2017-10-30 - HANCITOR INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-30-Hancitor-infection-traffic.pcap.zip 364.1 kB (364,140 bytes)
- 2017-10-30-Hancitor-infection-traffic.pcap (528,674 bytes)
- 2017-10-30-Hancitor-malspam-10-examples.zip 18.6 kB (18,605 bytes)
- 2017-10-30-Hancitor-malspam-1621-UTC.eml (5,996 bytes)
- 2017-10-30-Hancitor-malspam-1626-UTC.eml (5,921 bytes)
- 2017-10-30-Hancitor-malspam-1722-UTC.eml (6,002 bytes)
- 2017-10-30-Hancitor-malspam-1724-UTC.eml (6,058 bytes)
- 2017-10-30-Hancitor-malspam-1726-UTC.eml (5,934 bytes)
- 2017-10-30-Hancitor-malspam-1822-UTC.eml (6,033 bytes)
- 2017-10-30-Hancitor-malspam-1829-UTC.eml (5,965 bytes)
- 2017-10-30-Hancitor-malspam-1837-UTC.eml (5,967 bytes)
- 2017-10-30-Hancitor-malspam-1855-UTC.eml (5,933 bytes)
- 2017-10-30-Hancitor-malspam-1918-UTC.eml (6,007 bytes)
- 2017-10-30-malware-from-Hancitor-infection.zip 230.5 kB (230,540 bytes)
- 2017-10-30-ZeusPandaBanker.exe (153,088 bytes)
- statement_299584.doc (220,160 bytes)
TODAY'S TWEETS COVERING THE 2017-10-30 WAVE OF #HANCITOR MALSPAM:
- @James_inthe_box: Incoming #hancitor #malspam: "View your Office 365 Business billing statement for <domain>" pastebin.com/BDYSi0Zv updates forthcoming (link)
- @pollo290987: #Hancitor arizoznaic,us/s.php?nlv654=[email clear] 10stepstoyes,info/s.php?idw042=[email clear] colighaningr,com GET /ls5/forum.php (link)
