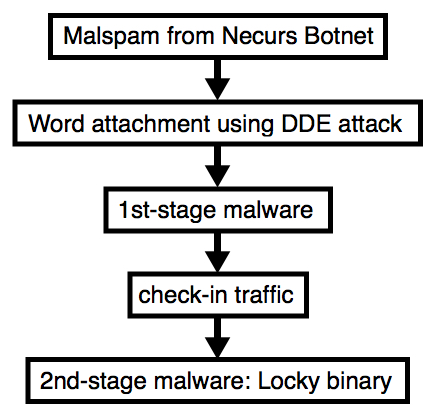
2017-10-30 - NECURS BOTNET MALSPAM USES DDE ATTACK TO PUSH LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-30-Necurs-Botnet-malspam-pushes-Locky-ransomware.pcap.zip 801.9 kB (801,931 bytes)
- 2017-10-30-Necurs-Botnet-malspam-tracker.csv.zip 0.8 kB (826 bytes)
- 2017-10-30-Necurs-Botnet-malspam-and-Locky-ransomware.zip 857.1 kB (857,056 bytes)
SOME PRIOR DOCUMENTATION:
- 2017-10-19 - SANS Internet Storm Center (ISC) - Necurs Botnet malspam pushes Locky using DDE attack
- 2017-10-24 - My Online Security - Another Locky ransomware fake Invoice malspam campaign using DDE "exploit"
- 2017-10-24 - My Online Security - Locky ransomware delivered via DDE exploit Scan Data malspam no-reply@victim domain
- 2017-10-24 - malware-traffic-analysis.net - Necurs Botnet malspam uses DDE attack to push Locky
NOTES:
- Thanks to @JAMESWT_MHT who notified me about today's Necurs Botnet malspam (link to tweet).
- I was able to grab 4 emails from this malspam that were submitted to Virus Total.
Shown above: Same chain of events as we've been seeing.
EMAILS
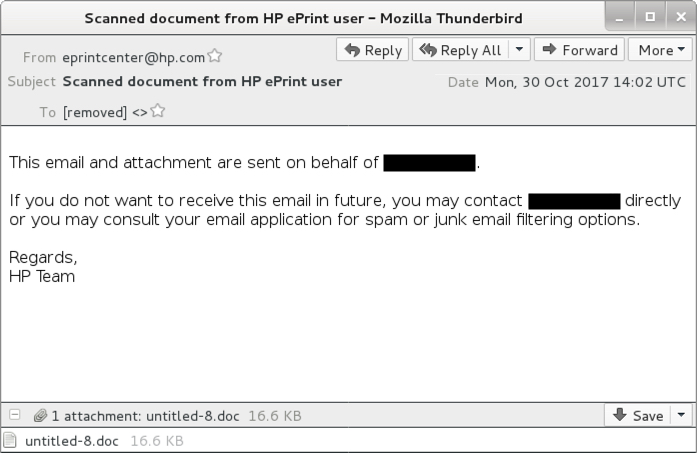
Shown above: Example of an email from this wave of malspam.
