27-Remcos-RAT-infection-traffic.pcap (6,248 bytes)
- 2017-10-27-Remcos-RAT-malspam-and-malware-files.zip 621 kB (620,621 bytes)
- 2017-10-26-malspam-pushing-Remcos-RAT-1743-UTC.eml (264,118 bytes)
- July_QUYEN0726.xls (107,520 bytes)
- Quotation_VANPHUONGNAM_2432_102617_xls.arj (191,738 bytes)
- Quotation_VANPHUONGNAM_2432_102617_xls.exe (847,872 bytes)
- filename.vbe.txt (382 bytes)
NOTES:
- Remcos is a supposedly a legitimate Remote Access Tool (RAT).
- I've seen recent reports of Remcos RAT in malware campaigns (example).
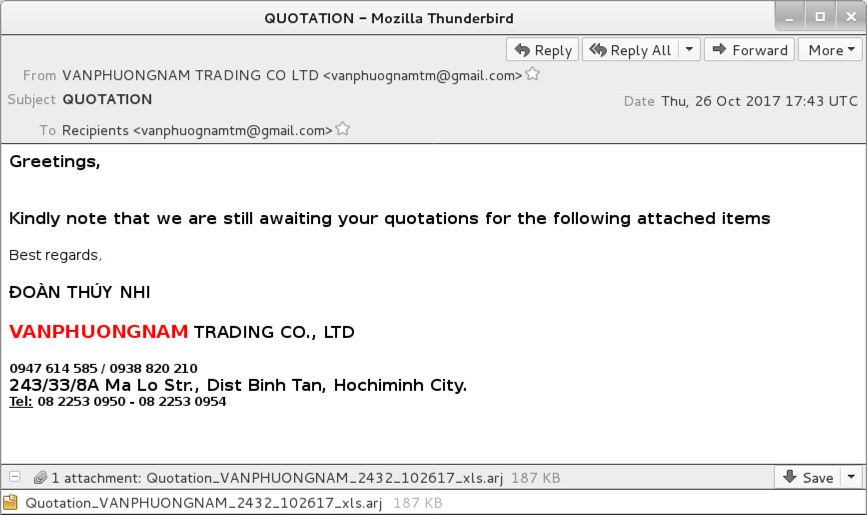
Shown above: Screenshot from the email.
EMAIL HEADERS:
- Date: Thursday, 2017-10-26 17:43 UTC
- Subject: QUOTATION
- From: VANPHUONGNAM TRADING CO LTD <vanphuognamtm@gmail[.]com>
- Attachment name: Quotation_VANPHUONGNAM_2432_102617_xls.arj
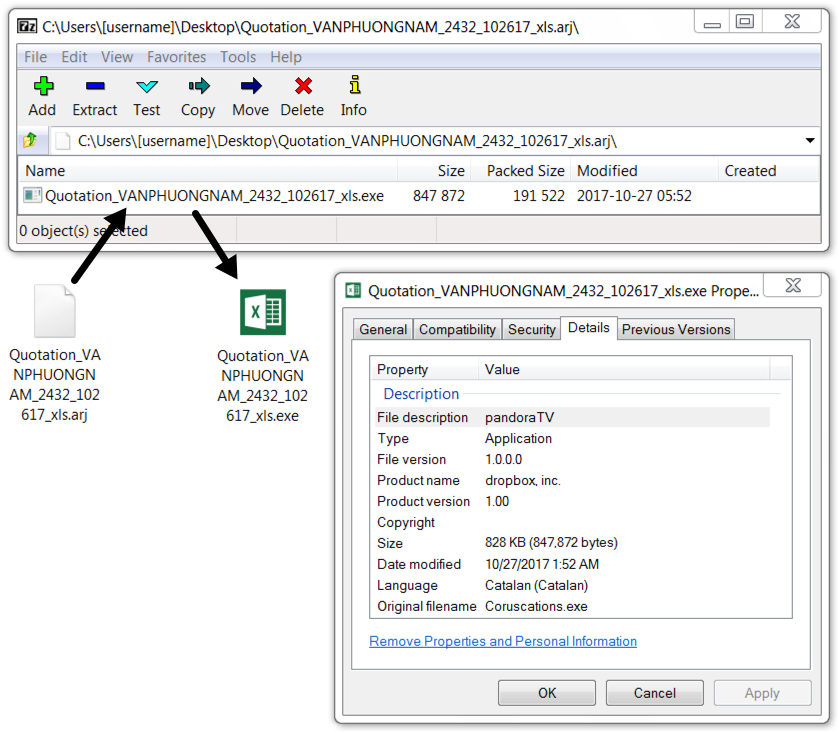
Shown above: Malicious attachment from the malspam.
TRAFFIC
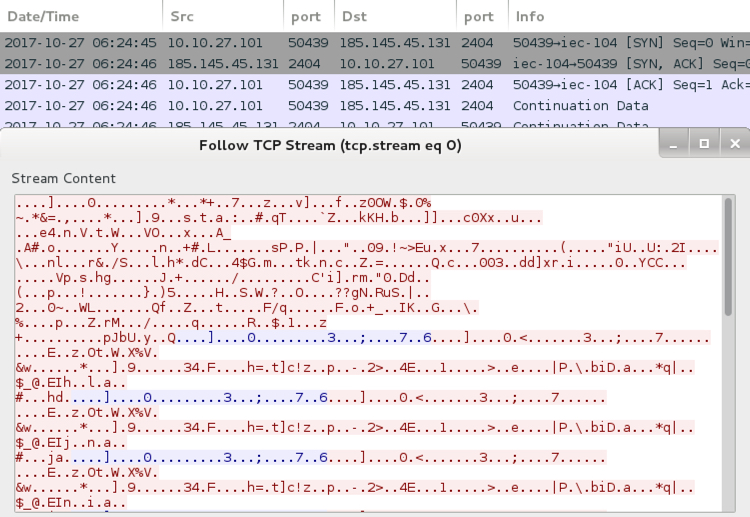
Shown above: Remcos RAT post-infection traffic from the infection filtered in Wireshark.