NOTES:
- The DDE attack we saw earlier this month from Hanictor malspam was very short-lived. Today, just like last time, it's been Word macros.
- Also like last time, we have Zeus Panda Banker (no ZLoader/DELoader).
EMAILS
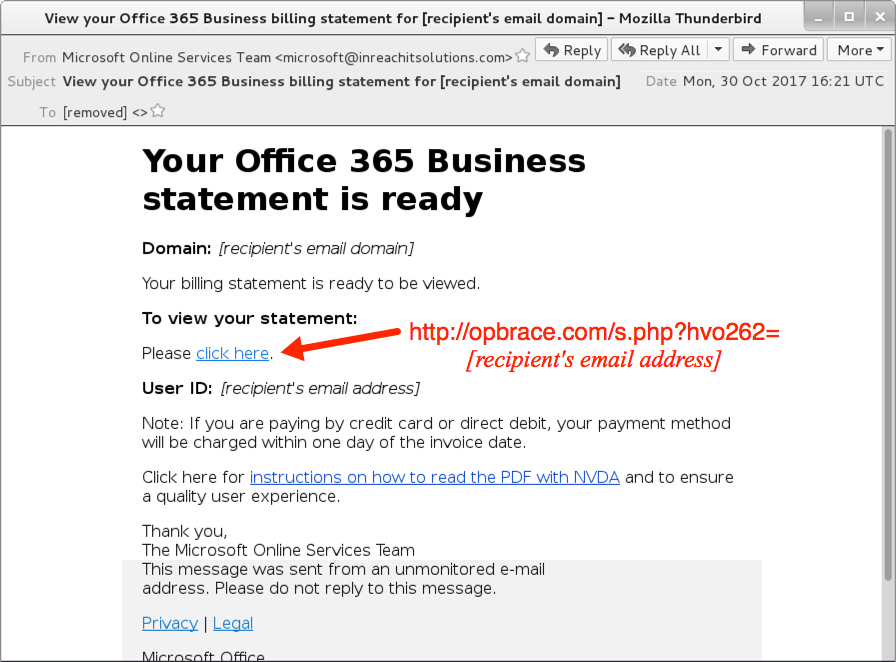
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Monday 2017-10-30 as early as 16:21 UTC through at least 19:18 UTC
- Subject: View your Office 365 Business billing statement for [recipient's email domain]
- From: "Microsoft Online Services Team" <microsoft@inreachitsolutions.com>
- Received: from inreachitsolutions[.]com ([50.206.59[.]110])
- Received: from inreachitsolutions[.]com ([67.88.39[.]194])
- Received: from inreachitsolutions[.]com ([69.11.104[.]192])
- Received: from inreachitsolutions[.]com ([74.95.217[.]206])
- Received: from inreachitsolutions[.]com ([76.73.153[.]98])
- Received: from inreachitsolutions[.]com ([79.10.219[.]3])
- Received: from inreachitsolutions[.]com ([98.198.65[.]62])
- Received: from inreachitsolutions[.]com ([108.190.156[.]147])
- Received: from inreachitsolutions[.]com ([136.61.93[.]165])
- Received: from inreachitsolutions[.]com ([174.226.18[.]159])
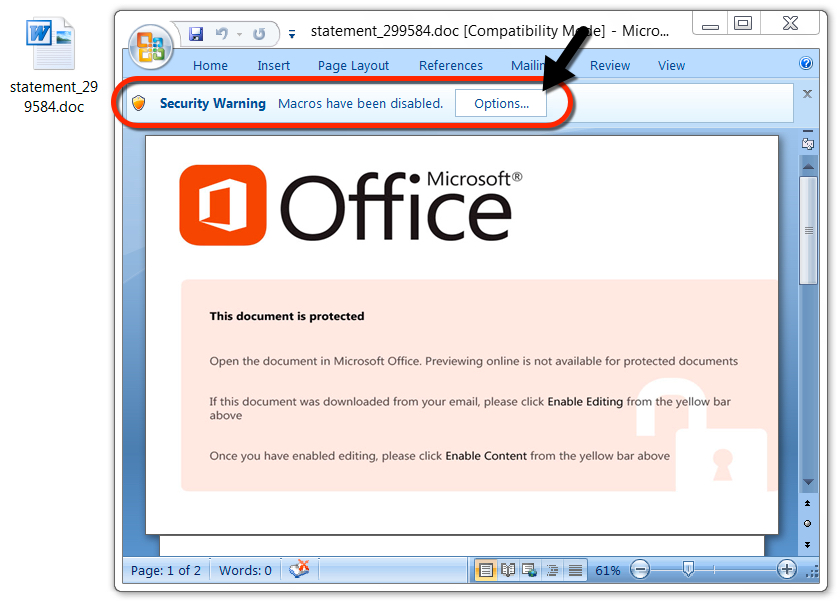
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
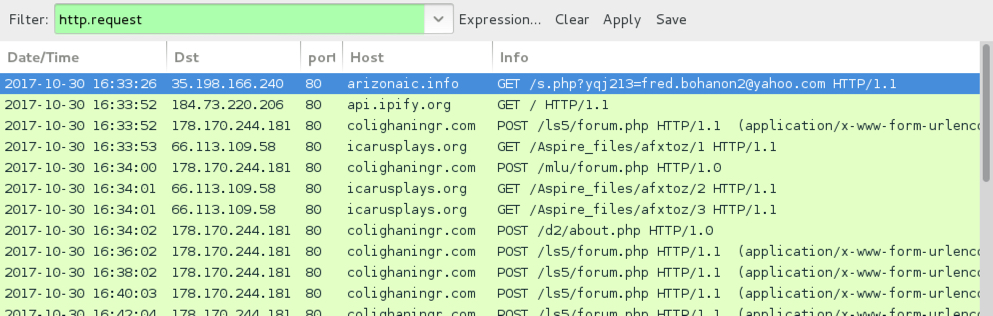
Shown above: Traffic from the infection filtered in Wireshark.