EMAIL HEADERS:
- Date: Monday 2017-10-30
- Sending email address (spoofed): eprintcenter@hp[.]com
- Subject: Scanned document from HP ePrint user
- Attachment names: filename-[1 or 2 digits].doc or new document-[1 or 2 digits].doc or untitled-[1 or 2 digits].doc
TRAFFIC
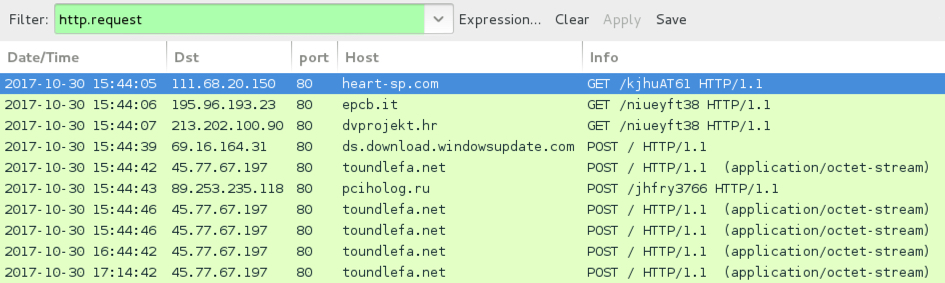
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS:
- 111.68.20[.]150 port 80 - heart-sp[.]com - GET /kjhuAT61 returned base64 string
- 195.96.193[.]23 port 80 - epcb[.]it - GET /niueyft38 returned 404 not found
- 213.202.100[.]90 port 80 - dvprojekt[.]hr - GET /niueyft38 returned file downloader
- ds.download.windowsupdate[.]com - POST / file downloader connectivity check
- 45.77.67[.]197 port 80 - toundlefa[.]net - POST / file downloader post-infection check-in
- 89.253.235[.]118 port 80 - pciholog[.]ru - POST /jhfry3766 returned Locky binary, encoded or otherwise encrypted
OTHER URLS FROM THE WORD DOCUMENTS:
- hotelruota[.]it - GET /kjhuAT61
- hilaryandsavio[.]com - GET /kjhuAT61
- internet-webshops[.]de - GET /kjhuAT61
OTHER URLS TO RETRIEVE THE FILE DOWNLOADER:
- fuettern24[.]de - GET /niueyft38
- h1854684.stratoserver[.]net - GET /niueyft38
- hobbystube[.]net - GET /niueyft38
TOR DOMAIN USED FOR LOCKY RANSOMWARE DECRYPTION INSTRUCTIONS:
- g46mbrrzpfszonuk[.]onion
FILE HASHES
WORD DOCUMENTS USING DDE ATTACK:
- SHA256 hash: b96d0bd2754229e19ec58f1cf91cdfd432bb789f6382034221d4911ef1ffd910 - 16,990 bytes - filename-68.doc
- SHA256 hash: 81b264cfd5ef6de817d4f1b31e5c887f384ede6eefe7ca628fdcde880a159332 - 16,997 bytes - untitled-24.doc
- SHA256 hash: 31ce389b4e2ae15144ee4488f41222fcb29b39909206987591e61fa5f6202d02 - 16,995 bytes - untitled-4.doc
- SHA256 hash: 4a5a0289f47b21b50310b0e00da6de795357e25e622848c5ccb5a53837e6bf14 - 16,996 bytes - untitled-8.doc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 790e7b97b8d5aa0e7129e3523f8c3d0c4c9a1e072d5ccd762881a2b030834c05
File size: 248,512 bytes
File location: C:\Users\[username]\AppData\Local\Temp\hti4.exesh
File location: C:\Users\[username]\AppData\Local\Temp\{68c5f030-bc1a-1282-1725-8eec14b32716}\9rD40BWa.exe
File description: Initial malware (generates callback traffic & downloads Locky)
-
Registry update: KHCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- SHA256 hash: 60834806865b1f4c3e1375a244f77d0a3ebcc4731a890eb6210dc2cc47666236
File size: 659,968 bytes
File location: C:\Users\[username]\AppData\Local\Temp\E5IxznC0.exe
File description: Locky ransomware (.asasin variant)
IMAGES
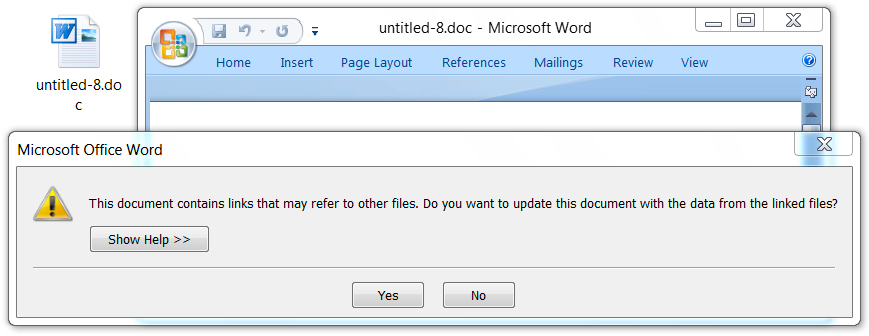
Shown above: Popup notification seen from Word document using DDE attack (1 of 3).

Shown above: Popup notification seen from Word document using DDE attack (2 of 3).