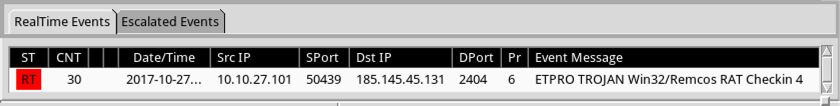
Shown above: Alerts on the post-infection traffic from the Emerging Threats Pro (ET Pro) ruleset using Sguil on Security Onion.
POST-INFECTION TRAFFIC:
- 185.145.45[.]131 port 2404 - Encoded traffic caused by Remcos RAT
FILE HASHES
EMAIL ATTACHMENT:
- SHA256 hash: 944a7309daca89a0f56312a2a5a25560acea724c12971253028587f1cddc9034
File name: Quotation_VANPHUONGNAM_2432_102617_xls.arj
File size: 191,738 bytes
EXECUABLE EXTRACTED FROM THE ARJ ARCHIVE:
- SHA256 hash: 730e50316d32204bc0d5e28ddf26c8e34b6767e2cf2d678c76071af44c8d20c7
File name: Quotation_VANPHUONGNAM_2432_102617_xls.exe
Post-infection location: C:\Users\[username]\AppData\Roaming\subfoler\filename.exe
File size: 847,872 bytes
File description: Remcos RAT
DECOY SPREADSHEET OPENED ON THE VICTIM'S DESKTOP (NOT MALICIOUS):
- SHA256 hash: 95c6e5c0f05395fb4ebc5d0152a87ede35a1a256f2343870c902285239228c39
File location: C:\Users\[username]\AppData\Local\Temp\July QUYEN0726.xls
File size: 847,872 bytes
File description: Decoy spreadsheet
VBE FILE IN STARTUP FOLDER FOR MALWARE PERSISTENCE:
- SHA256 hash: [different hashes, depending on the user account name]
File location: C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\filename.vbe
File size: Approximately 370 to 400 bytes
File description: Start menu item in startup folder
IMAGES
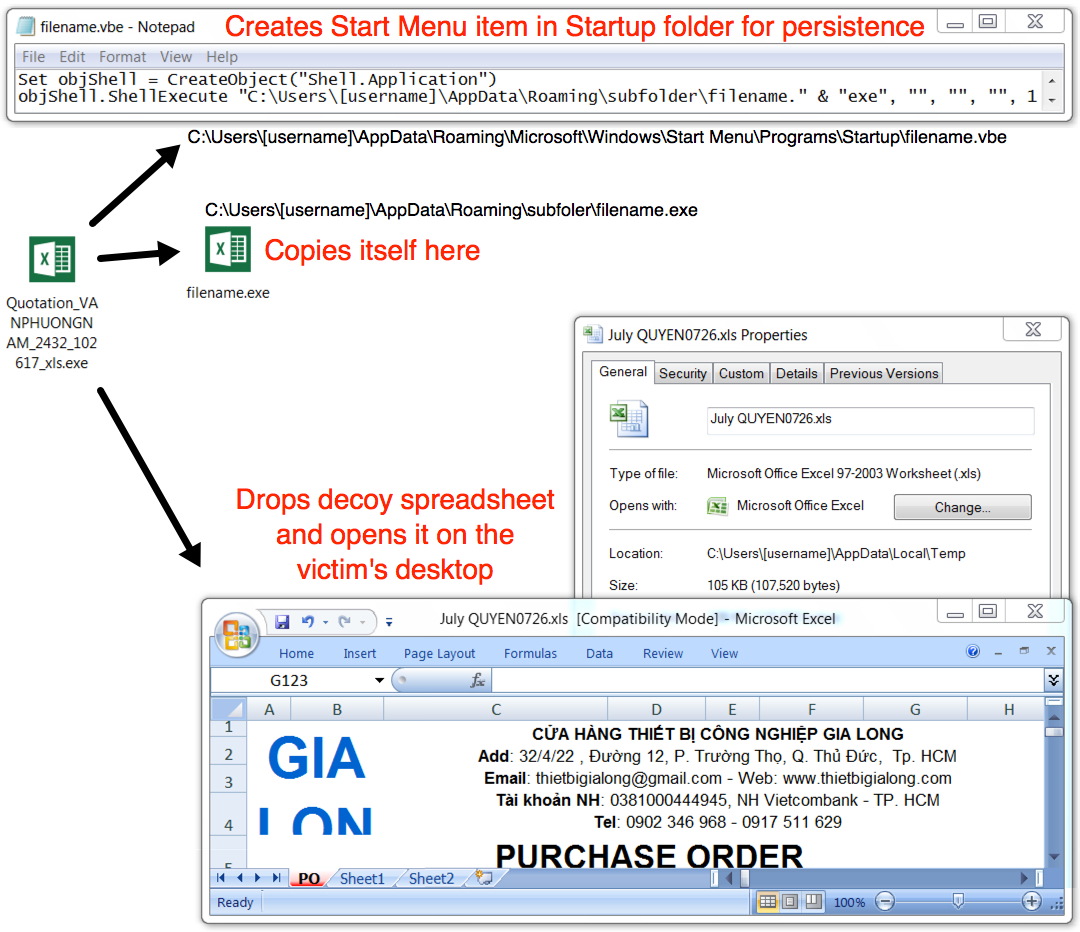
Shown above: Running the extracted executable on a Windows host.
Click here to return to the main page.