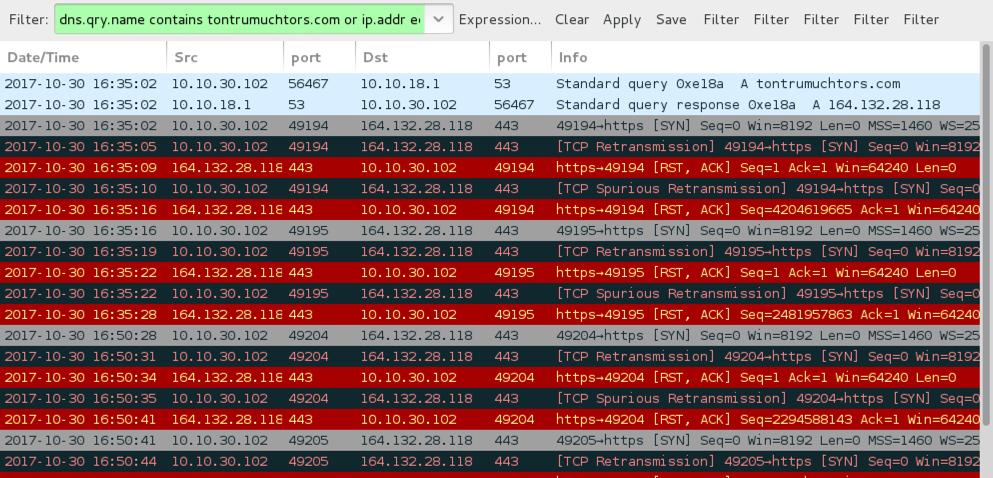
Shown above: Attempted TCP connections caused by Zeus Panda Banker on the infected host.
LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- arizonaic[.]biz - GET /s.php?fre574=[recipient's email address]
- arizonaic[.]biz - GET /s.php?tnx552=[recipient's email address]
- arizonaic[.]com - GET /s.php?ywy156=[recipient's email address]
- arizonaic[.]mobi - GET /s.php?mim650=[recipient's email address]
- arizonaic[.]net - GET /s.php?jxw684=[recipient's email address]
- arizonaic[.]net - GET /s.php?sns010=[recipient's email address]
- arizonaic[.]us - GET /s.php?aiz184=[recipient's email address]
- arizonaic[.]us - GET /s.php?kjw700=[recipient's email address]
- opbrace[.]com - GET /s.php?hvo262=[recipient's email address]
- tenstepstoyes[.]org - GET /s.php?vvg003=[recipient's email address]
NAME FOR THE MALICIOUS WORD DOCUMENT:
- statement_[six random digits].doc
POST-INFECTION TRAFFIC FROM MY INFECTED HOST:
- 178.170.244[.]181 port 80 - colighaningr[.]com - POST /ls5/forum.php
- 178.170.244[.]181 port 80 - colighaningr[.]com - POST /mlu/forum.php
- 178.170.244[.]181 port 80 - colighaningr[.]com - POST /d2/about.php
- 66.113.109[.]58 port 80 - icarusplays[.]org - GET /Aspire_files/afxtoz/1
- 66.113.109[.]58 port 80 - icarusplays[.]org - GET /Aspire_files/afxtoz/2
- 66.113.109[.]58 port 80 - icarusplays[.]org - GET /Aspire_files/afxtoz/3
- 164.132.28[.]118 port 443 - tontrumuchtors[.]com - attempted TCP connection (RST from the server)
- api.ipify[.]org - GET /
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: d2ddcfd70f9fb7eba158c1ce17438bd9328ddfaa6507428be4f802402b15ab9e
File name: statement_299584.doc
File size: 220,160 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: ba35a1c840ba413f1f92179b7dce1d84ae07b9f8a349e847692760a7b395ddb1
File location: C:\Users\[username]\AppData\Local\Temp\[random characters].tmp
File location: C:\Users\[username]\AppData\Roaming\[random existing path]\[random name].exe
File size: 153,088 bytes
File description: Zeus Panda Banker
Click here to return to the main page.