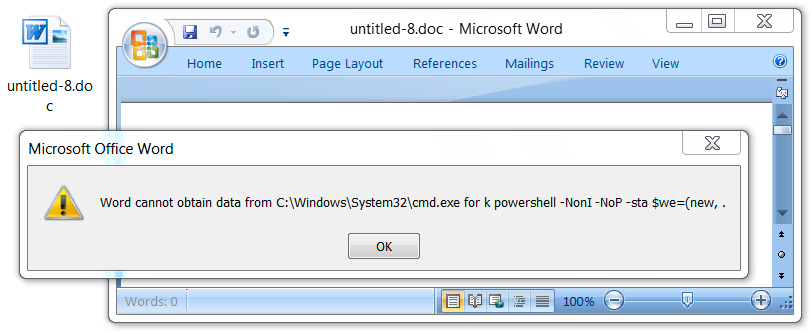
Shown above: Popup notification seen from Word document using DDE attack (3 of 3).
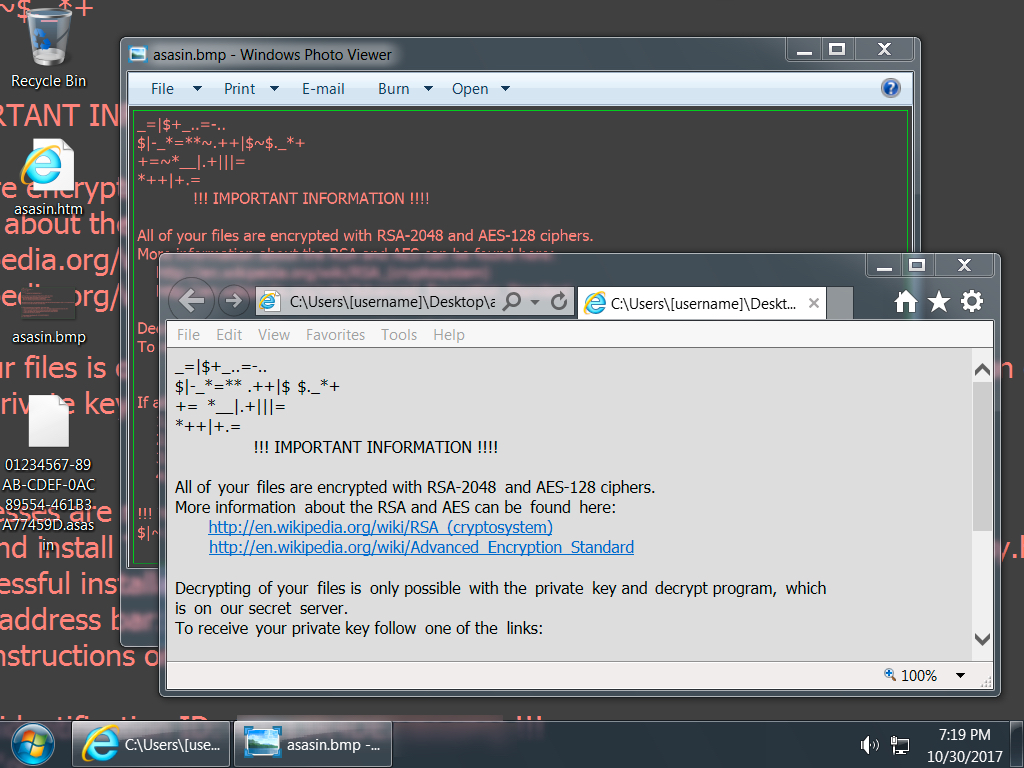
Shown above: Desktop from an infected Windows host.
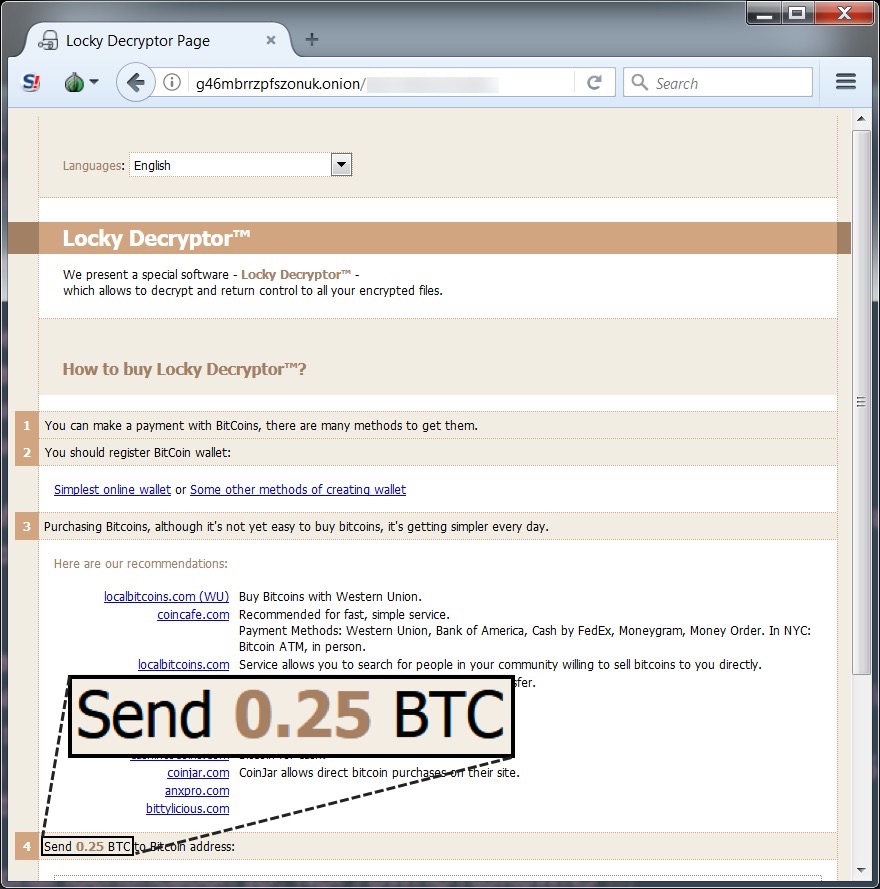
Shown above: Ransom payment was .25 bitcoin.
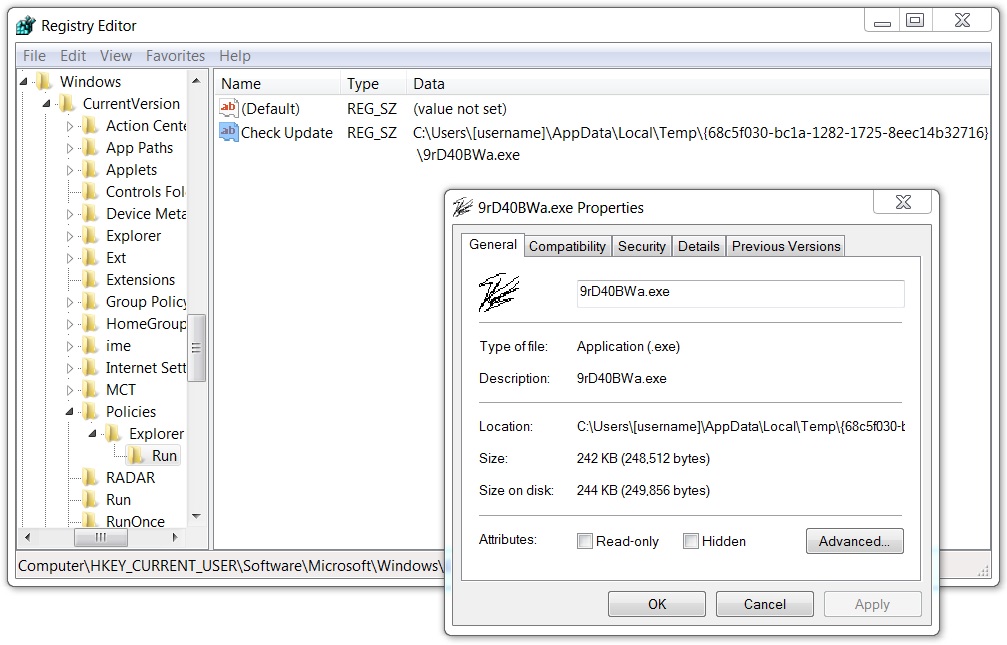
Shown above: Registry update to keep the initial malware persistent on the infected Windows host..
Click here to return to the main page.